| Caption |
Value |
Description
|
 Add ACME certificate Add ACME certificate
|
Add ACME certificateUTM Dialog Area Certificates Button Add ACME certificate
|
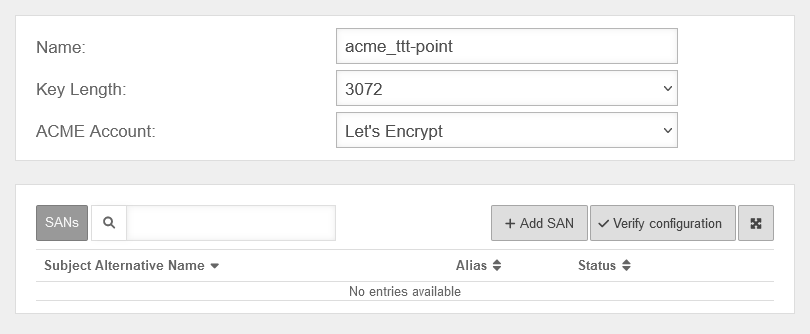
| Name |
acme_ttt-Point |
Name to identify the certificate
|
| Key length: |
2048 |
Key length of the certificate. Possible values:
|
| ACME Account |
Let's Encrypt |
ACME account which should be used
|
|
|
Subject Alternative Name configure with Add SANAdd Subject Alternative Name
|
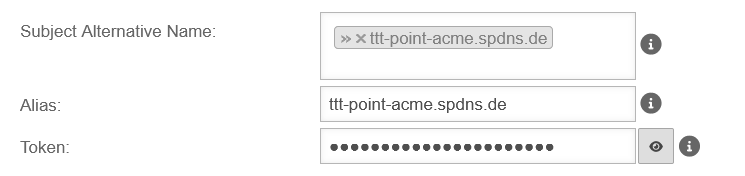
| Subject Alternative Name |
» ✕ttt-point.spdns.org |
The Subject Alternative Name ('SAN) is stored in the certificate and corresponds to the called URL
|
 Add Subject Alternative Name Add Subject Alternative Name
|
| » ✕*.ttt-point.spdns.org |
