Configuration in Azure AD to be able to access its users with the UMA
Last adaptation to the version: 3.3.4 (07.2023)
New:
- Azure Cloud Update in the Setup Wizard and in the Email Accounts menu
- User authentication using Microsoft Azure enables multi-factor authentication in the DMS
- Client secret ID from Azure AD required (v3.2)
Requirements
- Users in Azure AD with mail addresses to be archived
Azure AD configuration
The following steps are necessary:
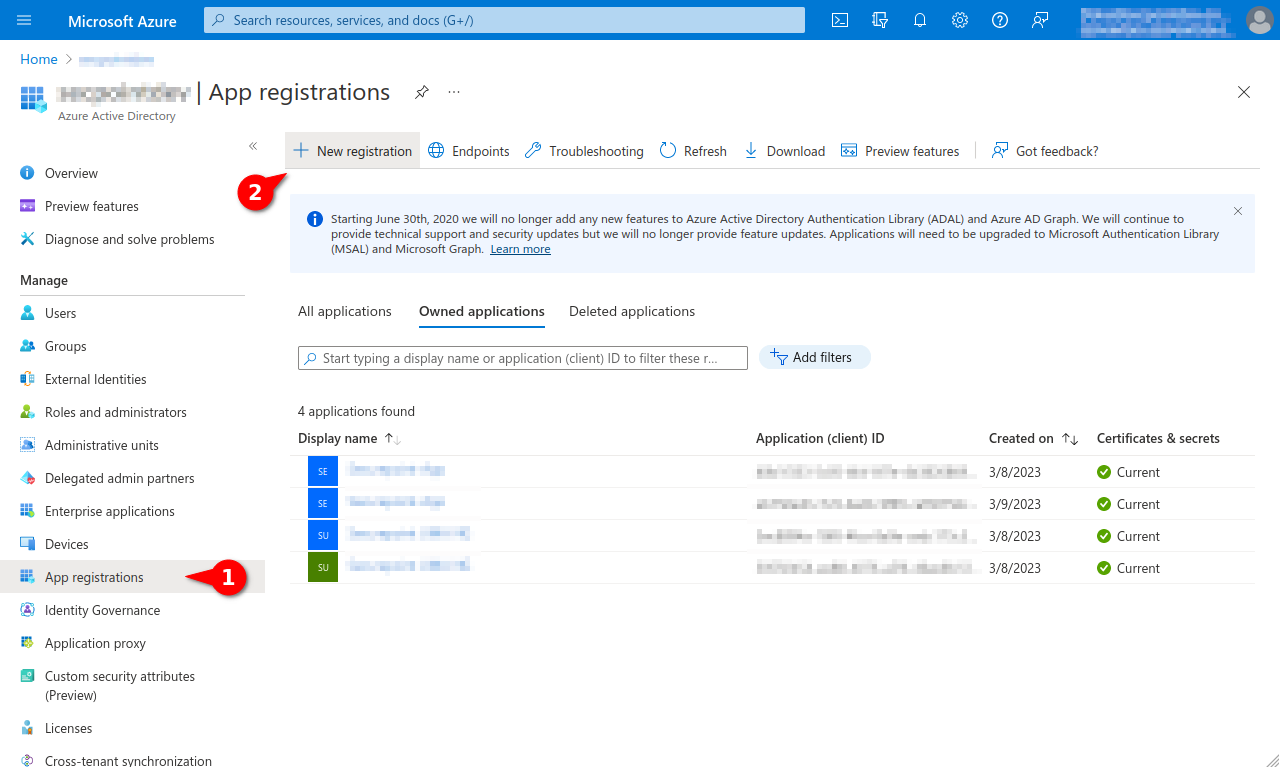
- In Azure AD, the Securepoint UMA NG must be registered as a new app
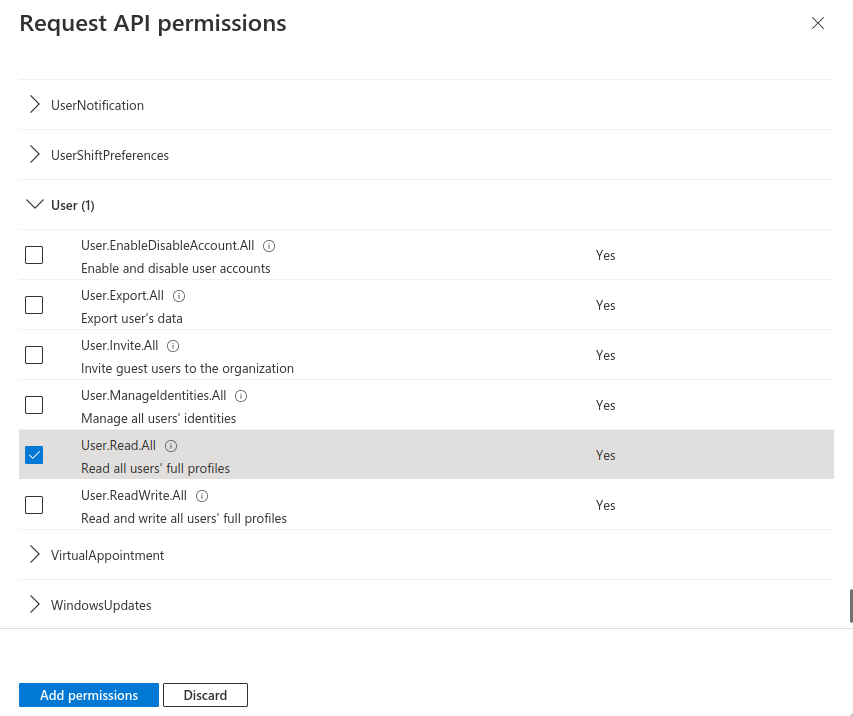
- The following permissions are required:
- MS-Graph / Delegated Permission:
- User.Read (should already exist as default permission)
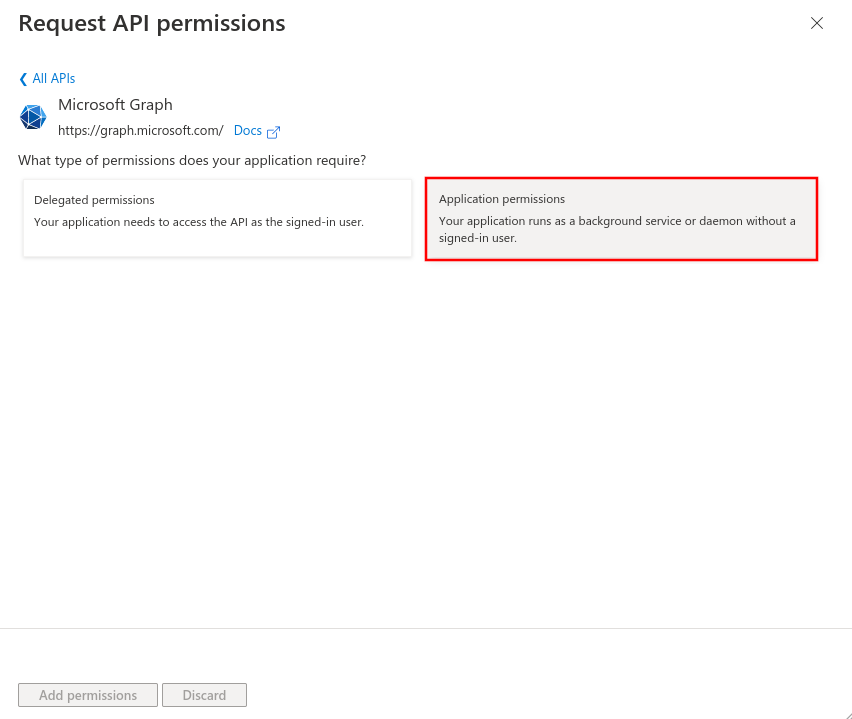
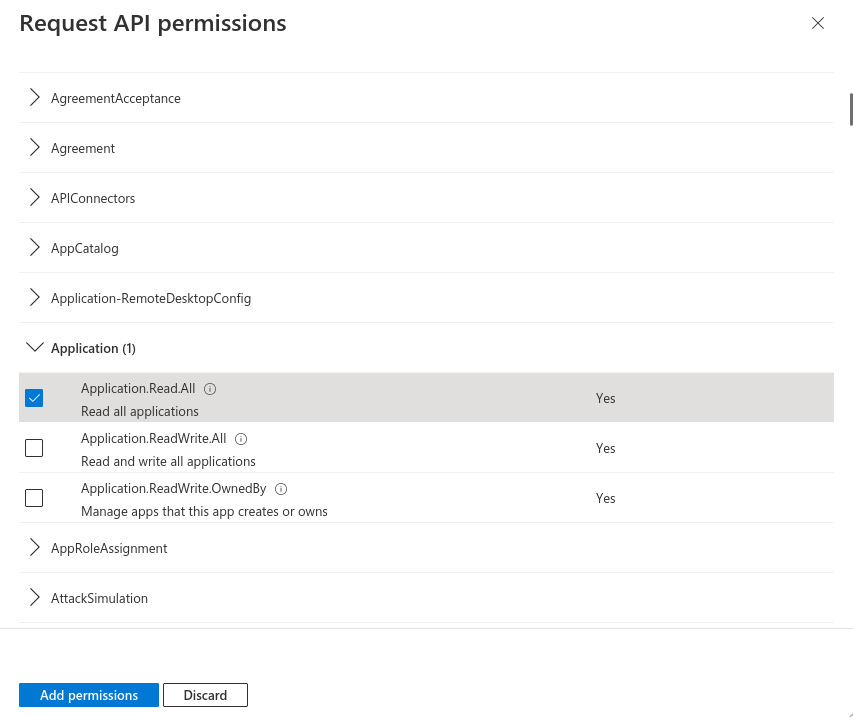
- MS-Graph / Application Permissions:
- Group.Read.All
- MailboxSettings.Read
- User.Read.All
- Application.Read.All
- MS-Graph / Delegated Permission:
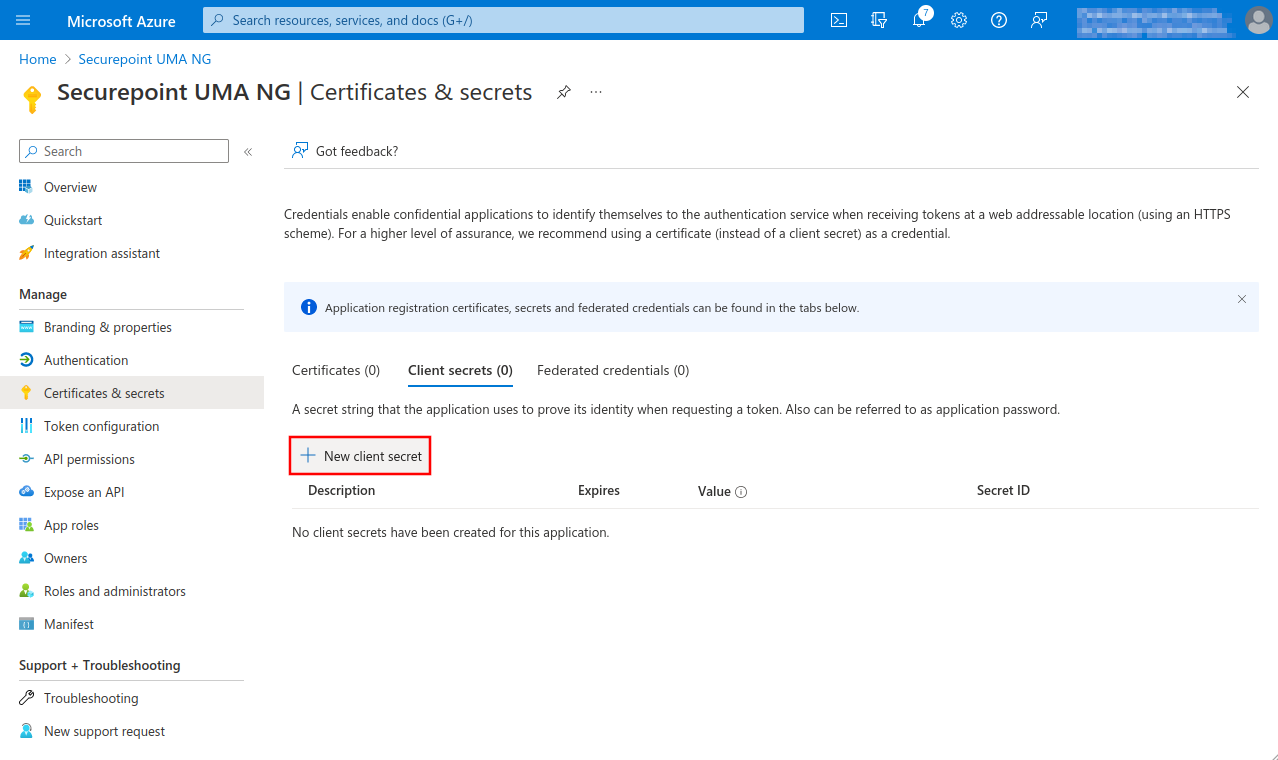
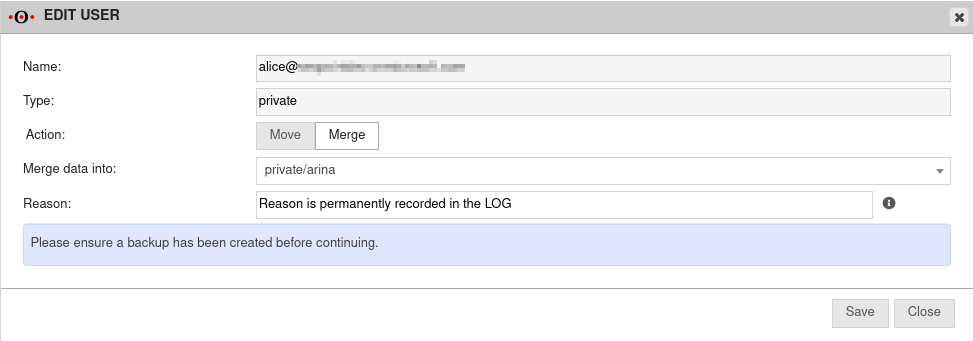
- A Secret Client Key must be added to the app
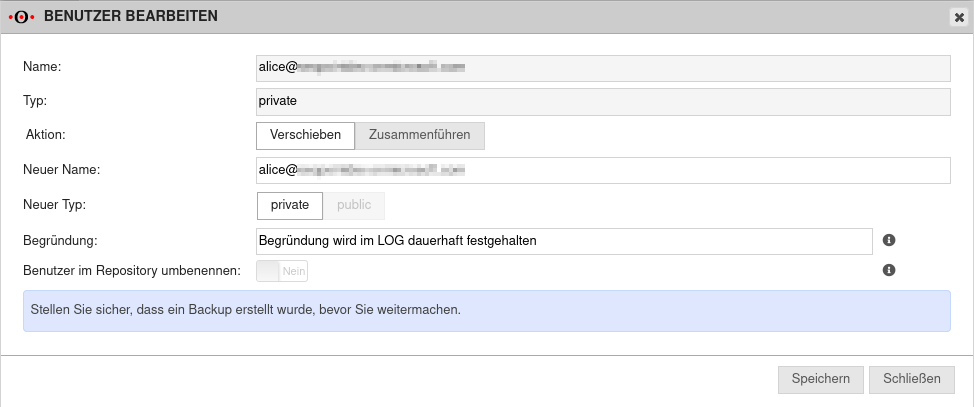
- In order to archive additional mail addresses besides the original Microsoft Azure email address, these must be stored in the user profile in the Azure Active Directory in the section Contact information as Alternative email address.
