Configuration of a bridge in connection with eth interfaces
Last adaptation to the version: 12.6.0
New:
- Updated to Redesign of the webinterface
Introduction
A bridge (network bridge) connects two physical networks to a common one.
The interfaces connected in this way have an IP and the IP addresses of the connected devices are in the same subnet.
notempty
The connection to the admin interface is lost as soon as the IP address is removed from the interface currently used to access the UTM.
If all available internal interfaces are to be added to a bridge (e.g. A1 and A2 for a Black Dwarf), external access to the firewall must be via A0.
Port forwarding from an internal network via an external IP address is not possible via a bridge.
This could be remedied by setting up a forward zone in the UTM name server, provided that the UTM is set up as the name server for the internal clients. In this case, the external URL called by Internal refers directly to the internal target server.
Instructions for setting up the forward zone can be found under Forward-Zone in the Nameserver Wiki.
The interfaces connected in this way have an IP and the IP addresses of the connected devices are in the same subnet.
notempty
The firewall must not be administered via the interface that is to be added to a bridge!
The connection to the admin interface is lost as soon as the IP address is removed from the interface currently used to access the UTM.
If all available internal interfaces are to be added to a bridge (e.g. A1 and A2 for a Black Dwarf), external access to the firewall must be via A0.
Port forwarding from an internal network via an external IP address is not possible via a bridge.
This could be remedied by setting up a forward zone in the UTM name server, provided that the UTM is set up as the name server for the internal clients. In this case, the external URL called by Internal refers directly to the internal target server.
Instructions for setting up the forward zone can be found under Forward-Zone in the Nameserver Wiki.
Prepare administration access
- Identify an interface on the firewall that should not be bridged.
- In the menu Area Network interfaces IP Addresses note down or assign existing IP address of this interface (e.g. 10.0.10.1/24 or 10.10.10.193/29).
- Find a free IP address from the corresponding network.
- Add this IP address or the entire associated network (e.g. 10.0.10.0/24 or 10.10.10.192/29) in the menu Area Administration and authorize it for administration.
- Establish access on the selected interface via this IP address or this network (e.g.: 10.0.10.1:11115 or 10.10.10.193:11115).
Prepare interfaces
UTMuser@firewall.name.fqdnNetworkNetwork configuration 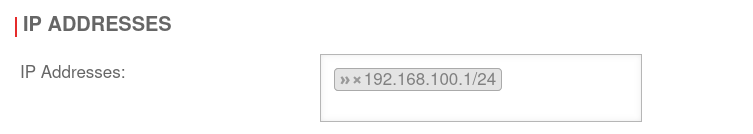 Removing IP address
Removing IP address
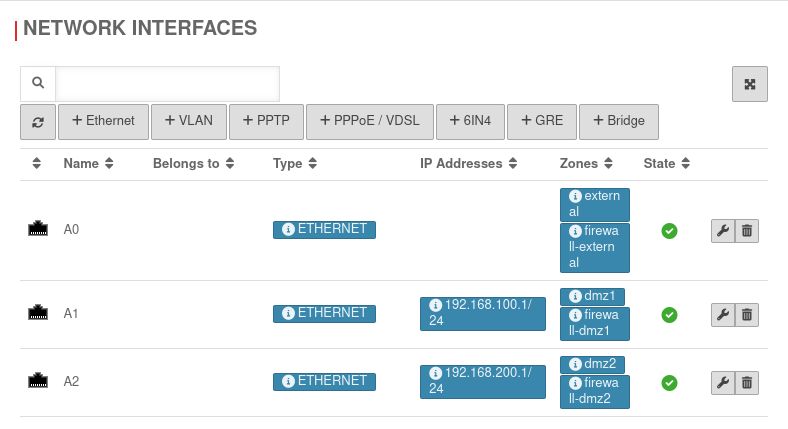
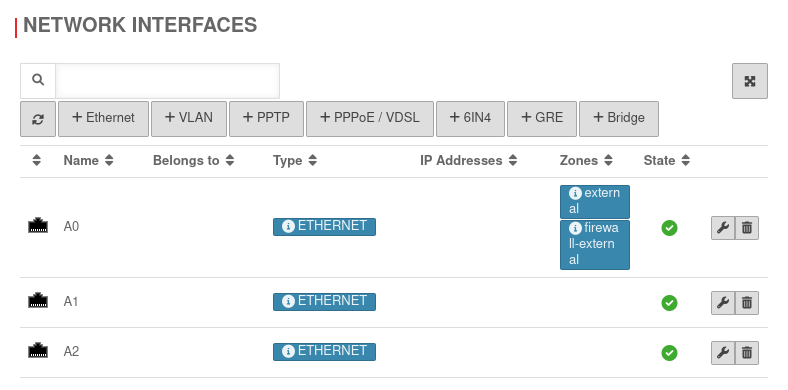
Menu → in the corresponding interface → Tab IP Addresses.
Remove IP addresses. In the example » ✕192.168.100.1/24 by clicking on
Under no circumstances may the IP address be removed which is used for the current access!
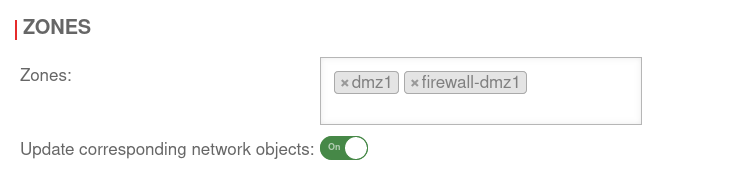
Menu → in the corresponding interface → Tab Zones.
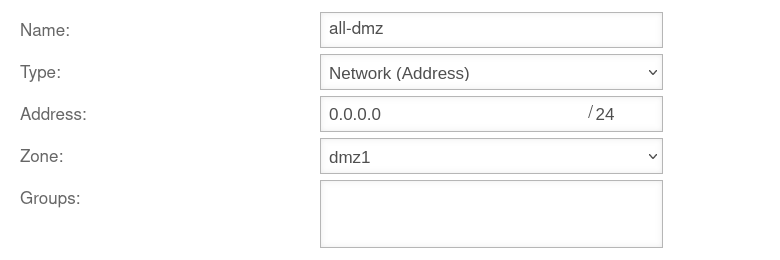
Remove the zones by clicking on . In the example » ✕dmz1 » ✕firewall-dmz1.
Then Save.
Under no circumstances may the zone be removed which is used for the current access!
Create a Bridge
In the example, the interfaces A1 and A2 are to be combined to a DMZ.
Start the wizard in the menu Area Network interfaces Button .
Step 1Step 1
| |||
| Caption | Value | Description | UTMuser@firewall.name.fqdnNetworkNetwork configuration 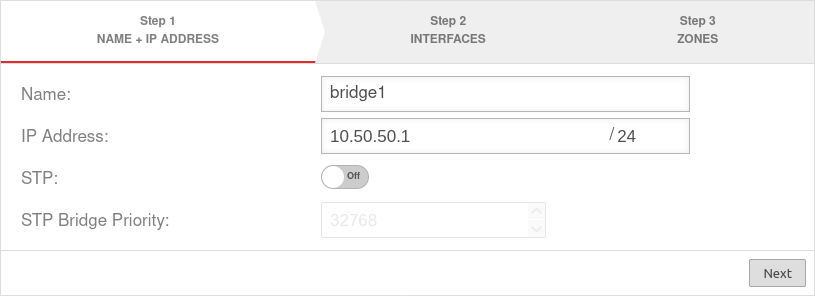 Assistant step 1 Assistant step 1
|
|---|---|---|---|
| Name: | bridge0 | Name of the bridge interface | |
| IP address: | 10.50.50.1/24 | Example-IP address of the bridge interface | |
| STP: | Off | In addition, the Spanning Tree Protocol can be activated. The Spanning Tree Protocol prevents parallel connections in networks with multiple switches and thus avoids unwanted circular packets | |
| STP Bridge Priority: | 32768 | ||
| Next step | |||
Step 2Step 2
| |||
| Interfaces: | » ✕A1 » ✕A2 | Interfaces that are to be combined. Available interfaces can be selected in the click box. | 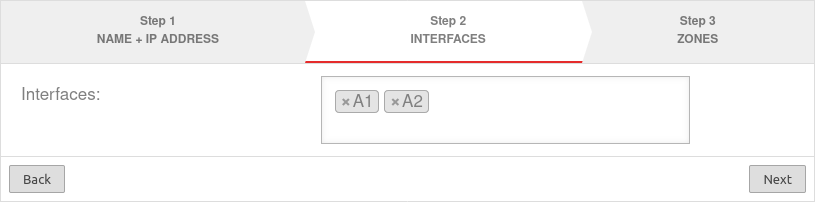 |
| Next step | |||
Step 3Step 3
| |||
| Zones: | » ✕dmz1 » ✕firewall-dmz1 | Zones that are to be linked with the bridge interface. In our example dmz1 and firewall-dmz1. |
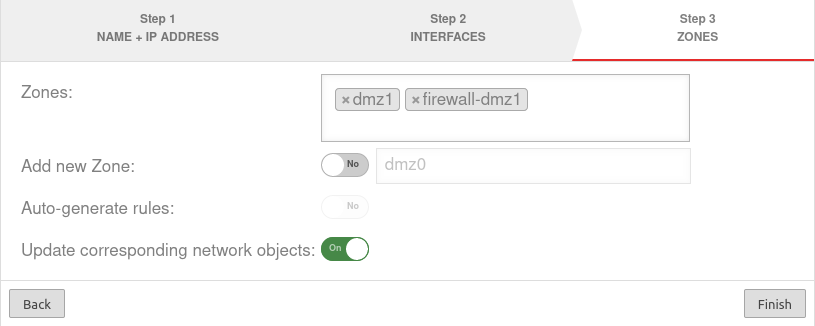 |
| Add new zone: | Off dmz2 | If activated, a new zone can be added to the bridge alternatively or additionally. | |
| Generate Rules: | Off | Packetfilter rules are automatically created for the new zone. These rules first allow any network traffic of the bridge to the internet (any rules) and must be replaced unconditionally by customized rules!