Wildcard SANs can also be used. Wildcard certificates are strongly recommended for use with a captive portalIf a forward zone is required for the captive portal in the nameserver and an A record is then entered for it, this is no longer resolved in the public DNS.
Verification and renewal of an ACME certificate with this name will then fail. |
| Alias |
ttt-point.spdns.org |
If the SAN is a spDYN hostname it is automatically taken on as alias.
(Also for wildcard domains without * )
|
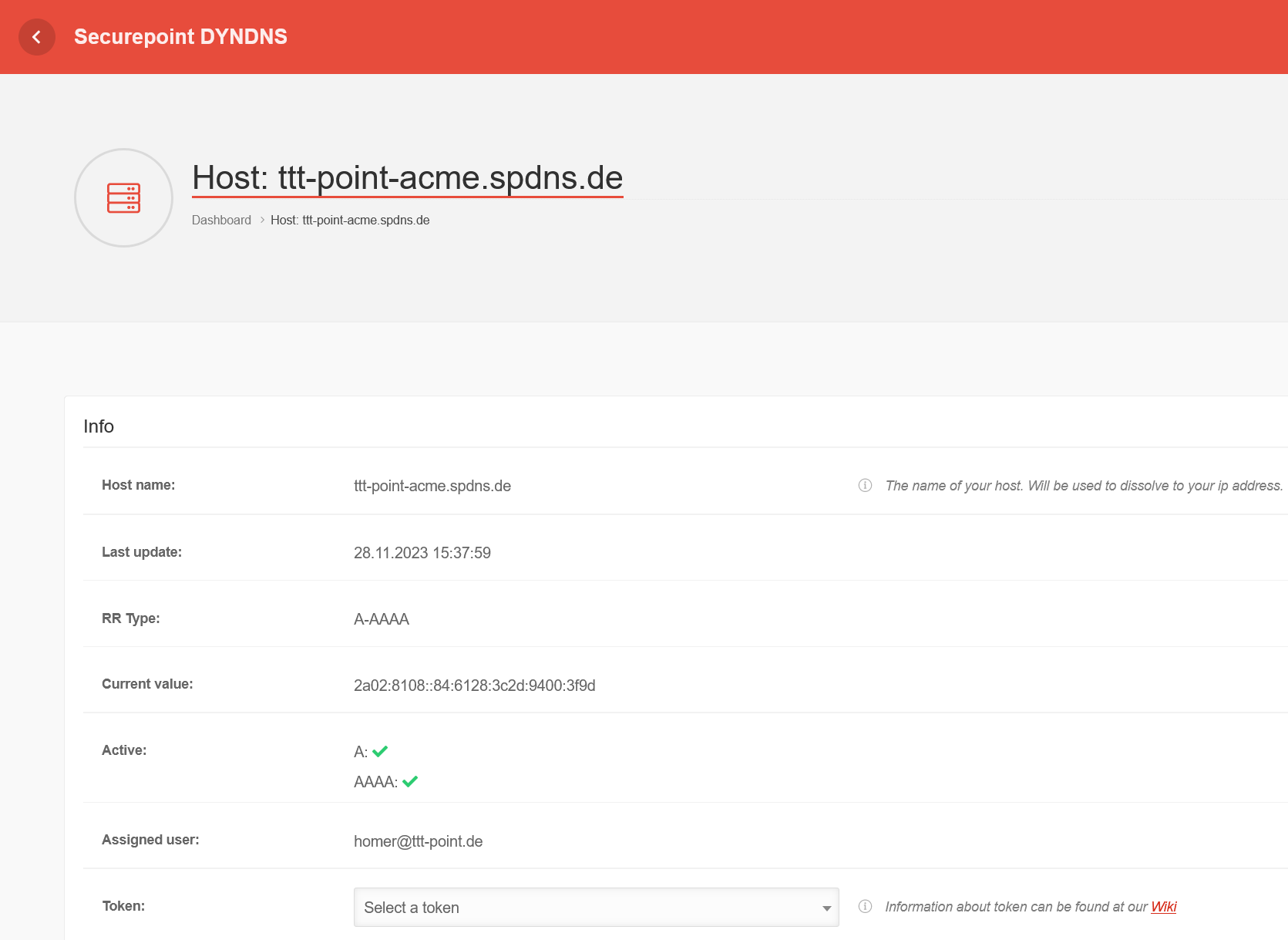
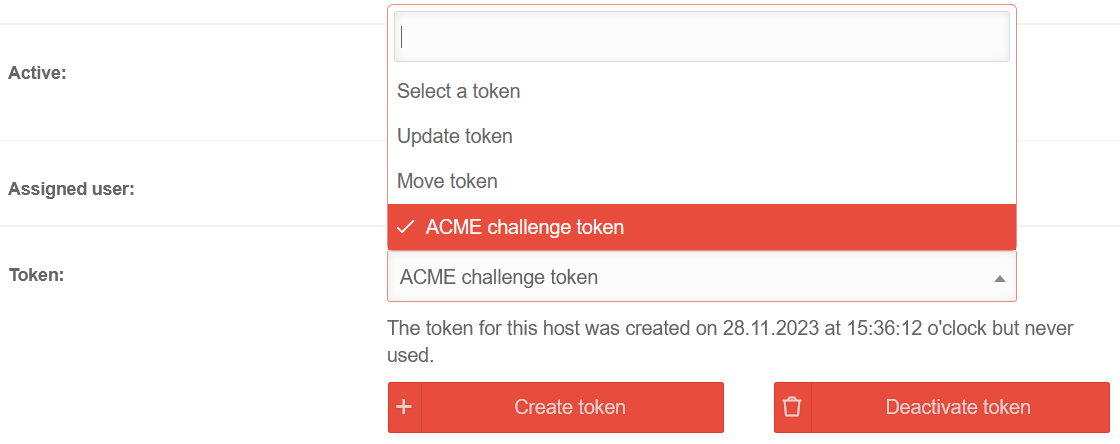
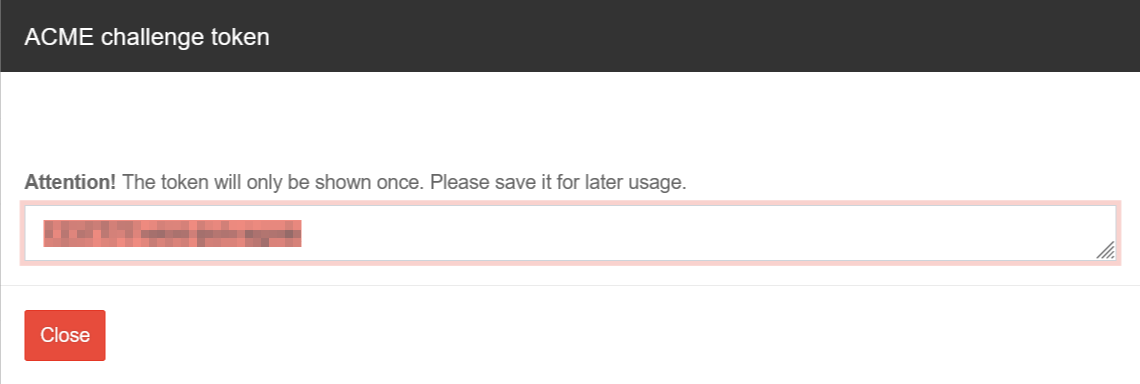
| Token |
••••••••••••• |
The token from the spDYN portal (see above) proves to the ACME service that you are allowed to dispose of the hostname.
