- Additional filter rules recommended:
SPF fail, SPF permerror, DKIM, DMARC quarantine, DMARC reject
These are our recommended settings.
All information provided without guarantee!
Requirements
These recommendations refer to the following scenario:
- Receiving the emails through the mail relay
- Delivery is made directly via MX
- Filtering occurs directly on input to MX
General
Global email address
Mail relay
Under , set the configuration to accept only emails to the recipient's address.
General
| Caption | Value | Description |
|---|---|---|
| Mail filter | On | The mail filter function must be activated |
| SPF/DKIM/DMARC audits: | On | Adds an RFC 8601 Authentication-Results header to the mail and allows filtering for corresponding SPF/DKIM/DMARC results in a Mailfilter rule (see below). |
Relaying
Relaying list
Configure with
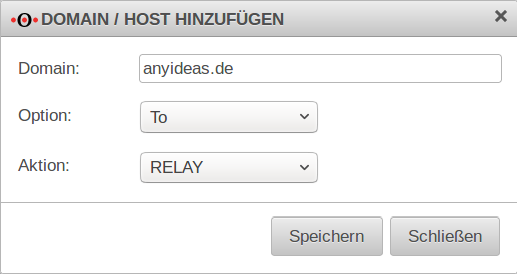
| Mails, addressed to the anyideas.de domain should be forwarded by mail relay | ||
| Domain: | anyideas.de |
Example domains for receiving emails |
| Option: | ||
| Action: | Relay | |
| If outbound emails are to be sent via the mail relay of the UTM, another entry is required: | ||
| Domain: | 192.168.175.100 |
IP address of the internal mail server |
| Option: | While making a connection | |
| Action: | Relay | |
| Entry for a mail server that is to be blacklisted: | ||
| Domain: | 203.0.113.113 |
IP address of the foreign mail server |
| Option: | While making a connection | |
| Action: | refuse | |
| Use exact domain name for relaying: | On | This option will not accept emails to recipients within a subdomain. |
TLS settings
| ||
| TLS encryption as a server: | On | TLS encryption for mail relay must be enabled, otherwise mails will be received over unencrypted connections.
See also the notes of the German BSI for using TLS (german language). |
| Certificate | Importing a certificate whose CN corresponds to the host name of the UTM is optional. If such a certificate is not imported, the mail relay uses a self-signed certificate for the purpose of transport encryption. | |
| TLS encryption as a client: | Ensures that emails are sent over an encrypted connection in all instances. | |
SMTP routes
section
Validation of recipients for valid e-mail addresses must be activated when smtp is used.
This means that only emails that go to a recipient that is also registered on the mail server are accepted.
Greylisting
Greylisting causes the delivery attempt of an unknown mail server to be rejected at first.
Spambots usually do not make any further delivery attempts, so the delivery of spam has already been successfully stopped before the mail had to go through the spam filter engine.
A regular mail server, on the other hand, will make another, this time successful, delivery attempt after a certain period of time.
In addition to fending off simple spambots through greylisting, valuable time is also gained to load new definitions to detect any new spam waves.
notempty| Labeling | Recommendation | Description |
|---|---|---|
| Greylisting: | On | Enables greylisting. |
| SPF: | On | If the Sender Policy Framework of the sender domain is correctly entered in the DNS, the mail is delivered without delay. In the SPF record, all mail server IP addresses of the sender are entered that are authorized to send emails. The recipient then checks the mail header field "Mail From" or the "HELO" command to see which domain is entered or named there and whether it matches one of the IP addresses in the SPF record. If the IP address of the sender does not match those of the SPF record, the mail goes into greylisting. |
| Add header: | On | By default, an additional greylisting entry is added for each recipient listed in the mail header. This can cause issues if there are many recipients in the header. |
| Automatic allow list for: | 60 days | The value can be increased up to 60 days. |
| Delay: | 2 minutes | Time frame given to the sending mail server to make another delivery attempt. notempty Depending on the configuration of the sending mail server, redelivery may be delayed by much more than the configured time frame (default settings 2 minutes) - in extreme cases by several hours.
notempty If a larger value is set for Delay for instance:
30 minutes selected, the scan engine may have a higher probability of detecting new outbreaks with redelivered emails, because the virus signatures may have been updated in the meantime.
|
Extended | ||
Greeting PauseGreeting Pause | ||
| Labeling | Recommendation | Description |
| Status | On | Similar to Greylisting, greeting pause takes advantage of the fact that the SMTP protocol is not fully implemented in spam bots. This allows them to be distinguished from regular mail servers. The greeting is a greeting that is transmitted from the mail relay to the sending mail server. |
Recipient limitationsRecipient limitations | ||
| Status | Off |
This option blocks mails that have more than a defined number of recipient addresses. In the meantime, most spam mails are sent as individual mails. This option should only be activated in special cases. |
| Limit: | 25 | Number of recipients that must not be exceeded (Attention: May apply to company-internal mail groups!). |
Limitations per client
| ||
| Limit connections | On | Here you can define how many connections the mail relay accepts at the same time. Allowed connections: 1 (Leave default value.) The connection limit counteracts possible DDOS attacks. |
| Enable access control | On | Possible DOS attacks are counteracted by the access control. |
| Time slot: | 60 seconds | |
| Connections per time slot: | 5 | |
| Host | If outbound mails are also to be sent via the mail relay of the UTM, the corresponding mail servers should be added. | |
Other Other | ||
| HELO required | On | If HELO is enabled, the SMTP client is requested to give its name. Must absolutely remain activated (default) This option exists to ensure backward compatibility. |
| Reverse DNS lookup needs: | On |
Checks if the HELO name exists and applies in the PTR. Deactivate action Off
|
| Accept unresolvable domains: | No |
Checks if host address and sender address are resolvable. Should remain disabled for SMTP. notempty Must be enabled when using the mailconnector
|
| Maximum number of processes: | 10 | The value should only be adjusted in case of permanently high mail volume and must consider the performance of the hardware! |
Mail filter
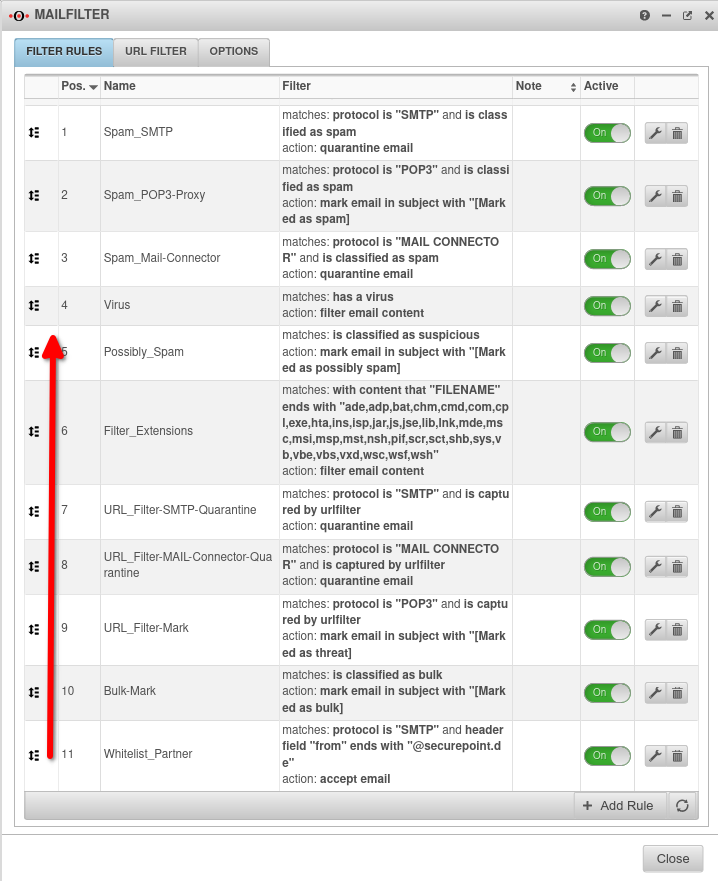
Under many different Filter rules should be adjusted and/or newly created:
Filter rules
| Filter rule | Description |
|---|---|
Filter rule »is classified as SPAM / SMTP«Spam_SMTP |
When an email is received
Run action:
Edit filter rule: Default: Quarantine email
Mail servers or senders whose emails are classified as SPAM have attracted attention as SPAM sources in the past. Emails from these systems should not be accepted under any circumstances.
