- Updated to Redesign of the webinterface
Initial situation
Many service providers require their own VPN router for connecting to their own server landscape, which establishes a secure connection to it and through which the connections are routed.
There are various approaches for implementation in the customer network. This article discusses the problems of such an implementation and gives a suggestion for optimal integration in customer networks.
Routing issues
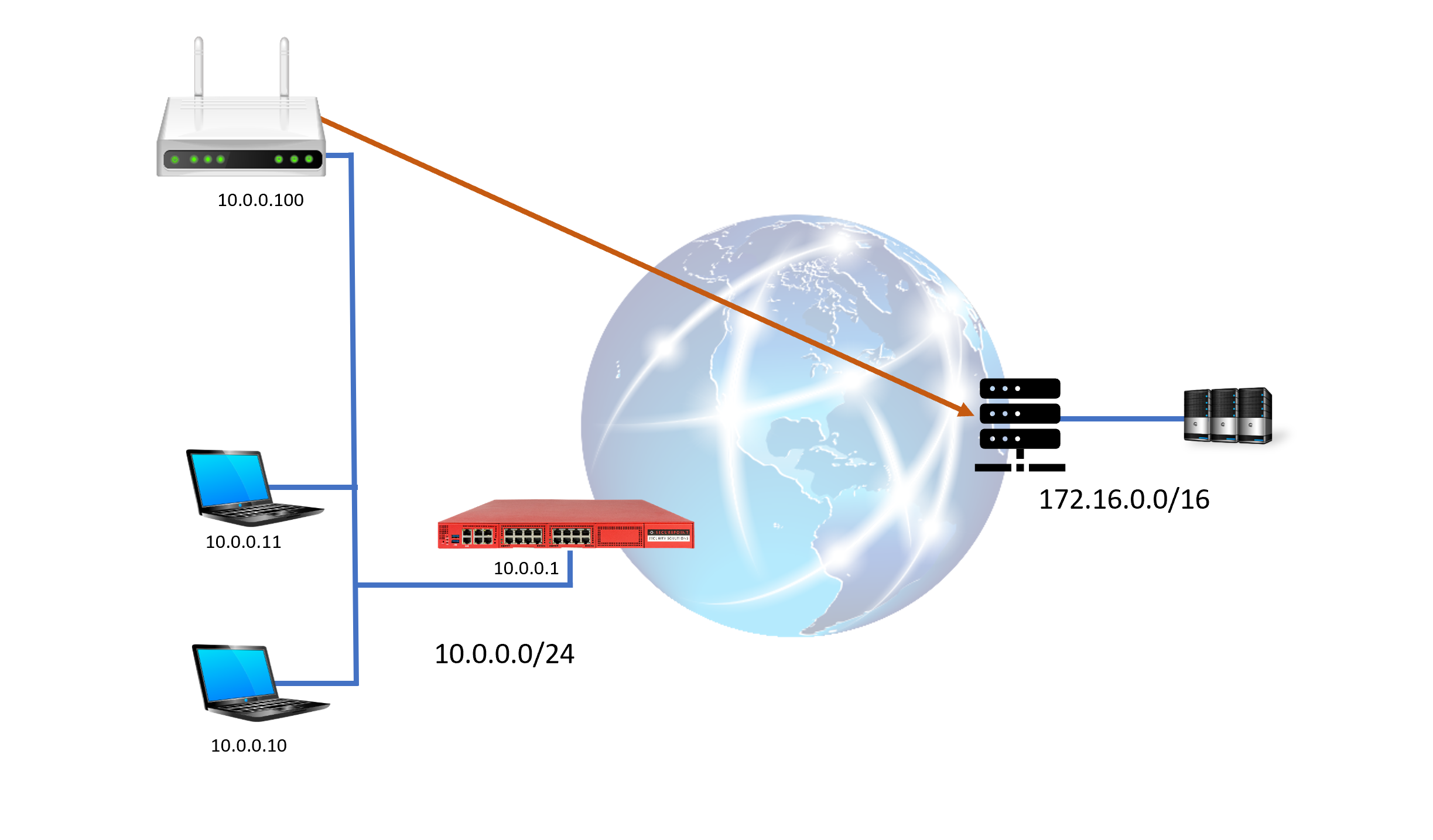
If the router is simply included in the internal network, then initially a routing problem arises:
Connections to the third-party network must go through this router. Local routing on the network devices is not an option. Routing via the firewall is also problematic.
When establishing a TCP connection, this results in asynchronous routing:
If such a connection is initiated by a device, the SYN packet of the TCP three-way handshake is first routed to the UTM and then via the third-party router. The SYN/ACK packet of the responder from the third-party network, on the other hand, is delivered by the router directly to the initiator and not via the UTM. The third packet of the three-way handshake (ACK) goes via the UTM again and is discarded there by the packet filter due to an implausible status (stateful inspection).
Zero trust issue
Even if the routing problems described above could be solved or circumvented, the connections to the third-party network are beyond the control of the UTM (virus scanner, web filter, port filter, ...), which is not acceptable in an untrusted network. Therefore, integration into existing customer networks should not be considered.
