- No changes to the Server Settings are required any more
- ACME wildcard certificates can be used for the landing page
12.1.9 (externe & lokale Zertifikate) 11.8.7 (externe Zertifikate) 11.8.7 (lokale Zertifikate) 11.7.3 (externe Zertifikate) 11.7.3 (lokale Zertifikate) 11.7
Preliminary remark
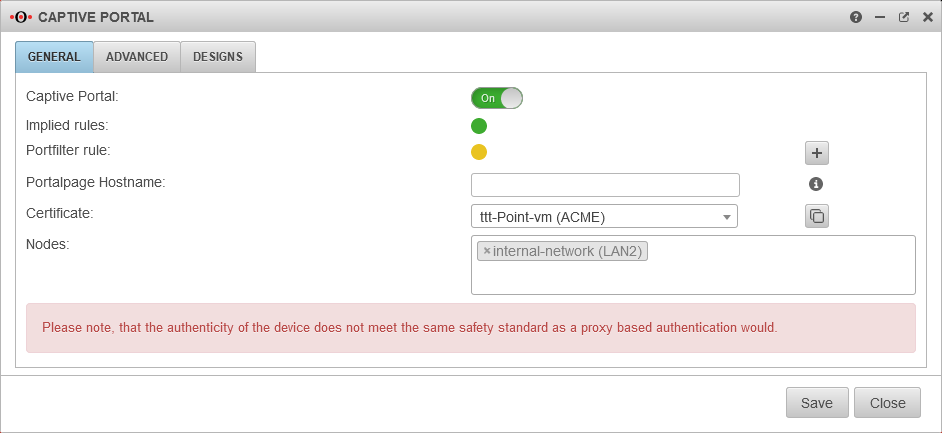
The captive portal redirects an HTTP client in a network to a special web page (so-called landing page) before it can connect normally to the Internet. Thus, acceptance of the condition of use must take place and additional authentication can be configured.
It is recommended to use either an ACME certificate or a purchased certificate from an official CA (or an already existing wildcard certificate) for the captive portal to prevent later irritations due to warning messages of the browser.
Planning
The following aspects should be considered before configuration:
- For which networks should the captive portal be configured?
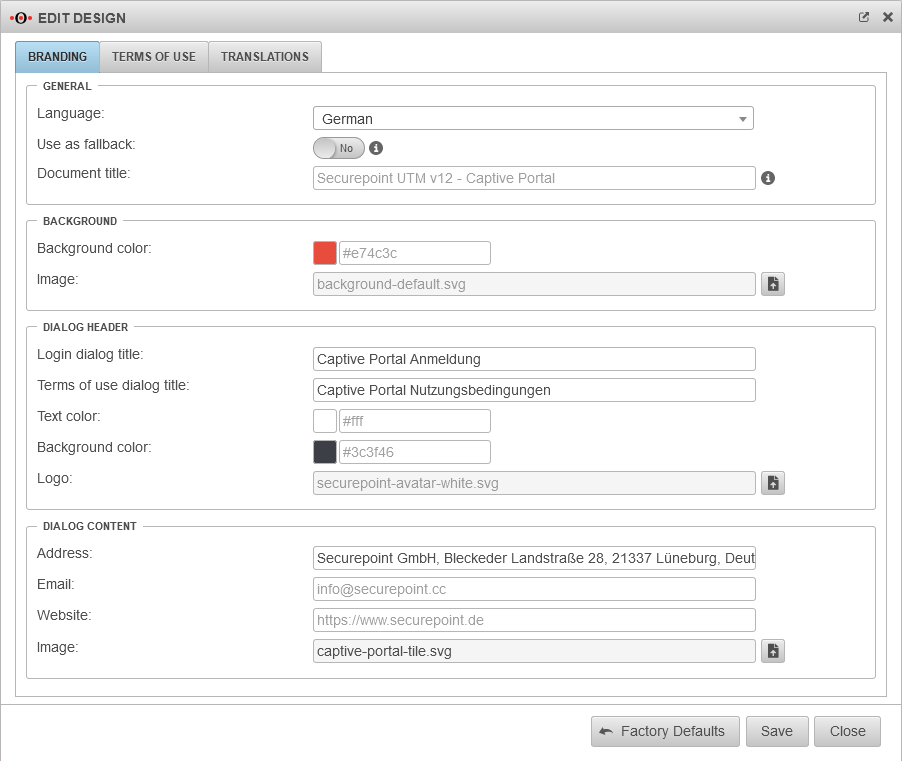
Will all potential users be reached exclusively? - How and by whom will the terms of use be written?
