- Updated to Redesign of the webinterface
Prerequisite
In order for the UTM to "see" the network traffic it is supposed to filter, the proxy of the UTM must also be used for https.
Therefore either
- the SSL interception ( Area SSL interception)
and
the transparent mode for https must be activated (menu Area Transparent mode).
or
on every host the UTM is set up as a proxy in every browser
Overview
- In the rule sets, the entire access or individual domains, URLs or categories are blocked or allowed
- The validity of the rule sets can be limited according to the day of the week and time of the day
- The rule sets are assigned to profiles
- The profiles are assigned to network or user groups
- The rule sets are checked in sequence to see whether they apply (in terms of content and time)
The Webfilter
General settingsGeneral | |||
| Caption | Value | Description | UTMuser@firewall.name.fqdnApplications 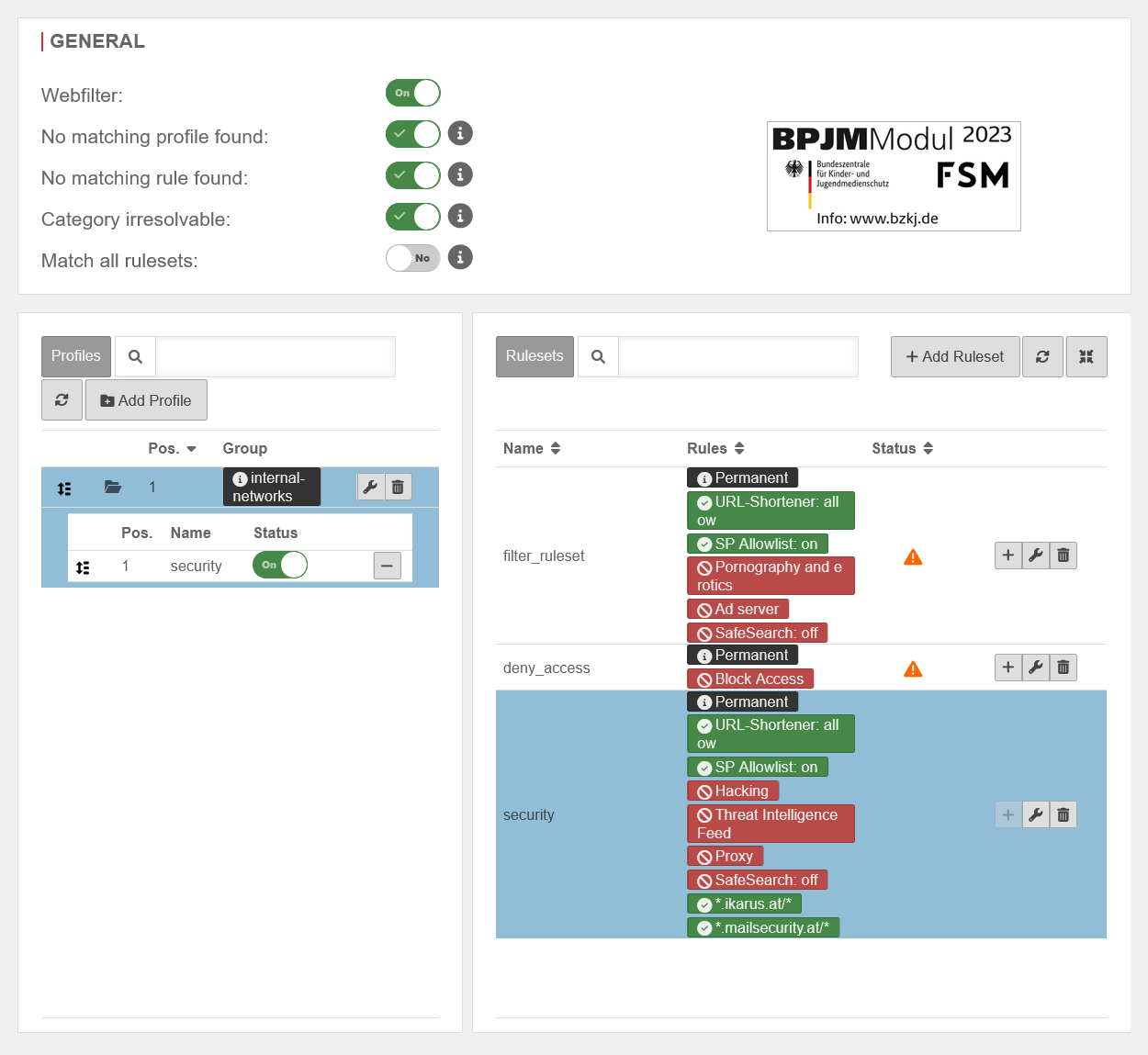 Webfilter overview Webfilter overview
|
|---|---|---|---|
| Webfilter | On | Activates (default) or deactivates (Off) the Webfilter functionality of the UTM | |
| No matching profile found | Allows data traffic for network and user groups for which no Webfilter profile has been created, as well as for groups whose profiles do not contain rule sets with a matching time stamp. | ||
| Blocks data traffic for network and user groups for which no Webfilter profile has been created, as well as for groups whose profiles do not contain rule sets with a matching time stamp. | |||
| No matching rule found | Allows data traffic if no matching rule was found in the profile | ||
| Blocks data traffic if no matching rule was found in the profile | |||
| Category irresolvable | Allows data traffic if the category has not been resolved. (For example, if no connection to the server could be established.) | ||
| Blocks data traffic if the category has not been resolved. (For example, if no connection to the server could be established.) | |||
| Review all rule sets: | No | The first rule set (if applicable, the first with a valid time profile) is searched. If no matching rule is found, the default behaviour of this rule set is applied. | |