displays the token.
When inserting the token from the clipboard it can happen that there are blanks before or after the actual token. These must be removed
|
|
|
Check configuration Check configuration
|
| Status
|
Not yet checked
|
Before the actual generation of the certificate, the configuration must first be checked. This is done by clicking on the Check configuration button.
|
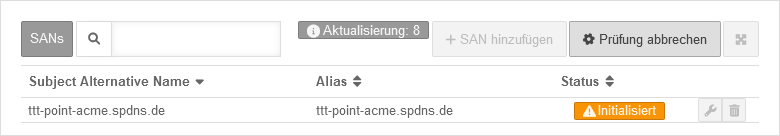
|
initialize
Initializes |
The check can take several minutes. During this process, the dialog is updated regularly.
|
| Valid |
If the check is successful, the status Valid is displayed.
|
| DNS error |
Possible causes:
- wrong token
- DNS resolution disturbed
- zone forwarding configured in DNS
- local DNS zone configured in DNS
- If there is a zone in the nameserver of the UTM for a domain that also uses the ACME certificate, the DNS resolution fails. Solution: Create a CNAME record for this domain.
• Search for the zone under Menu/Applications/Nameserver/Zones
• click on Edit
• Click on +Add Entry in the window
• enter a suitable name under Name:'
• select CNAME under Type:
• enter the domain under Value:
|
|
|
Configure Subject Alternative Name for an external DNS zone with Add SANAdd SAN for external DNS zone
|
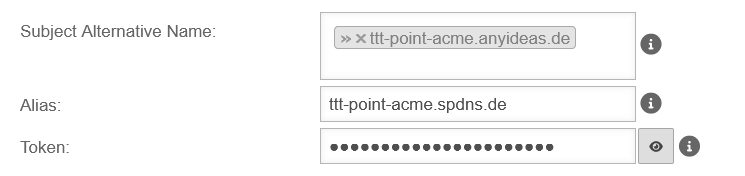
| Subject Alternative Name |
ttt-point.anyideas.org |
The Subject Alternative Name (SAN) from the external DNS zone. |
|
| Alias |
ttt-point.spdns.org |
The alias must also be the spDYN name for the external DNS.
|
| DNS-Provider |
Basically, an additional CNAME record with the prefix _acme-challenge and the subsequent host name must be created at the DNS provider hosting the external zone (here: ttt-point.anyideas.org). _acme-challenge.ttt-point.spdns.org. (With "." at the end!)
An example excerpt from a Zonefile for the configuration of the two hostnames mx.ttt-point.de and exchange.ttt-point.de looks like this:_acme-challenge.mx.ttt-point.anyideas.org. IN CNAME _acme-challenge.ttt-point.spdns.org.
_acme-challenge.exchange.ttt-point.anyideas.org. IN CNAME _acme-challenge.ttt-point.spdns.org.
The hostname must be resolvable in the public DNS.
Certificate creation for .local, .lan, etc. zones is not possible.
The UTM must be able to resolve the host name correctly via external nameservers.
notempty If the internal and the external/public domain are identical, the zone must also be delegated to the internal DNS.
