notempty
- Updating the Flowchart
- Default cipher for SSL-VPN updated
- Cipher for TLS 1.3 for SSL-VPN separately configurable
- Note on the encryption target at the Reverse Proxy
Introduction
In this menu you define the encryption protocol that is used to address the applications on the UTM. The basic settings selected by Securepoint are currently considered secure and have been tested for compatibility.
If a higher level of protection is required, the settings can be changed in the menu (jargon: harden).
- The tab Global displays the basic settings
- With Overwrite default values the default settings of Openssl can be overwritten for all following applications:
- Webserver
- SSL-VPN
- Mailrelay
- Reverse proxy (clients)
- The changes made in the Global tab can in turn be overwritten separately for each application.
- Individual settings in the application menus can (partially) apply the global values by selecting .
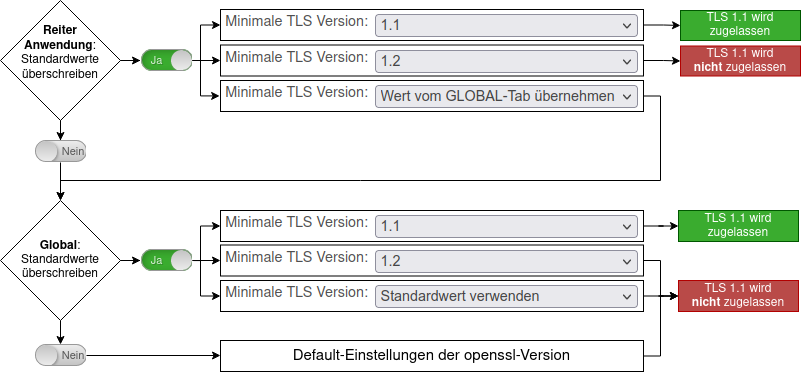
The graph on the right shows the dependency on the settings of an application for Global Setting using the minimal TLS version 1.1.
For all settings shown in the graphic: TLS 1.0 is not allowed. TLS 1.2 & TLS 1.3 is allowed.
Cryptographic settings
GlobalGlobal | |||
| Caption | Value | Description | 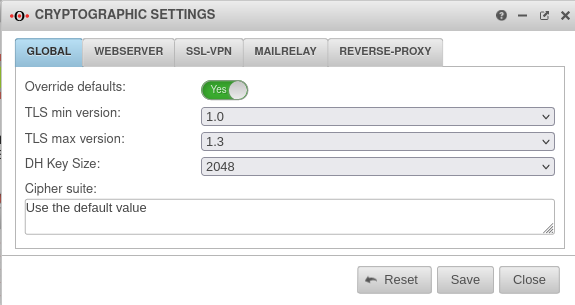 |
|---|---|---|---|
| Override defaults: | No | If this function is activated, the settings for the protocols can be changed. | |
| TLS min version: | TLS 1.0 to TLS 1.3 is available Default: | ||
| TLS max version: | TLS 1.0 to TLS 1.3 is available Default: | ||
| DH Key Size: | The length of the Diffie-Hellmann key can be set to bit (default) or bit. | ||
| Cipher suite: | In the field Cipher-Suite the desired encryption and modes can be defined. | ||
| Use default value | If no value is specified, the default value of the respective application (see below) is used | ||
WebserverWebserver | |||
| Override defaults: | No | If this function is activated, the settings for the protocols can be changed. | 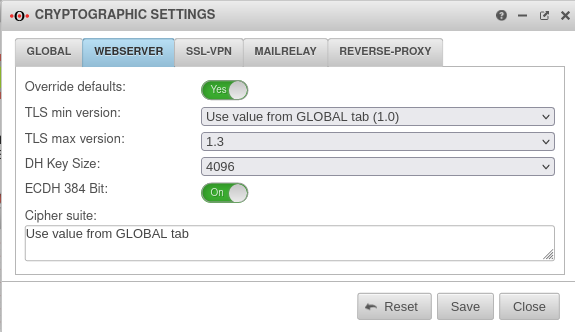 |
| TLS min version: | TLS 1.0 to TLS 1.3 is available Default: | ||
| TLS max version: | TLS 1.0 to TLS 1.3 is available Default: | ||
| DH Key Size: | The length of the Diffie-Hellmann key can be set to bit (default) or bit. | ||
| ECDH 384 Bit: | On | Uses the Elliptic Curve Diffie-Hellman method with 384 bits for key calculation. | |
| Cipher suite: | In the field Cipher-Suite the desired encryption and modes can be defined. Default: ECDH+AESGCM:DH+AESGCM:ECDH+AES256:DH+AES256:ECDH+AES128:DH+AES:ECDH+3DES:DH+3DES:RSA+AESGCM:RSA+AES:RSA+3DES:!aNULL:!MD5:!DSS; | ||
SSL-VPNSSL-VPN | |||
| Override defaults: | No | If this function is activated, the settings for the protocols can be changed. | 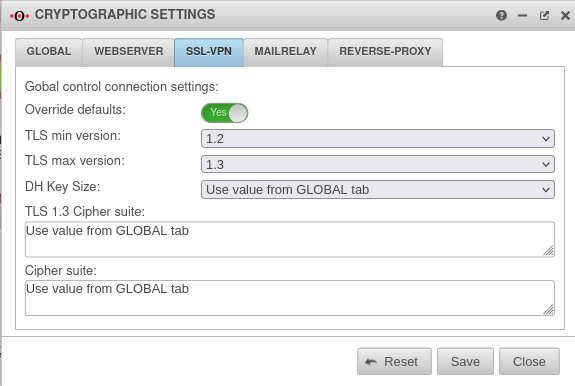 |
| TLS min version: | TLS 1.0 to TLS 1.3 is available Default: | ||
| TLS min version: | TLS 1.0 to TLS 1.3 is available Default: | ||
| DH Key Size: | The length of the Diffie-Hellmann key can be set to bit (default) or bit. | ||
| TLS 1.3 Cipher Suite | If applicable, restrictions on the cipher suites to be used for TLS 1.3 Default New in documentation
TLS_AES_128_GCM_SHA256:TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256:TLS_AES_128_CCM_SHA256:TLS_AES_128_CCM_8_SHA256 | ||
| Cipher suite: | In the field Cipher-Suite the desired encryption and modes can be defined. Default updated
ECDH+AESGCM:DH+AESGCM:ECDH+AES256:DH+AES256:ECDH+AES128:DH+AES:ECDH+3DES:DH+3DES:RSA+AESGCM:RSA+AES:RSA+3DES:!aNULL:!MD5:!DSS | ||
MailrelayMailrelay | |||