The login of the user in the Securepoint UMA NG is then done with the user principal name (user pricipal name) and the corresponding password from Azure AD.

Fig.1
- Opening the Azure Dashboard or the Microsoft 365 Portal
- Menu Azure Active Directory
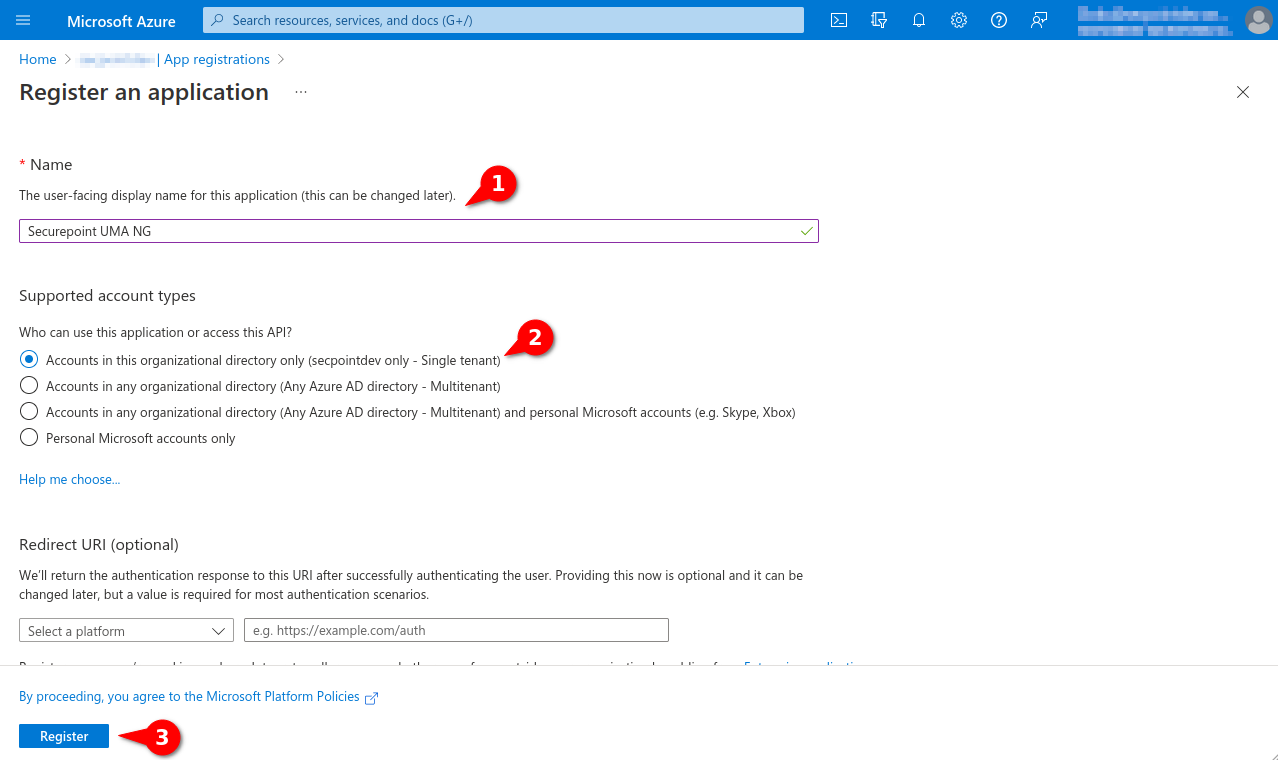
Fig.4
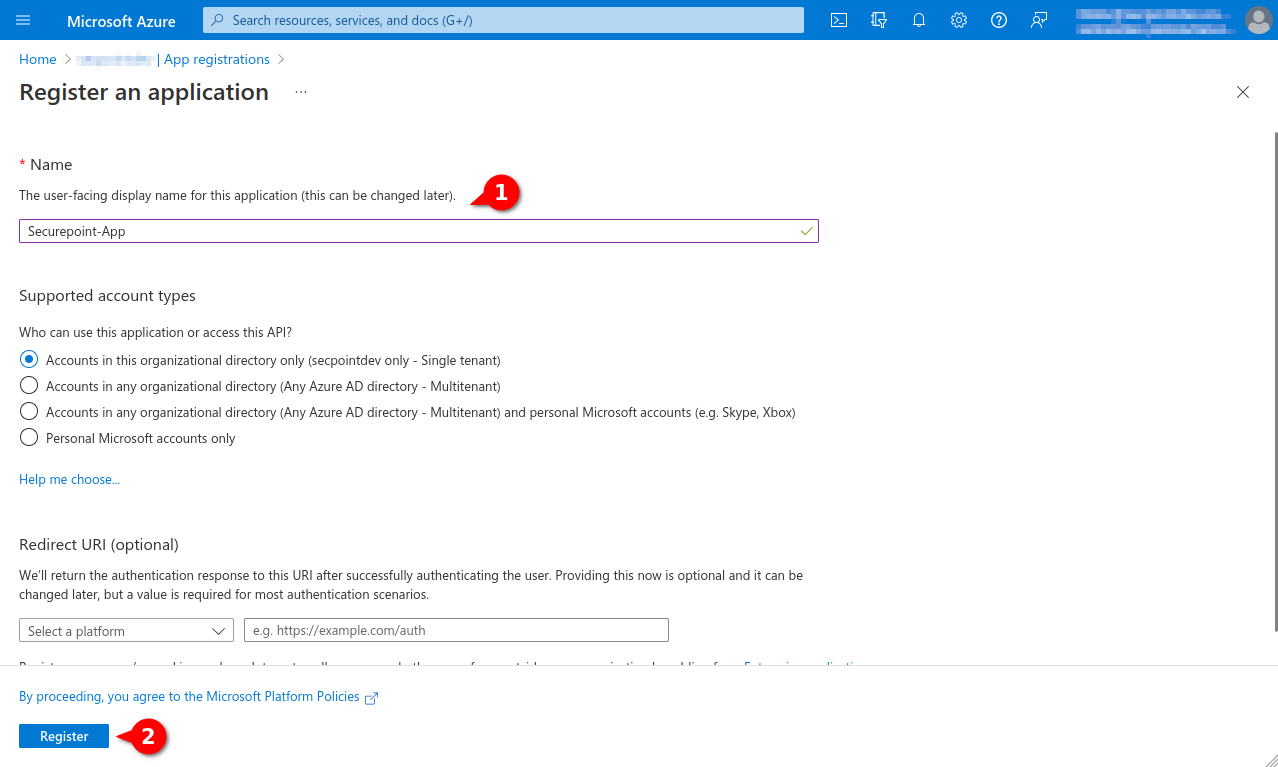
- Assigning unique name
- Option Only accounts in this organization directory (single client)
- A redirection URI is not required
- Button Register
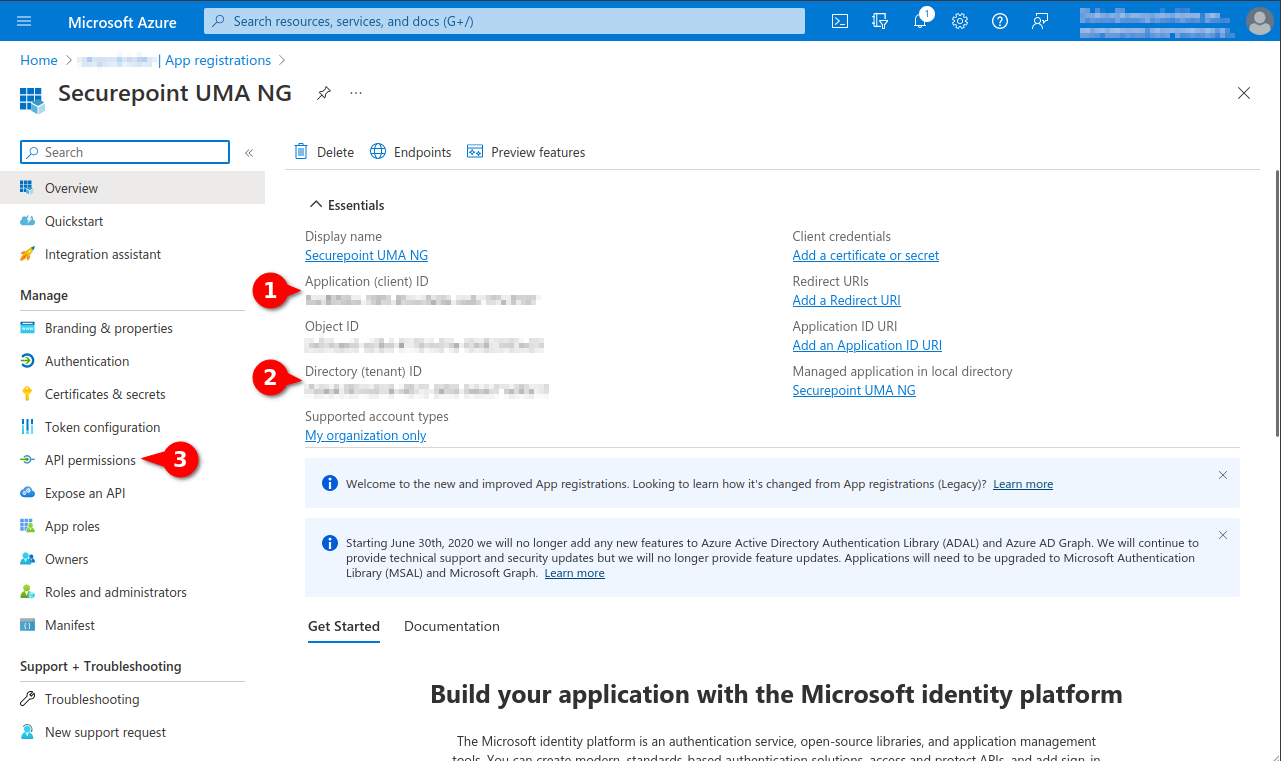
Fig.5
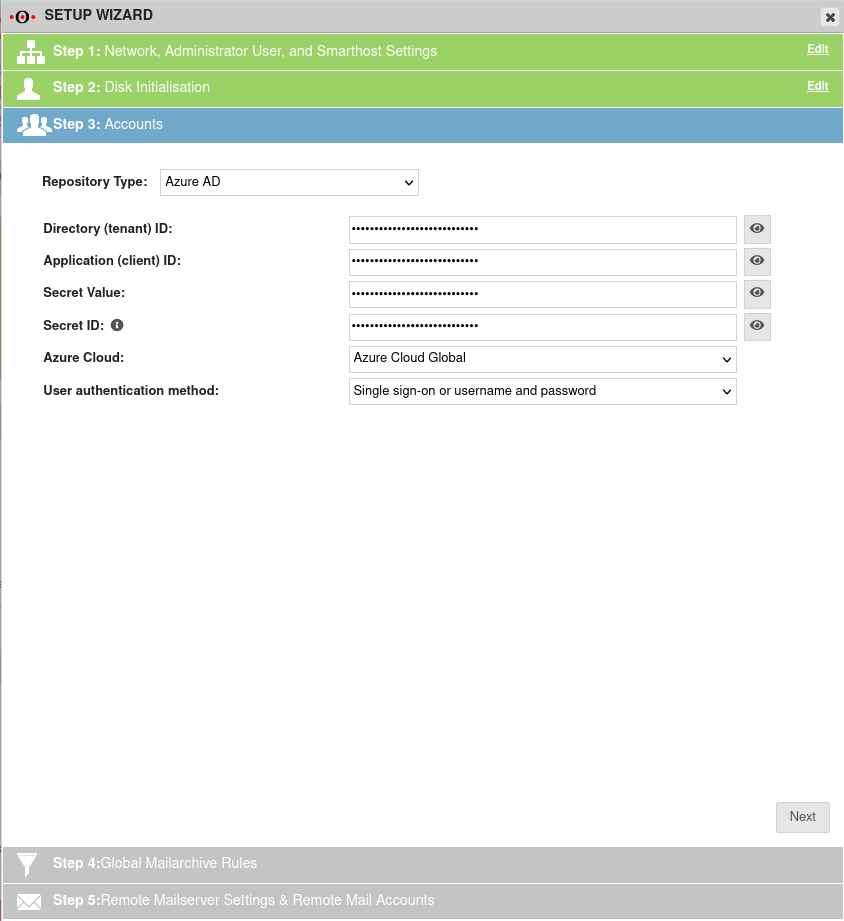
