- Updated to Redesign of the webinterface
Introduction
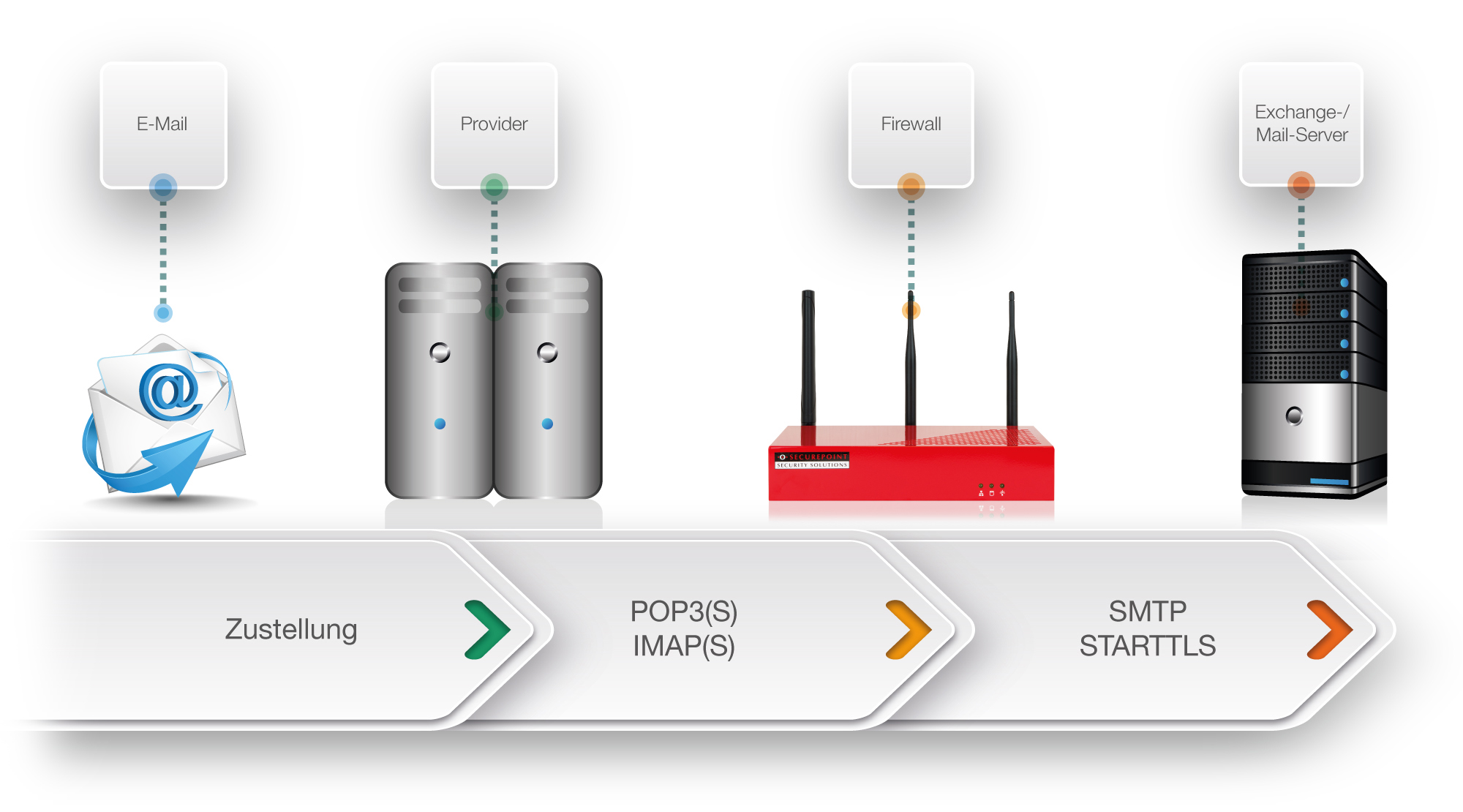
The Mail Connector offers the option of collecting emails from various mail servers via the POP3 and POP3S as well as IMAP and IMAPS protocols and forwarding them to an internal mail server. Forwarding to the internal mail server is done via the SMTP protocol.
Setup to pick up individual accounts
If a separate email account is configured for each user on the external mail server, a separate Mail Connector service must be created for each account. If a service is created for each additional email account, the minute interval is set in the General ranch under Interval (minutes).
If the local user accounts are always the same SMTP mail server, this will already be displayed faintly in the field from the second service onwards. You can then save without another entry in this field.
Configurations
Services
| To add a new Mail Connector service, click the button under Area Services. | |||
| Caption | Value | Description | UTMuser@firewall.name.fqdnApplicationsMail-Connector 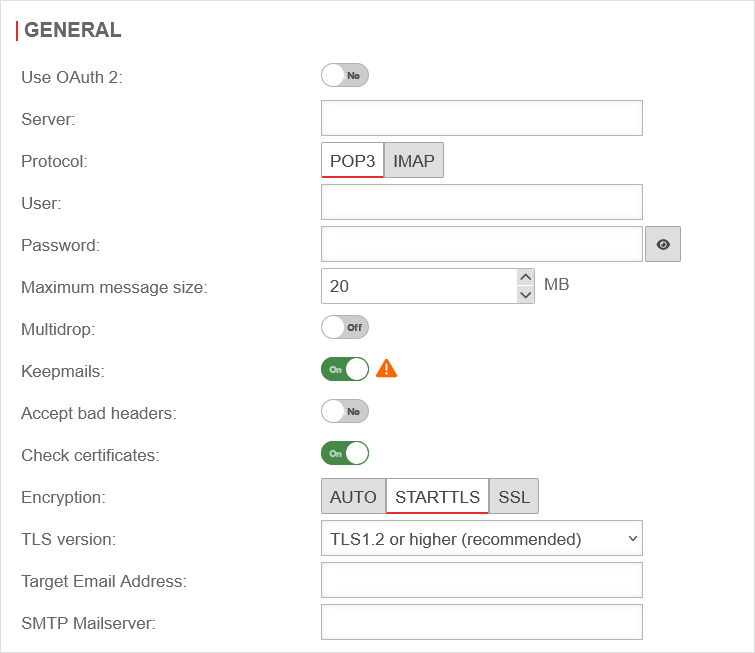
|
|---|---|---|---|
| Use OAuth 2: | No Default |
When Yes is enabled, OAuth 2 is used. The OAuth 2 connection item appears. | |
| OAuth 2 connection: |
An existing OAuth 2 connection is selected. With a new connection is created. | ||
| Server: | The external mail server from which the emails are fetched | ||
| Protocol: | Here the protocol used to connect to the external server is specified | ||
| User: | Username of the external mailbox. If Use OAuth 2 Yes is active, users can be selected from the OAuth source | ||
| Password: Hidden if Use OAuth 2 Yes is active. |
Password of the external mailbox | ||
| The password is displayed | |||
| Maximum message size: | 20 MB | Maximum message size for the Mail Connector | |
| Multidrop: | Off | If Multidrop is deactivated, the emails of a mailbox are forwarded to an internal email address. To collect emails for multiple recipients, Multidrop must be enabled. When On is enabled, the ranch Multidrop options is enabled. | |
| Keepmails | On | Usually emails are deleted after they have been picked up. Enabling of Keepmails prevents this deletion. Keepmails should only be used temporarily for test purposes, or if it is otherwise ensured that the external mailbox does not reach its capacity limit. | |
| Accept defective header: | Off | Emails with defective header are included in the Mail Connector | |
| Check certificates notempty New as of: v12.5 |
On | When activated Ein, the SSL certificates are checked. notempty For new connections this is activated by default, for existing connections it is deactivated by default. notemptyIf the SSL certificate is rejected during the check because it is no longer valid or trustworthy, no connection is established.
