- Layout adjustments
- Beispielszenario Grafiken ergänzt
Preliminary note
General
This HowTo explains what multipath routing is and how it can be set up on a Securepoint UTM. It also describes how traffic from specific services/end devices can be routed over a specific line.
What is multipath routing?
The combination of several Internet lines into one logical "Internet" is called multipath routing. Here, two or more default routes exist on the firewall and the packets are distributed accordingly. In addition to multipath routing, the Securepoint UTM also handles the distribution of data traffic (load balancing). In load balancing, a desired weighting can be entered for the individual routes. The Securepoint UTM can thus, for example, load two or more lines with a respective bandwidth of e.g. 16 MBit/s and 100 MBit/s equally.
Set-up
This manual explains two typical set-up options. One is multipath routing with two directly connected DSL lines (Scenario I) and the other is with one DSL line and one router connection (Scenario 2).
Example scenario 1
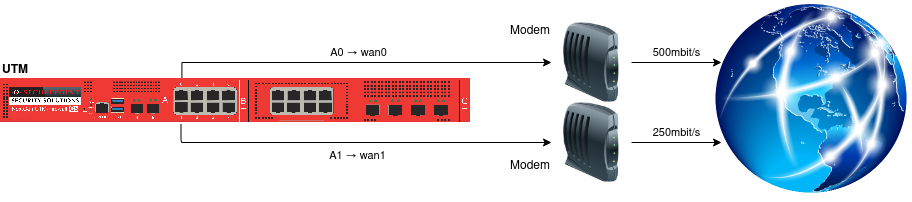
Two DSL lines are connected to the Securepoint UTM (wan0 and wan1). Line 1 (wan0) has a bandwidth of 500 MBit/s and line 2 (wan1) has a bandwidth of 250 MBit/s.
Example scenario 2
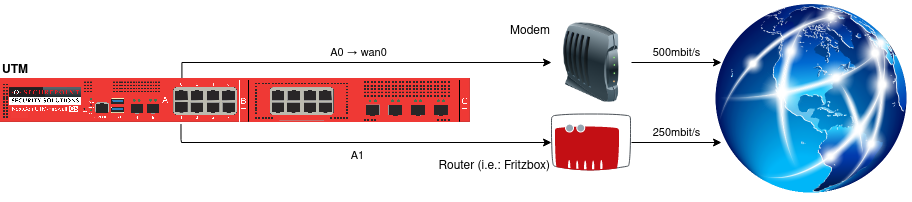
A modem is connected to LAN0 of the firewall, with the Securepoint UTM taking over dialing in. A Fritzbox, which acts as a router, is connected to LAN2. Line 1 (wan0) has a bandwidth of 500 MBit/s and line 2 (LAN2) has a bandwidth of 250 MBit/s.
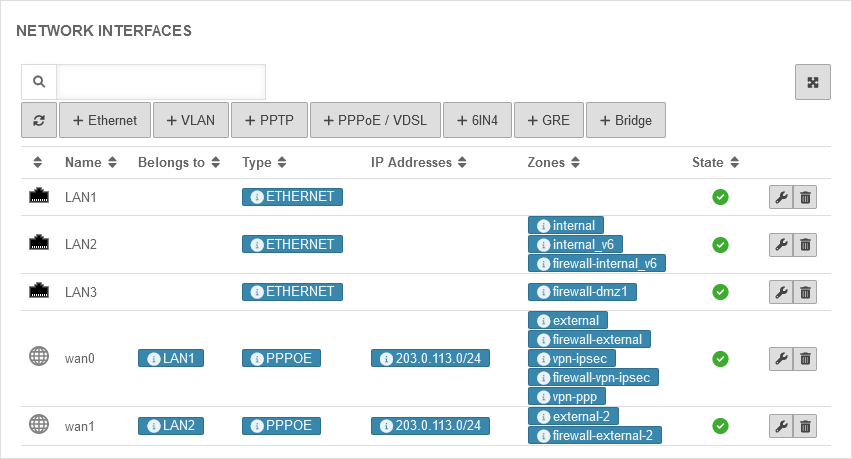
Zones Scenario 2, Step 1 - Zones
| |||||||||||||||||||||||||||||
|
The external interfaces (wan0 and LAN2) are configured so that both have unique zones. In this example, the zones "external-2" and "firewall-external-2" are also created and assigned to LAN2. The wan0 has the zones "external" and "firewall-external". The zones are necessary so that corresponding network objects and rules can be created later. | |||||||||||||||||||||||||||||
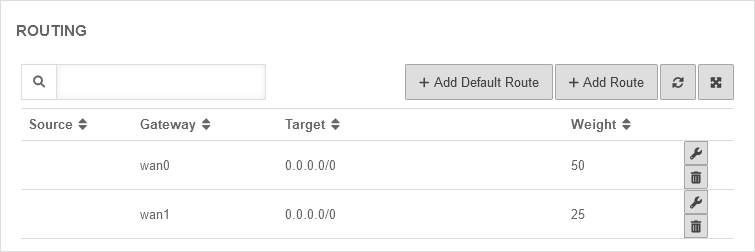
Routes Scenario 2, Step 2 - Routes
| |||||||||||||||||||||||||||||
|
In order for the data traffic to be send over both lines, a default route is required for each line. In this scenario, however, there is a special feature due to the router in front of the LAN2: | |||||||||||||||||||||||||||||
| MTU: | 1500 | Default | UTMuser@firewall.name.fqdnNetworkNetwork configuration 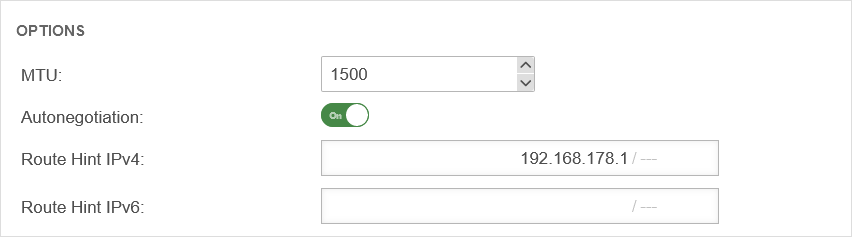 Route-Hint-Settings LAN2 Route-Hint-Settings LAN2
| ||||||||||||||||||||||||||
| Autonegotion: | On | Must be activated | |||||||||||||||||||||||||||
| Route Hint IPv4: | Specify the IPv4 address here | ||||||||||||||||||||||||||||
| Route Hint IPv6: | If available, enter the IPv6 address here | ||||||||||||||||||||||||||||
| Now the two default routes must be created. Since the lines have different bandwidths (500 MBit/s and 250 MBit/s respectively), the Weighting option can be used to achieve an even load on the lines. | UTMuser@firewall.name.fqdnNetwork 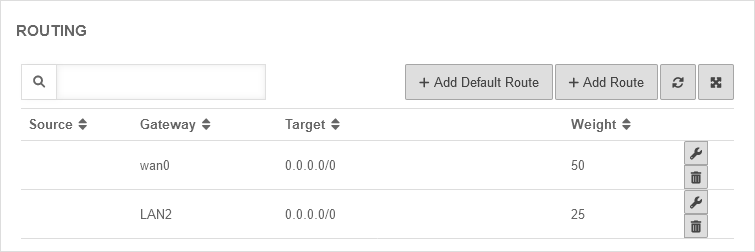 Created default routes Created default routes
| ||||||||||||||||||||||||||||
Create network objects Scenario 2, Step 3 - Create network objects
| |||||||||||||||||||||||||||||
| Rules are created in Securepoint UTM using network objects under Button . Since there is no network object for a second line by default, it must now be created. On the one hand we need the network object for the network (Internet-2) and on the other hand the network object for the interface of the firewall in this zone (external-interface-2).
| |||||||||||||||||||||||||||||
| Name: | Internet-2 | Choose a name | UTMuser@firewall.name.fqdnFirewallNetzwerkobjekte 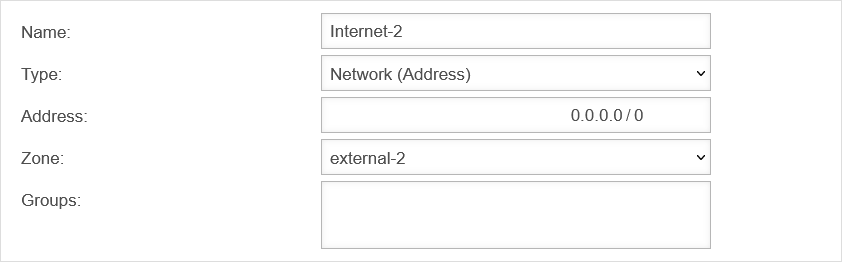 Internet-2-Object Internet-2-Object
| ||||||||||||||||||||||||||
| Type: | Select types in the drop-down menu | ||||||||||||||||||||||||||||
| Address: | 0.0.0.0/0 | Network IP for the entire internet | |||||||||||||||||||||||||||
| Zone: | Select created zone | ||||||||||||||||||||||||||||
| Groups: | |||||||||||||||||||||||||||||
| Name: | external-interface-2 | Choose a name | UTMuser@firewall.name.fqdnFirewallNetzwerkobjekte 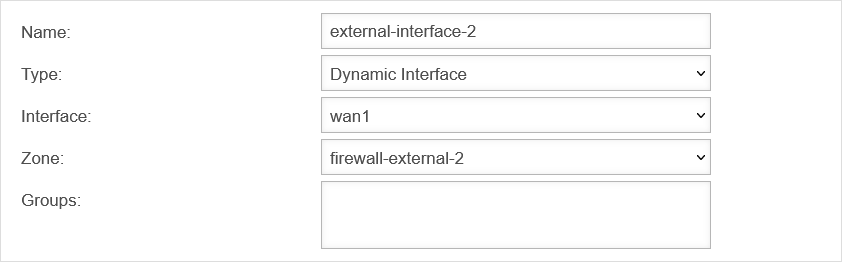 external-interface-2-Object external-interface-2-Object
| ||||||||||||||||||||||||||
| Type: | Select types in the drop-down menu | ||||||||||||||||||||||||||||
| Interface: | Select Wan1 as interface | ||||||||||||||||||||||||||||
| Zone: | Select created zone | ||||||||||||||||||||||||||||
| Groups: | |||||||||||||||||||||||||||||
Create rule Scenario 2, Step 4 - Create rules
| |||||||||||||||||||||||||||||
| Now the rules are created. In this example, "default-internet" must be released to the Internet. Here it must be ensured that the Internet object matches the selected HideNAT object as a rule! The rules will then look like this: |
UTMuser@firewall.name.fqdnFirewallPaketfilter 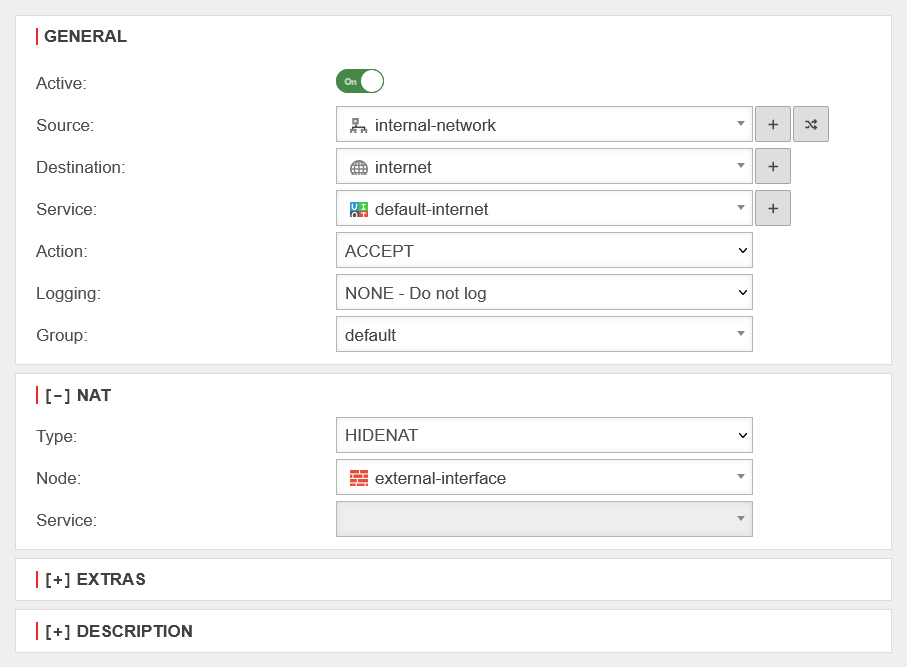 Rules in the packet filter Rules in the packet filter
| ||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||
Routing for specific end devices and services | |||||||||||||||||||||||||||||||||||||||
|
Since data traffic always "jumps" from line to line in multipath routing, this can lead to errors in certain scenarios. For example, an external server must always be addressed via the same source IP. To implement this, the "rule routing" function is used. As an example, the SBS with the IP 203.0.113.203 should always be sent via the line wan0. | |||||||||||||||||||||||||||||||||||||||
Network object for the server Step 1 - Network object for the server
| |||||||||||||||||||||||||||||||||||||||
|
First, a network object is created for the server so that it can be specified later in the rule. | |||||||||||||||||||||||||||||||||||||||
| Name: | Server | Choose a name | UTMuser@firewall.name.fqdnFirewallNetzwerkobjekte 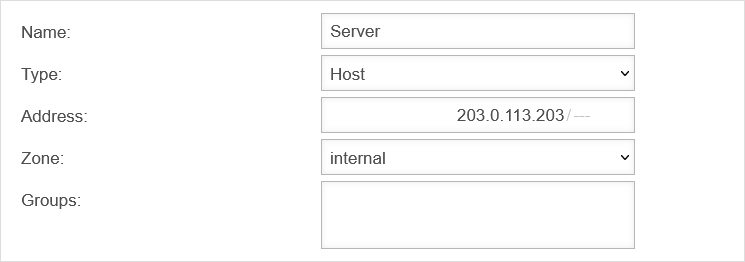 SBS-Netzwerk object SBS-Netzwerk object
| ||||||||||||||||||||||||||||||||||||
| Type: | Select the type host | ||||||||||||||||||||||||||||||||||||||
| Address: | Specify IP address | ||||||||||||||||||||||||||||||||||||||
| Zone: | Select "internal" as zone | ||||||||||||||||||||||||||||||||||||||
| Gruppen: | |||||||||||||||||||||||||||||||||||||||
Create rule Step 2 - Create rule
| |||||||||||||||||||||||||||||||||||||||
| Now a rule can be defined with the network object. In the rule, the rule routing must then be specified and set to wan0 so that the server always communicates to the outside via this interface.
notempty It is imperative that the destination network object (Internet) matches the HideNAT object (external-interface) and the rule routing interface (wan0)! Otherwise the rule routing will not work.
| |||||||||||||||||||||||||||||||||||||||
| Active: | On | The rule must be active | UTMuser@firewall.name.fqdnFirewallPaketfilter 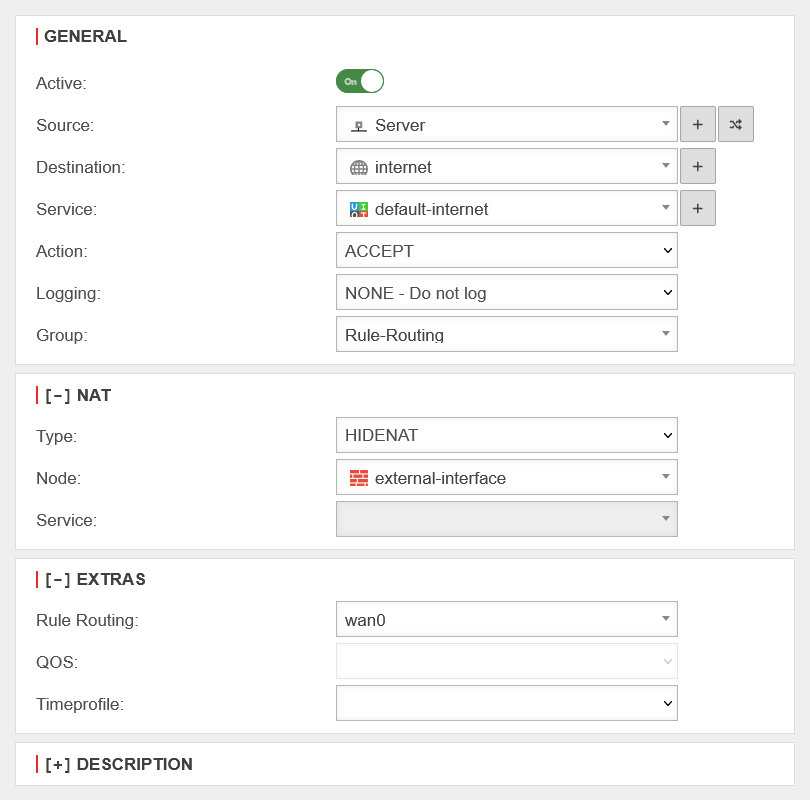 Rule-Routing-Rules Rule-Routing-Rules
| ||||||||||||||||||||||||||||||||||||
| Source: | Select server | ||||||||||||||||||||||||||||||||||||||
| Destination: | Specify the "Internet" as the destination | ||||||||||||||||||||||||||||||||||||||
| Service: | default-internet | choose "default-internet" | |||||||||||||||||||||||||||||||||||||
| Action: | Choose "Accept" | ||||||||||||||||||||||||||||||||||||||
| Groups: | Choose "Rule-Routing" | ||||||||||||||||||||||||||||||||||||||
NAT
| |||||||||||||||||||||||||||||||||||||||
| Type: | Must select | ||||||||||||||||||||||||||||||||||||||
| Network object (Node): | Choose "external-interface" | ||||||||||||||||||||||||||||||||||||||
| Service: | |||||||||||||||||||||||||||||||||||||||
Extras
| |||||||||||||||||||||||||||||||||||||||
| Rule Routing: | wan0 | Specify interface | |||||||||||||||||||||||||||||||||||||
| QOS: | |||||||||||||||||||||||||||||||||||||||
| Time profile: | |||||||||||||||||||||||||||||||||||||||
| Click here to add a rule | |||||||||||||||||||||||||||||||||||||||
Rule positioning Step 3 - Rule positioning
| |||||||||||||||||||||||||||||||||||||||
Since the ruleset in the Securepoint UTM is processed from top to bottom, it is essential that the rule routing rule comes before the "global" rule. To be on the safe side, it is best to create a new rule group that is positioned at the top of the port filter. All rule routing rules are then created in this rule group and thus take effect first.
| |||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||
| Rule routing can of course also "route" individual services, such as HTTP, over a specific line. The rule must then be adapted accordingly. | |||||||||||||||||||||||||||||||||||||||