- The following values are required later in the Securepoint UMA:
- Application ID (Client ID)
- Directory ID (client)
- Client Secret ID
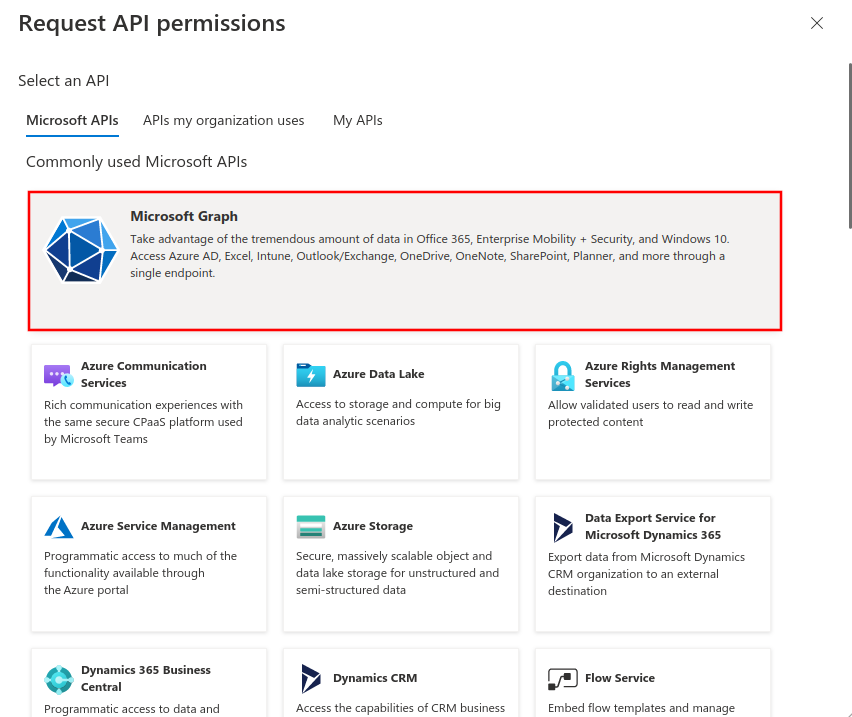
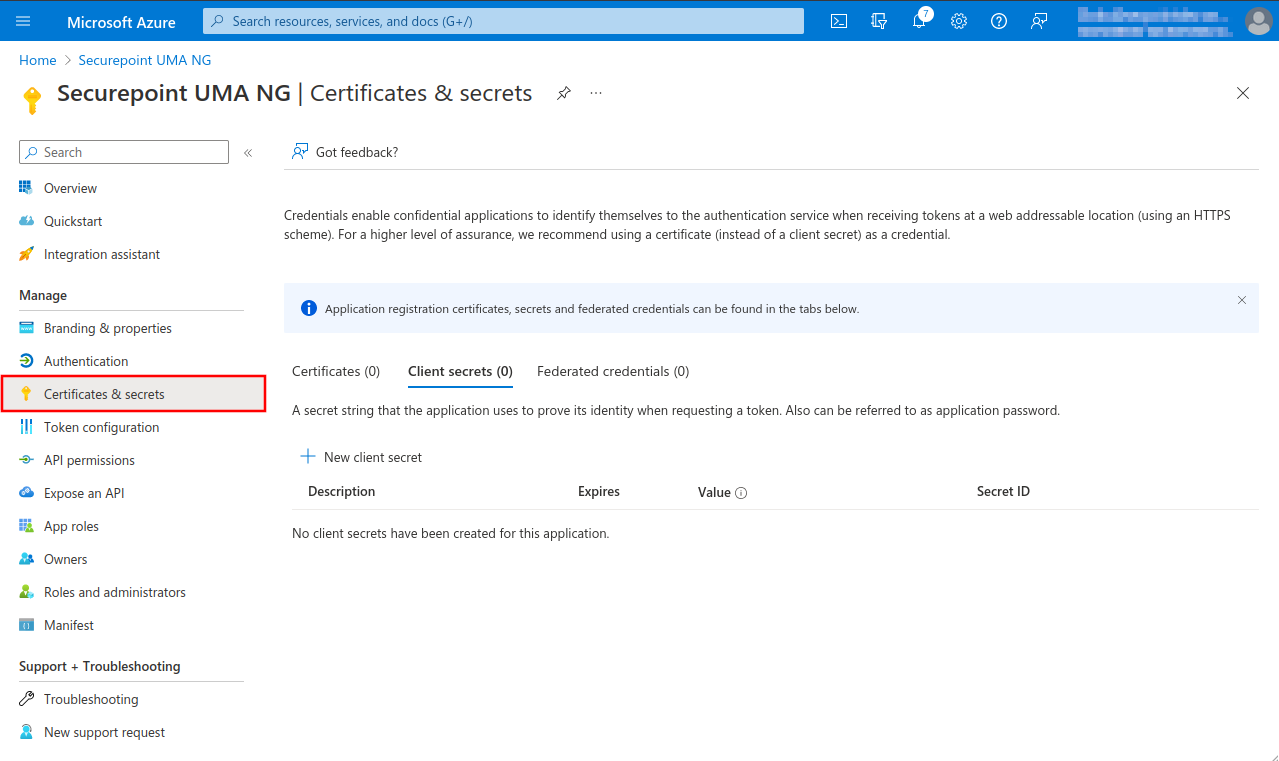
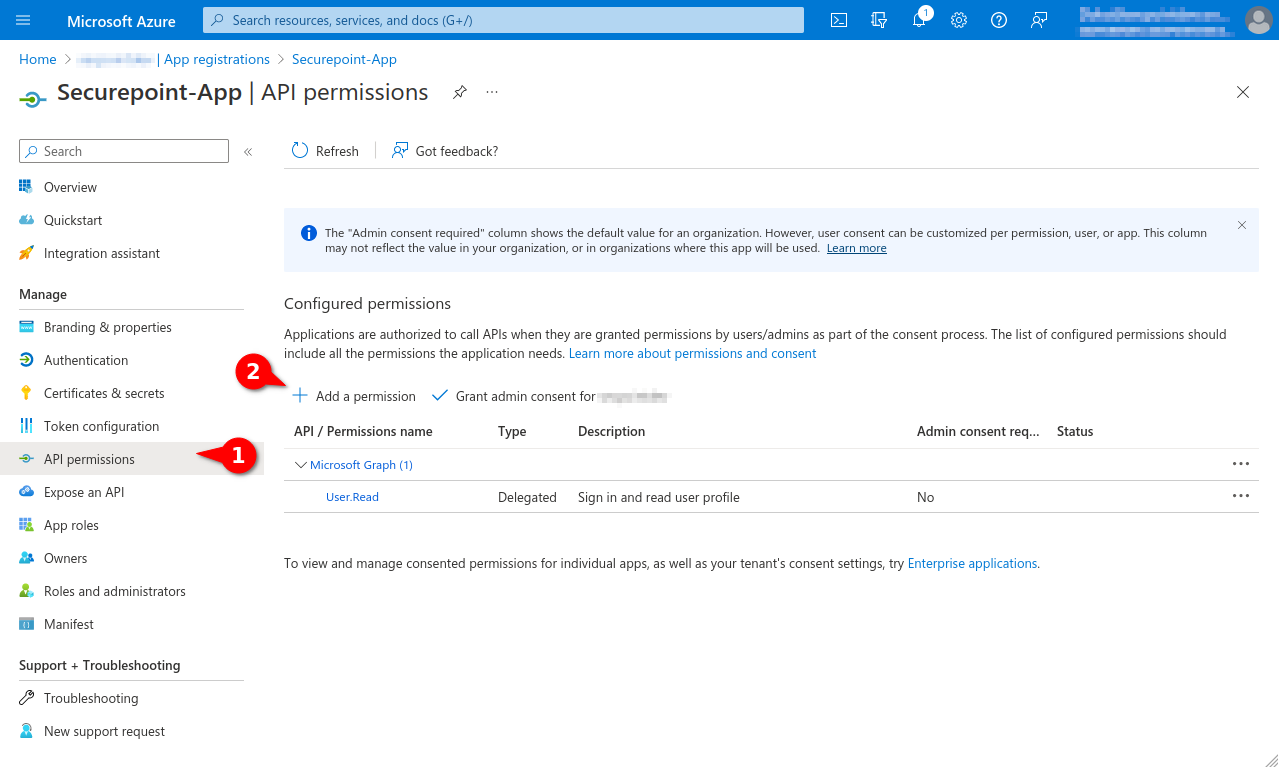
- Selection menu API permissions
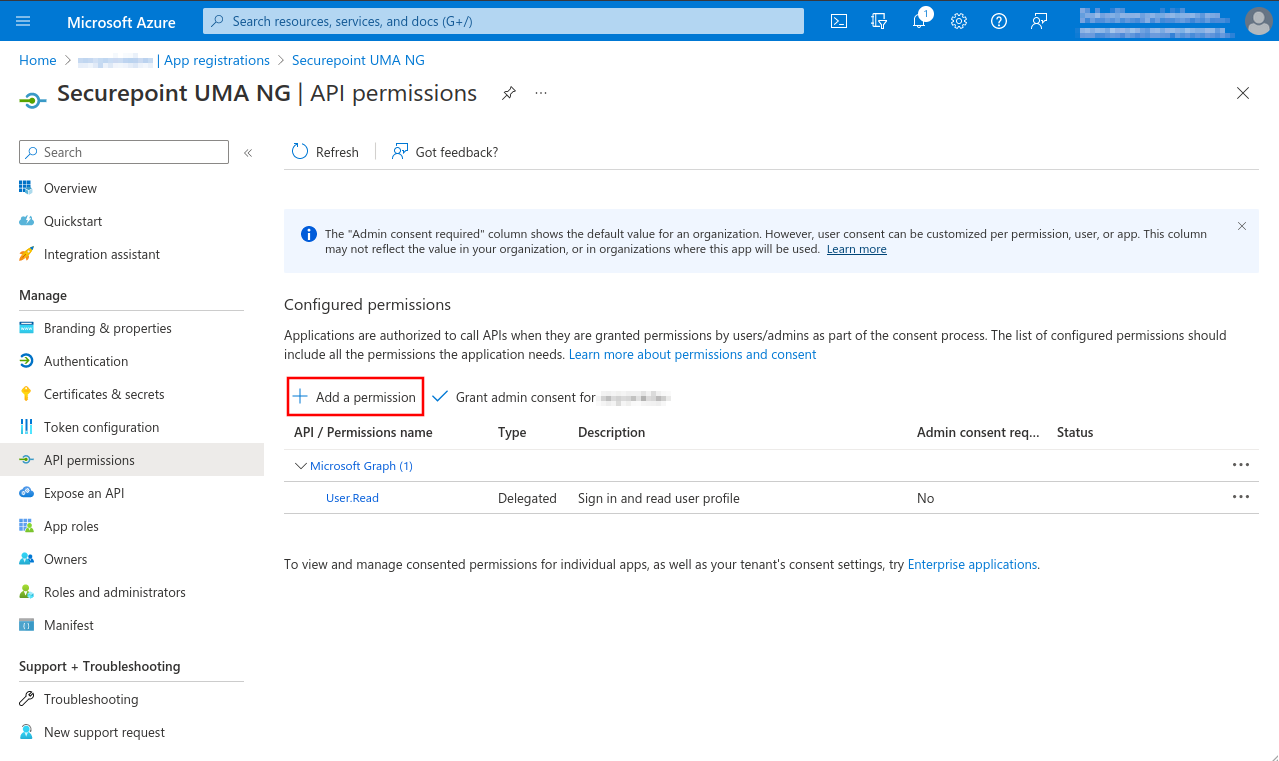
Fig.6
- Button + Add Permission
- The permission User.Read of type Delegated permission should already be entered as default permission
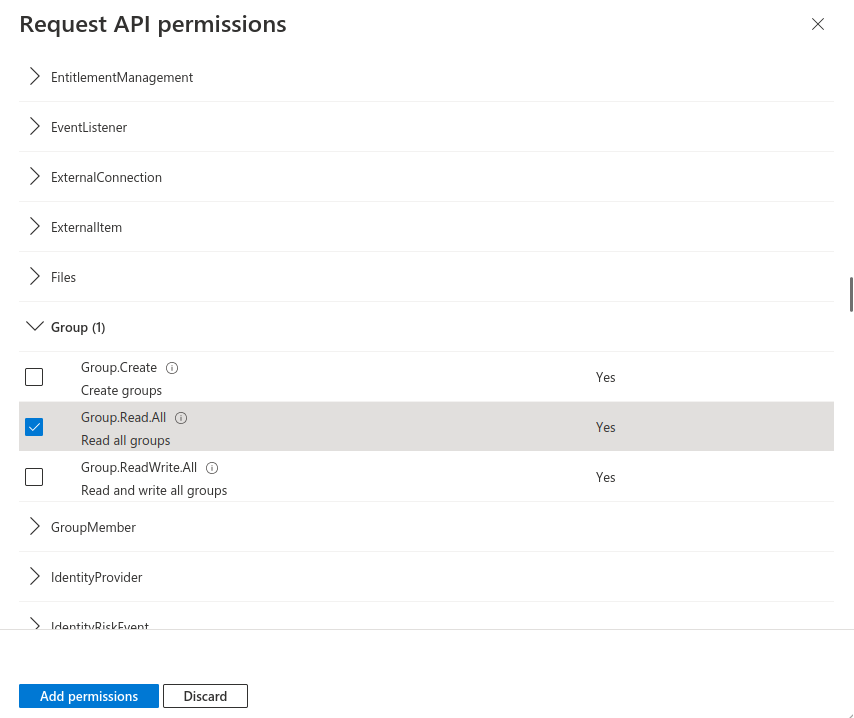
Fig.9
- Mark API permission Group.Read.All
This lets you find the permission you need faster.