| |
| Encryption: | Specifies the type of encryption | ||
| TLS version: Not when encyrption is: auto notempty New as of v12.5.1 |
The desired TLS version can be selected. | ||
| Destination email address: With multidrop deactivated |
| ||
| Destination domain: With activated multidrop |
Specifies the destination domain | ||
| SMTP Mailserver: |
| ||
Multidrop (Pickup from a collective account)Multidrop (Pickup from a collective account)
If all emails should be stored on the external mail server in a collective mailbox and only assigned to the local user mailboxes when they are collected, these can be set up with the Multidrop option. To do this, activate the Multidrop option for a new service or for an existing one. The following settings are made in the Multidrop options ranch: The idea behind multidrop in the Mail Connector is to pick up mails from a CatchAll collective mailbox of an external provider and to deliver them to the individual mailboxes on the company's own mail server. The differentiation of the individual mailboxes via the Mail Connector is done via an envelope header entry in the emails of the collective mailbox. However, this can vary depending on the provider and the mail server used. Make sure that if the Multidrop is used, the individual mailboxes must also be specified under "Remote User".
Otherwise the mail connector cannot deliver the mails to the individual mail accounts. |
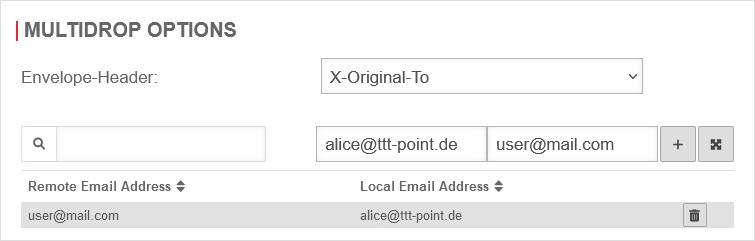 | ||
| Envelope-Header: | The envelope header entry is selected. It determines which emails from the original recipient with this envelope header entry will be assigned to a local mail account on the internal mail server. | ||
| Remote email address: | user@mail.com | Email address of the original recipient | |
| Local email address: | alice@tttpoint.de | Email address of the internal recipient | |
| Click to assign | |||
OAuth 2OAuth 2 | |||
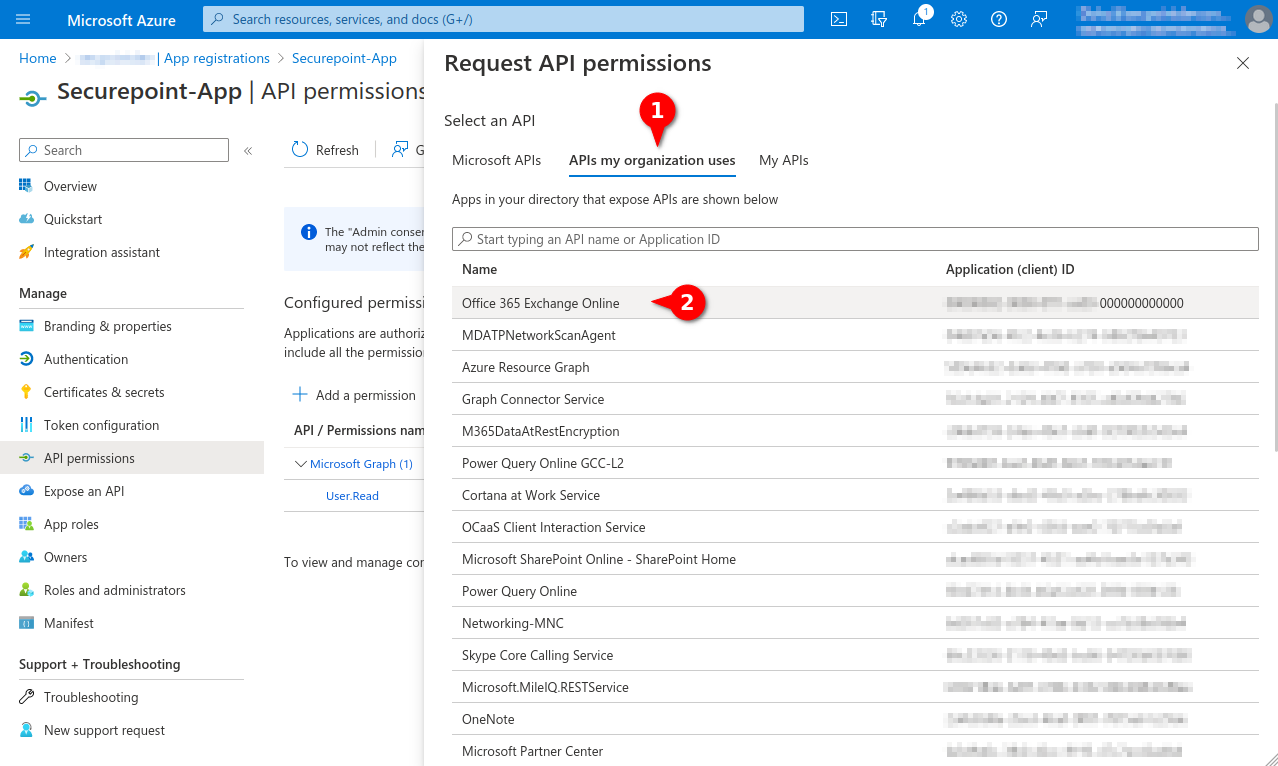
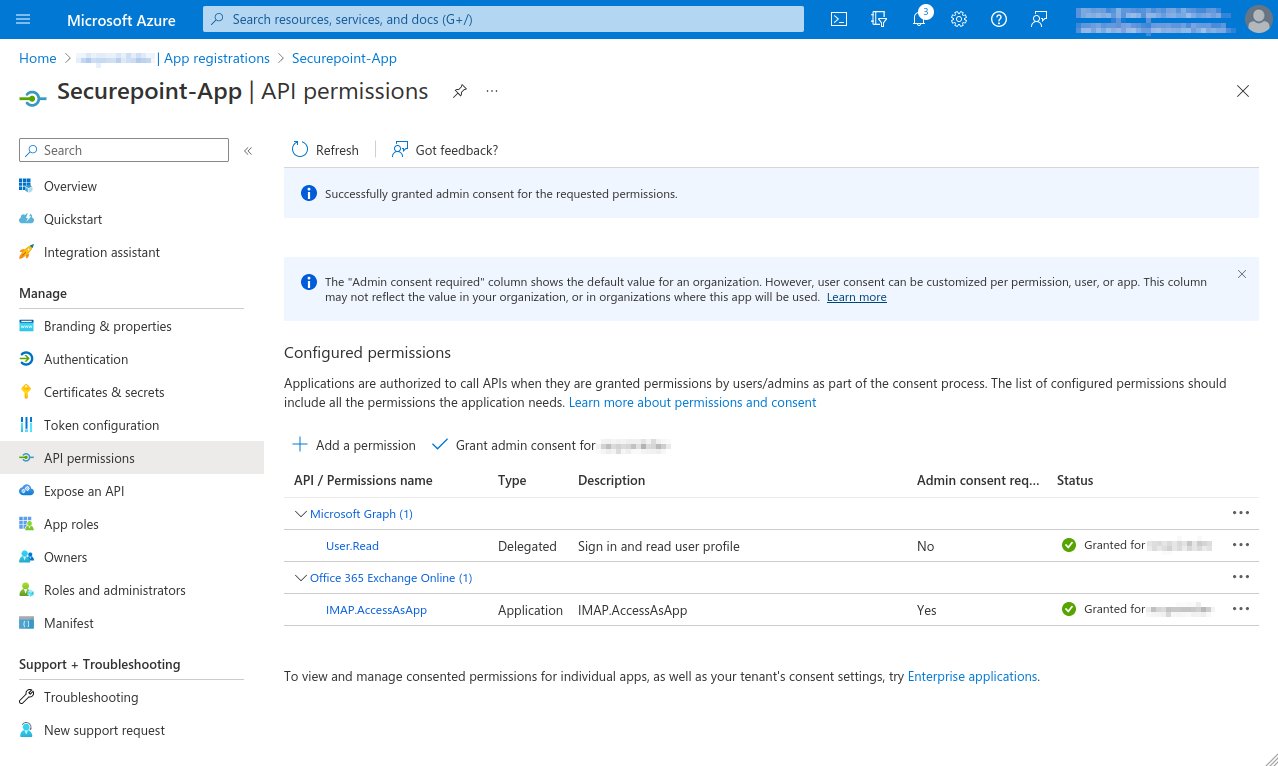
| In the OAuth 2 ranch, click the button to create a new OAuth 2 connection. Depending on the provider selection Google Workspace, Microsoft 365 (Secret Client Key), or Microsoft 365 (Certificate) the configuration steps will change. | |||
Google Workspace Google Workspace
| |||
| Name: | Name of the OAuth 2 connection | UTMuser@firewall.name.fqdnApplicationsMail-Connector 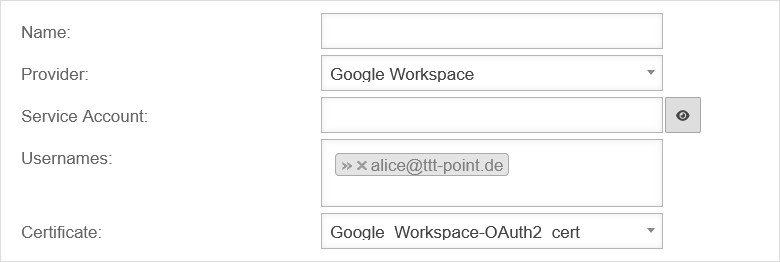
| |
| Provider: | Google Workspace | Provider selection | |
| Service account: | The Google Workspace service account is entered | ||
| User account: | » ✕alice@ttt-point.de | The user accounts are selected | |
| Certificate: | Google_Workspace-OAuth2_cert | The certificate that is uploaded in Azure is selected | |
| Preliminary note Microsoft 365 | |||
| In order to use Microsoft 365, configured Azure Apps are necessary. | |||
This article includes descriptions of third-party software and is based on the status at the time this page was created. Changes to the user interface on the part of the manufacturer are possible at any time and must be taken into account accordingly in the implementation. All information without warranty.
anf in the tab
 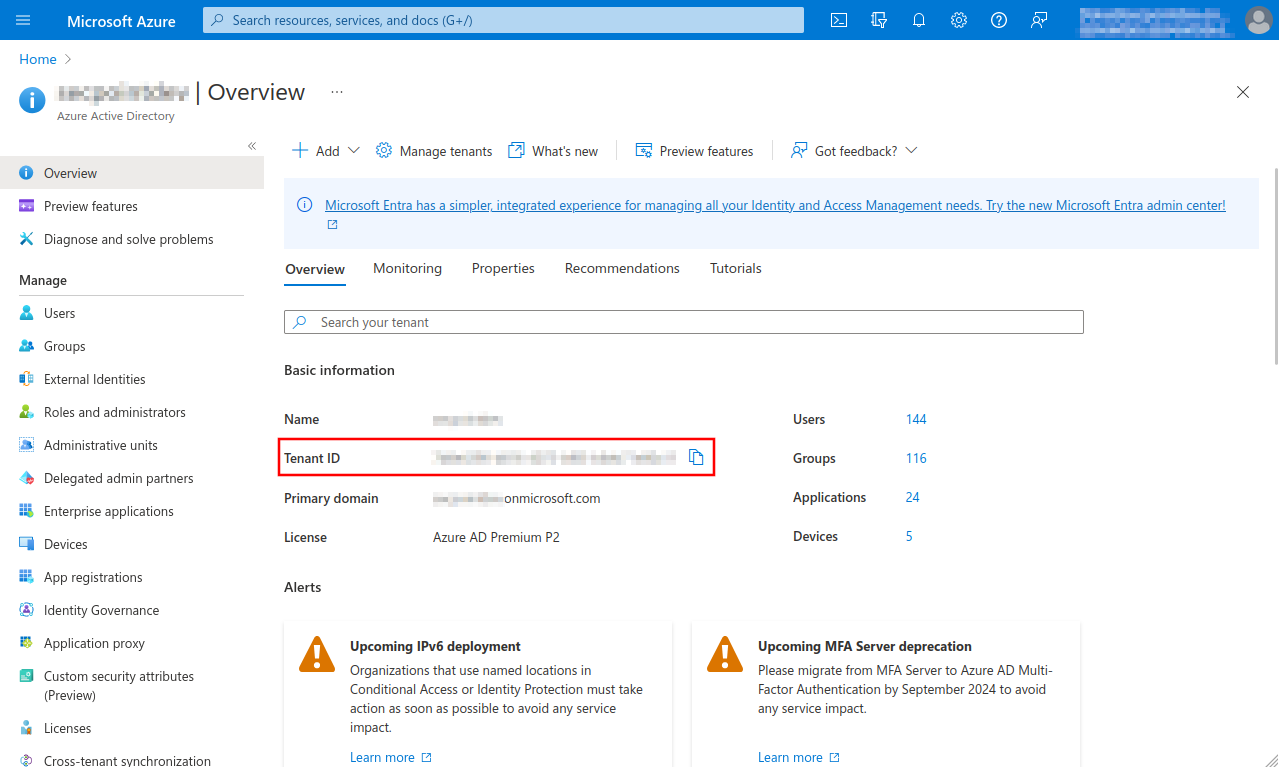 Fig.1
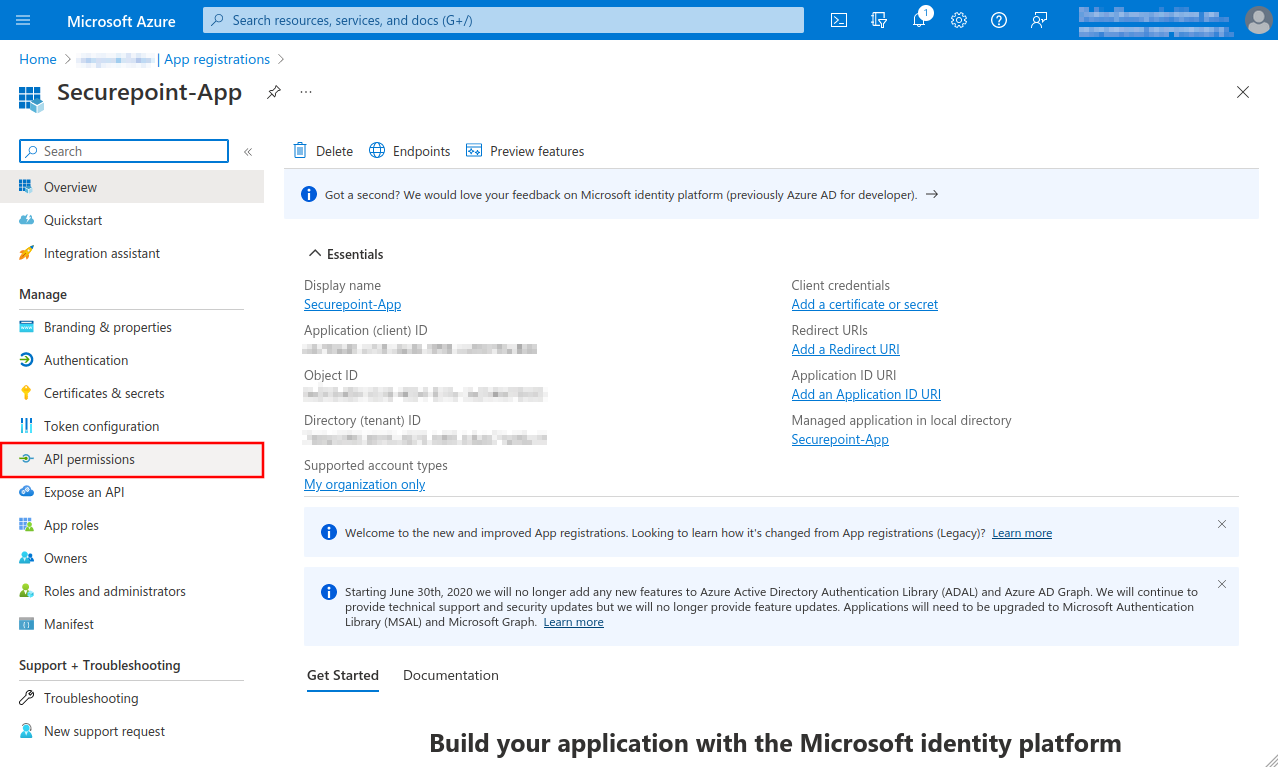 Fig.4 A summary of the newly registered app is displayed
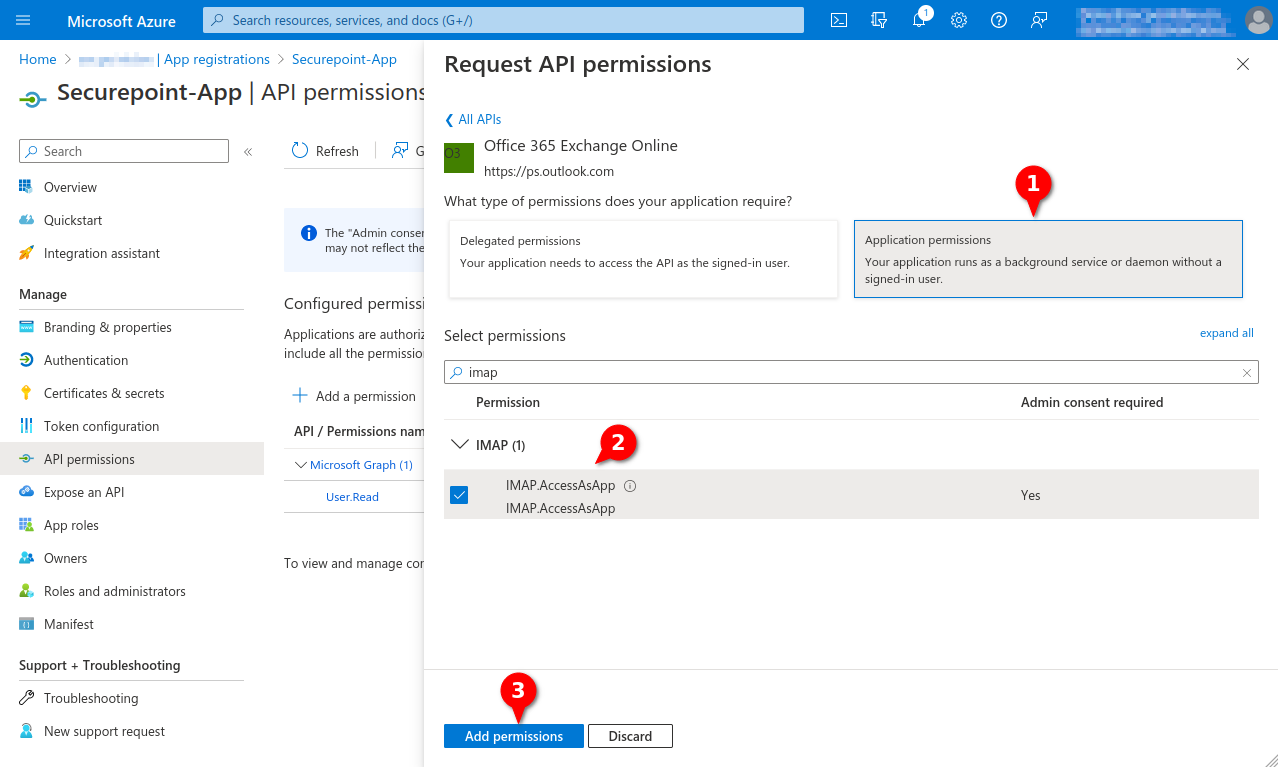 Fig.7
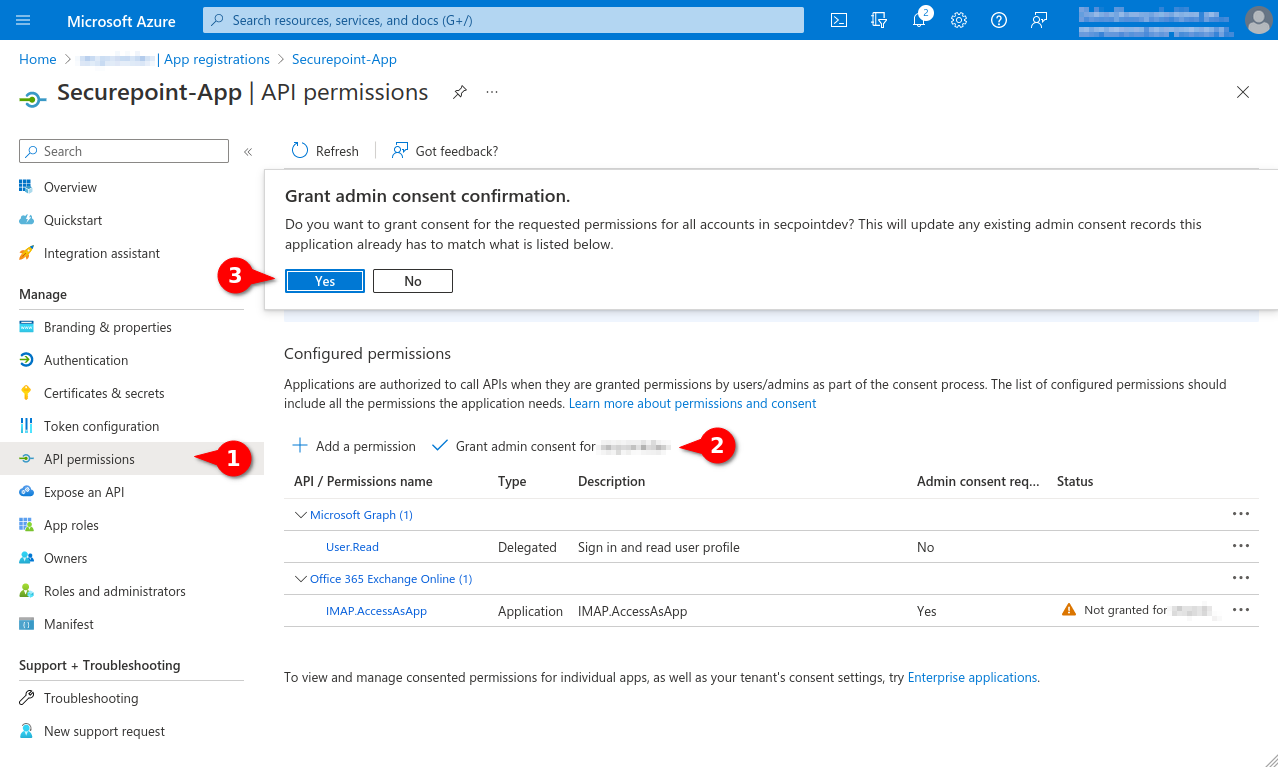 Fig.8
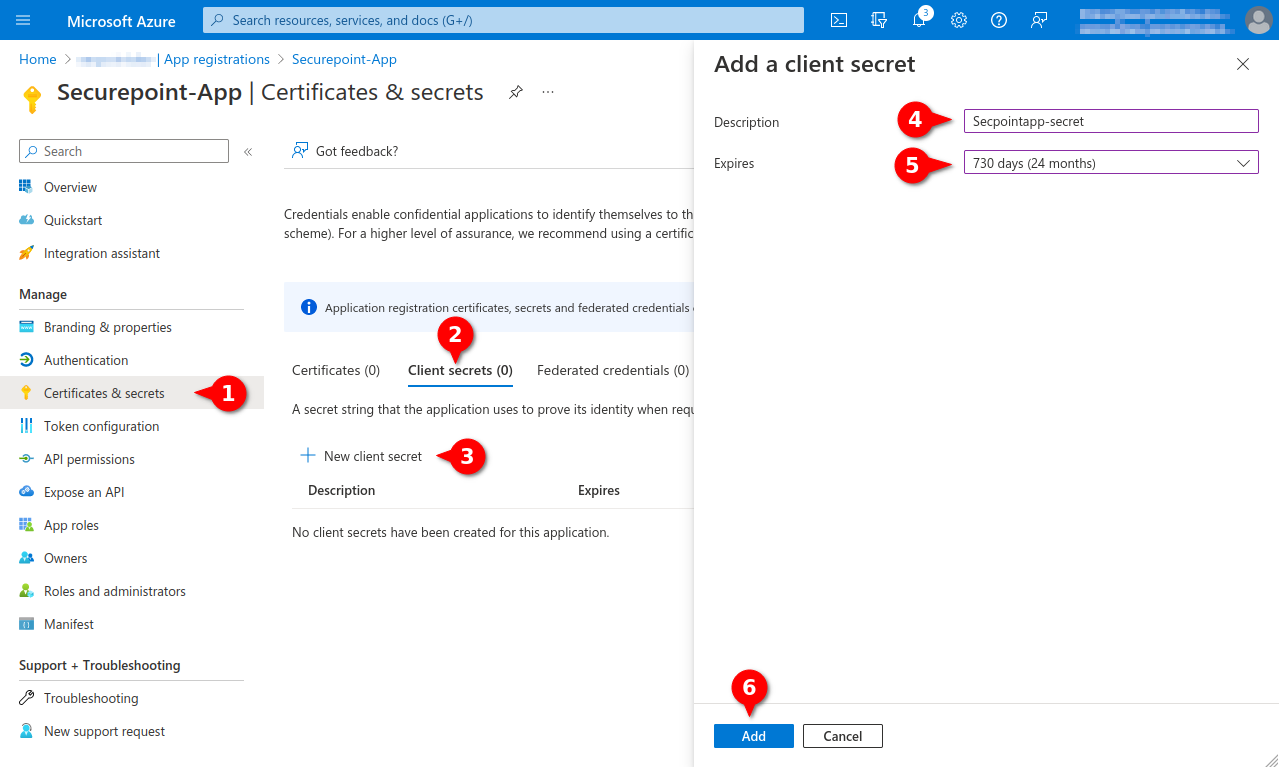 Fig.10
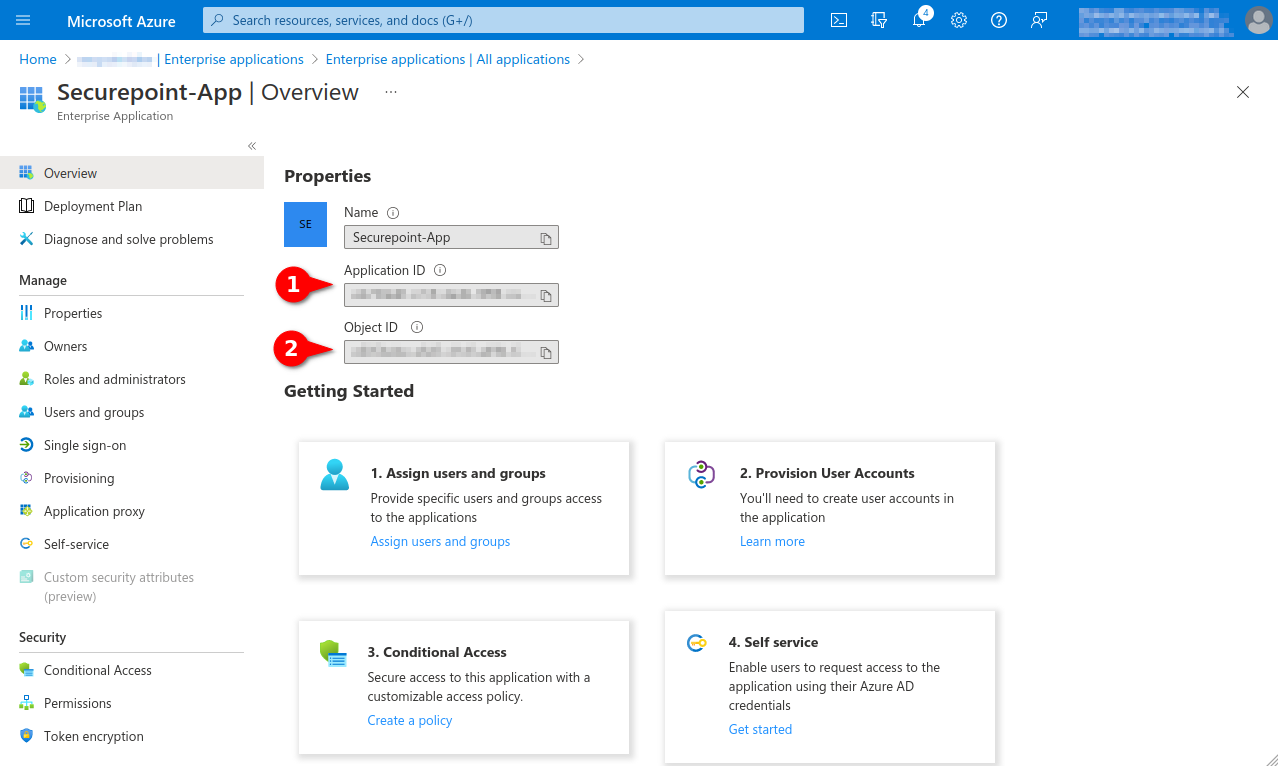 Fig.14 Note down from the app properties:
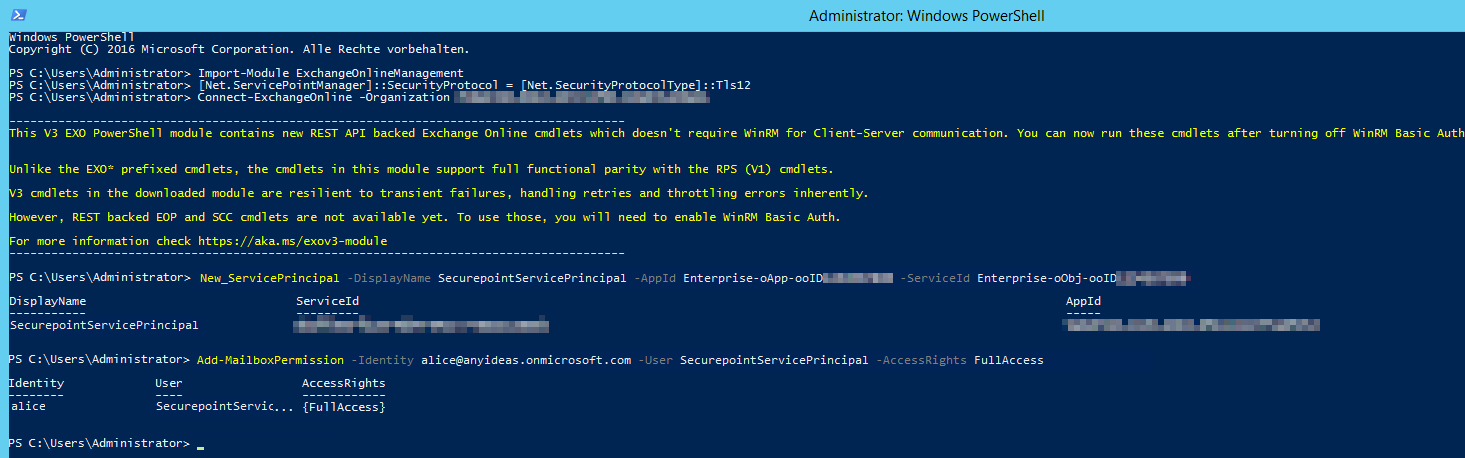 Fig.15
| |||
Microsoft 365 (Secret client key)Microsoft 365 (Secret client key) | |||
| Name: | Name of the OAuth 2 connection | 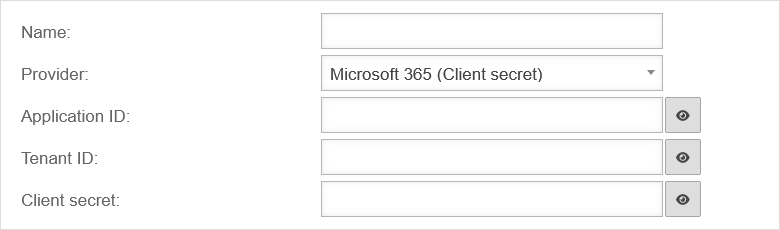 | |
| Provider: | Microsoft 365 (Secret client key) | Provider selection | |
| Application ID: | The application ID is entered In Microsoft Azure in the App property under Application ID | ||
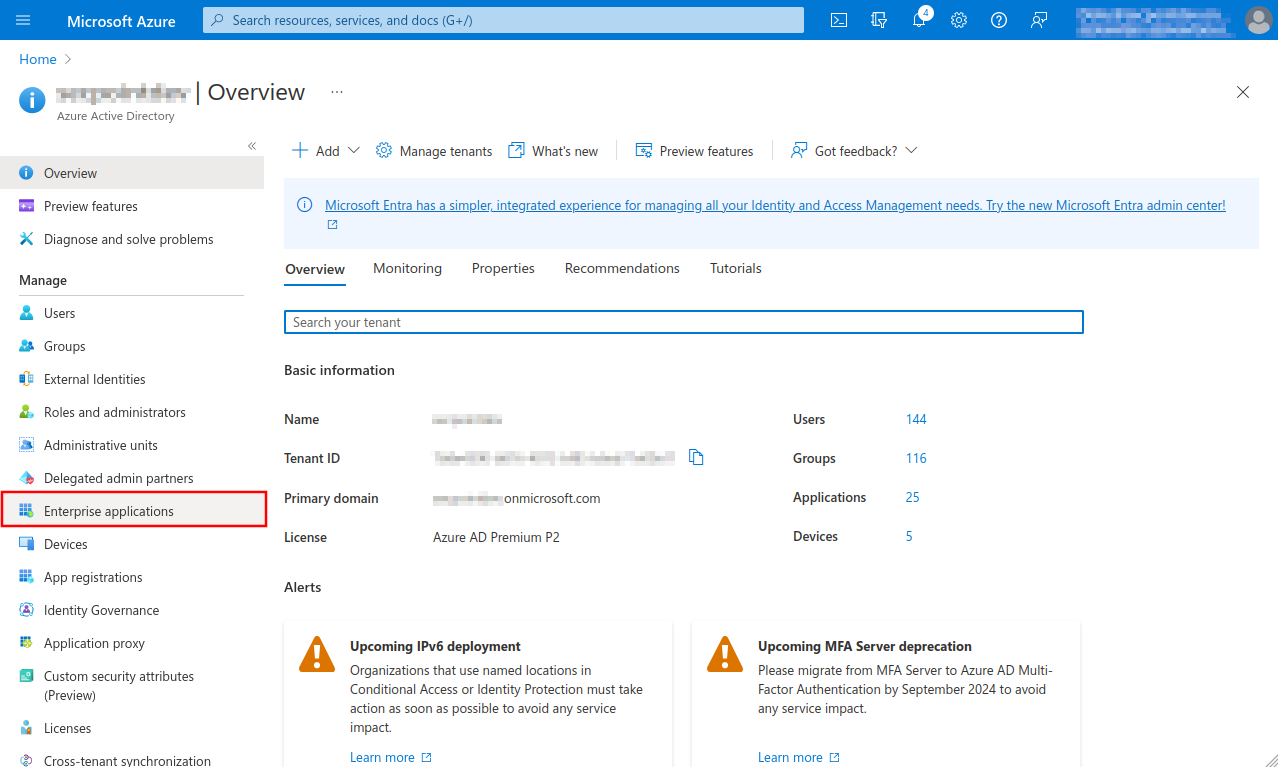
| Tenant ID: | The tenant's ID is entered In Microsoft Azure in the menu Azure Active Directory under Tenant ID | ||