| Override defaults: | No | If this function is activated, the settings for the protocols can be changed. |  |
| TLS min version: | TLS 1.0 to TLS 1.3 is available Default: If TLS is to be forced, the setting is made under Tab Relaying
| ||
| TLS max version: | TLS 1.0 to TLS 1.3 is available Default: | ||
| DH Key Size: | The length of the Diffie-Hellmann key can be set to bit (default) or bit. | ||
| Cipher suite: | In the field Cipher-Suite the desired encryption and modes can be defined. Default ECDH+AESGCM:DH+AESGCM:ECDH+AES256:DH+AES256:ECDH+AES128:DH+AES:ECDH+3DES:DH+3DES:RSA+AESGCM:RSA+AES:RSA+3DES:!aNULL:!MD5:!DSS | ||
Reverse-ProxyReverse-Proxy
These TLS settings apply to the connection between this appliance and the clients.
The TLS settings between the servers' (to be reached via the reverse proxy) and this appliance are configured under . See the wiki for Reverse Proxy | |||
| Override defaults: | No | If this function is activated, the settings for the protocols can be changed. |  |
| TLS min version: | TLS 1.0 to TLS 1.3 is available Default: | ||
| TLS max version: | TLS 1.0 to TLS 1.3 is available Default: | ||
| DH Key Size: | The length of the Diffie-Hellmann key can be set to bit (default) or bit. | ||
| Cipher suite: | In the field Cipher-Suite the desired encryption and modes can be defined. Default ECDH+AESGCM:DH+AESGCM:ECDH+AES256:DH+AES256:ECDH+AES128:DH+AES:ECDH+3DES:DH+3DES:RSA+AESGCM:RSA+AES:RSA+3DES:!aNULL:!MD5:!DSS | ||
Save / Restore
The button resets the settings in the currently opened area to the global values. If Overwrite default values is deactivated again, the settings in the currently opened area are reset to the default values of the individual application.
CLI
The settings that are made in the web interface are visible on the Command Line Interface using the following commands.
Global settings
extc value get application "securepoint_firewall"
The result should look similar to the following:
application |variable |value
--------------------+-------------------------------+-----
securepoint_firewall|ANONYMIZELOGS |1
|CIPHER_LIST |
|CLUSTERADVBASE |2
|CLUSTERDEADRATIO |15
|CLUSTERPREEMTIVE |0
|CLUSTER_ID |1
|CLUSTER_SECRET |secret
|CRYPTO_OVERRIDE |0
|DHPARAM_LENGTH |2048
|DHPARAM_LENGTH_DEFAULT |2048
|ECDHE_CURVE |secp384r1
|FULLCONENAT_ZONE_DST |external
|FULLCONENAT_ZONE_SRC |internal
|HTTP_TRANSPARENT_EXCEPTION_LIST|
|HTTP_TRANSPARENT_LIST |LAN2
|IPCONNTRACK |32000
|LANG |en_US
|LASTRULE_LOGGING |2
|POP3_TRANSPARENT_EXCEPTION_LIST|
|POP3_TRANSPARENT_LIST |LAN2
|PPPOE_LCP_ECHO |1
|TLS_VERSION_MAX |1.3
|TLS_VERSION_MAX_DEFAULT |1.3
|TLS_VERSION_MIN |1.2
|TLS_VERSION_MIN_DEFAULT |1.2
|UPDATE_TRIGGER_DELAY |2
|USE_ECDHE |1
|USE_OTP |0
In order to change the value of a single variable, the following command can be used. The value of the TLS_VERSION_MIN variable is changed.
extc value set application "securepoint_firewall" variable "TLS_VERSION_MIN" value 1.1
The result should look similar to the following:
|TLS_VERSION_MAX |1.3
|TLS_VERSION_MAX_DEFAULT |1.3
|TLS_VERSION_MIN |1.1
|TLS_VERSION_MIN_DEFAULT |1.2
Individual applications
The encryption of the individual applications can be done with the same command. Only the name of the application must be exchanged. The following applications are available:
extc value get application "webserver" extc value get application "openvpn" extc value get application "smtpd" extc value get application "squid-reverse"
Changes made on the CLI must be activated by restarting the respective application. The command for this is:
appmgmt restart application "[Name of the application]"