notempty
notempty
notempty Dieser Artikel bezieht sich auf eine nicht mehr aktuelle Version!
notempty
Der Artikel für die neueste Version steht hier
Zu diesem Artikel gibt es bereits eine neuere Version, die sich allerdings auf eine Reseller-Preview bezieht
Configuration of the SSL interception in the HTTP proxy
Last adaptation to the version: 12.5.2
New:
- SNI validation without webfilter
Part of the HTTP-Proxy
SSL-Interception
SSL-Interception
| Caption | Value | Description | 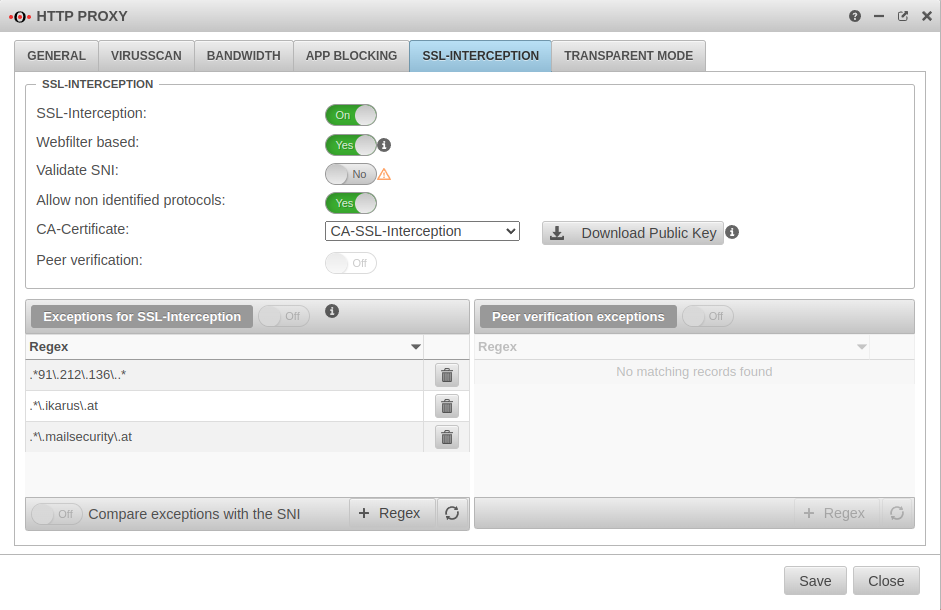 |
|---|---|---|---|
| SSL-Interception: | On | Activates the SSL interception |  |
| Webfilter based: | No | When enabled, only connections blocked by the web filter are intercepted. This avoids the problem that there are sites that do not tolerate an interruption of the encryption (e.g. banking software) without having to define an exception for it. | |
| Validate SNI Only available when "Webfilter-based" is active. |
No | Bei Aktivierung Yes wird eine sich ggf. im ClientHello des TLS-Handshake befindliche SNI geprüft. Dabei wird der enthaltene Hostname aufgelöst und die Adressen im Ergebnis mit der Zieladresse des abgefangenen Requests abgeglichen. | |
| SNI in den Ausnahmen validieren:notempty New as of v12.5.2 Nur verfügbar, wenn Webfilter basiert nicht aktiv ist |
No | Wendet die Server Name Indication Validierung nur auf aktivierte Yes Ausnahmen für SSL-Interception an | |
| Allow non identified protocols: | Yes | If this switch is deactivated, unrecognized protocols are blocked | |
| CA-Certificate: | Here, a CA must be selected that can re-encrypt the connection after decryption (and scanning). The public key of the CA must be installed on all client computers that are to use SSL Interception. Download can be done here directly with ⬇Download public key . | ||
| The public key should be installed on the clients that are going to use SSL interception to avoid certificate errors. | |||
| Peer verification: | Off | This should definitely be enabled With this, the HTTP proxy checks whether the certificate of the called page is trustworthy. Since the browser only sees the local certificate, a check by the browser is no longer possible. | |
| Exceptions for SSL-Interception | On | It is possible to define exceptions in the format of Regular Expressions. However, since only https can arrive here, it is not filtered for protocols, unlike the virus scanner. With new exceptions are added. So an exception for www.securepoint.de would be:
.*\.securepoint\.de" | |
| Peer verification exceptions | Aus | Here exceptions for certificate verification in regex format can be added. |