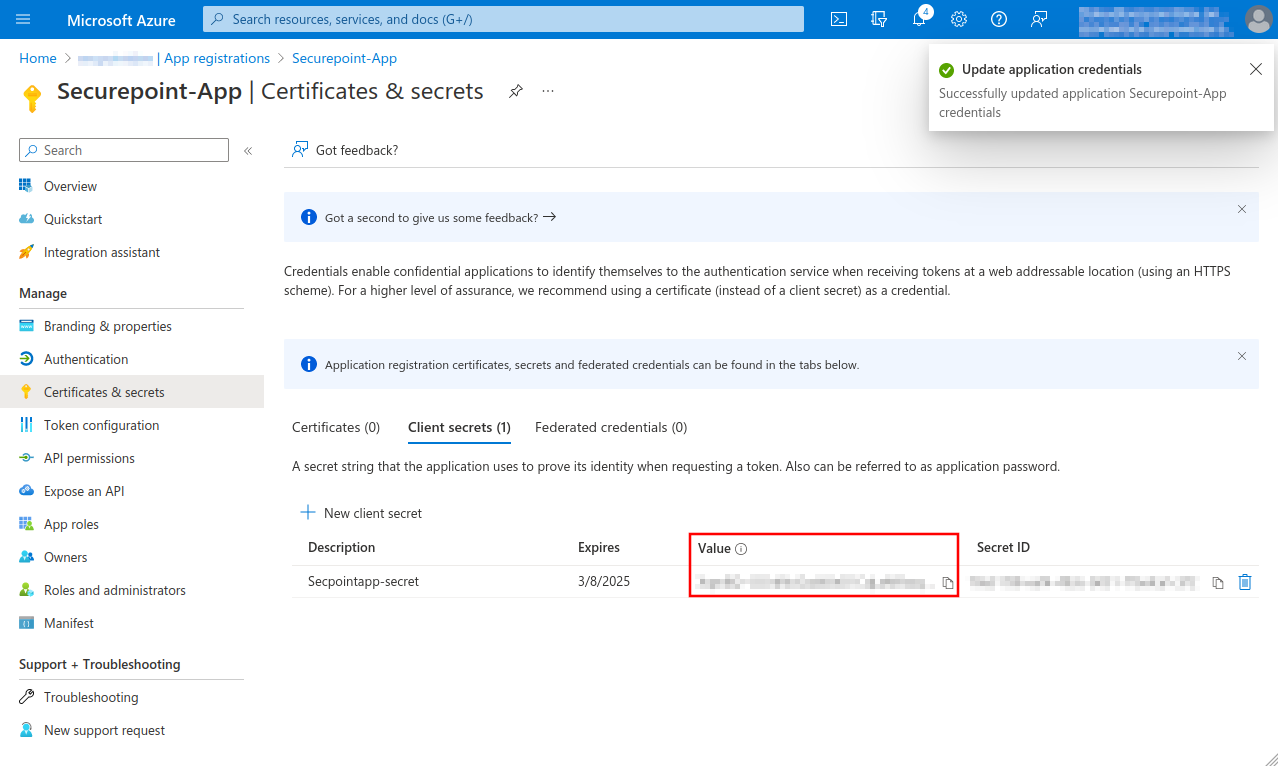
| Secret client key: | The secret client key is entered In Microsoft Azure in the menu Certificates & secrets in the tab Client secrets under Value | ||
Microsoft 365 (certificate) Microsoft 365 (certificate)
| |||
| Name: | Name of the OAuth 2 connection | 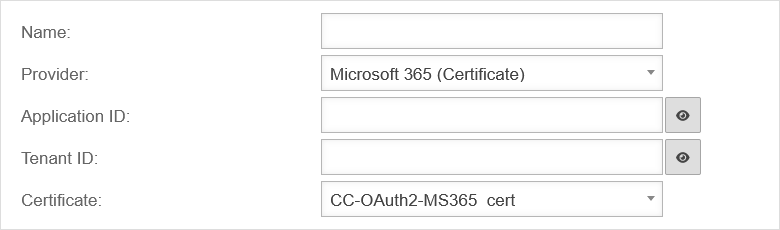 | |
| Provider: | Microsoft 365 (certificate) | Provider selection | |
| Application ID: | The application ID is entered In Microsoft Azure in the App property under Application ID | ||
| Tenant ID: | The tenant's ID is entered In Microsoft Azure in the menu Azure Active Directory under Tenant ID | ||
| Certificate: | CC-OAuth2-MS365_cert | The certificate that is uploaded in Azure is selected | |
GeneralGeneral | |||
| In the General ranch, the following settings can be made, effective for all Mail Connector services. | |||
| Interval (minutes): | 15 | The minute interval in which the external mail server is checked for new emails | UTMuser@firewall.name.fqdnApplications 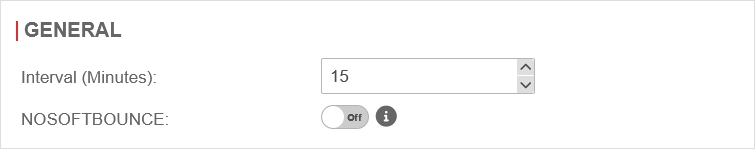
|
| NoSoftBounce: | Off | If enabled, no further delivery attempt is made for emails that generate a permanent forwarding error. These emails are deleted from the mailbox (if Keepmail is inactive) or marked as read (if Keepmail is active). | |