notempty
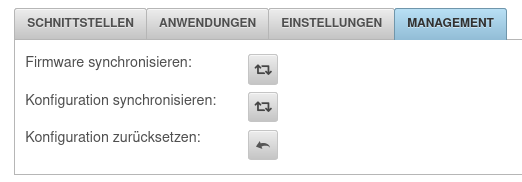
- Es kann ein manueller Download der neuesten Firmware ausgelöst werden
- Die aktuelle Firmware kann direkt an den Clusterpartner übertragen werden
- Hinweis zur Reihenfolge (Hover-Text bei )
Requirements
Software
The systems must always be kept at the current release level. Unpredictable behaviour may occur when updating from an old release.
Changelog
Before performing an update, the changelog should be checked as there may be changes to the cluster functionality.
The changelog can be found at the following URL:
http://wiki.securepoint.de/index.php/UTM/Changelog
Flawlessness
Auf den UTM-Systemen sollten keine Fehler oder Störungen vorliegen.
Test of the cluster function
Before the update is carried out on the cluster system, the functionality (see description "Test procedure") must be tested with the current version.
If the test is not successful, the update process may be disrupted.
Configuration backup
Before updating the UTM systems, it should be ensured that current configurations are available and that these can be imported in an emergency.
Implementation
Scenario 1: Online update
This scenario assumes that both systems have independently downloaded the latest firmware version.
Step 1
First, the update is activated on the spare UTM.
Falls noch kein Update automatisch verteilt wurde, kann dieses über Button bezogen werden
Step 2
After the update has been installed on the Spare-UTM, the web interface of the Spare-UTM must be called up and checked whether the update has been installed correctly.
Menü Tab Management Schaltfläche Firmware synchronisieren
Step 3
Now the update can be installed on the master UTM. During the installation of the update, the master UTM is restarted in the meantime; the spare UTM should take on the role of the active UTM firewall in the cluster.
Step 4
As soon as the update has been successfully installed on the master UTM and it has booted up again, it should take on the role of the active UTM again.
Again, the web interface of the master UTM should be called up to check whether all functions are working properly.
Scenario 2: Offline update
This variant is used for systems without an active Internet connection.
Step 1
Instructions for updating a UTM firewall can be found here.
The images can always be found in the Securepoint Reseller Portal.
The Reseller Portal can be reached at the following URL https://my.securepoint.de:
Step 2
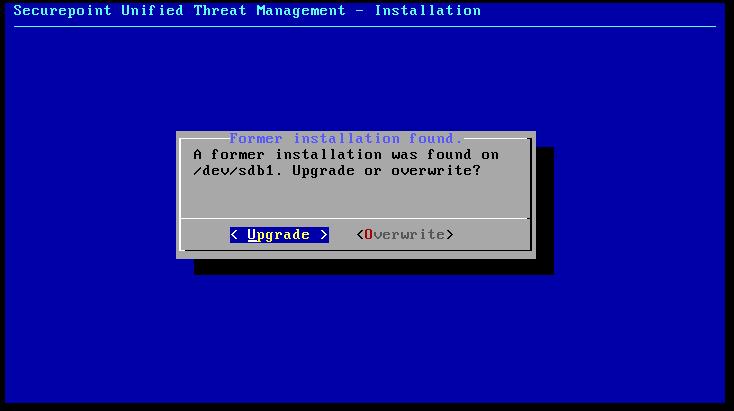
As you can read in the instructions, you should wait for the interaction. For the update, the option Upgrade must be selected.
After the update has been installed on the Spare-UTM, the web interface of the Spare-UTM is called up and checked whether the update has been installed correctly.
Step 3
After a successful check, the update can be carried out on the master UTM.
During the time of the update, the spare UTM takes over the cluster function.
Step 4
As soon as the update has been successfully installed on the master UTM and it has booted up again, it should take on the role of the active UTM again.
Again, the web interface of the master UTM should be called up to check whether all functions are working properly.
Test of the cluster functionality
Simulation: Failure of the master UTM
Test: The master UTM must be shut down properly via the interface.
Expected behaviour: The spare UTM takes over the function.
Simulation: Failure of an HA interface on the master UTM
Test: The network cable must be removed from an HA marked interface.
Expected behaviour: The spare UTM takes over the function.
Remark: This test should be carried out with each HA interface.
Synchronisation of the configuration
Test: After the successful test, the synchronisation of the configuration between the master and spare UTM must be tested.
Expected behaviour: The synchronisation of the configuration takes place without errors.