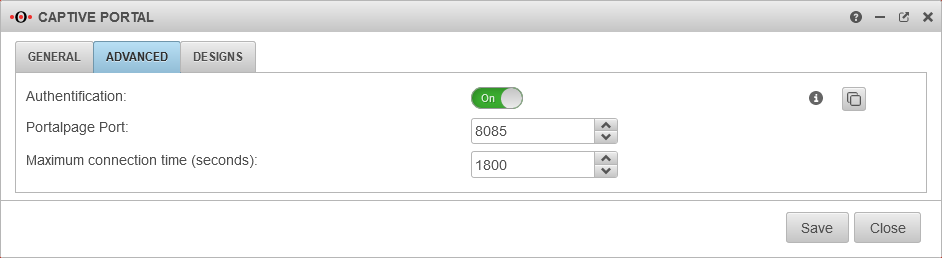
- Should authentication take place?
- Which internal web servers are not allowed to be reached from the network behind the captive portal?
Jus a few preparations must be made to use the captive portal:
- A certificate must be available for the landing page
- Implicit and port filter rules must allow access
The host name of the portal page is configured under Area General.
Provide certificate
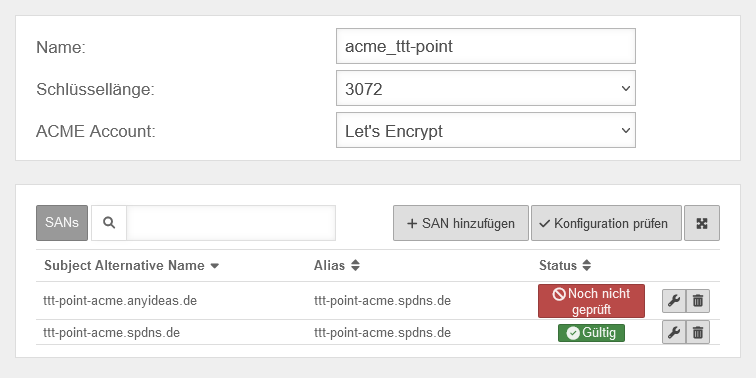
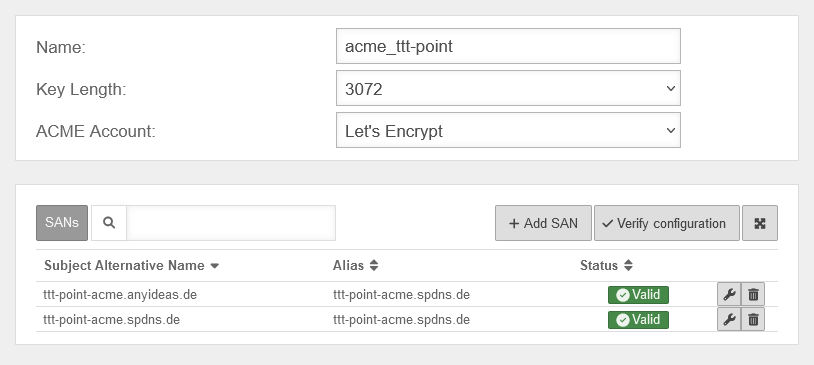
Create an ACME certificate
To use ACME certificates (Let's Encrypt) the following steps are required:
- Activate ACME service
- Generate ACME Challenge Token on spDyn
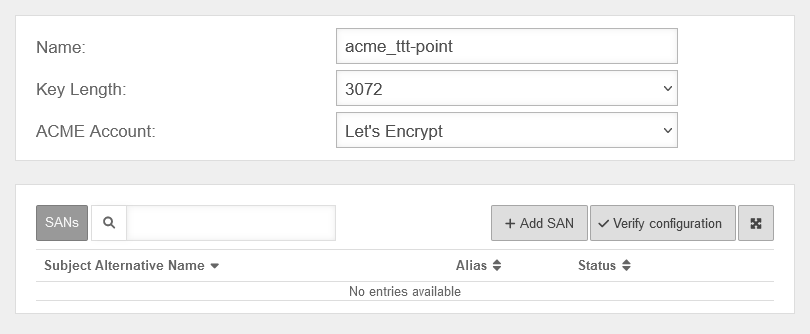
- Create certificate
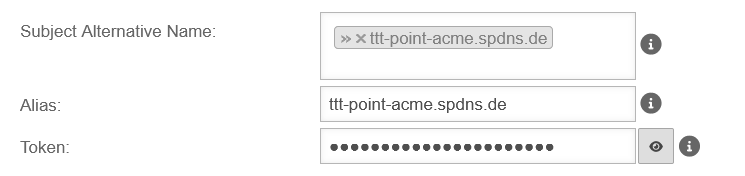
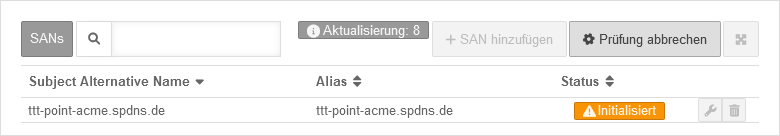
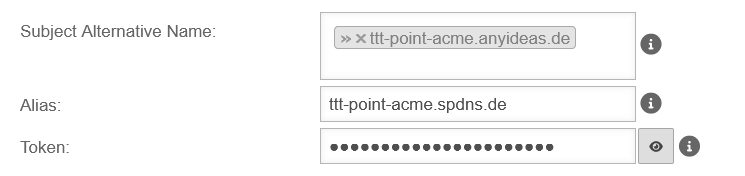
- Add SAN with spDyn hostname and token
- Create certificate
Area ACME
| Caption | Value | Description | UTMuser@firewall.name.fqdnAuthentifizierung 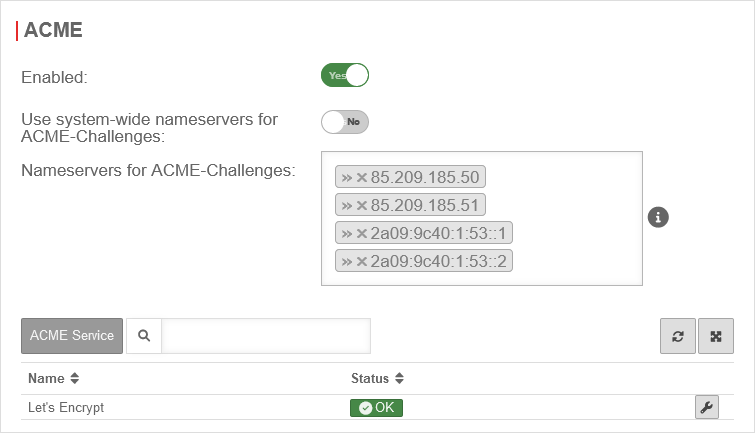
|
|---|---|---|---|
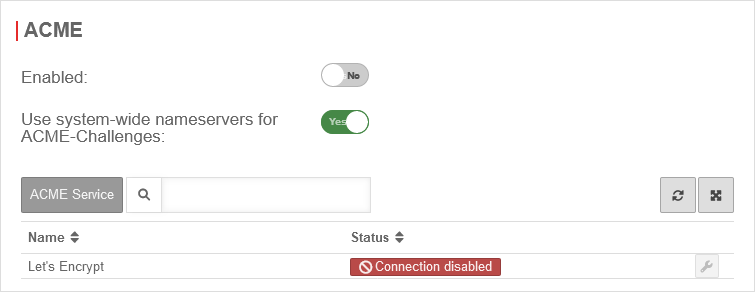
| Activated: | Yes | Enables the use of ACME certificates. For more information see below Activate ACME service. | |
| Use system-wide nameservers for ACME challenges: | Yes | If the addresses for the servers for the extension of the ACME challenges cannot be resolved via the system-wide nameserver (e.g. due to configured relay or foreward zones), alternative nameservers can be entered by deactivating No. | |
| Nameserver for ACME challenges: Can be used for ACME challenges when system-wide nameserver is disabled |
» ✕85.209.185.50» ✕85.209.185.51» ✕2a09:9c40:1:53::1» ✕2a09:9c40:1:53::2 | Here you can enter the nameservers for the ACME-Challenges. | |
Activate ACME service
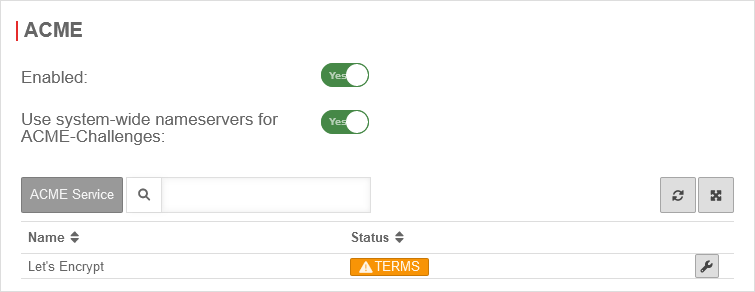
Activate ACME serviceUm ACME Zertifikate nutzen zu können, muss dies unter Area ACME Aktiviert: Ja aktiviert werden.
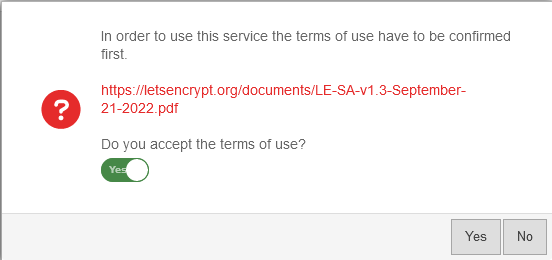
- Sobald der Dienst aktiviert wurde und dies mit gespeichert wurde, wird der Link zu den Nutzungsbedingungen geladen und es lassen sich die Einstellungen aufrufen.
