- Updated to Redesign of the webinterface
- These instruction describes how to establish the use of the Outlook Web App via a browser with the reverse proxy.
- This is no instruction to enable the access with Outlook to the Exchange Server.
Prerequisite
The prerequisite for these guideline is a fully functional Exchange Server with already imported certificates, on which the Outlook on the web. Formerly known as Outlook Web App can be called up with a Port Forwarding.
Preparations
Certificate
Since Outlook on the web. Formerly known as Outlook Web Ap can only be reached via an SSL-encrypted connection, a certificate is required. There are various possibilities for this:
- A certificate from a public certification authority that is purchased.
- An ACME certificate (e.g.: Let's encrypt) → Wiki for creation and management
- A certificate created by the UTM itself
The certificate management is located in the menu .
If not already available, a CA (Certification Authority) must be created and then, based on this CA, the certificate for the domain.
- Further information on creating and importing certificates can be found in the Wiki article Certificates.
If the client calls the domain owa.ttt-point.de, as in our example, the name of the certificate must also be owa.ttt-point.de.
If subdomains are available, such as web.ttt-point.de, a so-called wildcard certificate can also be created. In our example, this is *.ttt-point.de.
Packet filter rule
- The OWA of the Exchange Server is to be accessed exclusively via the proxy of the UTM.
- Therefore, only access to the network object external interface, which provides the proxy, may be permitted for https connections from the Internet.
- There must be no port forwarding to this Exchange server.
User Webinterface Port
IIS Settings
Configuration
The settings for the reverse proxy are located in the menu
Clicking on the button opens the wizard.
Wizard
| Caption | Value | Description | |
|---|---|---|---|
Step 1 - Internal | |||