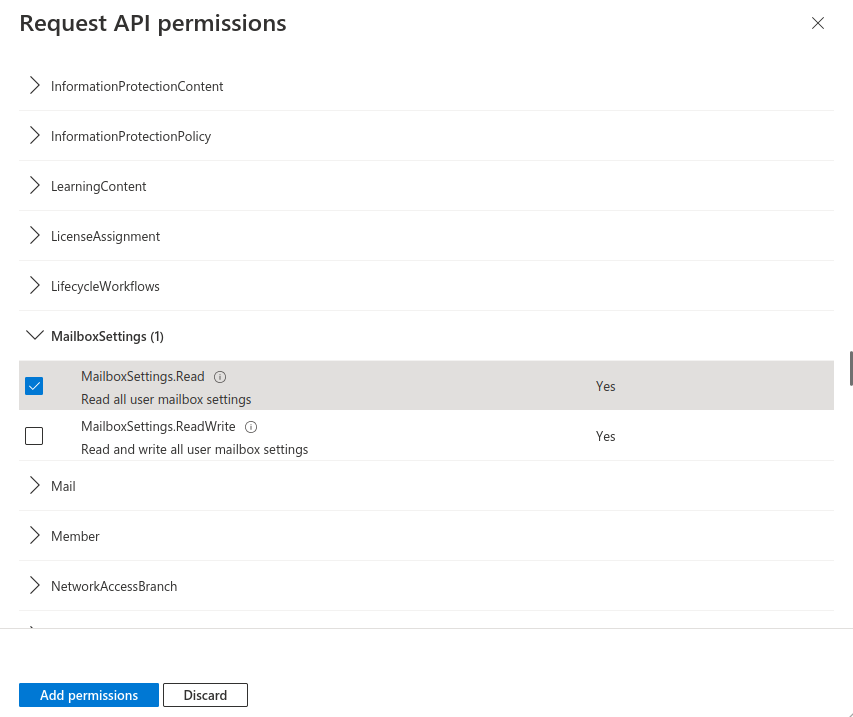
Fig.10
- Mark API permission MailboxSettings.Read
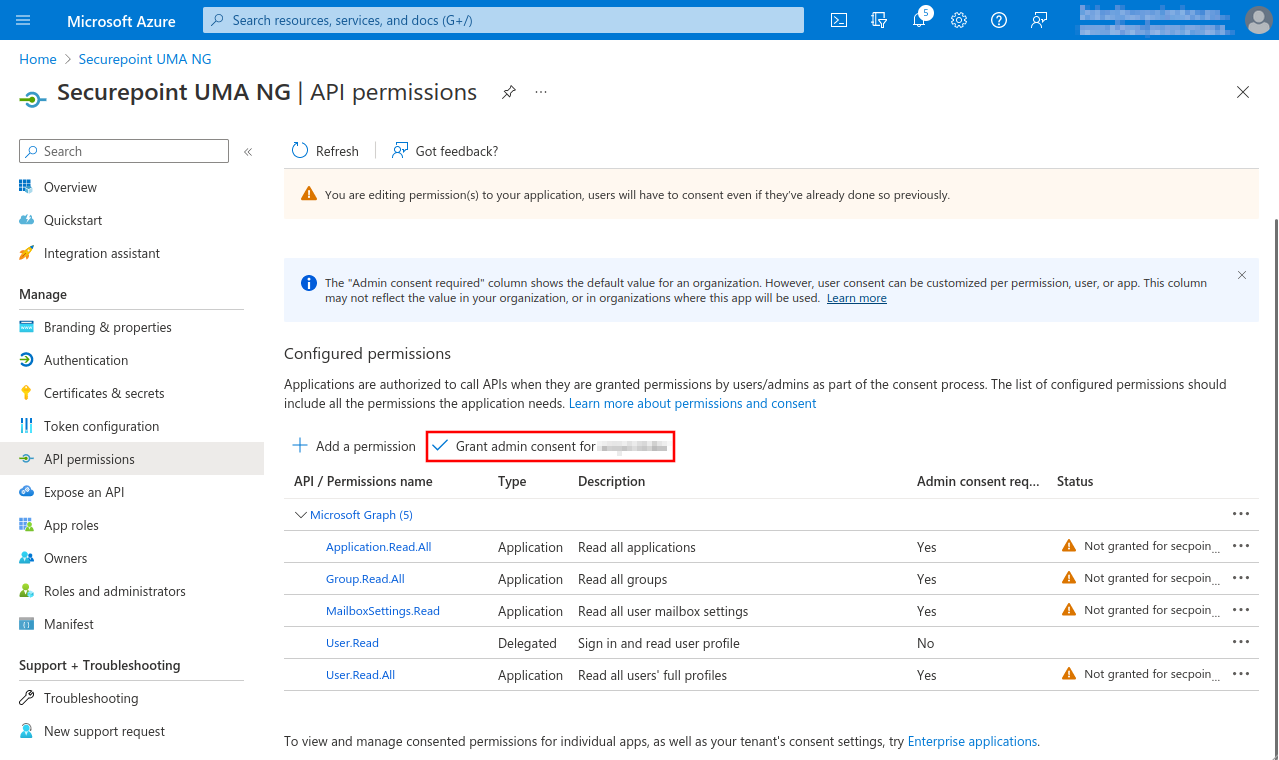
Fig.13
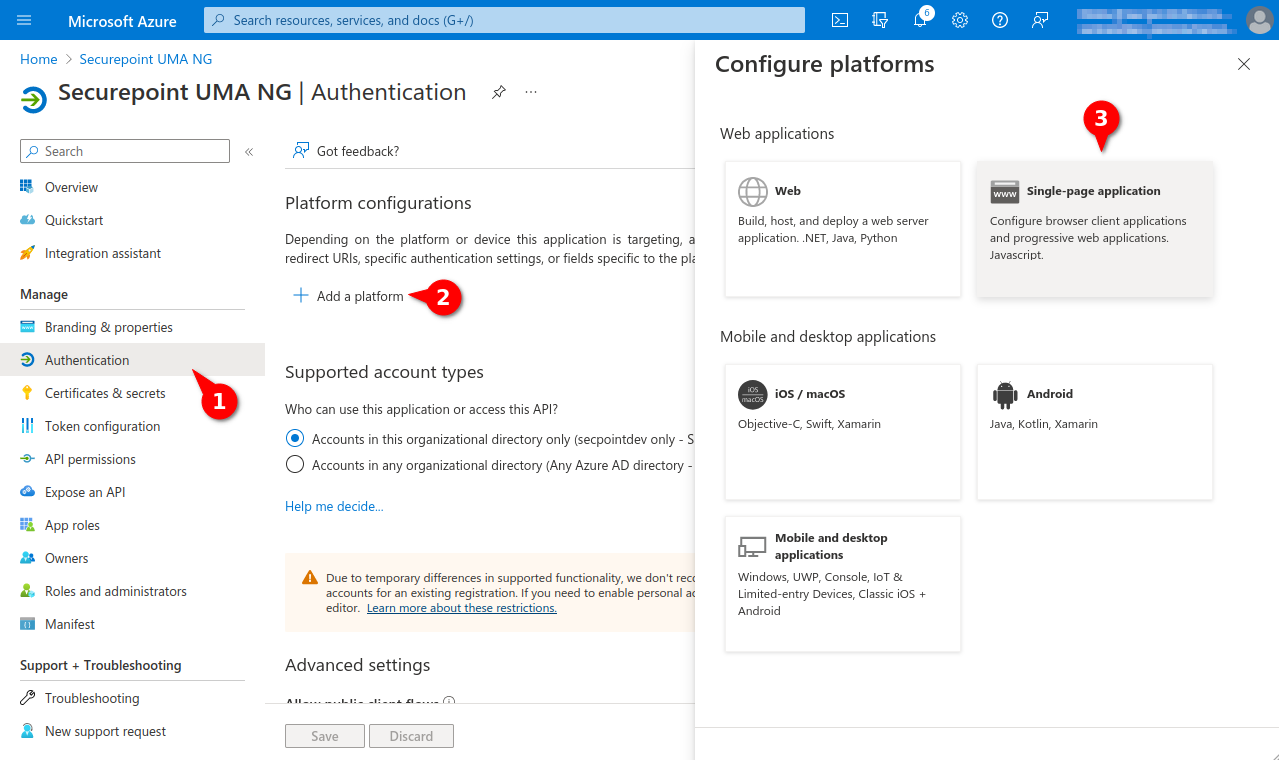
Fig.16
- Back to the dashboard, menu Azure Active Directory
- Menu Authentication
- Entry Add a platform
- Click on Single-page application in the Configure platform section.
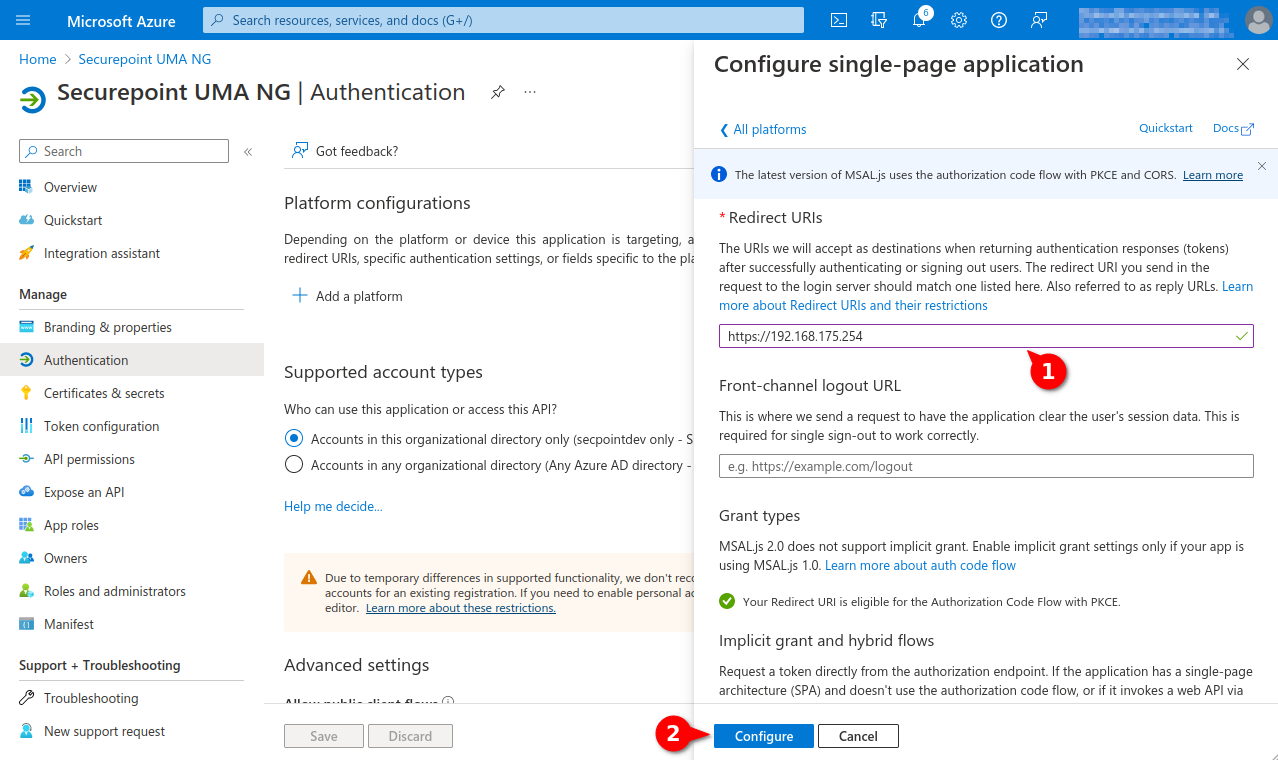
Fig.17
- Under Redirect URIs enter either the hostname or the IP address of the UMA.
- Click the Configure button
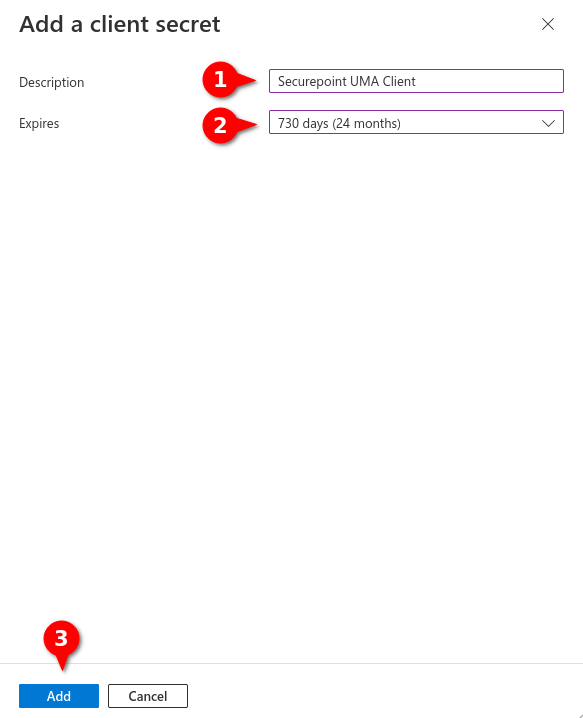
Fig.20
- Assigning unique name
- Selecting desired validity period
The Secret client Key must be renewed in a timely manner. After the validity period expires, emails will no longer be delivered to the UMA and users of the UMA DMS will no longer be able to be authenticated by Azure AD. - Button Add
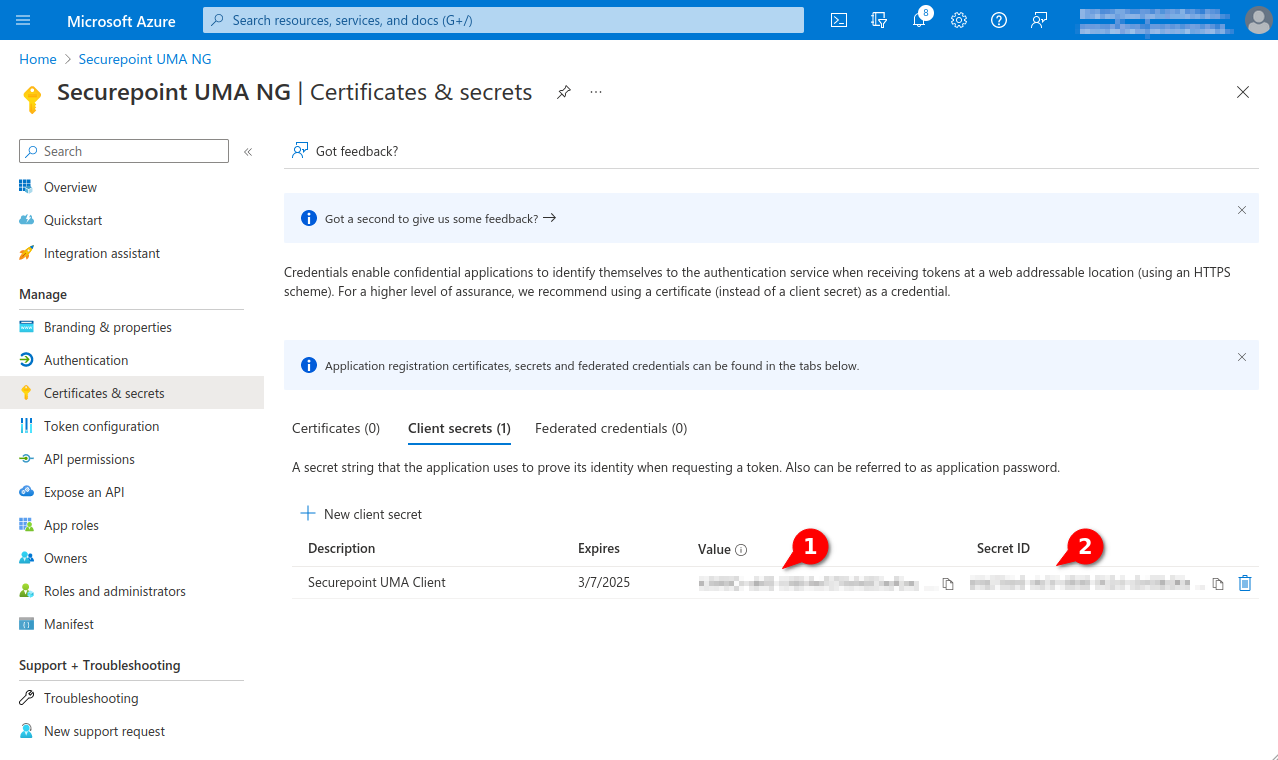
Fig.21
- The Client Secret is displayed in the Value column
- The Client ID is displayed in the column Secret ID
New as of 3.1.3 Both values are required for configuration in the Securepoint UMA.