- With the button Activate Yes and the storage of an Email address for notifications by the ACME service provider (here: Let's Encrypt), the information can be saved with
- A dialog will appear with a link to the Terms of Use, which must be accepted Yes.
Generate token
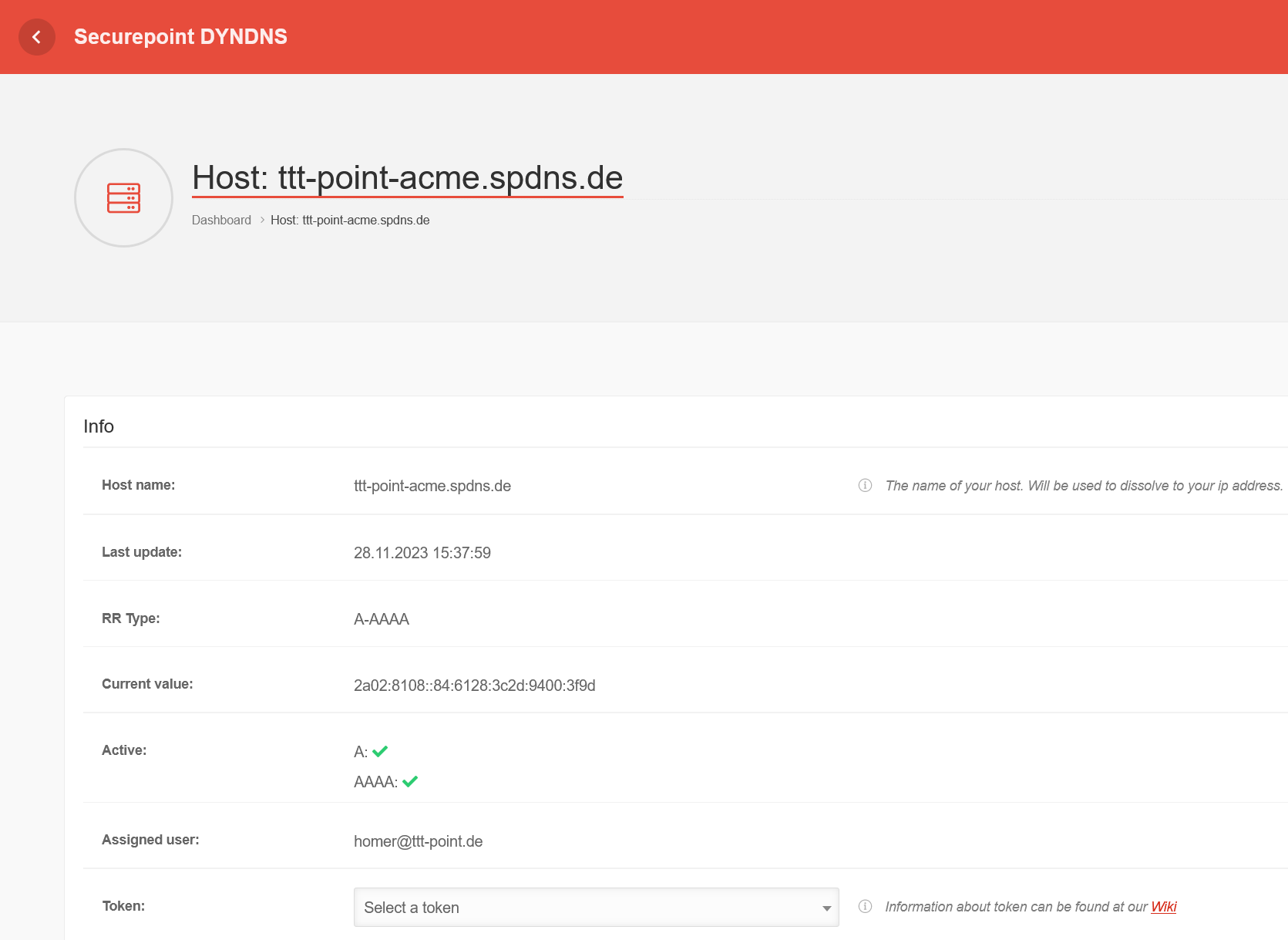
Generate tokenspDYN To generate the certificates, the ACME token must first be generated in the spDYN portal.
Within the spDYN portal, the corresponding host must be opened.
