This description is based on the status of the Microsoft 365 Portal in June 2023. Changes to the user interface on the part of Microsoft are possible at any time and must be taken into account accordingly in the implementation.
All information without warranty.
Configure Microsoft 365 Defender for Phishing Simulation
New article: 06.2023
notempty
This article refers to a Resellerpreview
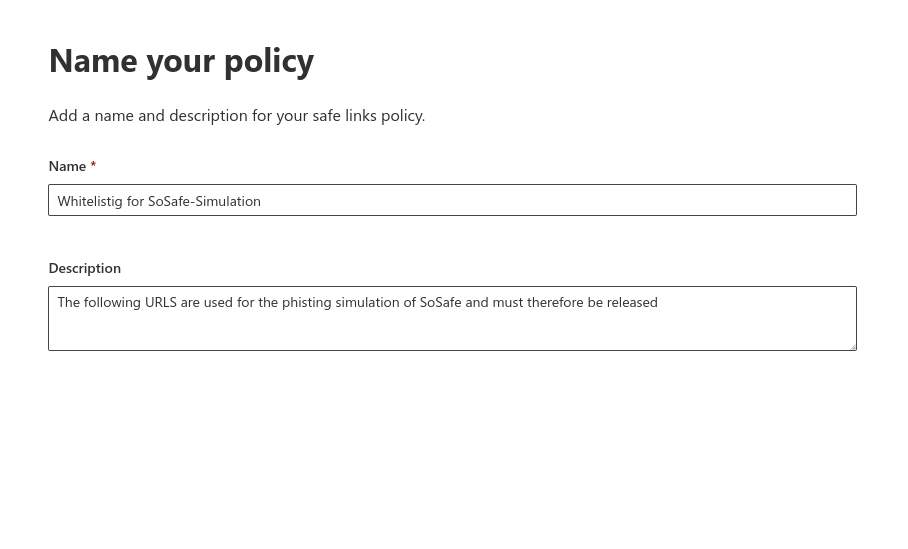
Whitelisting
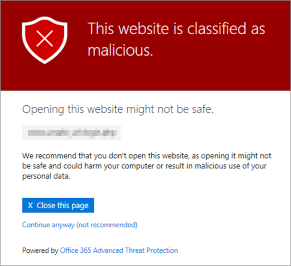
To ensure that the simulated phishing emails of the Awareness PLUS training are not blocked by the Microsoft mail server or Microsoft Defender, whitelisting must be configured at various points.
The domains used in the phishing simulation can be stored in Microsoft 365 Defender (formerly Advanced Threat Protection - ATP) so that no warning message is displayed.
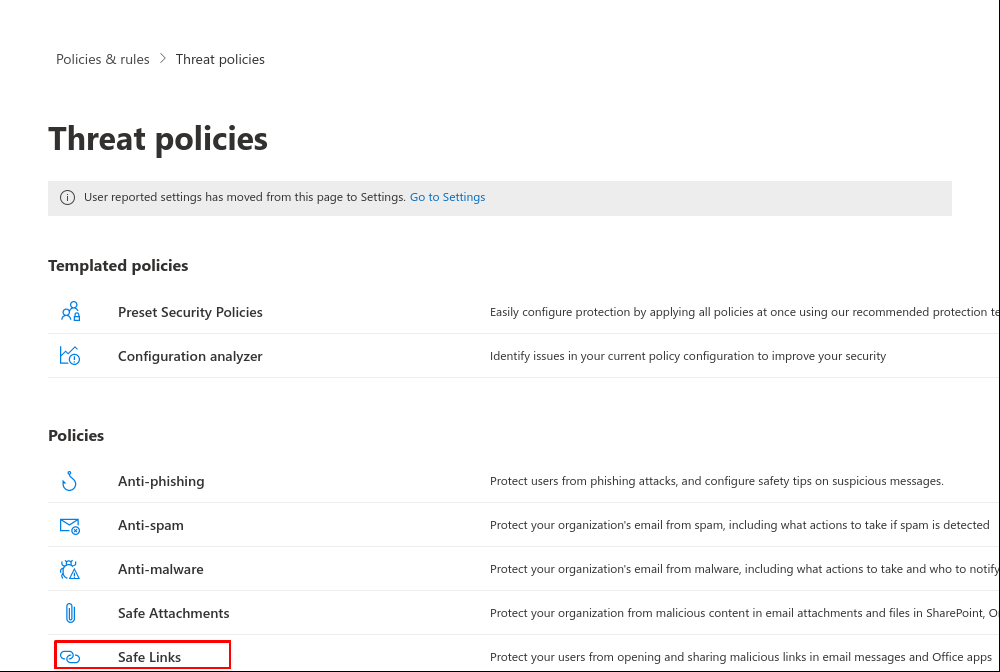
Set up secure links in Microsoft 365 Defender

Fig.1
- Login to Microsoft
- Select menu Security
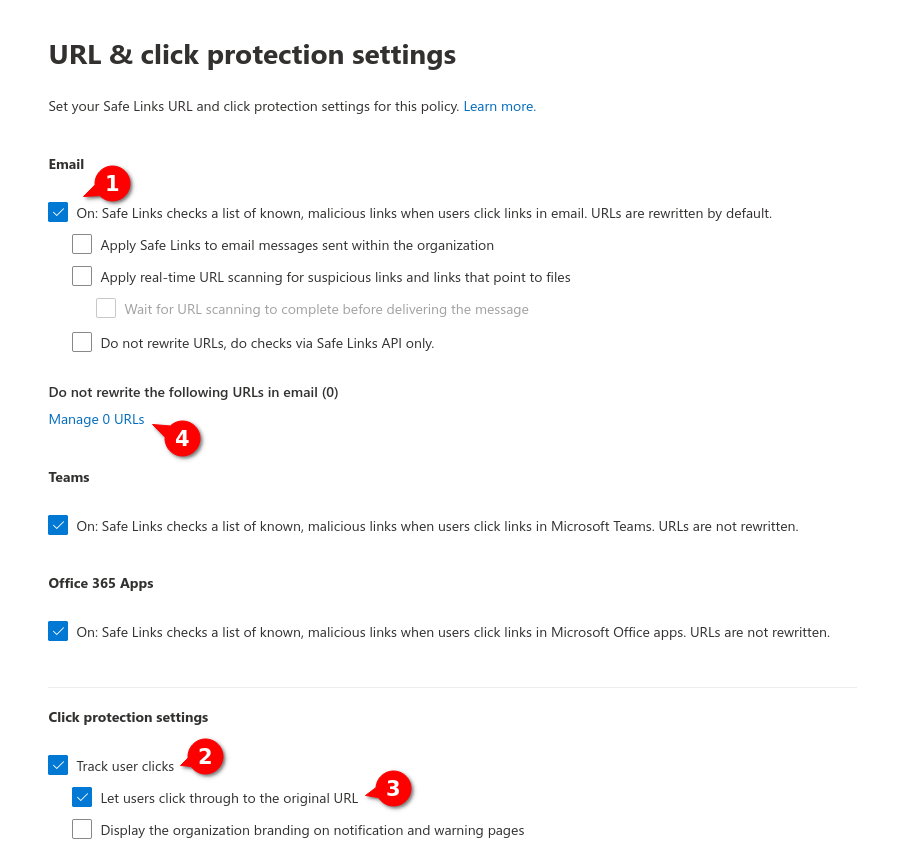
Fig.7
- Selects that URLs can be rewritten
- User clicks should be trackable
- Users should be able to click through to the original URL
- Click on Manage 0 URLs
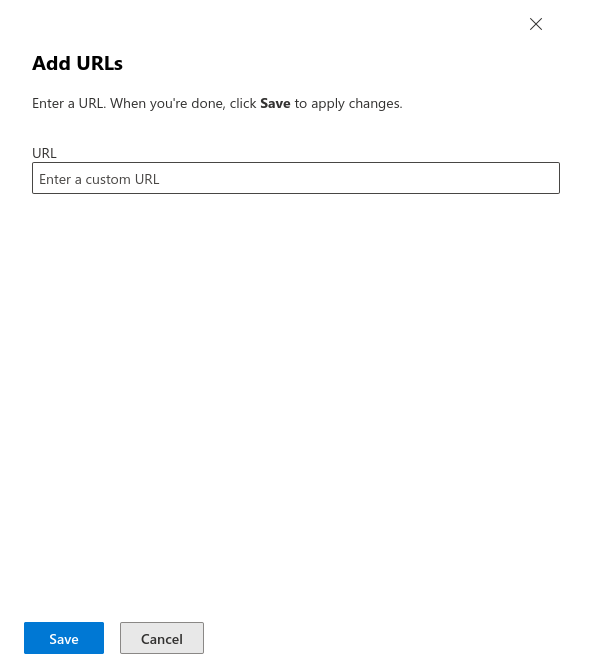
Fig.9
Enter URLs that are located under "Simulation" → "Whitelisting" → "List of used domains in phishing links". Keep to the format https://domain/*.