| |
| Update associated network objects: | On | If activated, all network objects whose zone is assigned to another interface and which have specified an interface as the target are now assigned the new bridge as the target. | |
| Completes the bridge setup. | |||
| Configured bridge | UTMuser@firewall.name.fqdnNetwork 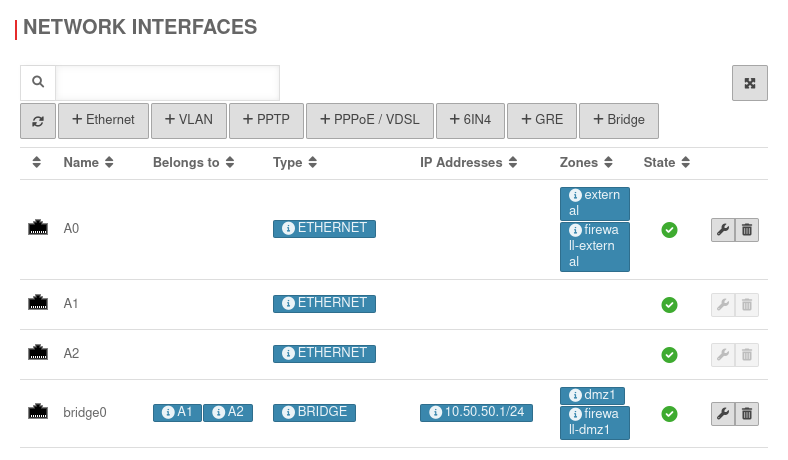 Configured bridge Configured bridge
| ||
Set up packetfilter rule
A packetfilter rule is required to allow network traffic between the interfaces belonging to the bridge.
A new network object is created for this purpose.
UTMuser@firewall.name.fqdnFirewallPacketfilter 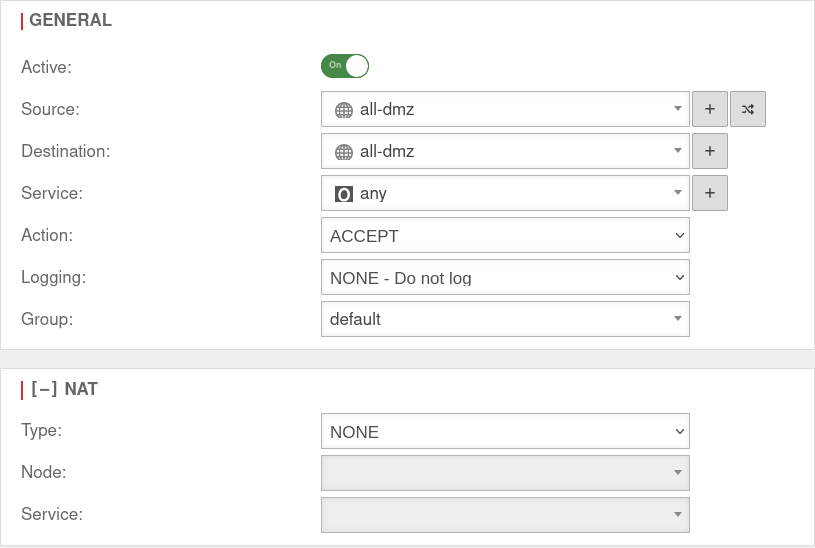 Packetfilter rule for the bridge
Packetfilter rule for the bridge
Finally, only the packetfilter rule with the network object just created has to be created.
At this point a any-rule may actually be used so that the interfaces can communicate completely with each other.
| # | Source | Destination | Service | NAT | Action | Active | |||
| 4 | Accept | On |
Network traffic to other networks (internal or external) should then be restricted by rules that work with the network objects that are mapped to the bridge zone.
Example rule to release only ftp services from the DMZ
| # | Source | Destination | Service | NAT | Action | Active | |||
| 4 | HNE | Accept | On |
The bridge setup is completed with .