notempty
- Terms corrected: Instead of Domain Forwarding, the term DNS Forwarding is used.
- Special case configuration: Safe Search with external DHCP server (02.2023)
Introduction
Name resolution is the procedure that allows names of computers or services to be resolved into an address (IP) (e.g.: support.securepoint.de in 85.209.185.22). The UTM can forward a name resolution to another name server or find a specific name for an IP address (reverse lookup).
Additionally there is the function DNS forwarding, which allows to forward all DNS requests to a specific name server.
The network tools article provides an overview of the data that is managed in a name server.
DNS Forwarding
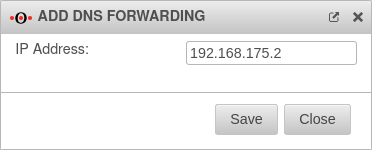
A DNS forwarding is used to forward all DNS requests made to the firewall's name server to another IP.
Add DNS Forwarding
Domain forwarding through a VPN tunnel
Sometimes it is necessary to forward internal domain requests to a remote name server located in a VPN.
It should be noted here that, by default, all direct requests addressed to external name servers are sent from the firewall with the external IP. However, a public IP is not routed into a VPN tunnel.
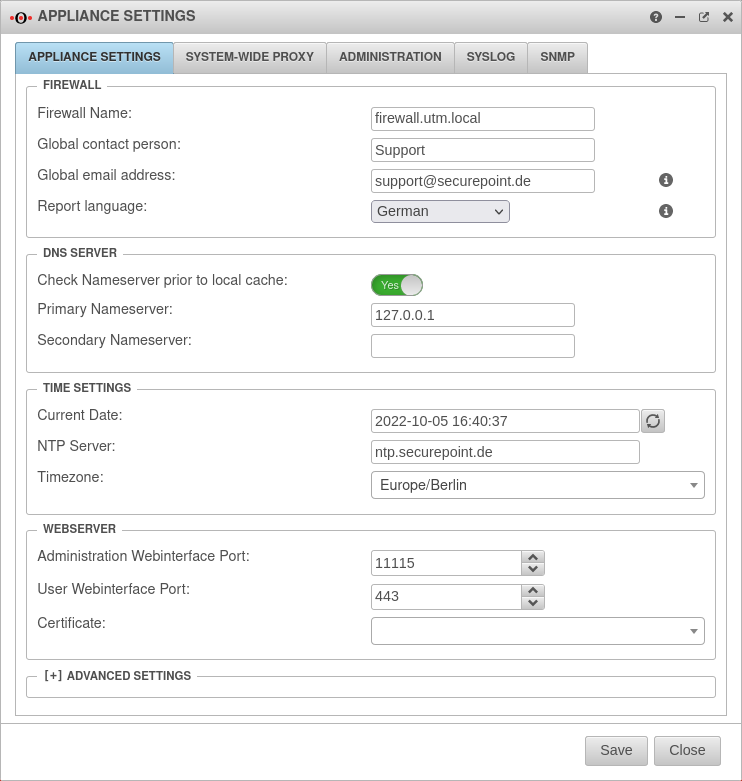
Set the name server of the firewall
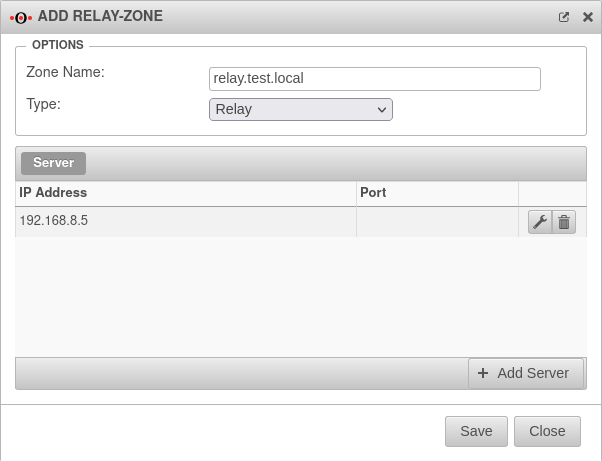
Create relay
Menü Button
The changes in the zone must also be saved by clicking the button.
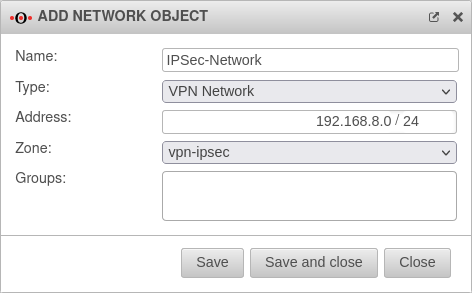
Create network object
From the Tab Network Objects navigation bar, the network object is created under . A network object must be created for the IPSec network.
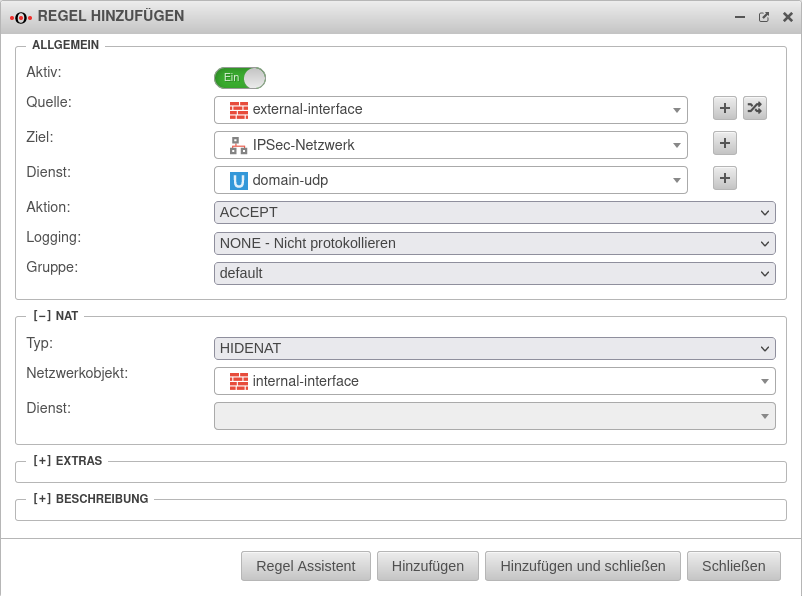
Create rule
In the last step, a firewall rule with a Hide NAT must be created. This causes the DNS forwarding to also go into the tunnel, and not directly into the Internet. From the navigation bar, the application is selected and a rule can be added under .
The entry can be saved by clicking the button.
The port filter must be updated via the button.
With this rule, all domain UDP requests made through the firewall to the remote name server are now nated over the IP of the internal interface and can thus be routed into the IPSec tunnel.
Safe Search with external DHCP server
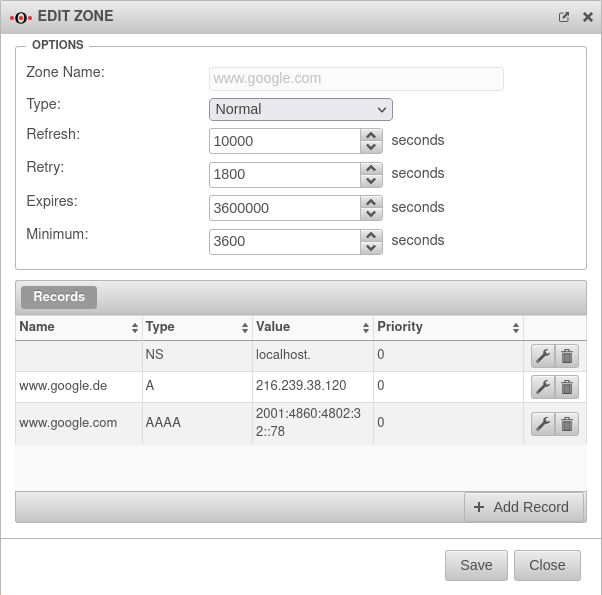
If an external DHCP server is used, the active web filter Safe Search often does not work for search engines, especially Google, when searching for images.
In order for this web filter to take effect there as well, the following forward zones must be set up for all ccTLDs (see https://www.google.com/supported_domains : www.google.de, www.google.ch, ...). From the navigation bar, use to add a forward zone: