- Function: Update associated network objects
- Design update
Introduction
The GRE (=Generic Routing Encapsulation) protocol can be used to encapsulate other protocols and transport them via tunnels. It should be noted that the packets are not encrypted.
Possible use of the GRE protocol:
- For PPTP VPN
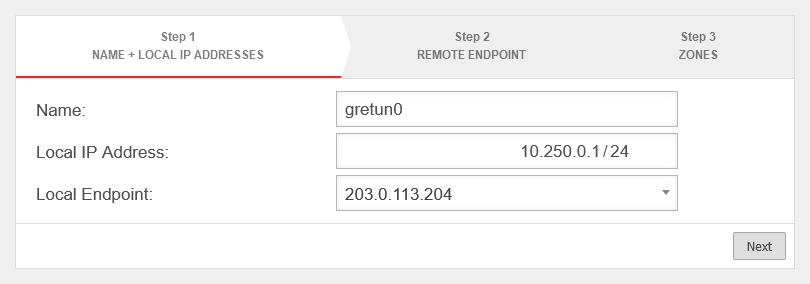
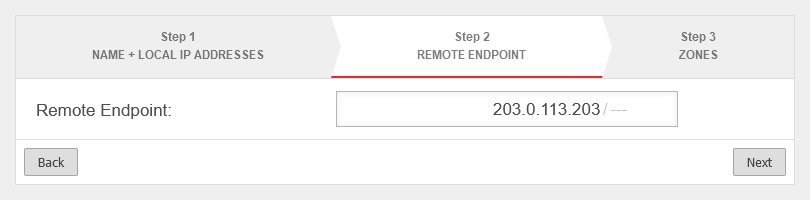
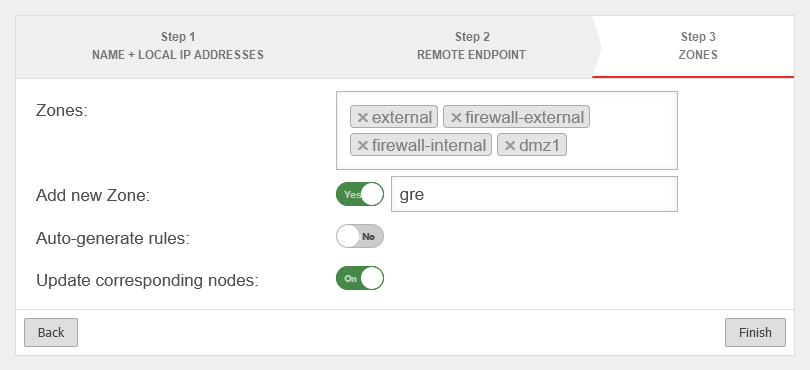
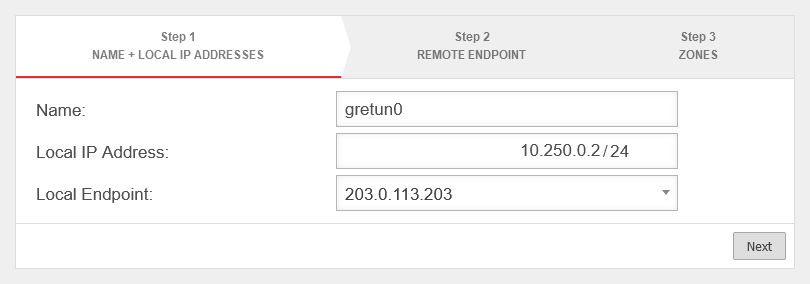
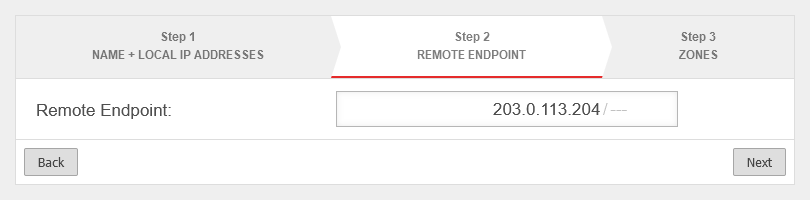
Create GRE tunnel
In this example, the firewall "Headquarters" has the IP address 198.51.100.75/24 on LAN1 and the remote site "Site-01" has the IP address 198.51.100.1/24 on LAN1.
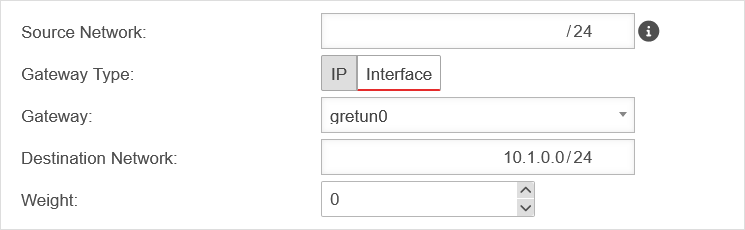
The local subnets are 10.0.0.0/24 for "Central" and 10.1.0.0/24 for "Site-01".
To establish this connection, a transfer network is still required, which in this example is 10.250.0.0/24.
Packet filter
Create firewall rule
The simple variant to connect the networks with each other is using the network objects of the entire networks and the any service.
The packet filter services should therefore be adapted to the application accordingly. In the test scenario, default-internet can be used, in which case the two packet filters look as follows:
| # | Source | Destination | Service | NAT | Task | Active | ||
| ACCEPT | On | |||||||
| ACCEPT | On | |||||||
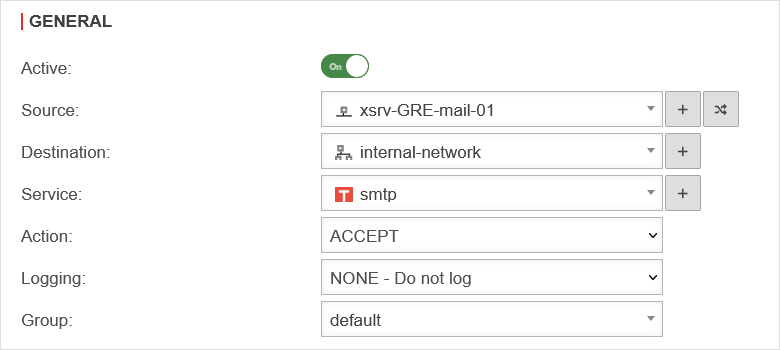
Create dedicated firewall rule
Of course, it is also advisable to work in a dedicated manner, i.e. to create individual network objects for each required connection and to enable only the required services in the port filter rule.
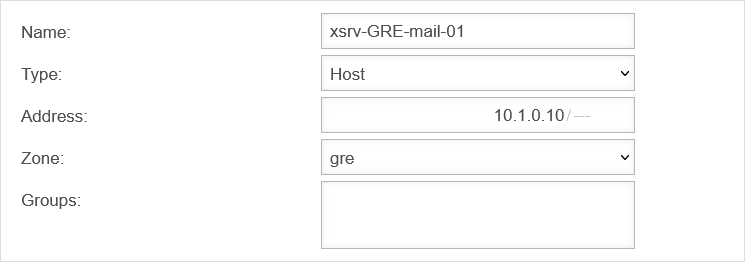
In this example, the mail server in "Site-01" is to be reached from the "Headquarters" network via "smtp". In addition, clients from the network of "Site-01" are to access the terminal server of the "Headquarters" via RDP.
- Open Area Network Objects
- Add a new object:
The following packet filter rules must then be added under Button :
| # | Source | Destination | Service | NAT | Task | Active | ||
| ACCEPT | On | |||||||
| ACCEPT | On | |||||||
Configuration of the remote terminal
On the remote UTM, the settings must be made in reverse.