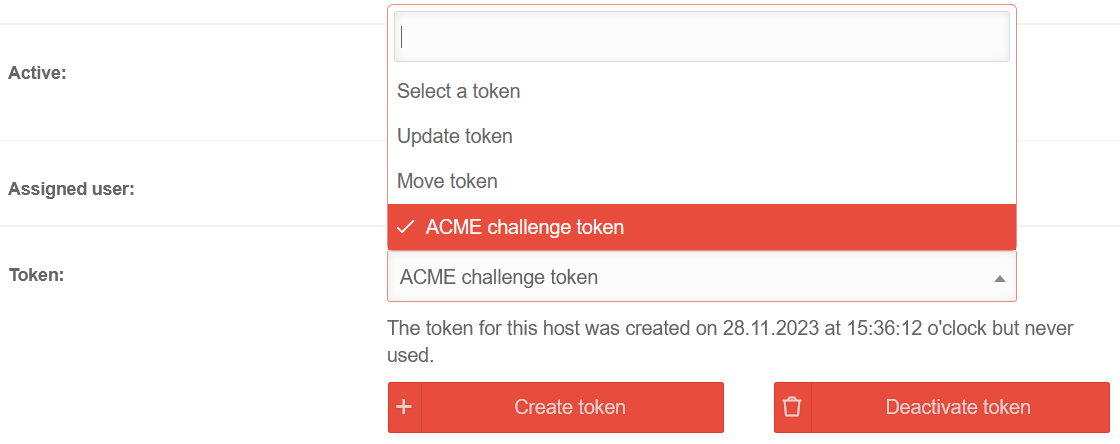
- Call up spDyn Host
- Select the ACME Challenge Token from the Token drop-down menu.
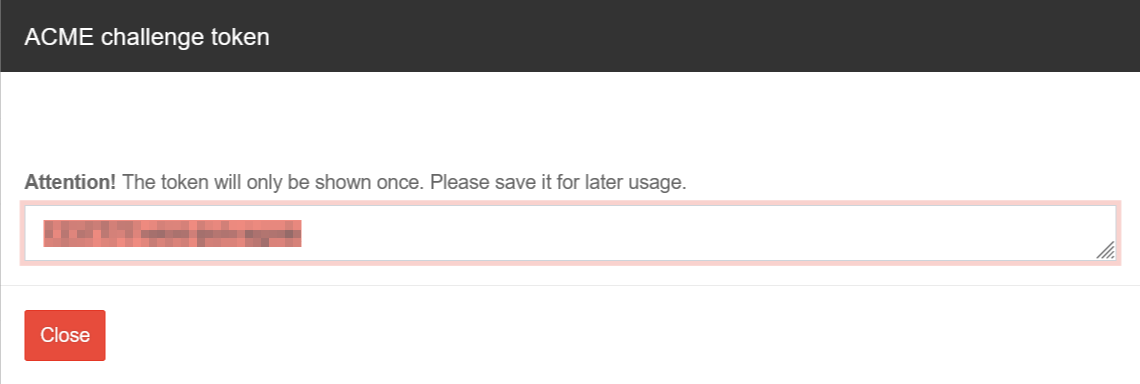
- Generate token
notemptyThe token is displayed once during generation and cannot be displayed again.
The token should be noted and stored safely.
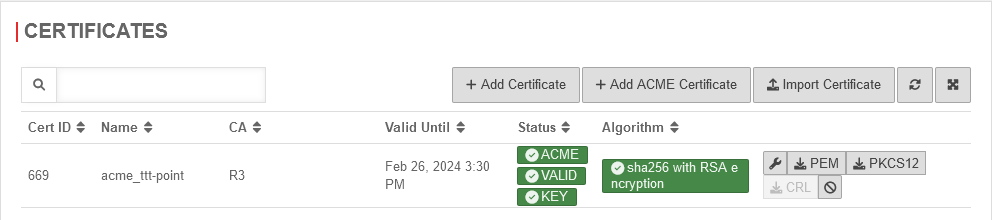
Renewal of ACME certificates
Renewal of ACME certificates
ACME Certificates
ACME CertificatesPurchased certificate
Alternatively, a purchased certificate can also be imported
Grundsätzlich bestehen hier zwei Optionen:
- A Certificate for a FQDN
- in this case the common name of the certificate would be portal.anyideas.de
- A wildcard certificate
- in which case the common name of the certificate would be *.anyideas.de
In the first step, the CA provided together with the certificate must be imported into the UTM.
Menu Area CA ButtonIn the first step, the CA provided together with the certificate must be imported into the UTM.
Menu Area CA Button
Import format
Certificates and CAs to be imported into a UTM must be in the format .pem or .p12 (pkcs12).
Certificates can be converted with the tool openssl - available for all common platforms (part of Linux, call via console) - and the following commands:
| Certificate | Command |
|---|---|
| X509 to PEM | openssl x509 -in certificatename.cer -outform PEM -out certificatename.pem |
| DER to PEM | openssl x509 -inform der -in certificate.cer -out certificate.pem |
| P7B to PEM | openssl pkcs7 -print_certs -in certificate.p7b -out certificate.pem |
Error message during import
During import, the error message "The certificate format is not supported..." may appear.
Password protected certificates in pkcs12 format (.p12 , .pfx , .pkcs12) in conjunction with older ciphers can trigger this error.
