Hidenat exclude rules
Last adaptation to the version: 12.6.0
New:
- Updated to Redesign of the webinterface
notemptyThis article refers to a Resellerpreview
12.1
11.7
HideNat Exclude
If certain data connections must be established with the original source IP, but a HIDENAT already exists for this source via the network interface to the destination, exceptions can be set up via the NAT type HIDENAT EXCLUDE. As a rule, the HIDENAT EXCLUDE is used in connection with IPSec VPN connections. This ensures that data packets for the VPN remote terminal with the private IP address are routed through the VPN tunnel.
Otherwise, these packets would be masked with the public WAN IP address like all other packets in the direction of the Internet and, since they are sent with a private destination address, would be discarded at the next Internet router.
The corresponding rule then looks like this:
|
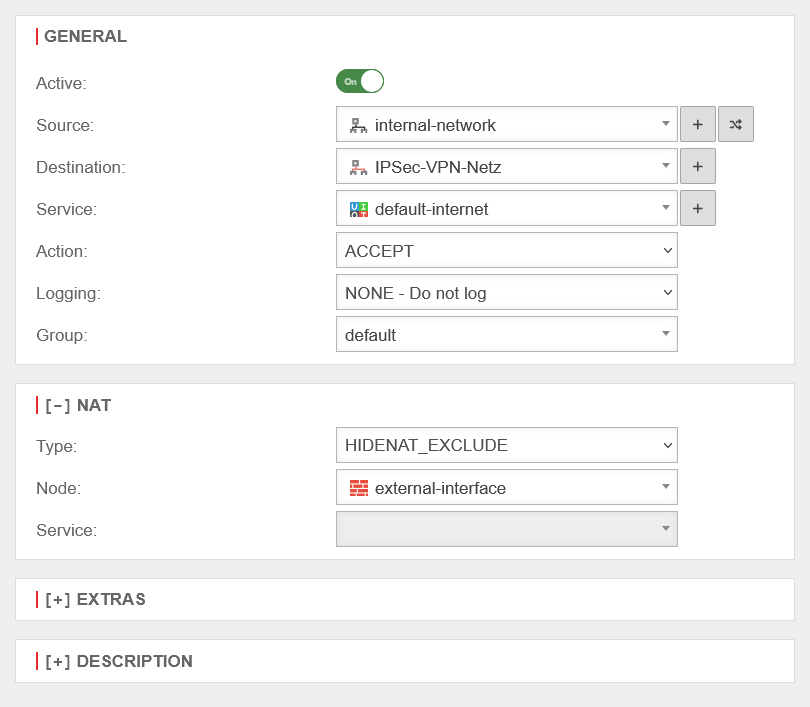
|
| Caption |
Value
|
| Source: |
 internal-network internal-network
|
| Destination: |
 internal-network internal-network
|
| Service: |
 default-internet default-internet
|
| Action: |
ACCEPT
|
|
|
|
| Type: |
HIDENAT EXCLUDE
|
| Node: |
external-interface
|
|
|
|