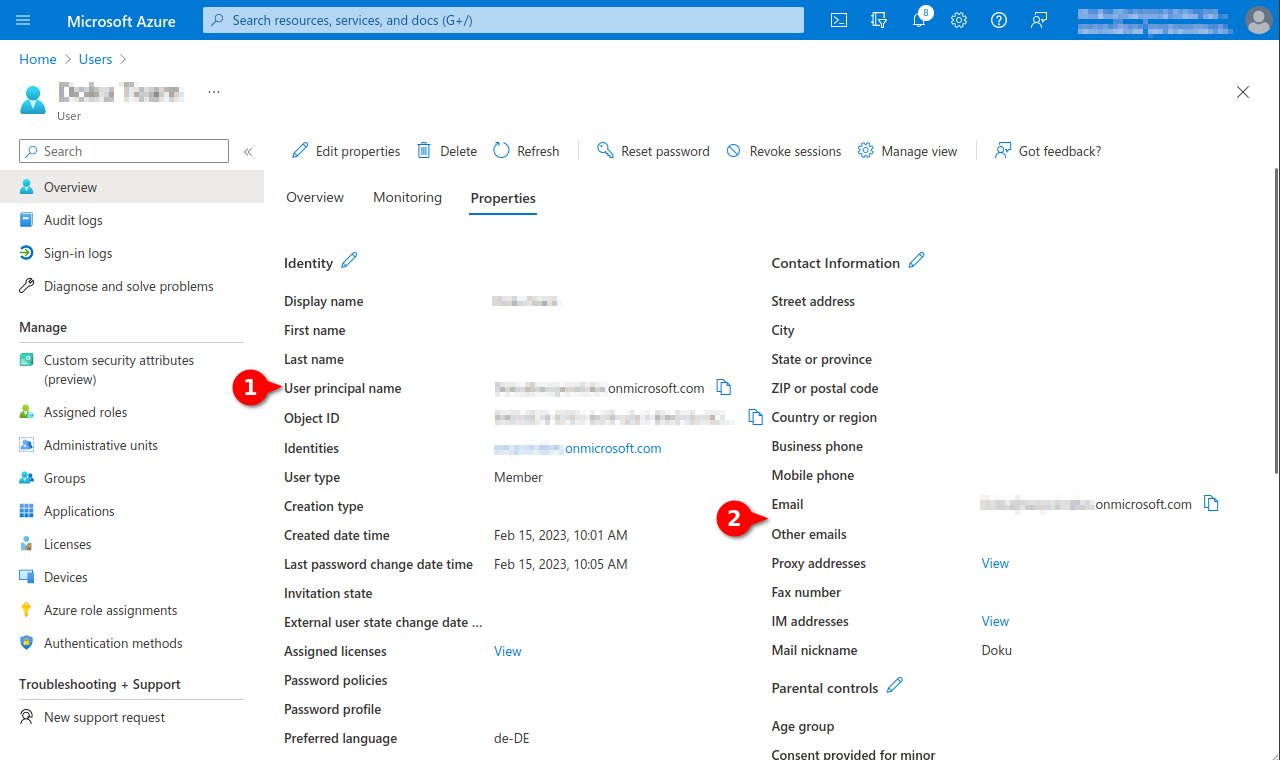
Fig.22
- In order to archive additional mail addresses besides the original Microsoft Azure email address, these must be stored in the user profile in the Azure Active Directory in the section Contact information as Alternative email address.
The login of the user in the Securepoint UMA NG is then done with the user principal name (user pricipal name) and the corresponding password from Azure AD.
For mailbox import and journal mailbox use from Azure, additionally configured apps in Azure are required.

This article includes descriptions of third-party software and is based on the status at the time this page was created.
Changes to the user interface on the part of the manufacturer are possible at any time and must be taken into account accordingly in the implementation.
All information without warranty.
- Tenant ID
- Client ID
- Client secret
- Launch Azure Active Directory admin center
- Note down/Copy Tenant ID from the Azure Active Directory menu
- Register new app under theApp registration menu under the New registration button
- Assign a unique name and click the register button
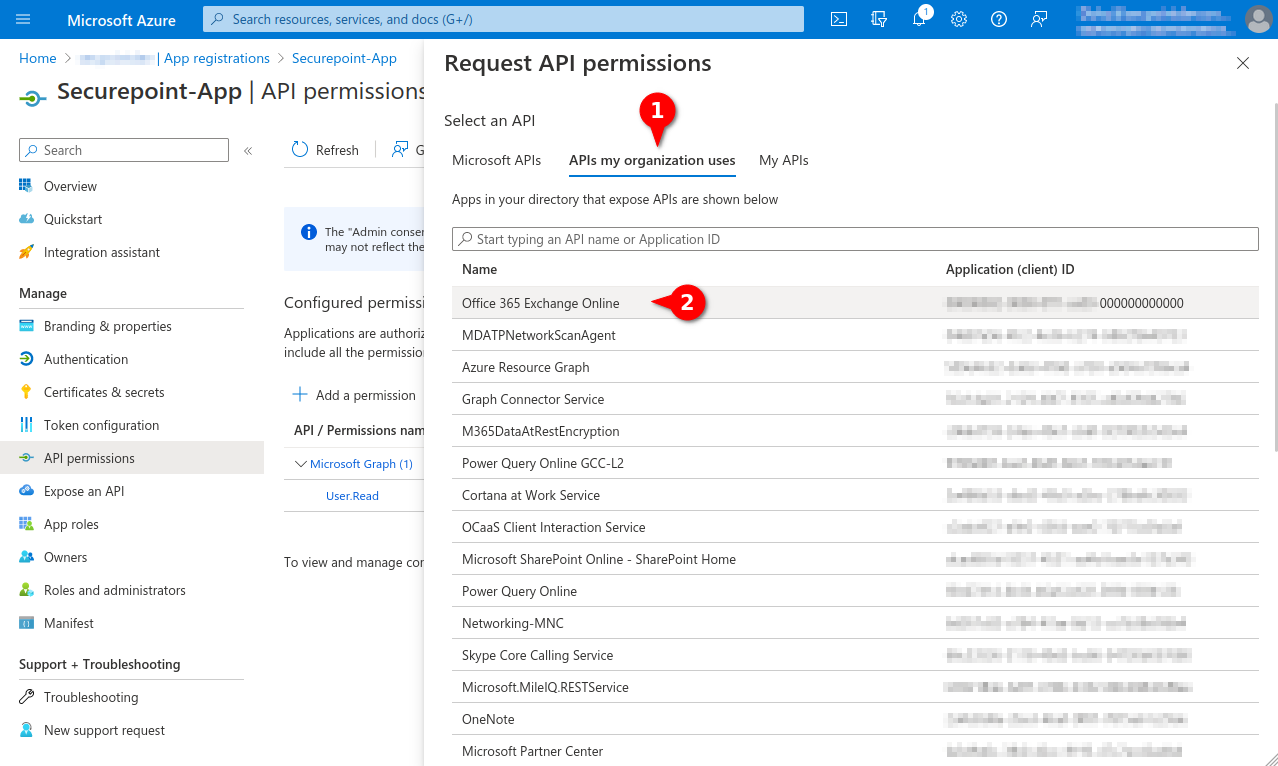
- In the API permissions menu, click the Add a permission button.
- Select permission for Office 365 Exchange Online in the APIs my organization uses tab
- Add IMAP.AccessAsApp permission for Office 365 Exchange Online
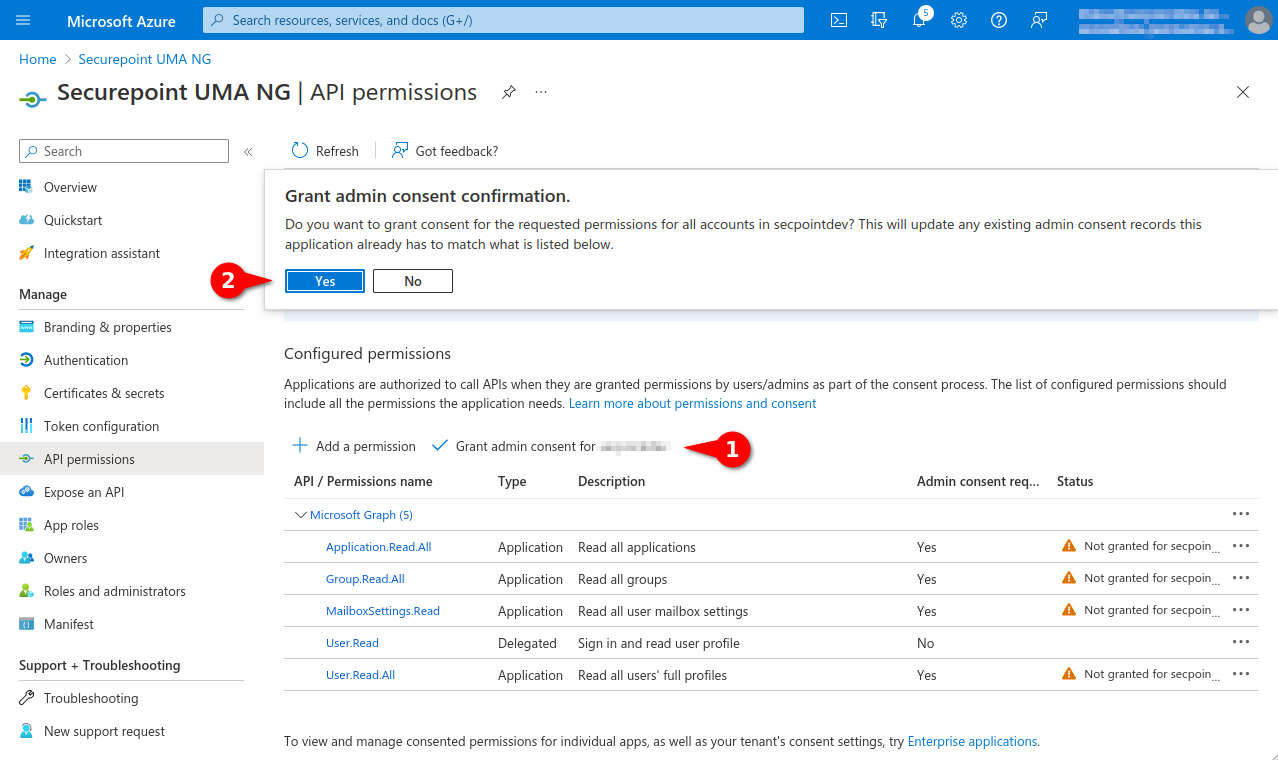
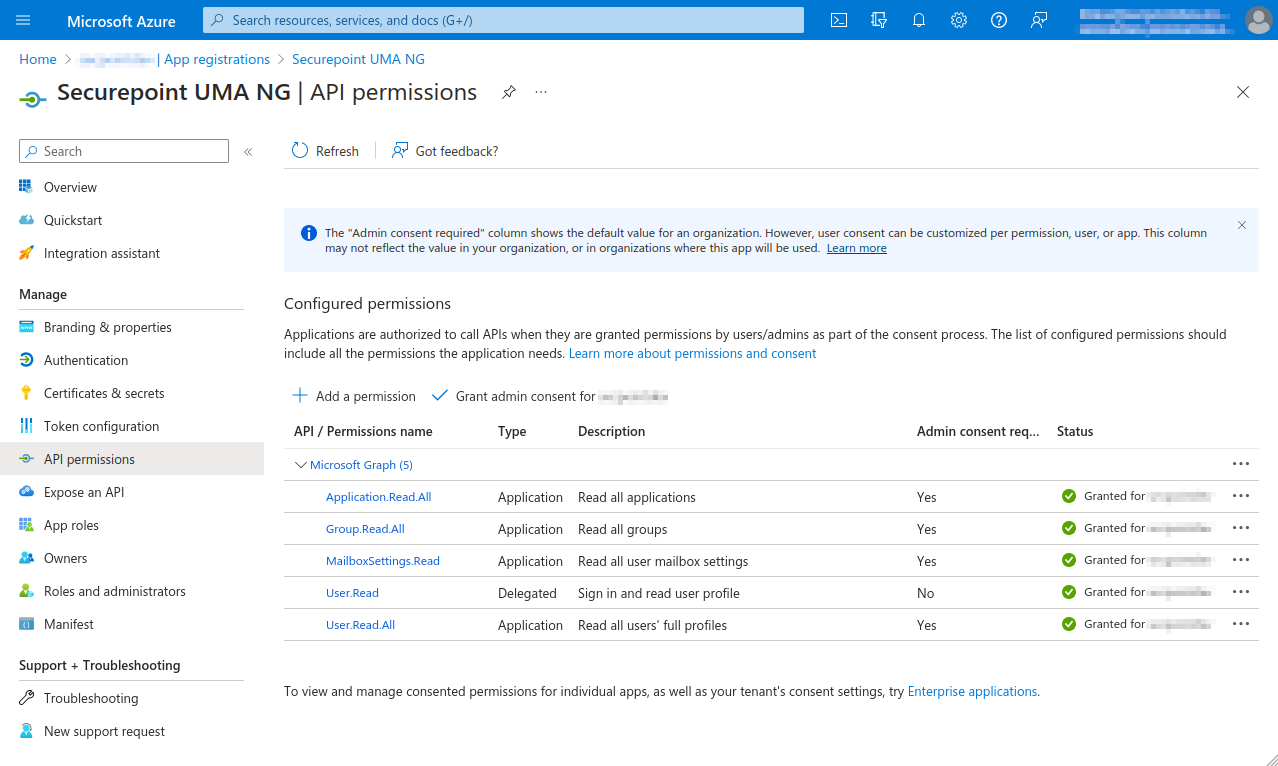
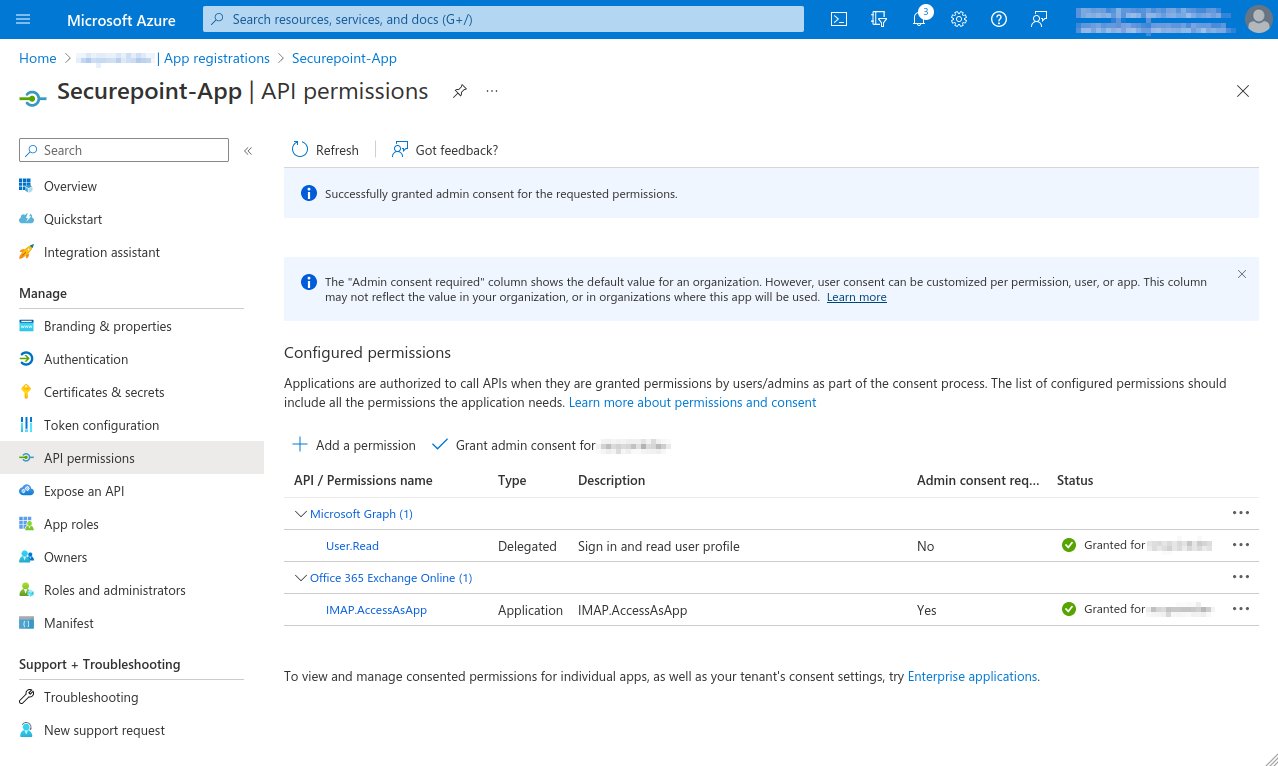
- In the menu API permissions activate the entry Grant admin consent for [...].