|
|
|
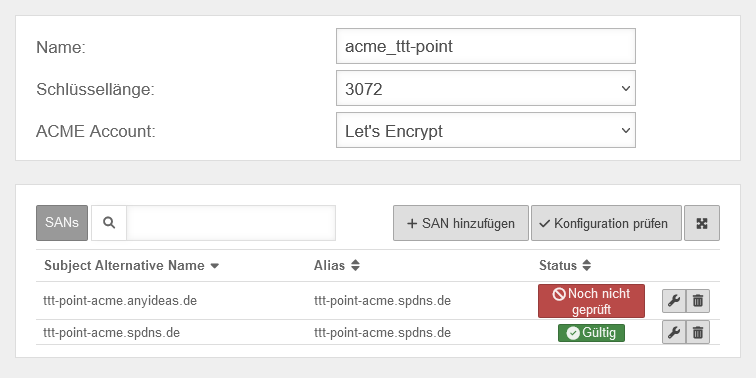
| Check configuration |
Additional SANs can be added and checked as long as the Save button has not been pressed. |
|
|
|
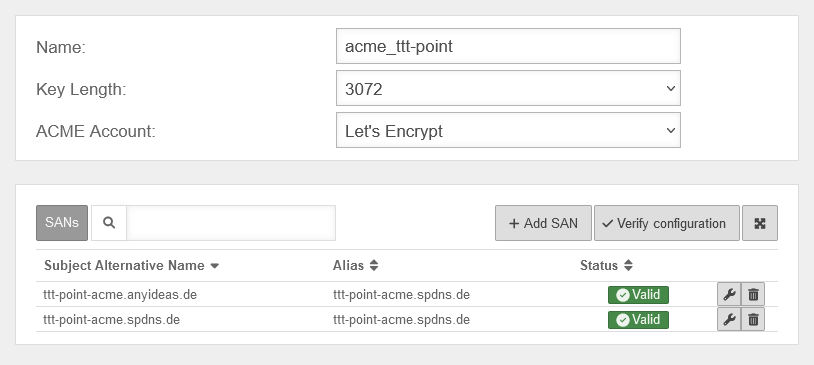
| Status |
Valid |
Once all the required SANs have been successfully checked, the certificate can be saved. |
|
| |
notempty Once the certificate has been saved, no more changes can be made. Only the alias and the token can be changed for existing SANs.
If additional or different SANs are required, a new certificate must be created and the existing one has to be revoked.
|
|
|
Creation of the ACME certificateCreation of the ACME certificate
|
|
|
If the previous steps have been completed successfully, the actual process for validating and generating the certificate is triggered by clicking Save.
This process may take some time. To update the status, the dialog must be reloaded manually.
|
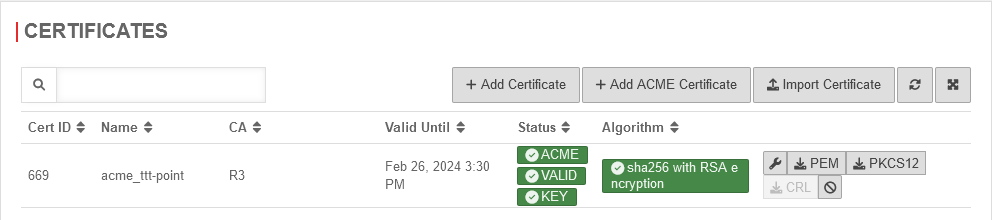
|
|
|
Status valuesStatus values
|
| The following status values can occur
|
| Status |
Description |
Note
|
| Valid |
The ACME certificate is valid |
|
| Not yet verified |
The ACME certificate still needs to be verified |
|
| Internal error |
An internal error has occurred |
Possible causes:
- Broken hardware
- Software error
- Configuration error
|
| Connection error |
No connection possible / present |
Check the connection settings
|
| Invalid |
The ACME certificate is invalid and cannot be used |
|
| DNS error |
A DNS error has occurred |
Possible causes:
- wrong token
- DNS resolution disrupted
- zone forwarding configured in DNS
- local DNS zone configured in DNS
- If there is a zone in the nameserver of the UTM for a domain that also uses the ACME certificate, the DNS resolution fails. Solution: Create a CNAME record for this domain.
• Search for the zone under Menu/Applications/Nameserver/Zones
• click on Edit
• Click on +Add Entry in the window
• enter a suitable name under Name:'
• select CNAME under Type:
• enter the domain under Value:
|
| Banned |
The ACME certificate has been revoked |
Either it has been manually revoked, or it has lost its validity. For example, the ACME certificate expired and was not renewed.
|
| Initializing |
The verification of the ACME certificate is initiated |
This can take several minutes. The status is updated regularly.
|
| Deferred |
The verification of the ACME certificate is postponed |
Refreshing the status will take some time, since the limit of requests was already reached
|
| Initialized |
The ACME certificate is being verified |
The verification of the ACME certificate is initiated
|
|
|