Accepting such emails (even if they are quarantined afterwards) only makes the email domain more interesting for potential SPAM and virus senders. notempty
Securepoint recommends that these mails be rejected. |
Filter rule »is classified as suspicious«.Possibly_Spam |
When an email is received
Run action:
Edit filter rule:
Default: Tag email in subject with [Marked as possibly spam]
Emails that are classified as suspicious contain suspicious patterns and content and should not be delivered to the user's mailbox.
notempty
Securepoint recommends that these mails be quarantined. Here we recommend
|
Filter rule »contains a virus«Virus |
When an email is received
Run action:
Edit filter rule:
Default: Filter applicable content
Accepting such emails (even if they are quarantined afterwards) only makes the email domain more interesting for potential SPAM and virus senders.
notempty
Securepoint recommends that these mails be rejected. Here we recommend
Here we recommend
|
Filter rule »with content of«Filter_Extensions |
When an email is received
Run action:
Edit filter rule:
Default: Filter applicable content
Executable files should not be delivered. They are filtered based on the file extension. Can be added to as needed.
notempty
Securepoint recommends that these mails be rejected. Here we recommend
|
Filter rule »is a bulk email«bulk_rescan Bulk_Mail |
rule name bulk_rescan
When an email is received
Run action:
Edit filter rule: 30 minutes
Default: Accept email Emails classified as BULK are currently being sent out in masses and should not be delivered to the user's mailbox.
These could be, for example, the first emails of a new SPAM wave. notempty
Securepoint recommends that these mails be quarantined. Here we recommend BULK Mail
Another rule is needed that defines how to proceed in case of a new scan with the same result! rule name Bulk_Mail
When an email is received
From Run action:
Edit filter rule:
Default: Accept email
|
Filter rule »Investigate / further investigations are recommended«Investigate |
rule name Investigate
When an email is received
Run action:
Edit filter rule: 15 minutes
Default: Accept email The spam filtering engine expects that the category of this email may change in the next 15 minutes.
notempty
Securepoint recommends that these mails be quarantined. Here we recommend Check content (no classification)
|
Filter rule »was caught by the URL filter«URL_Filter |
Create a new rule: rule name URL_Filter
When an email is received
Run action:
Edit filter rule:
Default: Accept email
Emails containing a dangerous URL should not be accepted and delivered to the user's mailbox.
Please note the settings of the URL filter.
notempty
Securepoint recommends that these mails be quarantined. Here we recommend
|
The current threat situation makes it clear that standard procedures can no longer keep up in the fight against malware. Documents are identified by MIME types and file extensions. | |
Filter rule »Word documents based on MIME types«Word_MIME |
Create a new rule: rule name Word_Mime
When an email is received
Run action:
Edit filter rule: 30 minutes
Default: Accept email
In order for Word documents to be filtered based on MIME types, a new rule is needed.
Here we recommend
|
Filter rule »Excel documents based on MIME types«Excel_MIME |
Create a new rule: rule name Excel_Mime
When an email is received
Run action:
Edit filter rule: 30 minutes
Default: Accept email
In order for Excel documents to be filtered based on MIME types, a new rule is needed.
notempty
Securepoint recommends that mails with Office documents attached are temporarily quarantined and filtered again after 30 minutes! Here we recommend
|
Filter rule »Open Office / Libre Office documents based on MIME types«OOffice_MIME |
Create a new rule: rule name OOffice_MIME (Open-Office)
When an email is received
Run action:
Edit filter rule: 30 minutes
Default: Accept email
notempty ! Securepoint recommends mails with Office documents attached are temporarily quarantined and filtered again after 30 minutes! Here we recommend
|
Filter rule »Office documents based on file extension«Office_Extension |
Create a new rule: rule name Office_Extension
When an email is received
Run action:
Edit filter rule: 30 minutes
Default: Accept email
In order for Office documents to be filtered by file extension, a new rule is needed.
notempty
Securepoint recommends that mails with Office documents attached are temporarily quarantined and filtered again after 30 minutes! Here we recommend
|
Filter rule »Compressed files based on MIME types«Compressed_MIME |
Create a new rule: rule name Compressed_MIME
When an email is received
Run action:
Edit filter rule: 30 minutes
Default: Accept email
In order for compressed files to be filtered based on MIME types, a new rule is needed.
notempty
Securepoint recommends that mails with compressed files attached are temporarily quarantined and filtered again after 30 minutes! Here we recommend
|
Filter rule »Compressed files based on extension«Compressed_Extension |
Create a new rule: rule name Compressed_Extension
When an email is received
Run action:
Edit filter rule: 30 minutes
Default: Accept email
In order for compressed files to be filtered based on the file extension, a new rule is needed.
notempty
Securepoint recommends that mails with compressed files attached are temporarily quarantined and filtered again after 30 minutes! Here we recommend
|
Filter rule »ISO files based on MIME type or extension«images
|
Create a new rule: rule name Images
Rules with -Connect operators When an email is received
Run action:
Edit filter rule: 30 minutes
Default: Accept email
In order for .iso and .img files to be filtered, a new rule is needed.
notempty
Securepoint recommends that mails with images attached are temporarily quarantined and filtered again after 30 minutes! Here we recommend
|
WL_mark or filter attachmentsWL_mark attachments WL_accept attachements Filter attachments |
Scenario: Attachments from specific senders are to be tagged and delivered. All other attachments should be filtered.
Create a new rule:rule name WL_mark attachments
Run action: Edit filter rule: Sender verified
Create a new rule:rule name WL_accept attachements
Run action: Edit filter rule: Since this email was flagged - i.e. a filter applied - it is displayed in the quarantine as filtered. Nevertheless, thanks to the 2nd rule, it will be delivered.
Create a new rule:rule name Filter attachments
Run action: Edit filter rule: 30 minutes |
Create whitelist exception rulesWhitelist updated
|
If emails from a certain sender (here from securepoint.de) are to be delivered in any case, a whiltelist exception must be created in the mail filter rule set. Create a new rule:rule name Whitelist
from Run action: Edit filter rule:
For a rule to work as a whitelist rule, the order must be defined so that this rule takes effect before the general spam quarantine rule. |
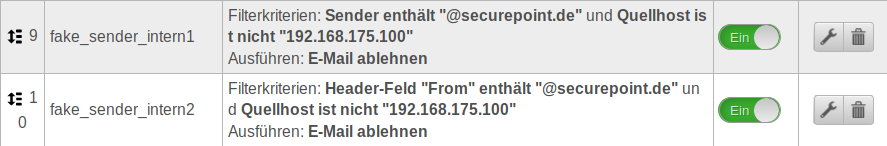
Fake senderfake_sender_internal |
In order to avoid accepting emails with fake internal senders (which usually enjoy a high level of trust), we recommend creating three filter rules according to the following example: notempty In this example, mails of the mail domain @securepoint.de are to be accepted. The IP address of the mail server is assumed to be 192.168.175.100. notempty These are only sample addresses that need to be customized locally.
Create a new rule:rule name fake_sender_internal1
Run action: Edit filter rule:
Create a new rule:rule name fake_sender_internal2
From
Run action: Edit filter rule:
Create a new rule:rule name fake_sender_internal3
From
Run action: Edit filter rule: |
Filter rule SPF failSPF fail New in the wiki
|
Create a new rule:Regelname SPF fail
» ✕anyideas.de Run action: Edit filter rule: |
Filter rule SPF permerrorSPF permerror New in the wiki
|
Create a new rule:Regelname SPF permerror
» ✕anyideas.de Run action: Edit filter rule: SPF error / check sender! |
Filter rule DKIMDKIM New in the wiki
|
Create a new rule:Regelname DKIM
» ✕anyideas.de Run action: Edit filter rule: |
Filter rule DMARC quarantineDMARC quarantine New in the wiki
|
Create a new rule:Regelname DMARC quarantine
Run action: Edit filter rule: |
Filter rule DMARC rejectDMARC reject New in the wiki
|
Create a new rule:Regelname DMARC reject
Run action: Edit filter rule: |
URL filter
Tab URL filter
The URL filter verifies
- the URL itself. Further notes in the wiki about the Mailfilter.