- Create a Client secret in the Certificates & secrets menu
- Note down Value, is entered as Client secret for Remote e-mail accounts and Import single mailboxes
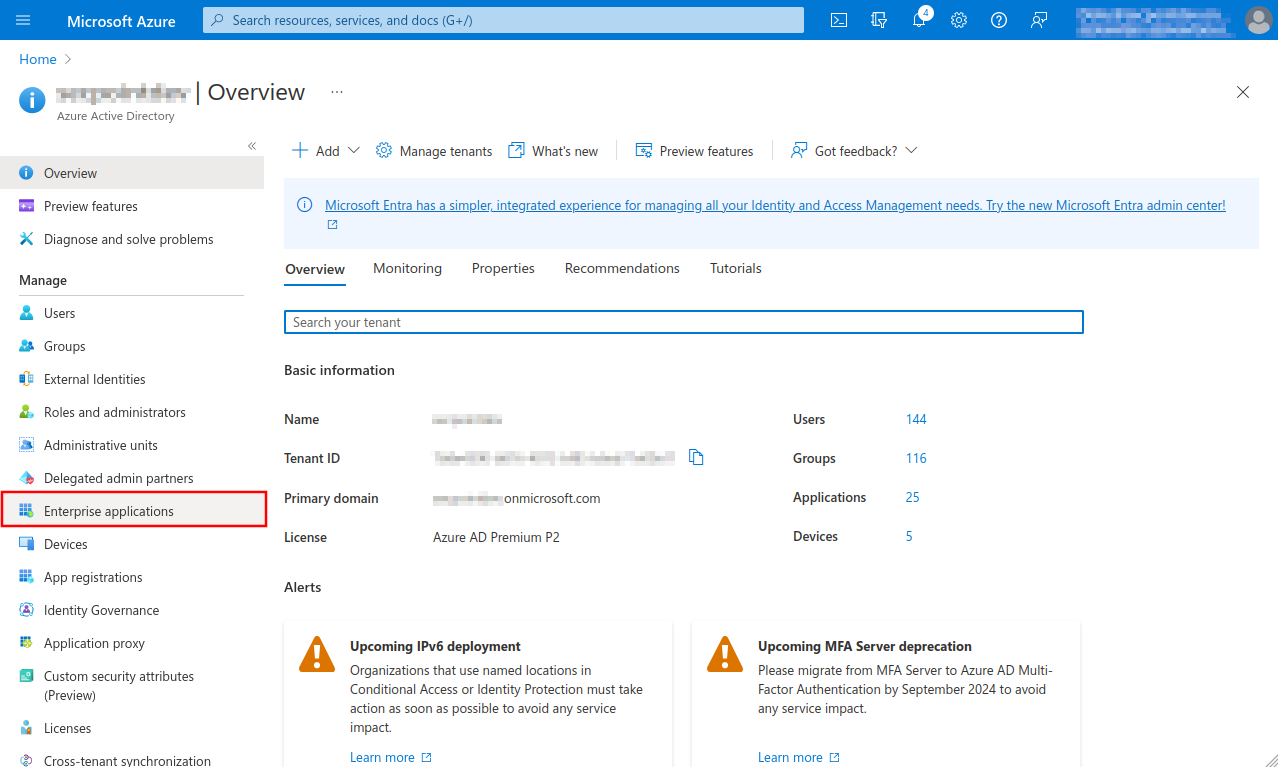
- Open menu Enterprise Applications and select app
- Note down from the app properties Application ID and Object ID.
- Open Powershell on Windows Client Administrator, import ExchangeOnlineManagement and connect to tenant
- Select the recipient mailbox in the Exchange admin center and choose Read and manage (Full Access) as delegation.
- Add member for Mailbox Delegation
- This completes the configuration in Microsoft Azure.
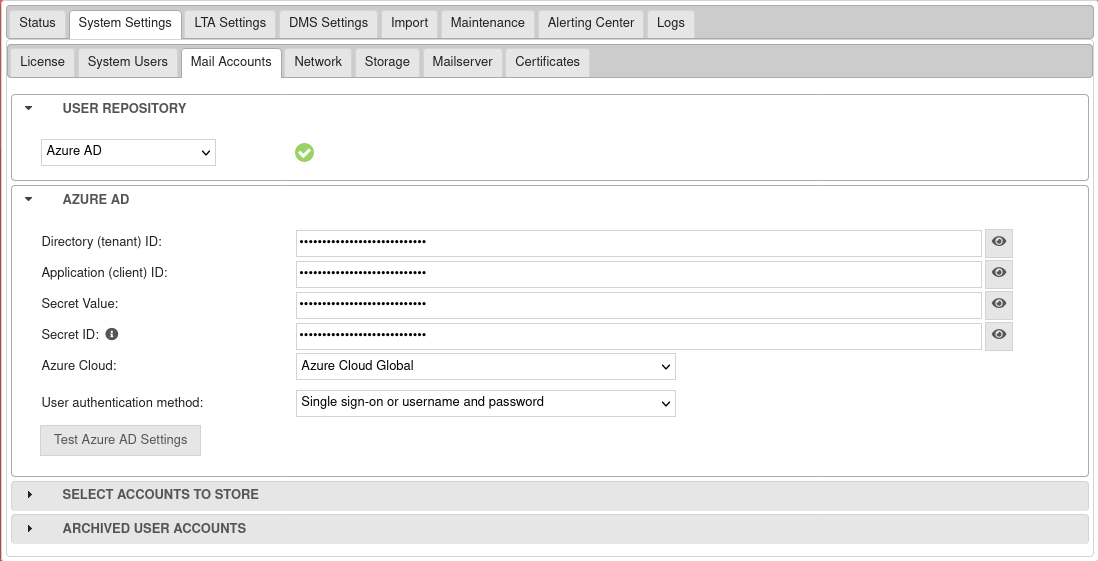
Further configuration is done in the UMA in the
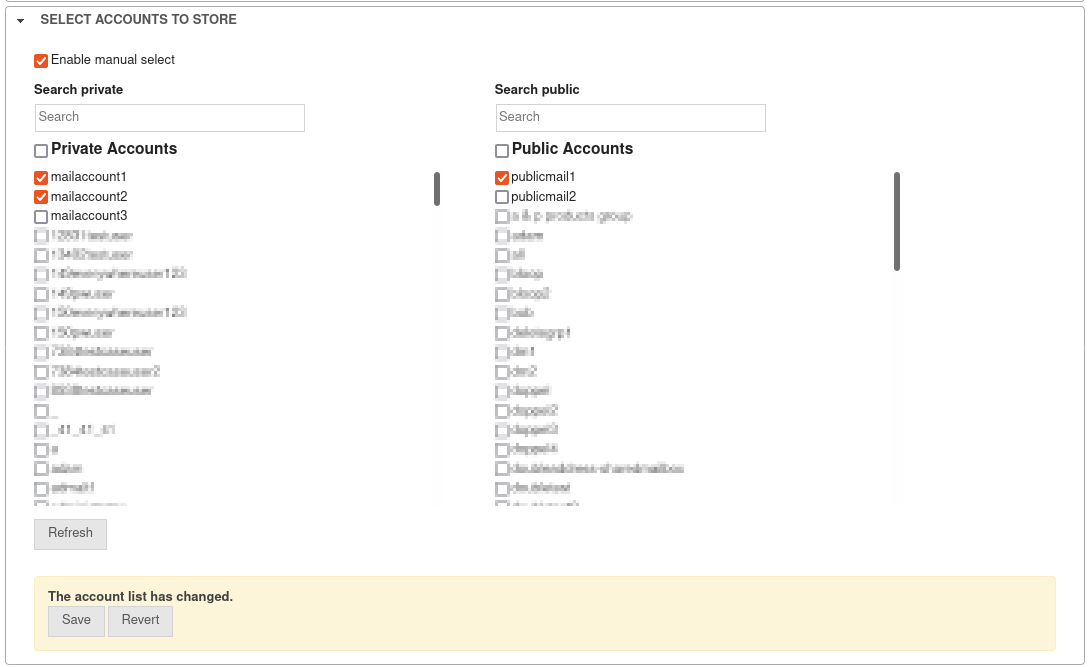
System settings Tab Email accounts section Azure AD menu, in the setup wizard or when importing mailboxes. - The Microsoft servers may take up to 30 minutes before access works
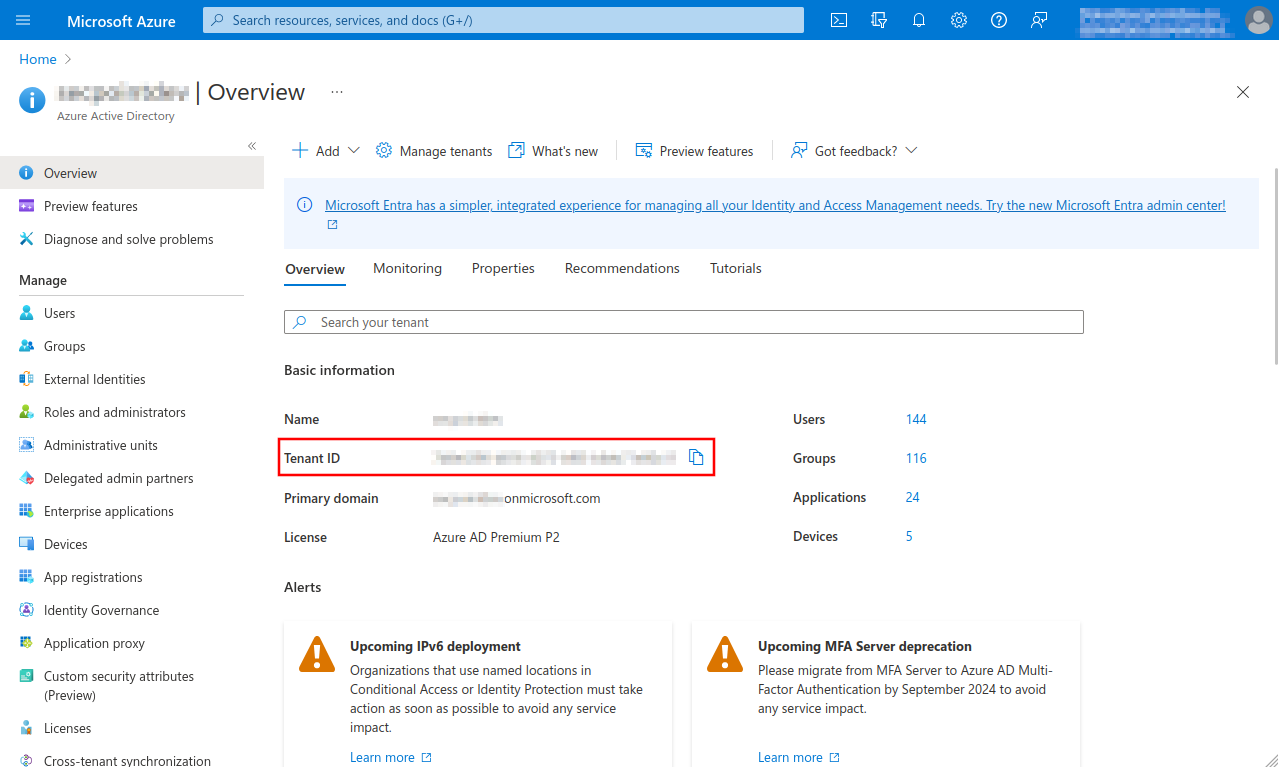
Fig.1
- Select Azure Active Directory menu
- Note down or copy Tenant ID, is entered for remote e-mail accounts and for importing single mailboxes
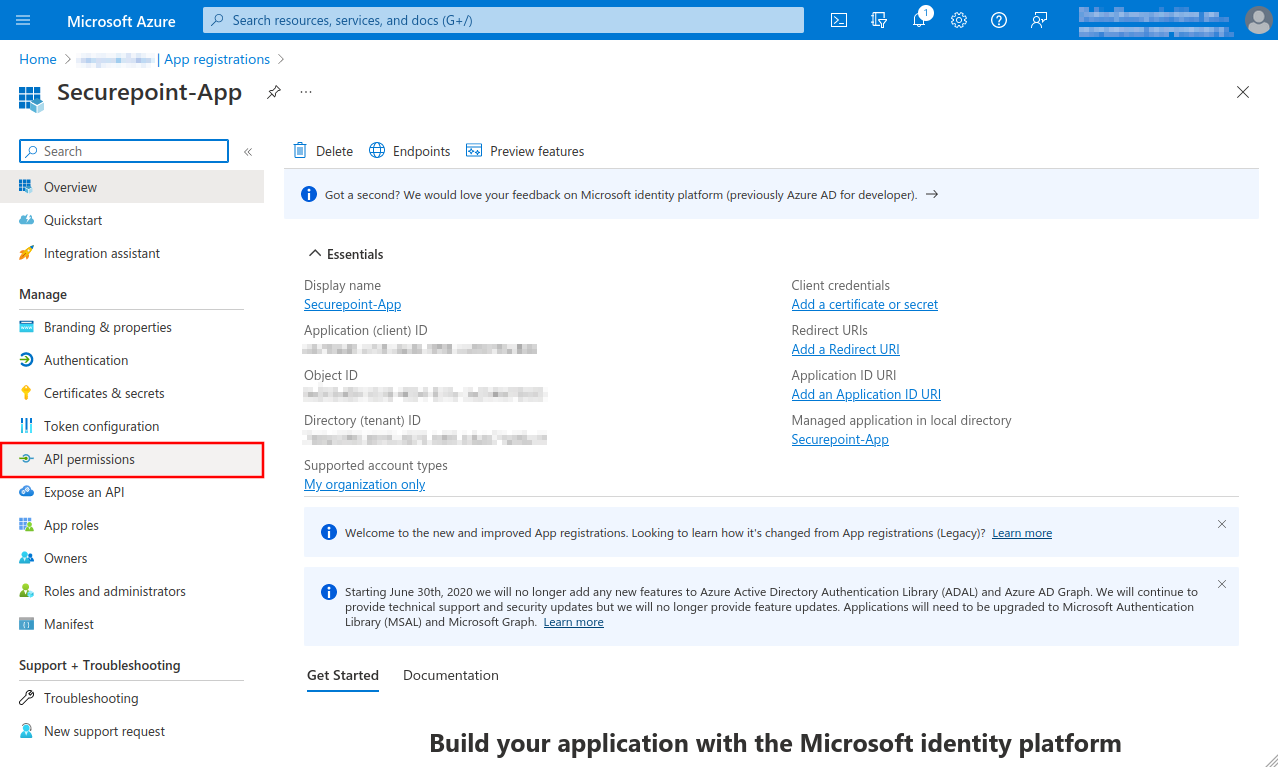
Fig.4
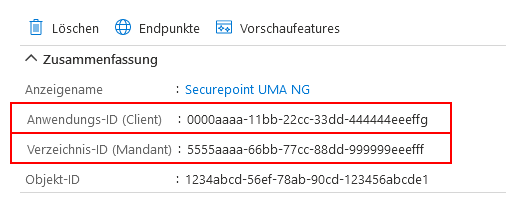
A summary of the newly registered app is displayed
- The Object ID displayed here does not belong to the app and is not needed!
- Select API permissions menu
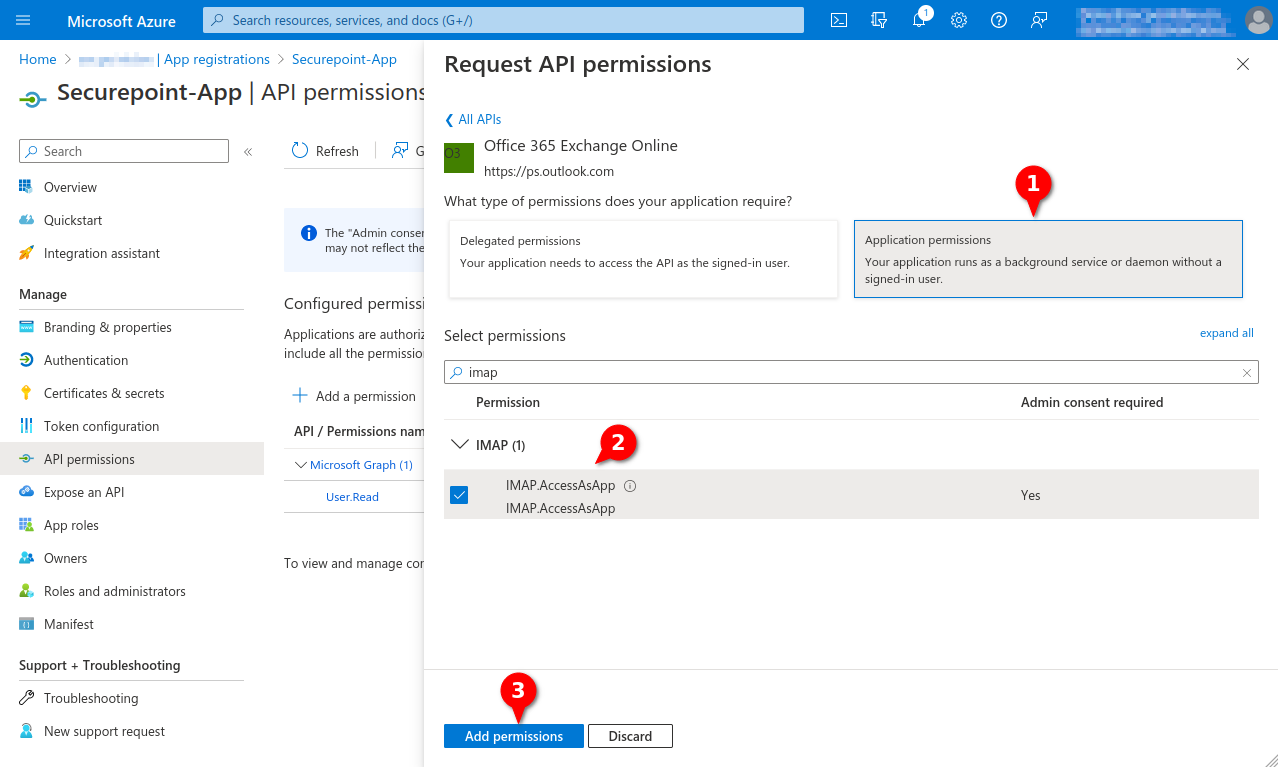
Fig.7
- Click Application permissions button
- Search for imap
- Checkmark IMAP.AccessAsApp
- Click the Add permissions button
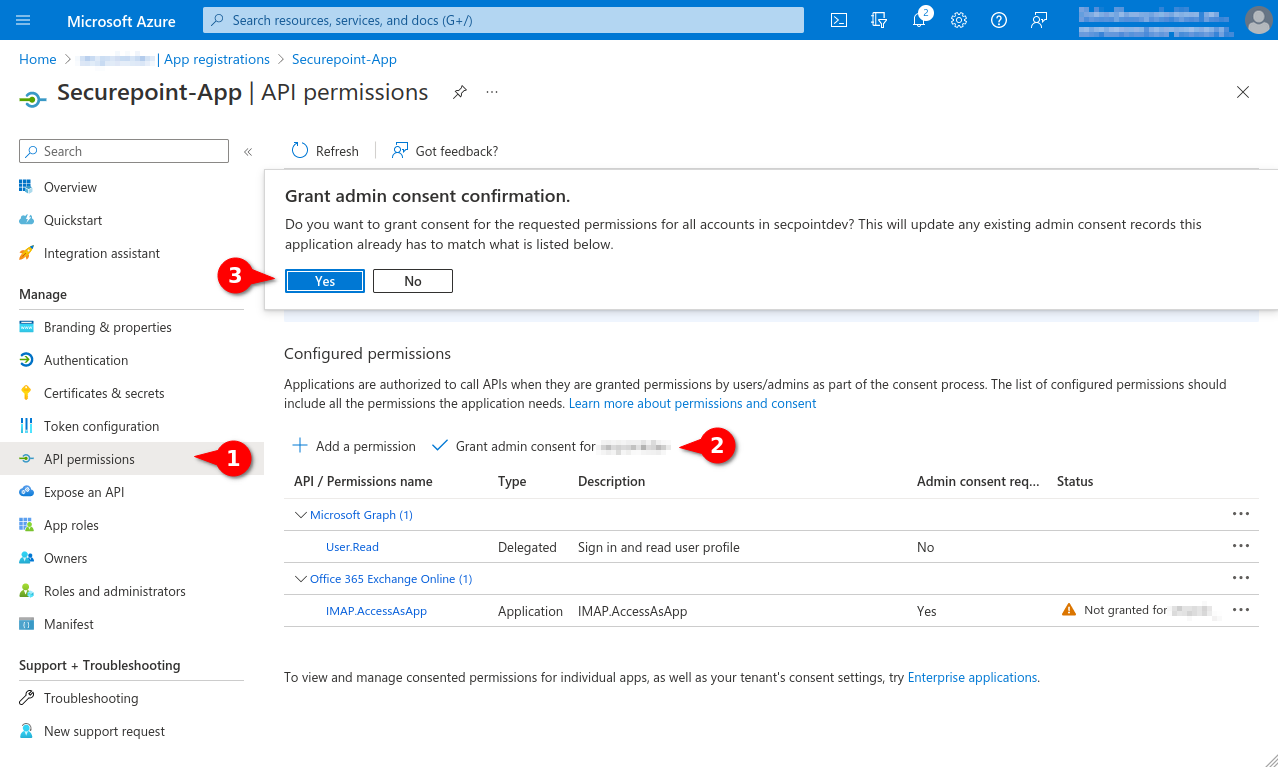
Fig.8
- Select menu API permissions again.
- Select entry Grant admin consent for [...]