| Target Server: | If the host has already been created as a network object, it can be selected directly in the drop-down menu. | UTMuser@firewall.name.fqdnApplicationsReverse-Proxy 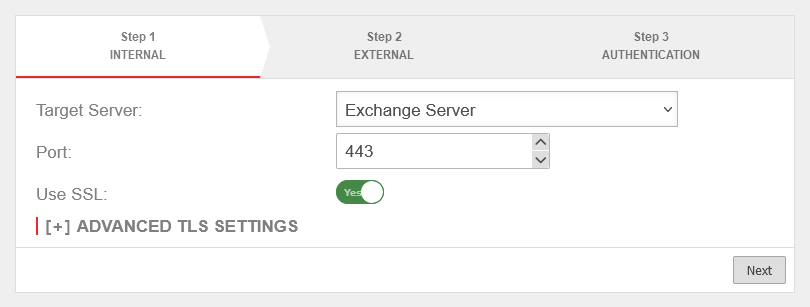 Target server already exists as a network object Target server already exists as a network object
| |
| Port | 443 | Since the OWA of the Exchange can only be accessed via an encrypted connection, port 443 is selected. | |
| Use SSL: | On | SSL must be activated. | |
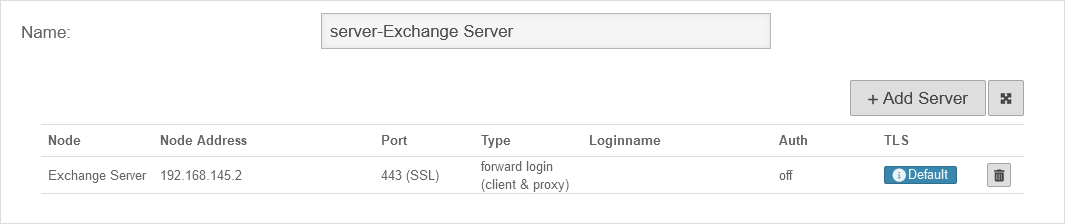
| Target Server: | If the Exchange Server does not yet exist as a network object, it can be created via the selection point in the wizard. | UTMuser@firewall.name.fqdnApplicationsReverse-Proxy 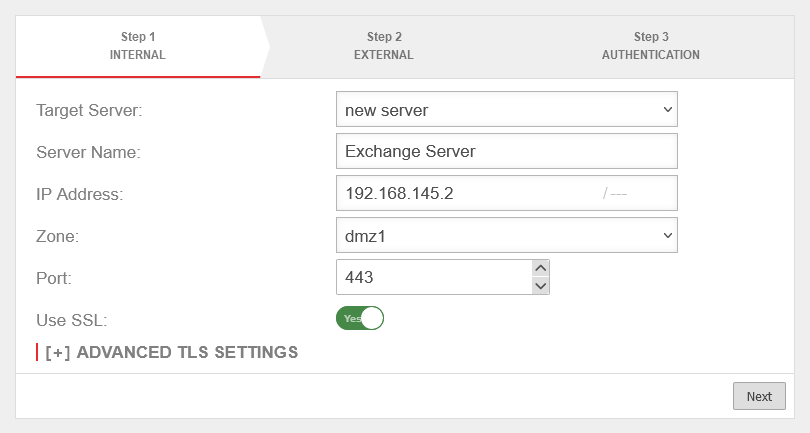 Target server does not yet exist as a network object Target server does not yet exist as a network object
| |
| Server Name: | Exchange Server | Name of the network object | |
| IP Address: | IP address of the Exchange Server | ||
| Zone: | Zone of the network object | ||
| Port | 443 | Since the OWA of the Exchange can only be accessed via an encrypted connection, port 443 is selected. | |
| Use SSL: | On | SSL must be activated. | |
Step 2 - External | |||
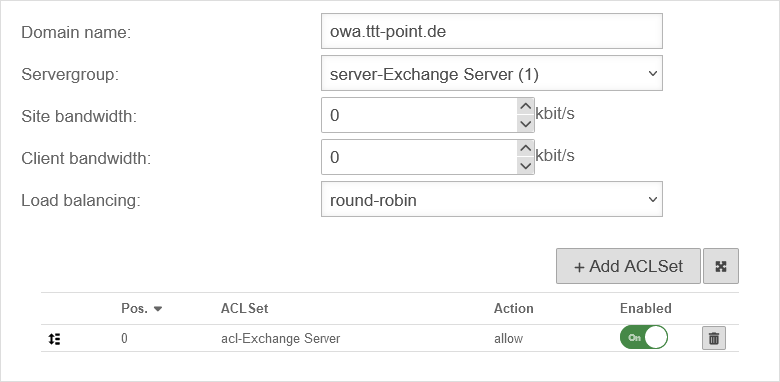
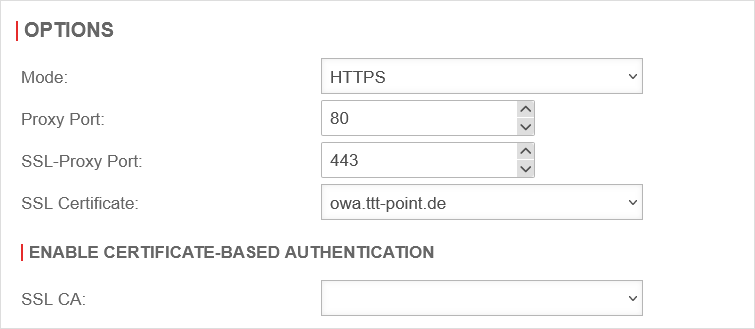
| External domain name: | owa.ttt-point.de | The mail domain (ttt-point.de) is entered with an additional subdomain (owa) through which a client may access the OWA. |
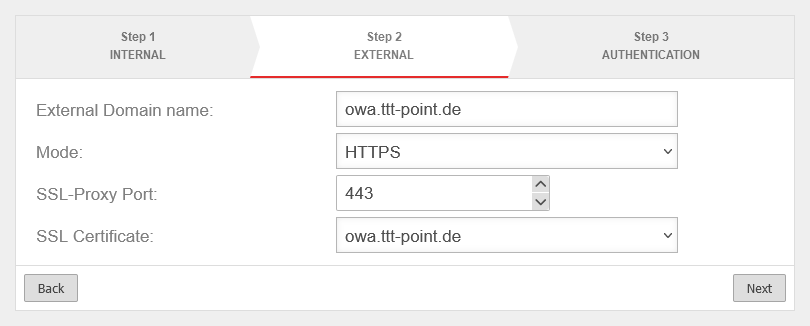 |
| Mode | Access shall be exclusively encrypted via https. | ||
| SSL-Proxy Port: | 443 | The OWA is also to be addressed directly via the usual port 443 for https. | |
| SSL certificate: | The certificate that was selected in the step Preparations is selected here. | ||
Step 3 - Authentication | |||
| Forward authentication: | The proxy passes authentication to the Exchange Server or the OWA through | 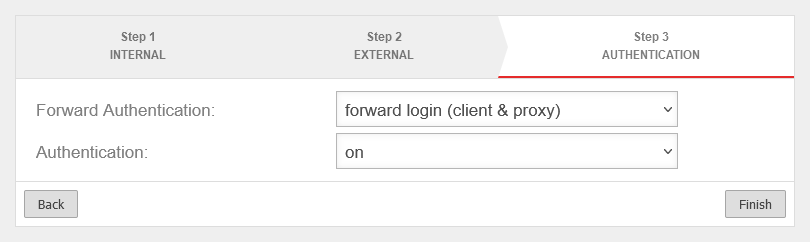 | |
| Authentication: | Authentication is required Since the reverse proxy does not forward NTLM authentication, only Basic/Standardauth must be active in the IIS settings of the Exchange Server so that the clients can reach the OWA interface of the Exchange Server.