This can be used in combination with the allow action to create mainly whitelists - in which content category the visited page falls.
This categorization is constantly updated by our content filter team.
Allowlist entries (e.g. Education (schools and training institutes, universities) can also be created here with the allow action, or blocklist entries with the action.
The following categories are preconfigured in installations since 11.8 and should not be missed in older installations:
| Type | Name | Description | Action |
|---|---|---|---|
| Category | This category contains URLs currently classified as malicious which spread malware and contain phishing pages (phishing, malware, botnets, crime ware, etc.) | block | |
| Category | This category contains URLs that provide pornographic or predominantly sexual content. | block | |
| Category | This category contains URLs that provide advice on hacking, warez, building malware, tricking systems or subscription traps. | block | |
| Category | Server and services for important software updates This category is intended for whitelist environments. |
allow |
By clicking on the filter rule will be added.
Spam Report
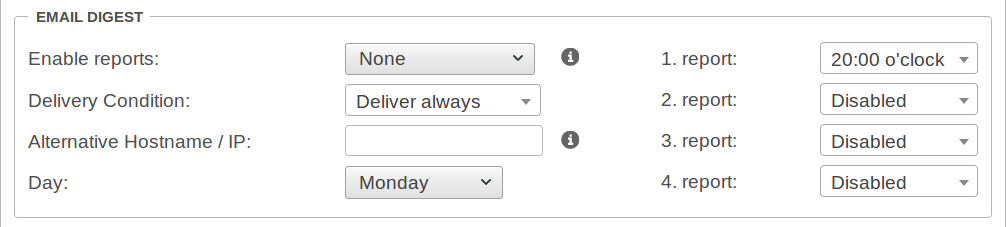
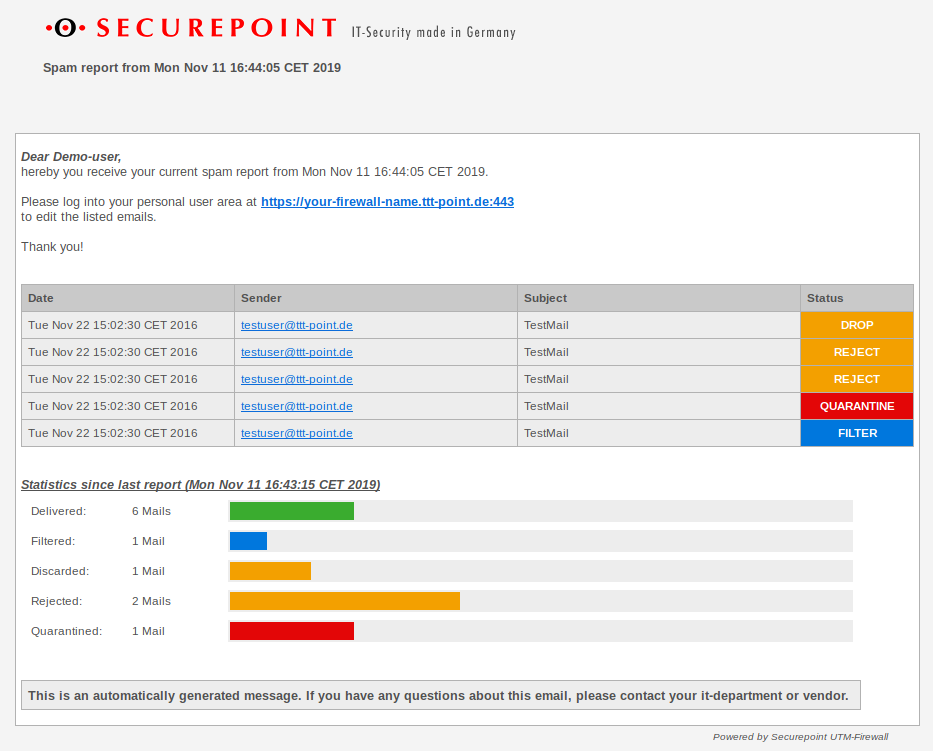
Tab Settings sectionThe spam report can inform email users at certain intervals about emails filtered, blocked or quarantined by the UTM. This report can be sent either on a specific day of the week or daily, at a specific time.
| Action | Value | Description |
|---|---|---|
| Enable reports: | (Default) | No spam reports will be sent. |
| Reports are sent to the users. | ||
| Reports are sent to the users and an overview is sent to the administrator. | ||
| Delivery Condition: | Deliver always (Default) | In any case, a spam report will be sent. |
| Not accepted | Quarantined or filtered | |
| Quarantined or filtered | A spam report will only be delivered if at least one email has been quarantined or filtered. | |
| Alternative Hostname / IP: | If the web interface with the mail server is to be accessed via an external IP or another host name. | |
| Day: | (Default) | This report can be sent either on a specific or . |
| 1. Report | 20:00 o'clock | Specifies the time for sending the report. |
| 2.Report 3.Report 4.Report |
Disabled | With every day reports, a total of four reports can be sent at specified times. |
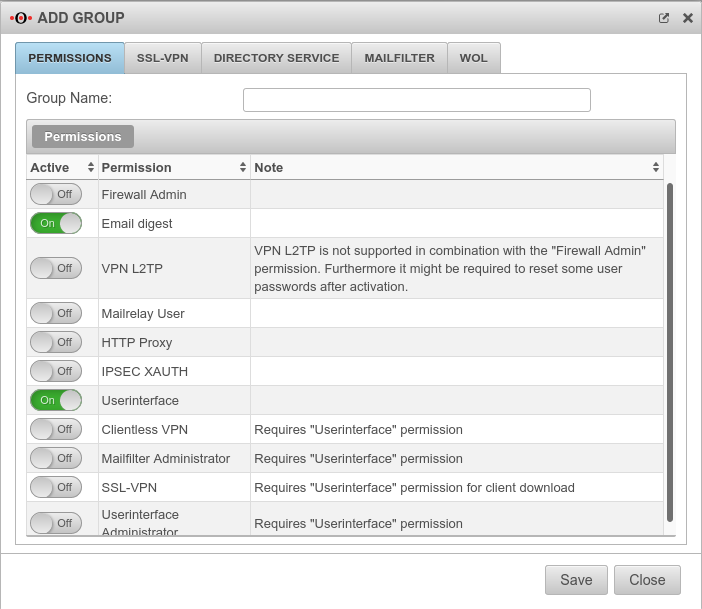
In order for the report to reach the e-mail user, it is necessary for the e-mail user to be in a group with the 'Spamreport permission.
If several mail addresses for a user are stored in an AD, the entry configured there as Primary SMTP address is used as the default address.
The setting for this is made in the menu
Groups or Edit under Permissions:
The following sections must be activated here:
- Email digest
- On activates the creation of the spam report
- Userinterface
- On The email address can be taken from a directory server such as ActiveDirectory or LDAP if the UTM is connected to it. Otherwise, the user must be created with his email address on the UTM.
The email address can be taken from a directory server such as ActiveDirectory or LDAP if the UTM is connected to it. Otherwise, the user must be created with his email address on the UTM.
In the Mailfilter tab, further settings must be made, including the e-mail address to which reports are sent:
| Email address | ||
| Caption | Default | Description |
|---|---|---|
| support@ttt-point.de | Email accounts that can be viewed by members of this group to control the mail filter. Delete with | |
| Email address | Adding a mail address to the list | |
| Allow downloads of following attachments: | (Default) | Members of this group can download attachments from mails in the user interface that meet certain criteria. |
| Allow forwarding of following emails: | (Default) | Members of this group can forward emails in the user interface that meet certain criteria |
| Report email address: | Email address to which a spam report is sent. If no entry is made here, the spam report is sent to the first email address in the list. If several mail addresses for a user are stored in an AD, the entry configured there as Primary SMTP address is used as the default address..
| |
| Report language: | Default under → Firewall → language of reportsIt can be specifically selected: or |
Spam report to the user.
Disclaimer and hints
This website was compiled with the greatest possible care. Nevertheless, no guarantee can be given for the correctness and accuracy of the information provided. Any liability for damages arising directly or indirectly from the use of this website is excluded. If this website refers to websites operated by third parties, Securepoint GmbH is not responsible for any content linked or referred from this site.
The following wiki articles may be helpful for setup.