Options for importing certificates:
- Convert certificate to *.pem
Certificates can be converted with the tool openssl - available for all common platforms (part of Linux, call via console) - and the following commands:
openssl pkcs12 -in Zertifikat.pfx -out Zertifikat.pem -nodes
Alternatively with the help of an online service - CLI commands to allow certificate import with obsolete ciphers in the UTM
extc global set variable GLOB_ENABLE_SSL_LEGACY value 1
appmgmt config application "securepoint_firewall"
appmgmt config application "fwserver"
system reboot
notemptyRequires a This will interrupt all connections (incl. VPN connections) to the UTM!
cli> extc global get variable GLOB_ENABLE_SSL_LEGACY variable |value ----------------------+----- GLOB_ENABLE_SSL_LEGACY|0 cli> extc global set variable GLOB_ENABLE_SSL_LEGACY value 1 OK cli> extc global get variable GLOB_ENABLE_SSL_LEGACY variable |value ----------------------+----- GLOB_ENABLE_SSL_LEGACY|1 cli> appmgmt config application "securepoint_firewall" cli> appmgmt config application "fwserver"
Local certificate
The UTM can also provide its own certificate
- At Area CA a CA must be created
- At Area Certificates a Server- certificate must be created. A separate certificate should be created for the captive portal so that it can be revoked if necessary without affecting other connections or applications.
How to create a certificate on the UTM can be read here.
The user receives a warning message in which the trustworthiness must be confirmed once.
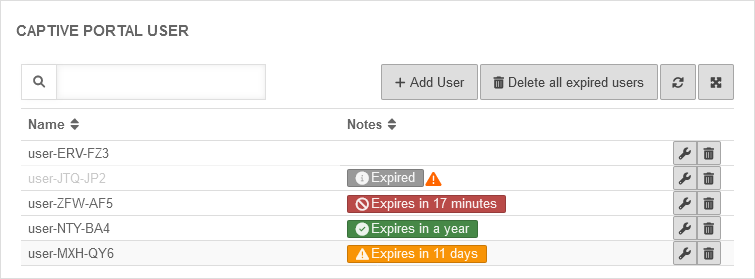
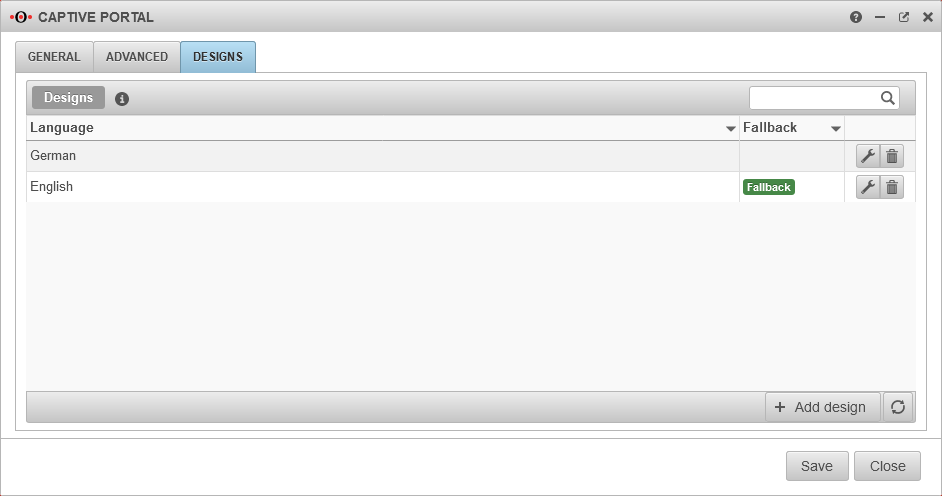
Captive Portal User
Add user
Captive Portal users can be managed by:
- Administrators
- Users who are members of a group with the permission Userinterface Administrator .
They reach the user administration via the user interface.
Implied rules
UTMuser@firewall.name.fqdnFirewall 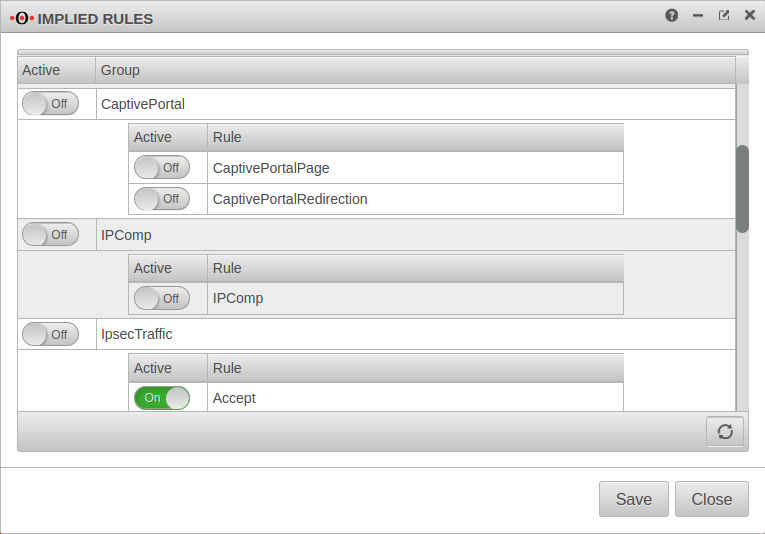 Firewall - Implied rules
Menu Group Ein Captive Portal
Firewall - Implied rules
Menu Group Ein Captive Portal
At the item Captive Portal in the menu Implied Rules you have to make sure that both rules are activated.
The switch CaptivePortalPage opens an incoming port on the corresponding interface of the firewall, which is intended for the Captive Portal to be able to display the landing page.
The switch CaptivePortalRedirection is, as the name suggests, responsible for the corresponding redirection of the traffic to the port mentioned above.
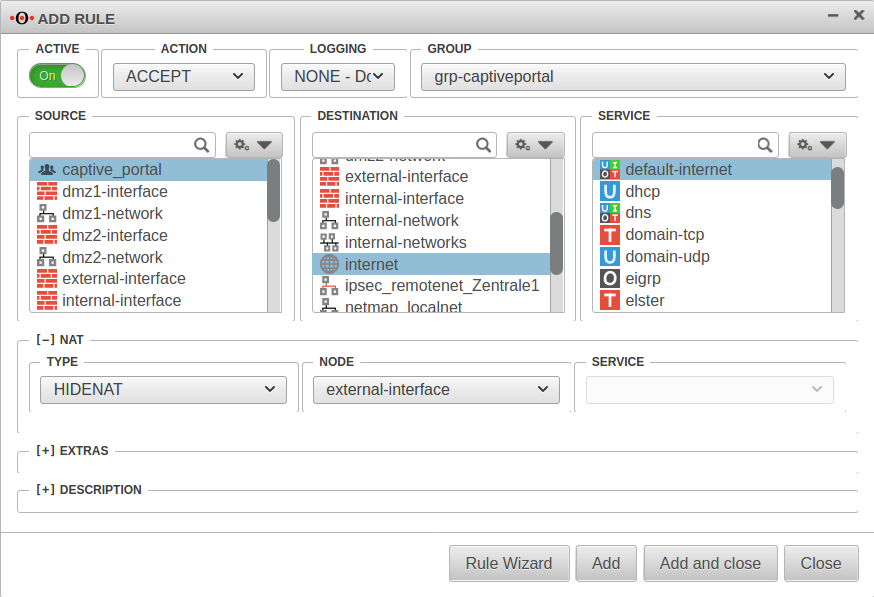 Firewall - Portfilter IP
A rule is required in the port filter to allow Captive Portal users to access the Internet.
Firewall - Portfilter IP
A rule is required in the port filter to allow Captive Portal users to access the Internet.
Alternatively, an autogenerated any rule can also be created in the Captive Portal settings using the button in the General tab.
| Source:: | |
| Destination:: | |
| Service: | |
[–] NAT
| |
| Type:: | |
| Network object: |
Save
Settings in the Captive Portal
Menu
General
Nameserver
Menu Area Zones
If the firewall name cannot be changed to a FQDN, for example because the UTM is used as outgoing mail relay, the name server of the firewall must also be used: In this example, it is assumed that the firewall for the network of the captive portal is the responsible DHCP server and is set up as primary DNS server.
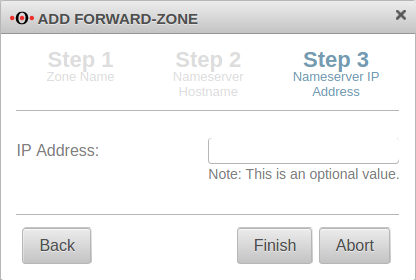
Add Forward Zone
Button
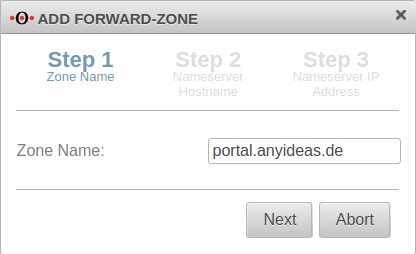
The zone name to be assigned corresponds to the landing page of the captive portal.
In the example portal.anyideas.de.
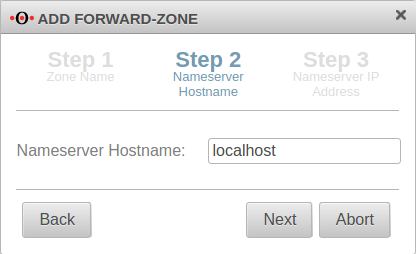
localhost is used as the host name of the name server.
The IP address field can be left empty.