- Click the Yes button
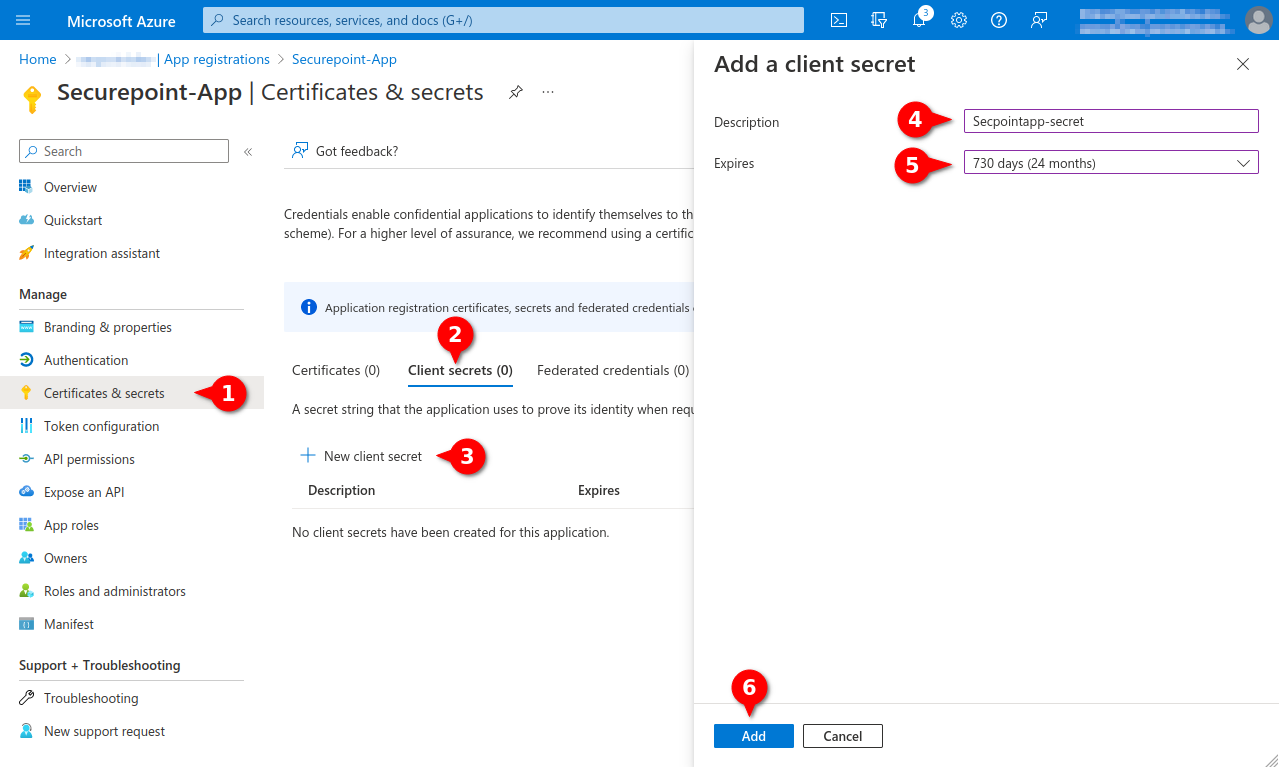
Fig.10
- Menu Certificates & secrets
- Tab Client secrets
- Entry New Client secret
- Enter unique description
- Select desired duration (max. 24 months)
- Click Add button
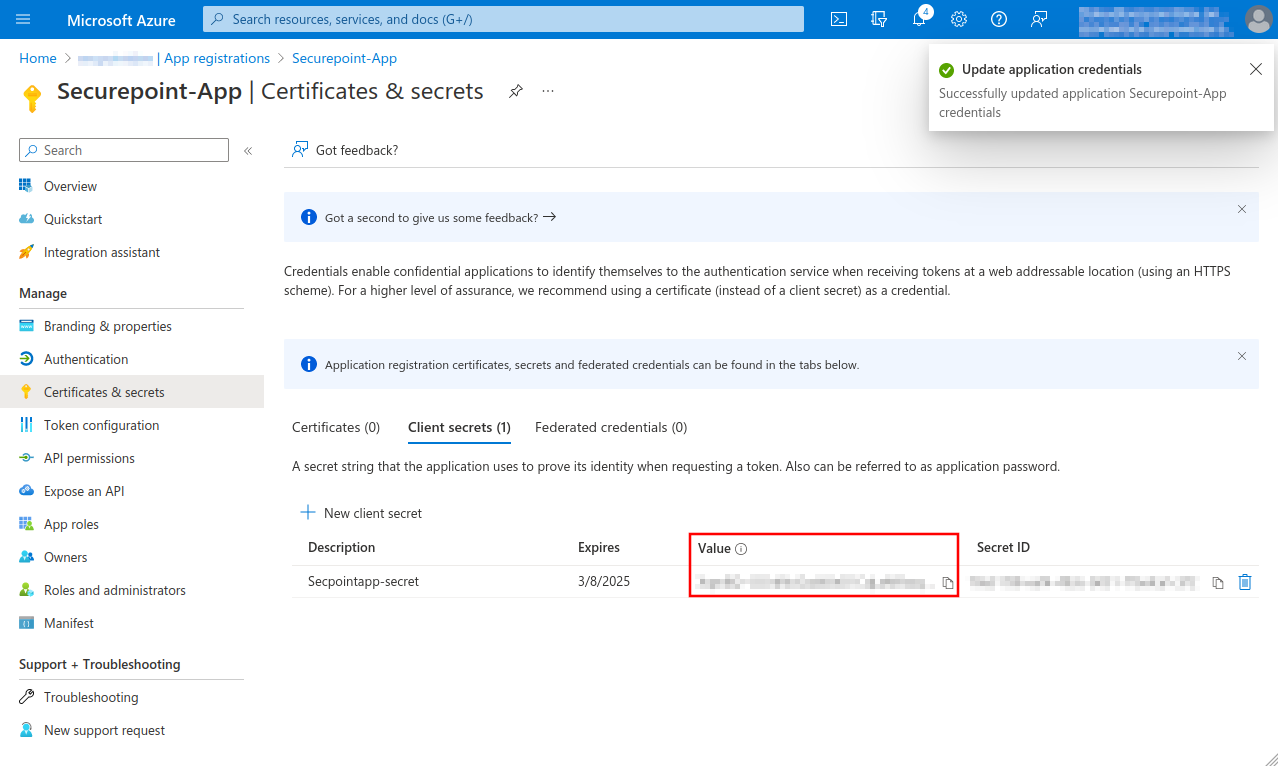
Fig.11
Note down Value, is entered as Client secret for Remote e-mail accounts and Import single mailboxes
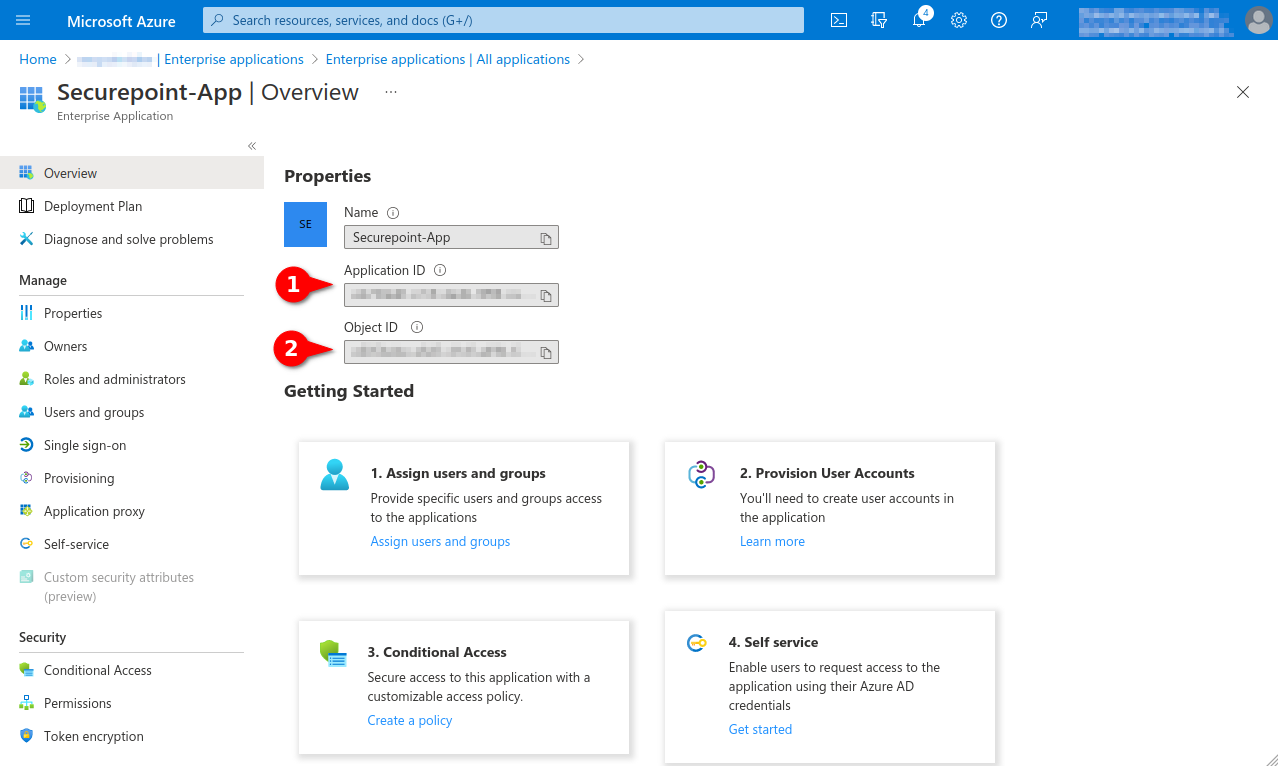
Fig.14
Note down from the app properties:
- Application ID, is entered as Application (Client) ID for Remote E-mail Accounts and Import Individual Mailboxes
- Object ID, is required for the granting of the authorisation via Powershell
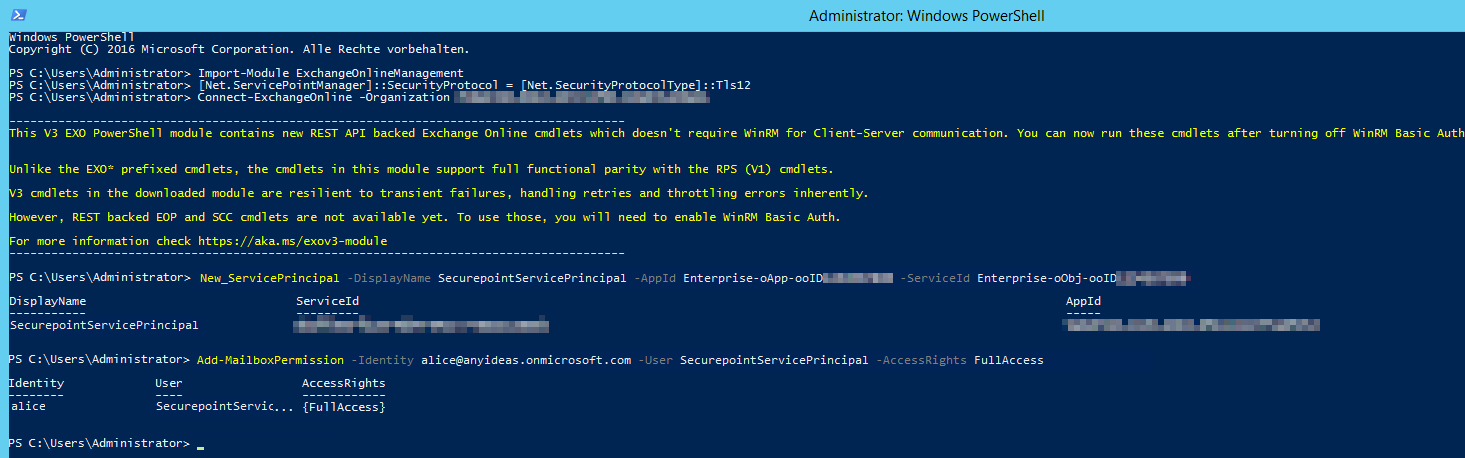
Fig.15
- Open Powershell on a Windows client administrator
- Install ExchangeOnlineManagement module If there are problems installing the module or connecting, you may need to configure Powershell to TLS 1.2:
>[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12- > Install-Module -Name ExchangeOnlineManagement -allowprerelease
- Import ExchangeOnlineManagement and connect to Tenant:
- > Import-module ExchangeOnlineManagement
- > Connect-ExchangeOnline -Organization Tenant ID (See Fig.1)
- Create a new service principal and assign a unique name:
- > New-ServicePrincipal -DisplayName SecurepointServicePrincipal -AppId Enterprise-oApp-ooID-oooo-oooooooo -ServiceId Enterprise-oObj-ooID-oooo-oooooooo
- For Enterprise-oApp-ooID-oooo-oooooooo enter the Application ID and for Enterprise-oObj-ooID-oooo-oooooooo enter the Object ID (see Fig. 14)
- Then assign mailbox permissions:
- > Add-MailboxPermission -Identity alice@anyideas.onmicrosoft.com -User SecurepointServicePrincipal -AccessRights FullAccess
The Microsoft servers may take up to 30 minutes before access works
The preparatory configuration of the Azure AD is now complete
Configuration in the UMA
In the setup wizard
Menu System Settings / Email Accounts
Troubleshooting
Error messages when testing Azure AD settings:
| Error message | Description |
|---|---|
| Insufficient privileges to complete the operation. | In this case, make sure that all Permissions have been set correctly |
| The requested user is invalid. | Self-explanatory. User names must exist and be permissible. Not allowed is for example: '@ttt-point.onmicrosoft.com |
| To many requests were made. Please try again later. | Throttling. Happens rarely to never. The Microsoft Graph API can handle a lot of requests in a short time. If not, it helps to wait a bit. |
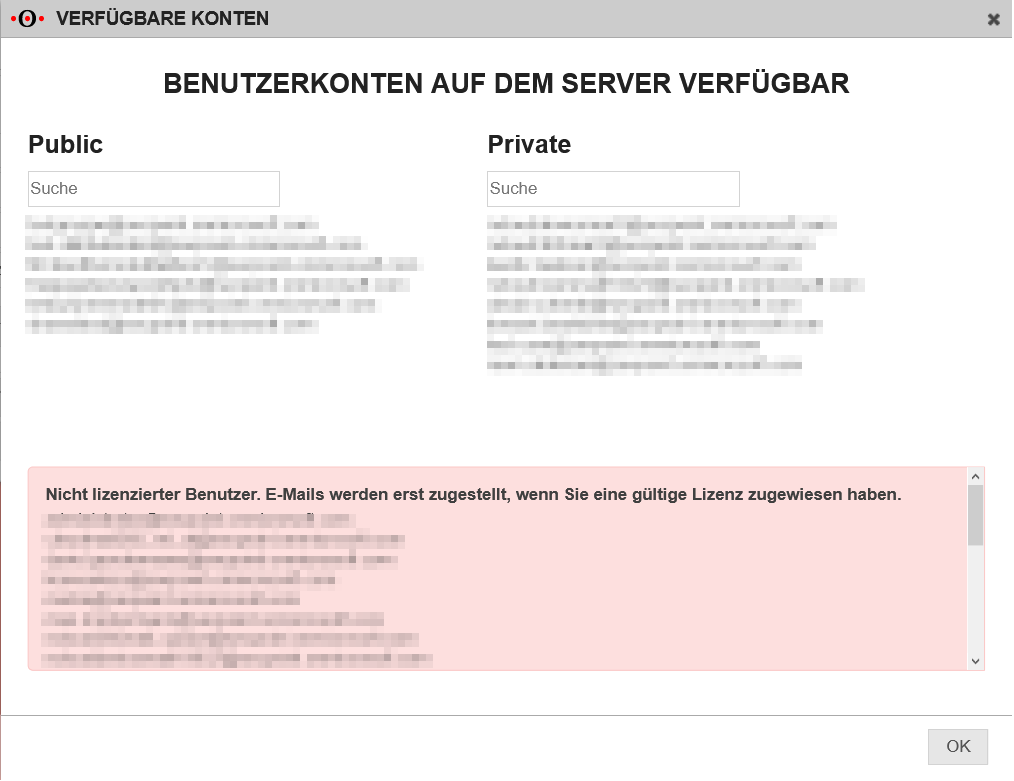
| Unlicensed user. Mails will not get delivered until there has been a valid license assigned. | Occurs when the queried account does not have a valid license. This results in the mailboxSettings attribute not being able to be queried. This is necessary to check whether the account is a shared mailbox. If the attribute cannot be queried, it is uncertain whether the account must be archived as public or private. |
| An unknown error occurred. | This is the fallback if the error could not be identified. This happens rarely. The Microsoft Graph API does not send a valid json in incredibly rare situations. Please try again. |