| Yes | All rule sets (if applicable, provided they have a valid time profile) are checked in sequence until a suitable rule is found. If no suitable rule is found, the default behaviour of the last rule set is applied (if applicable, the last rule set with a valid time profile). | ||
Profiles Profiles
| |||
In the individual profiles, the rule sets are linked to
For profiles applies:
|
UTMuser@firewall.name.fqdnApplications  Webfilter - Profiles section Webfilter - Profiles section
| ||
| You can move the items by drag and drop into the desired sequence | |||
| Rule set is overlaid by… | This rule set is completely or partially overlaid by another rule set and is therefore completely or partially not applied | ||
| Edit | Opens the dialogue for editing the profile. The network or user group can be changed | ||
| Delete | Deletes the profile | ||
| Remove from profile | Removes the rule set from a profile | ||
| Opens the dialogue for adding a profile | UTMuser@firewall.name.fqdnApplicationsWebfilter 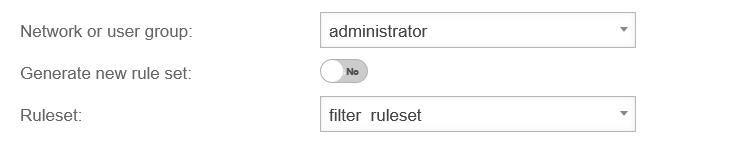
| ||
| Network or user group: | administrator | Network or user group to which the profile is to be applied | |
| Generate new rule set: | No | If Yes, automatically creates a new rule set assigned to this profile
| |
| Ruleset: (Only if generate new rule set No is deactivated) |
filter_ruleset | Existing rule set to apply in this profile | |
Rule sets Rule sets
| |||
| The rule sets define which websites and categories are blocked and released. The rule sets can also be limited for a period of time, e.g. to allow employees to surf privately during their lunch break. | UTMuser@firewall.name.fqdnApplications 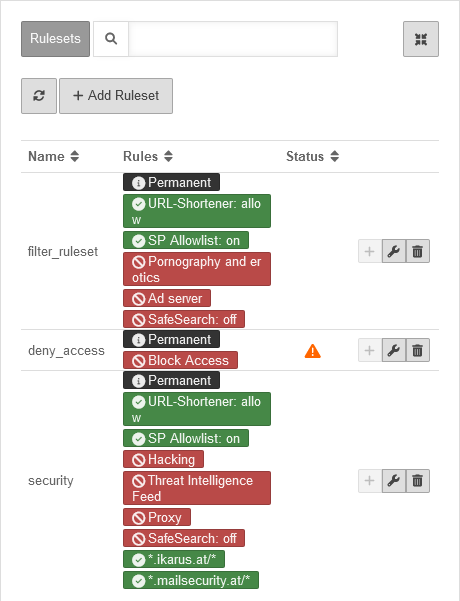 Rule sets Rule sets
| ||
| Add to profile | Adds the current rule set to the currently selected profile | ||
| Edit | Opens the settings of the rule set for editing | ||
| Delete | Deletes a rule set | ||
| Opens the dialogue for creating a new rule set | |||
Rule set detailsRule set details
GeneralGeneral | |||
| Name | security | Unique name | UTMuser@firewall.name.fqdnApplicationsWebfilter 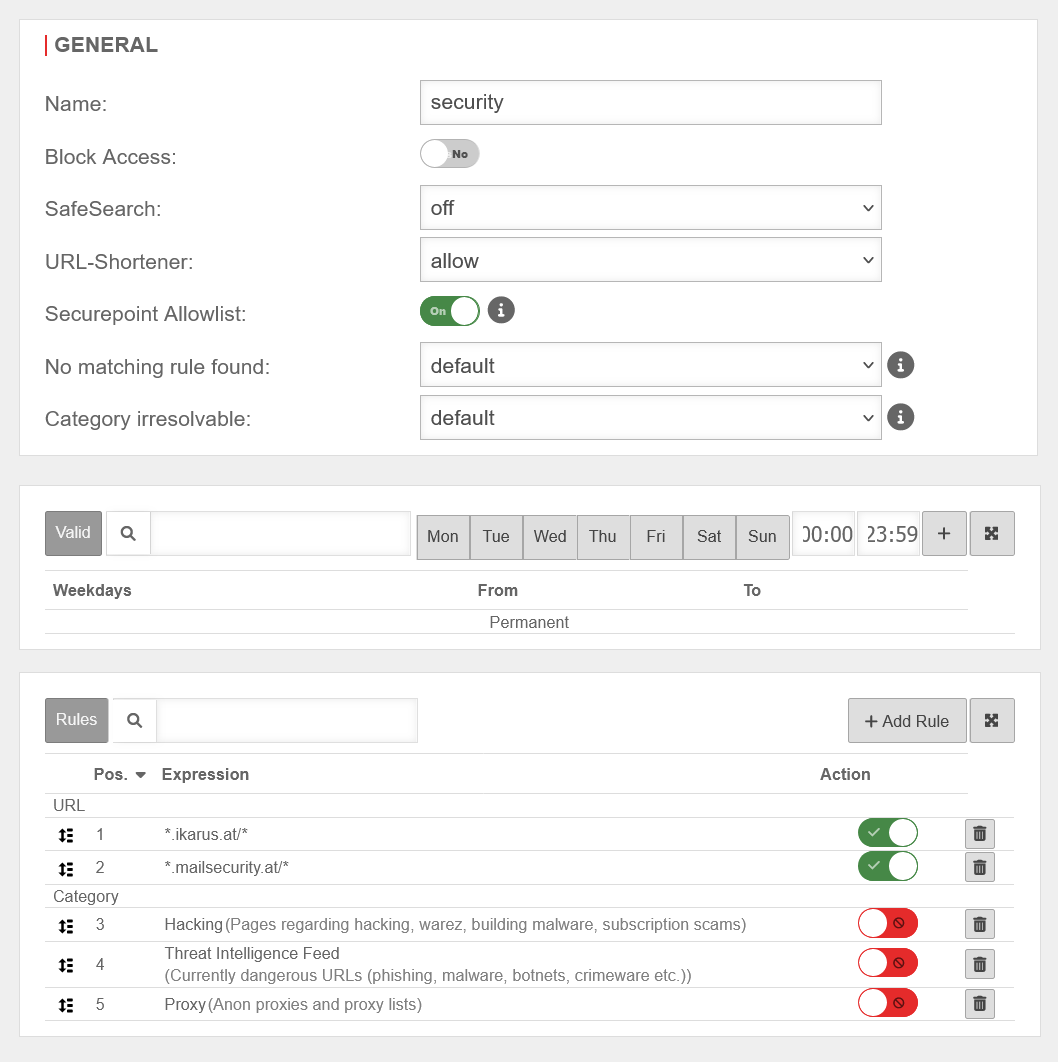 Display when adding a new rule set or editing an existing rule set Display when adding a new rule set or editing an existing rule set
|
| Block access | No | All websites will be blocked | |
| SafeSearch | Content that is not suitable for minors is not filtered. | ||
| Text, images and videos that are not suitable for minors are filtered out of the search results. | |||
| Pictures and videos that are not suitable for minors are filtered out of the search results, but corresponding texts are not. | |||
| URL-Shortener | Defines access to websites whose host names use URL shortener services. Here, you can choose whether these are blocked or allowed regardless of the actual destination or whether the host name is resolved and then handled according to existing rules. | ||
| Securepoint Allowlist | On | Access to URLs that Securepoint designates as trusted The Securepoint Allowlist contains, for example: Reputable addresses, public and corporate websites, technical services that should not be blocked. | |
| No matching rule found | Adopts the global settings from Webfilter general | ||
| Blocks the data traffic if no suitable rule was found in the rule set | |||
| Allows data traffic if no suitable rule was found in the rule set | |||
| Category irresolvable | Adopts the global settings from Webfilter general | ||
| Blocks data traffic if the category has not been resolved. (For example, if no connection to the server could be established.) | |||
| Allows data traffic if the category has not been resolved. (For example, if no connection to the server could be established.) | |||
Valid Valid
| |||
| Here one or more time periods can be assigned to the rule set, during which it is valid | |||
Rules Rules
| |||
| Define here which websites are allowed or not to be reached. The rules are processed in order:
| |||
| You can move the items by drag and drop into the desired sequence | |||
| allow | Allows data traffic | ||
| block | Blocks data traffic | ||
| Delete | Deletes the rule | ||
Add Rule | |||
| Type | example.com | Domain in plain text notation. All subdomains and subpages are filtered. | 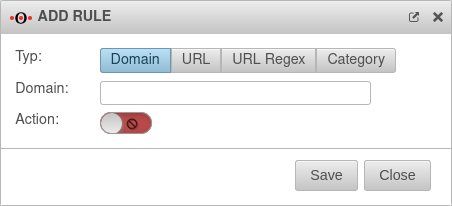 |
| Type | *.example.com/pages/* | Only the exact URL is filtered (wildcard * is possible). | |
| Type | .*\.example\.com | URL in regex format, which allows numerous placeholders Syntax of regular expressions - Regex | |
| Type |
category |
New as of v12.5 Category: UnknownThis allows you to block access to all websites that have not yet been classified by Securepoint.
| |
Whitelisting example Whitelisting example
| |||
| In this example, the URL www.google.de and the category Education were added to the whitelisting via the function . notempty g Since the web filter processes the rules from top to bottom, in this example the category Education had to be manually pushed to the first position.
|
UTMuser@firewall.name.fqdnApplicationsWebfilter 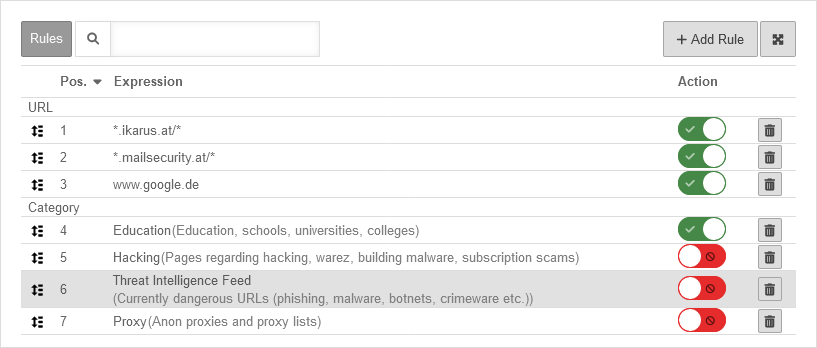
| ||
Other
Examples of exceptions for Windows update server
For more examples on setting up the Webfilter, authentication exceptions, virus scanner and SSL interception regarding Windows updates, see the Knowledge Base article Windows Updates with HTTP proxy and webfilter
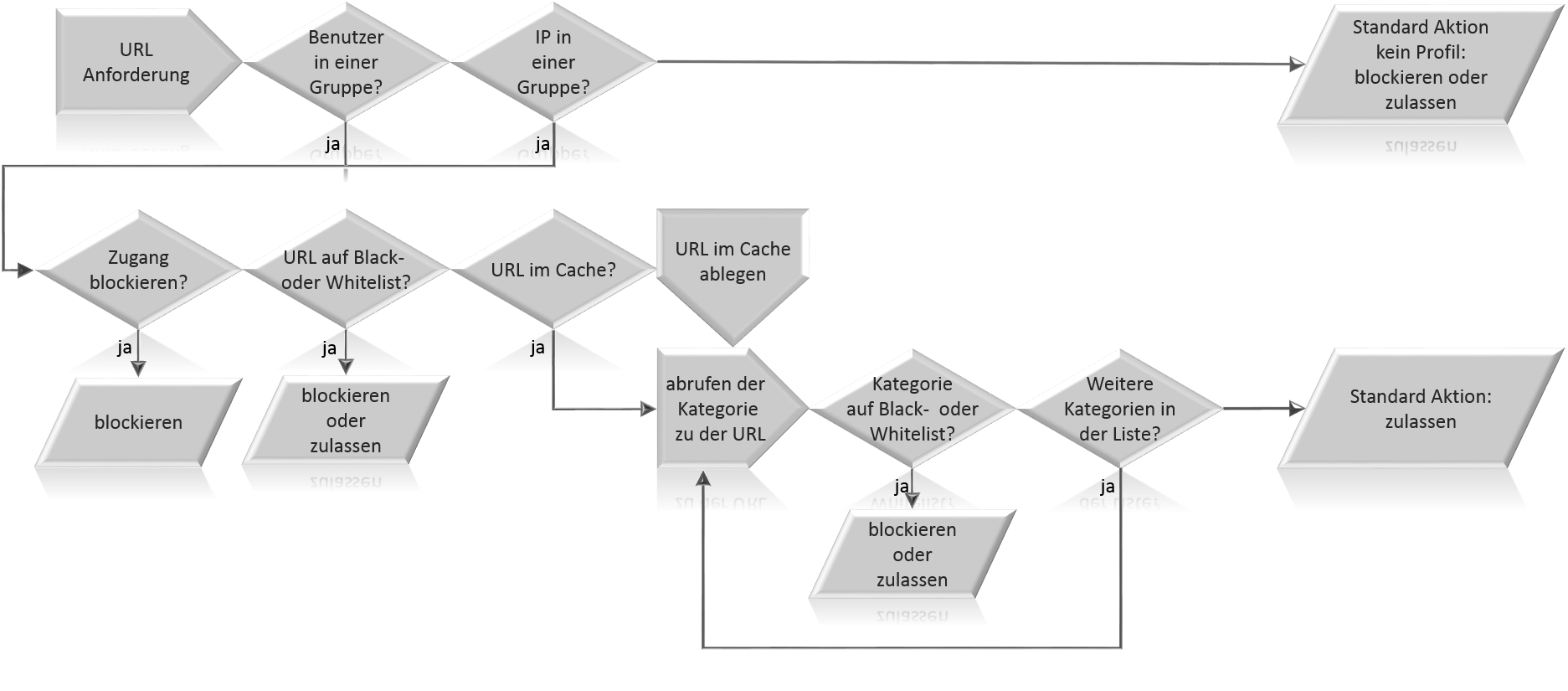
Architecture of the Webfilter
The Webfilter works with URL and category rule sets that must be assigned to network groups or user groups in profiles.
The process is as follows:
A user accesses a web page via a browser or another application. The data packets, including the Uniform Resource Locator (URL) of the website, are routed through the HTTP proxy. Either by the HTTP proxy being set up as a transparent proxy or by the proxy configuration of the browser on the client.
Depending on whether a profile was first created for a user group or a network group, it is checked whether the username or the IP address matches a profile.
If neither the username nor the source IP address matches a group profile, the default action defined under Webfilter in the General section under No matching profile found: takes effect. These requests are either allowed or blocked, depending on the setting in the Webfilter.
After a profile is recognised, the rule set associated with it is checked.
First, the temporal validity of the rule set is reviewed. If this does not match, the Webfilter checks whether another rule set is stored for this profile. If this is not the case, the standard action of the Webfilter takes effect.
If the rule set is not timed or if the rule set matches in time, the next step is to check whether this rule set should block access in principle. This is the case if in the window Edit Rule set the check box Block Access: has been set.
If not everything is blocked with the rule set, the Webfilter checks the URLs stored here and compares them with the client's request. If the URL or parts of the URL are listed in the rule set, it is checked whether they are on the allowlist or on the blocklist and thus allowed or blocked.
If the requested URL is not listed, the system checks whether it fits into a category.
To do this, it first checks whether this URL has already been reviewed for assignment to a category and whether this request is still in the cache.
If this is not the case, a request is made to the Securepoint content filter servers via the UTM, which works similar to a DNS request: The URL is first transmitted to the server. The request is answered with an IP address that informs the Webfilter in which category this URL is listed.
Now it is checked whether the category is listed and on a allow or blocklist. The request to this URL is then allowed or blocked.
It is possible that a URL is listed in several categories. The request to the content filter servers is repeated and compared with the other entries in the list.
If neither the URL nor a suitable category are stored in the rules, the setting under "Edit rule set" "No suitable rule found" applies. Here, a different behaviour to the default rules can be set for each rule set. If the categories are not resolvable, the behaviour set under "Edit rule set" "Category irresolvable" also applies here.