Edit Forward Zone
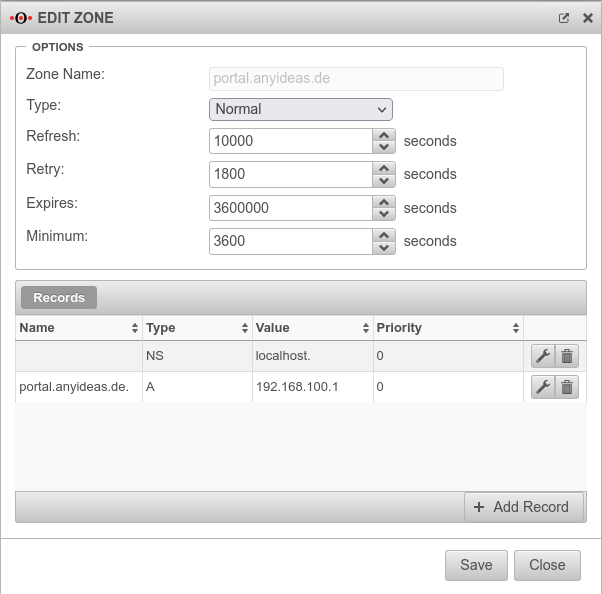 Nameserver - A-Record with IP address
The following entry is added to the zone just created → Button :
Nameserver - A-Record with IP address
The following entry is added to the zone just created → Button :
| Caption | Value | Description |
|---|---|---|
| Name:: | portal.anyideas.de. | FQDN of the firewall |
| Type:: | A-Record | |
| Value: | 192.168.100.1 | IP of the interface via which the captive portal is to be reached (here wlan0 ) |
Transparent mode
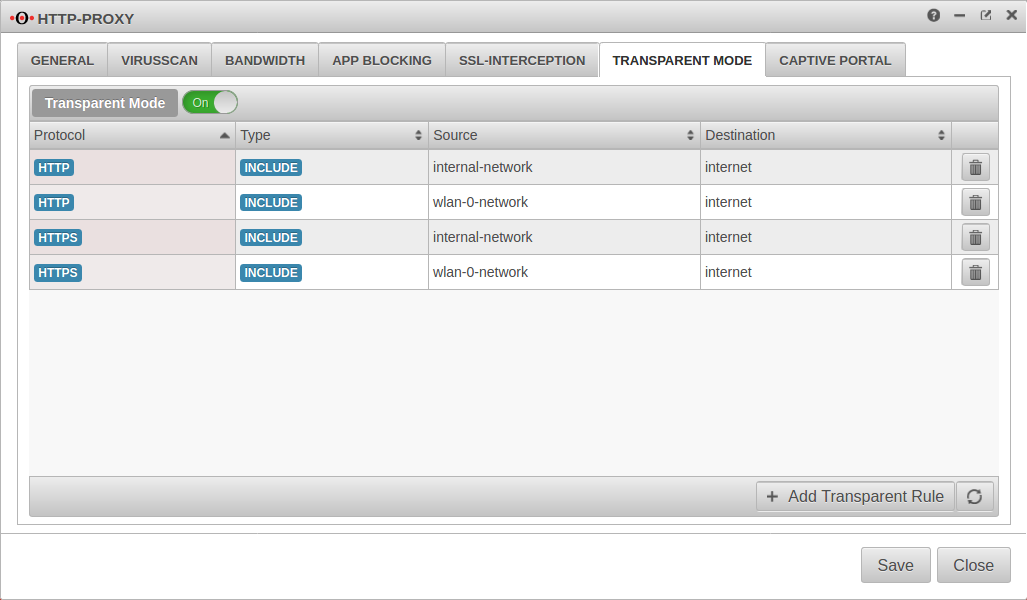 HTTP Proxy - Transparent Proxy
Menu Area Transparent mode
HTTP Proxy - Transparent Proxy
Menu Area Transparent mode
To access the Internet via the required HTTP proxy, at least one rule is necessary (HTTP), better two (additionally HTTPS)
Button
| Caption | Value |
|---|---|
| Protocol: | |
| Type: | |
| Source: | |
| Destination: |
To access https pages, in the tab SSL Interception SSL Interception On must be activated. (Requires a CA certificate of the UTM)
| Caption | Value |
|---|---|
| Protocol: | |
| Type: | |
| Source: | |
| Destination: |
Webfilter
Finally, the web filter should be configured, since surfing through the proxy is possible without rules in the port filter access to e.g. internal web servers:
with authentication
- Area Network objects Button
Create a group (e.g. grp_CP_webfilter) that contains the wlan-0-network network object - Button
- Network or user group: Select the newly created group
- Edit newly generated rule record
- webserver.anyideas.de URL of the (internal) server to which access via the captive portal should be blocked
- Leave action on block
without authentication
- Button
- Select the user group
- Edit newly generated rule record
- webserver.anyideas.de URL of the (internal) server to which access via the captive portal should be blocked
- Leave action on block