| ||
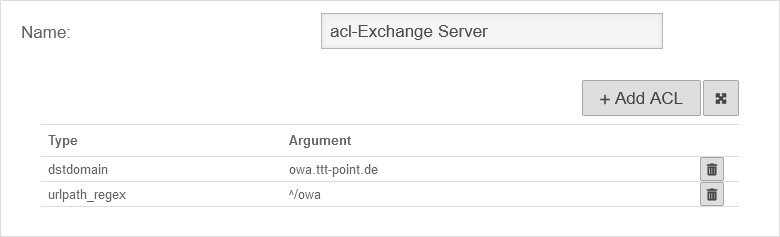
Customize ACL SetTo ensure that only the OWA interface can be accessed and not the administration web interface of the Exchange Server (Exchange Control Panel / ECP), the ACL set must be extended: |
UTMuser@firewall.name.fqdnApplicationsReverse-Proxy 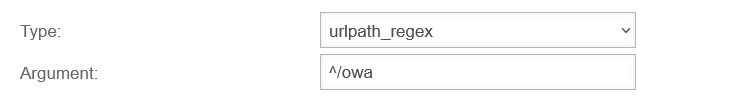 New ACL for OWA access New ACL for OWA access
| ||
| Type | Restricts the URL path | ||
| Argument: | ^/owa | Regular expressions (regex) are expected. Further paramaters in regex format are possible. However, these are not required for the Outlook Web App. If such services are required, an SSL VPN connection should be used.
| |
| Speichern und schließen | Add ACL | ||
| Speichern und schließen | ACL Set speichern | ||
Certificate-based authentication | |||
| In order to prevent unauthorised attackers from getting through to the Exchange Server (and its authentication) in the first place, Certificate-based authentication can be activated. The reverse proxy only forwards requests to the Exchange Server if a corresponding certificate is installed on the user's device. Enable certificate-based authentication: |
UTMuser@firewall.name.fqdnApplications 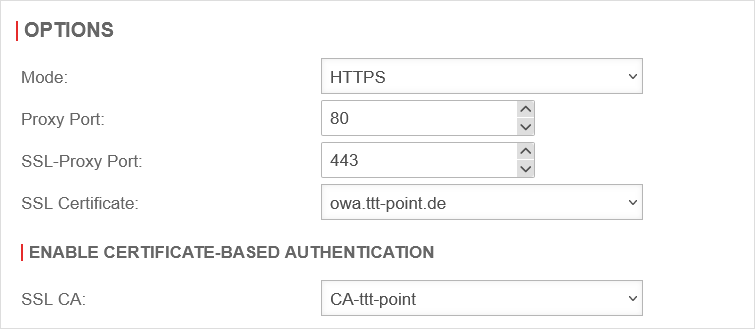 Activated certificate-based authentication Activated certificate-based authentication
| ||
| SSL-CA | A certificate signed with the CA to be selected here must be installed on the user's device for this purpose. | ||
For this purpose, we recommend access with a (SSL) VPN. | |||
Overview
The settings for this scenario must then look like this: