notempty
Encryption Algorithms of the UTM
Last adaptation to the version: 11.8.2
- New:
- Article adaptation
- Layout changes
- DH Key-Size 1024 removed ( now considered as unsafe)
Previous versions: 11.6
Introduction
In this menu you define the encryption protocol that is used to address the applications on the UTM. The basic settings selected by Securepoint are currently considered secure and have been tested for compatibility.
If a higher level of protection is required, the settings can be changed in the menu (jargon: harden).
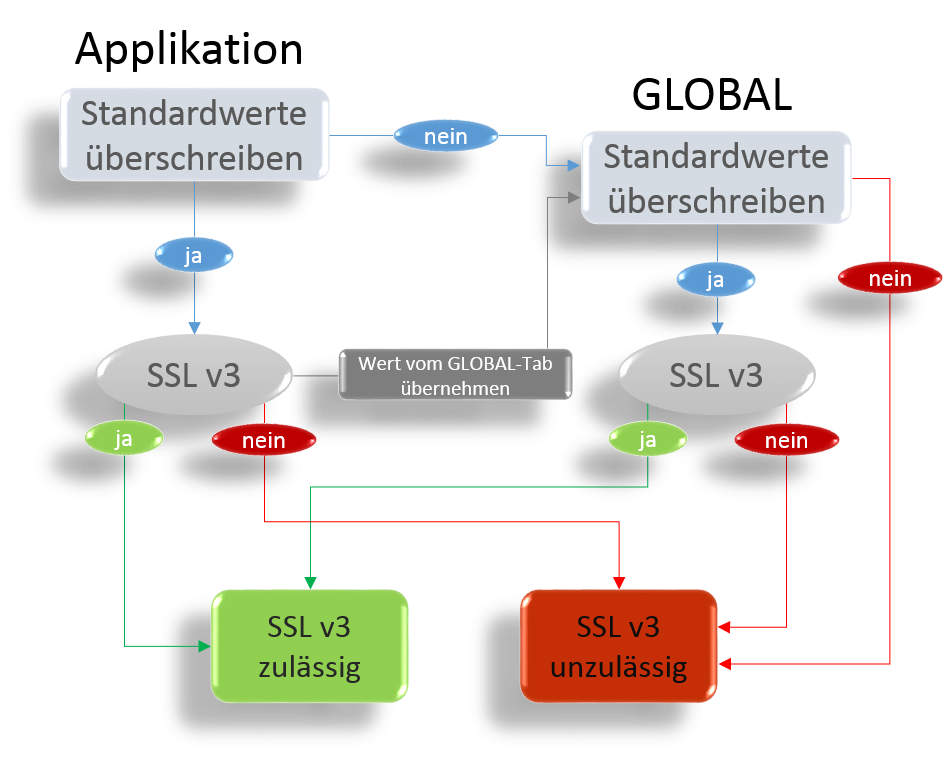
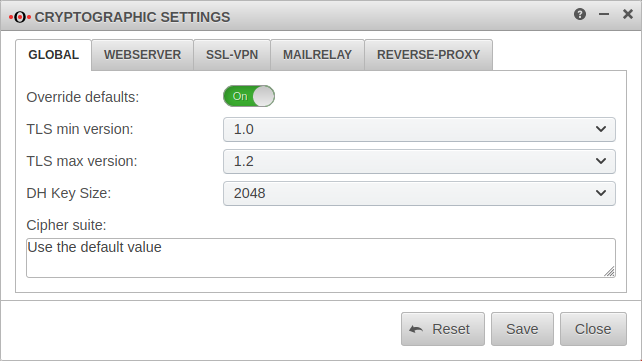
- The tab Global displays the basic settings.
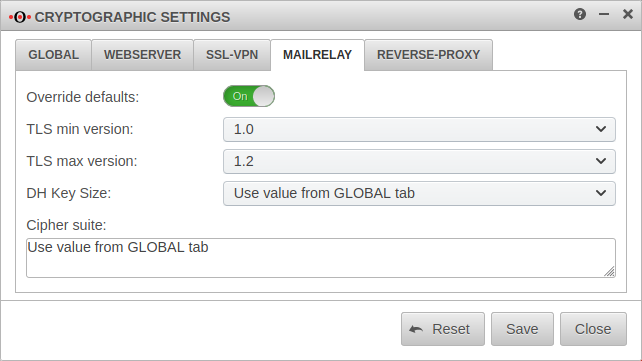
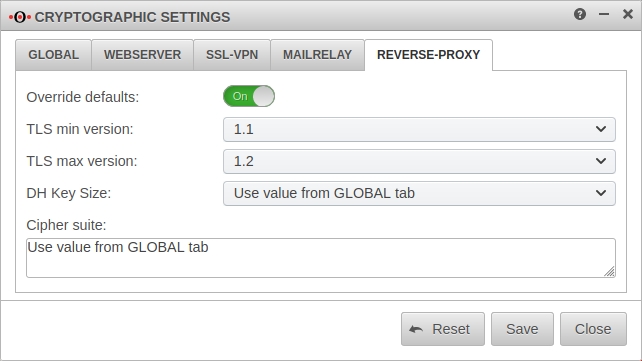
- With Overwrite default values: these values for all applications can be overwritten.
- The default values or
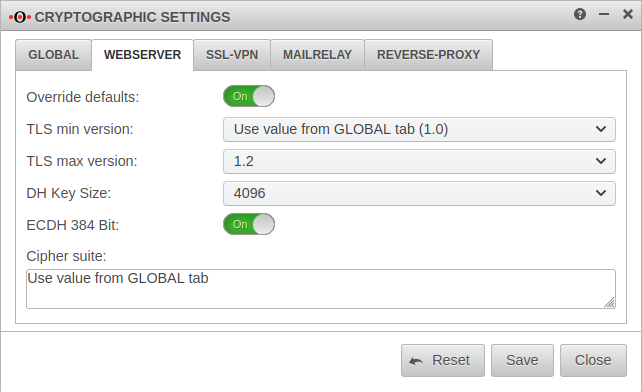
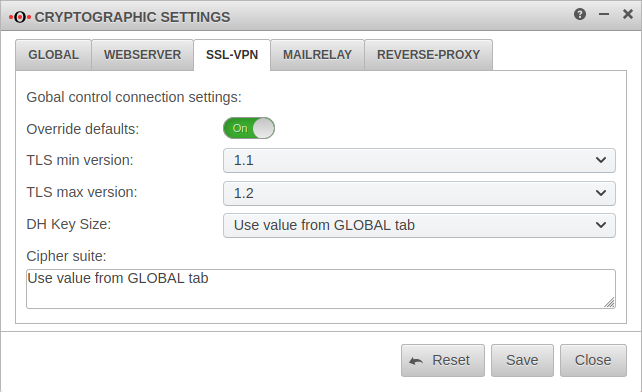
- The changes made in the Global tab can in turn be overwritten separately for each application.
- The settings in the application menus can (partially) apply the global values by selecting .
The graph on the right shows the dependency on the settings of an application for Global Setting using the SSL v3 protocol.
Cryptographic settings
The settings are made in the menu
Save / Restore
The button resets the settings in the currently opened area to the global values. If Overwrite default values is deactivated again, the settings in the currently opened area are reset to the default values of the individual application.
Changing the default settings may result in not all target systems being available for all users. For example, if they use older clients or web browsers that do not support the required encryption.
The services are restarted when the new settings are saved. This results in the web server requiring the administrator and/or user of the UTM web interface to log on again.
CLI
The settings that are made in the web interface are visible on the Command Line Interface using the following commands.
Global settings
extc value get application "securepoint_firewall"
Das Ergebnis sollte ähnlich wie folgt aussehen:
application |variable |value
--------------------+-------------------------------+-----
securepoint_firewall|ANONYMIZELOGS |1
|CIPHER_LIST |
|CLUSTERADVBASE |2
|CLUSTERDEADRATIO |15
|CLUSTERPREEMTIVE |0
|CLUSTER_ID |1
|CLUSTER_SECRET |secret
|CRYPTO_OVERRIDE |0
|DHPARAM_LENGTH |2048
|DHPARAM_LENGTH_DEFAULT |2048
|ECDHE_CURVE |secp384r1
|FULLCONENAT_ZONE_DST |external
|FULLCONENAT_ZONE_SRC |internal
|HTTP_TRANSPARENT_EXCEPTION_LIST|
|HTTP_TRANSPARENT_LIST |eth1
|IPCONNTRACK |32000
|LANG |en_US
|LASTRULE_LOGGING |2
|POP3_TRANSPARENT_EXCEPTION_LIST|
|POP3_TRANSPARENT_LIST |eth1
|PPPOE_LCP_ECHO |1
|TLS_VERSION_MAX |1.2
|TLS_VERSION_MAX_DEFAULT |1.2
|TLS_VERSION_MIN |1.0
|TLS_VERSION_MIN_DEFAULT |1.0
|UPDATE_TRIGGER_DELAY |2
|USE_ECDHE |1
|USE_OTP |0
Um hier den Wert einer einzelnen Variablen zu ändern, kann folgender Befehl verwendet werden. Geändert wird der Wert der Variablen TLS_VERSION_MIN.
extc value set application "securepoint_firewall" variable "TLS_VERSION_MIN" value 1.1
The result should look similar to the following:
|TLS_VERSION_MAX |1.2
|TLS_VERSION_MAX_DEFAULT |1.2
|TLS_VERSION_MIN |1.1
|TLS_VERSION_MIN_DEFAULT |1.0
Individual applications
The encryption of the individual applications can be done with the same command. Only the name of the application must be exchanged. The following applications are available:
extc value get application "webserver" extc value get application "openvpn" extc value get application "smtpd" extc value get application "squid-reverse"
Changes made on the CLI must be activated by restarting the respective application. The command for this is:
appmgmt restart application "[Name of the application]"