Solutions
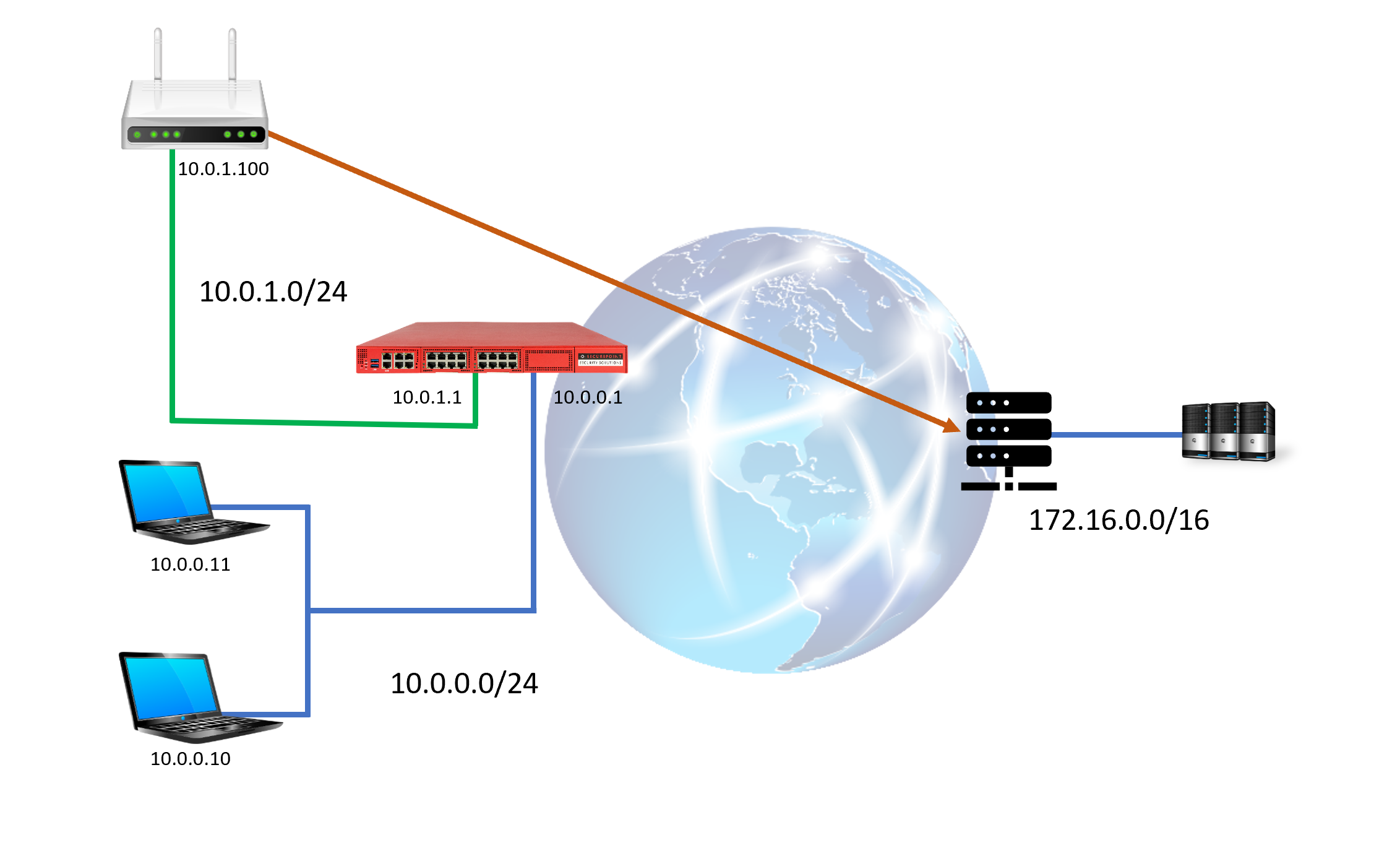
All the problems described can be solved by placing the router in a separate subnet at the UTM and establishing a transfer network. In principle, this is possible with any UTM appliance from Securepoint. All that is needed is another free Ethernet interface or VLAN interface.
Approach
- Prerequisites:
- Specify an internal network 10.0.0.0/24 on LAN2.
- There is another interface available on the UTM that has not been used yet (LAN3)
- Objective:
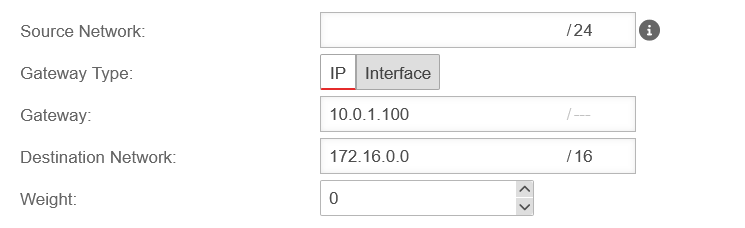
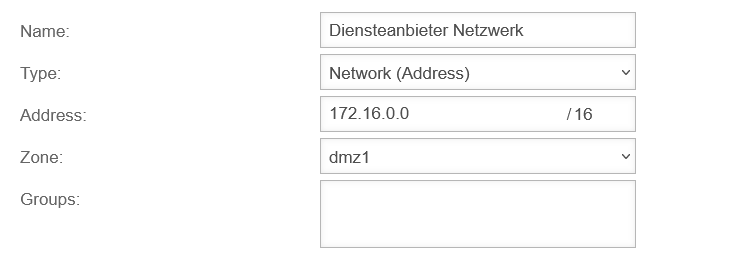
- A service provider's router is to be used to connect to a private subnet 172.16.0.0/16
- Approach:
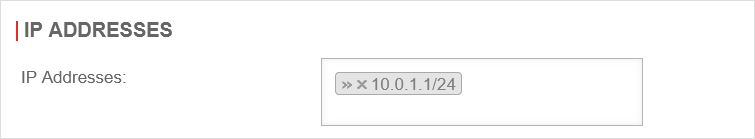
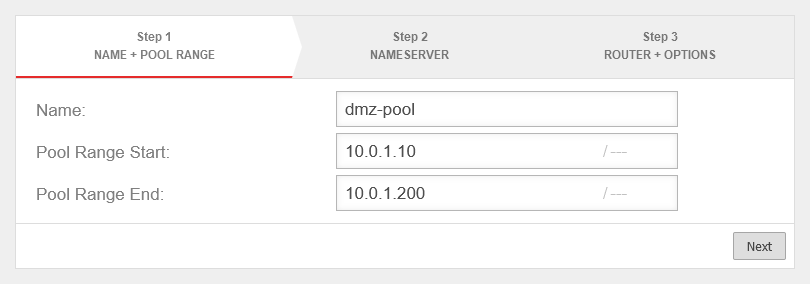
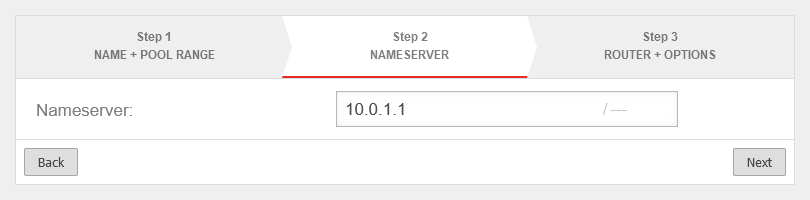
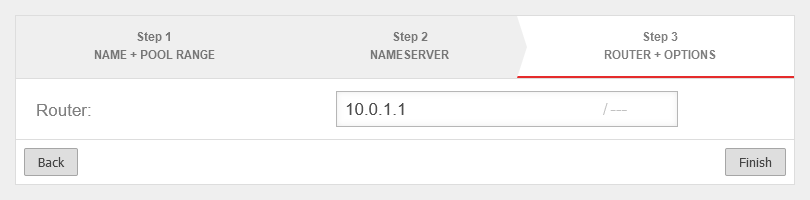
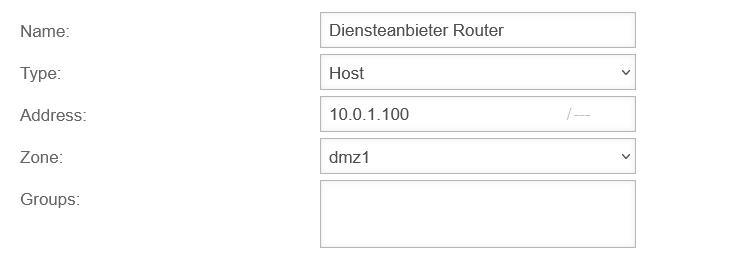
- The unused interface (LAN3) should get the subnet 10.0.1.0/24 with the IP 10.0.1.1
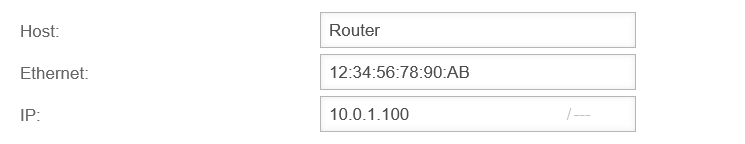
- The router of the service provider receives the IP 10.0.1.100
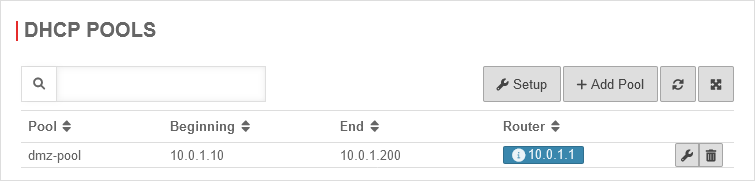
- To simplify the integration of the router, the UTM should serve as a DHCP server in this subnet.
For this purpose, a fixed lease is to be configured for the router interface with the IP 10.0.1.100
Network configuration
Port filter rules
The required port filter rules depend on which VPN method the router uses and which services are required within the secured connection.
Assumptions for this example:
- The connection is established via IPSec
- In the service provider's network, various terminal servers are to be reached via the RDP protocol
Summary
By integrating the service provider router into the DMZ, all of the routing issues described above were eliminated while maintaining control over all connections into and out of its own network.