Last adaptation to the version: 12.6.0
- Updated to Redesign of the webinterface
notemptyThis article refers to a Beta version
General
The Securepoint firewall uses digital certificates for authentication for various functions:
- VPN connections
- SSL Interception
- Captive Portal
- Mailrelay
- Reverse Proxy
The certificates comply with the x.509 standard.
Certificates are intended to certify the identity of the holder.
They are
- issued by the Securepoint Appliance and signed by the appliance's own CA (Certification Authority; also called root certificate).
- The CA itself is also a certificate that must first be created on the Apliance in order to create certificates, because certificates must be signed with the CA when they are created.
- issued by a Automatic Certificate Management Environment service and certified by it. Available here Let's Encrypt.
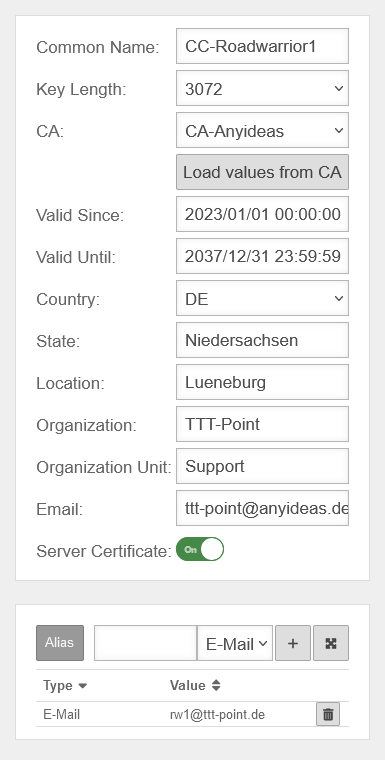
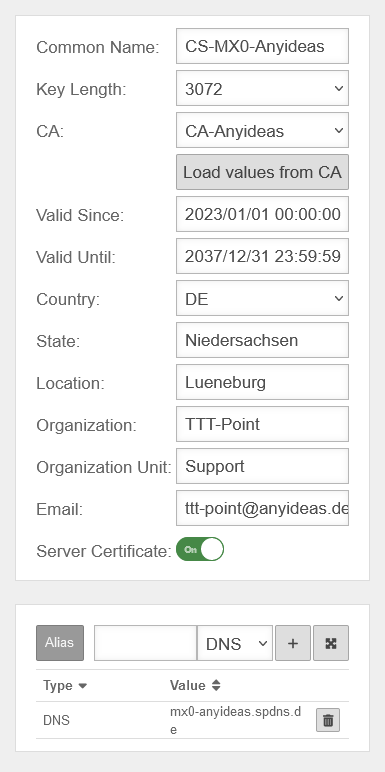
To be able to uniquely assign the certificate, a distinguished name (DN) is generated from the individual details that must be set when the certificate is created.
. This includes:
- Name of the certificate (CN) Common Name
- Country (CO) Country
- State/Region (ST) State
- City (LO) Location
- Company (OR) Organization
- Department (OU) Organization Unit
- E-mail (email-address)
- An alias can still be specified to strengthen the uniqueness. This alias is either an email address, a DNS name or an IP address.
- Some VPN software requires this alias for proper functionality (e.g. Windows 7 IPSec Client).
- In addition, a validity period must still be specified, whose start and expiration time is composed of time and date. The validity period is not prescribed and can be adapted to your own needs. After the expiration of this period, the certificate can no longer be used.
- A flag can also be set, which identifies the certificate as a server certificate. This is required by OpenVPN for the server. OpenVPN always requires a server system with server certificate for a site, even for site-to-site connections. Other VPN protocols do not require this flag.
The following shows how certificates are created and signed by the UTM.
Create CA
Menu Area CA button
| Value | Description | UTMuser@firewall.name.fqdnAuthenticationCertificate 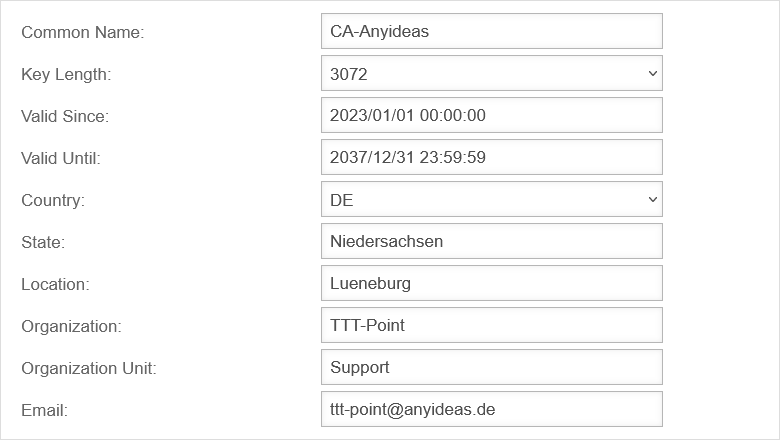 Dialog Add CA Dialog Add CA
|
|---|---|---|
| Common Name: | Unique name | |
| Key length: | Key length of the certificate. Possible values:
| |
| Valid until: | The date must be entered in the following format YYYY/MM/DD hh:mm:ss. If the mouse is clicked in the input field, a calendar opens automatically, on which the date and time can be selected. When the CA expires, the validity of the certificates signed with this CA also expires. | |
| Create the CA with the button. | ||
notempty
The BSI recommends—as of January 2025—key lengths of 3000 bits or more and SHA256 BSI – Technical Guideline – Cryptographic Methods: Recommendations and Key Lengths BSI TR-02102-1 | Chapter 2.3: RSA encryption The default setting of the UTM for new certificates is RSA encryption with 3072 bits and SHA256 as the hash algorithm | ||
Create server and client certificate
certificate can now be created for a server or client. This can be done under: Area Certificate button notemptyServer and client certificates can only be created once a CA has been created.
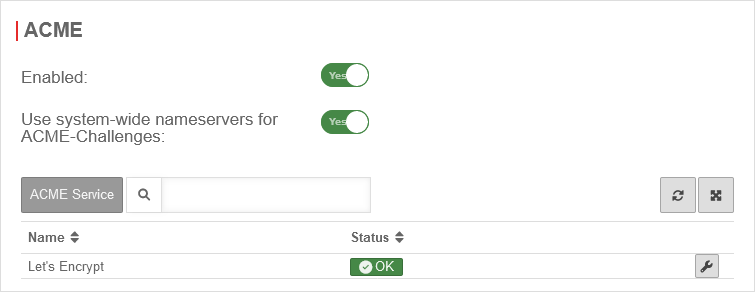
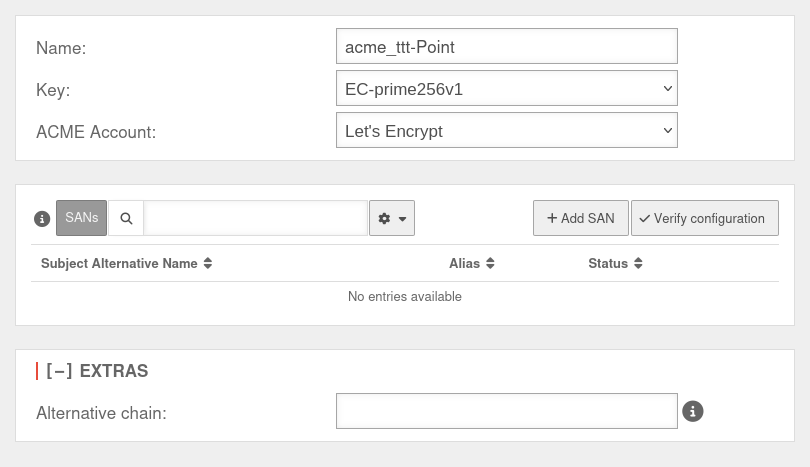
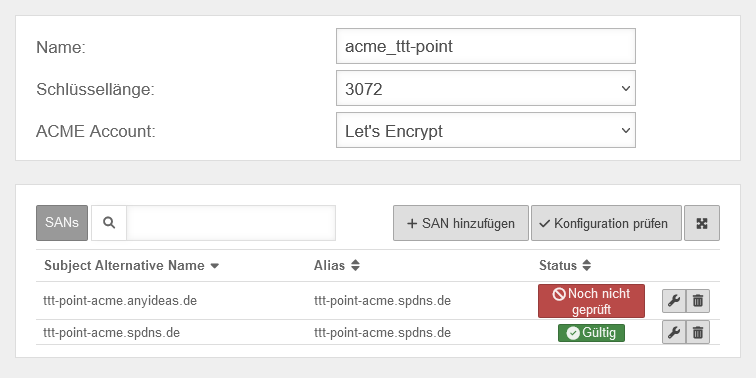
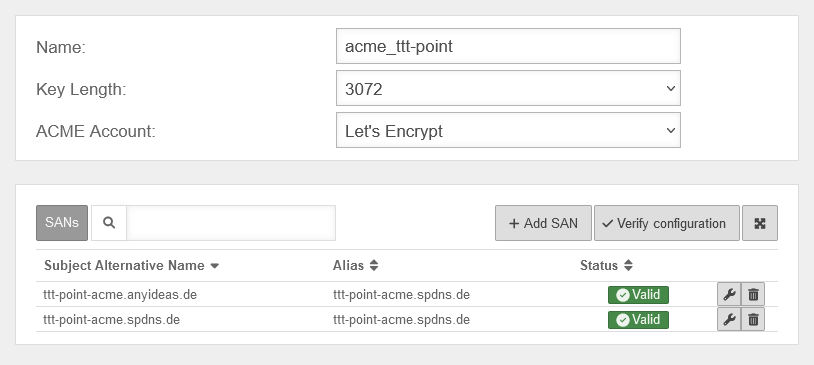
ACME certificates (Let's Encrypt)
Area ACME
| Caption | Value | Description | UTMuser@firewall.name.fqdnAuthentifizierung 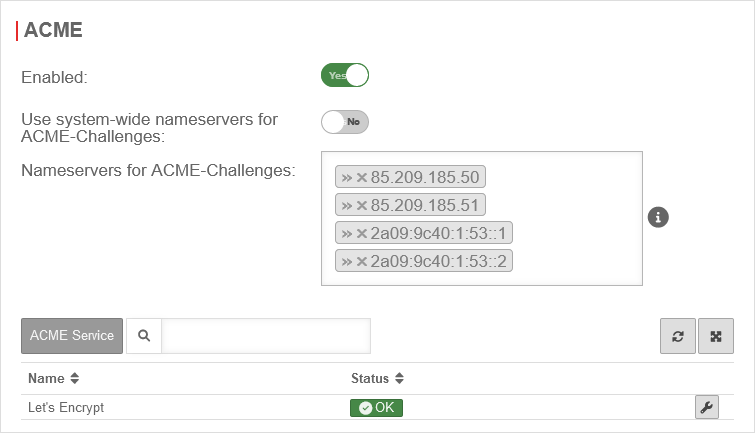
|
|---|---|---|---|
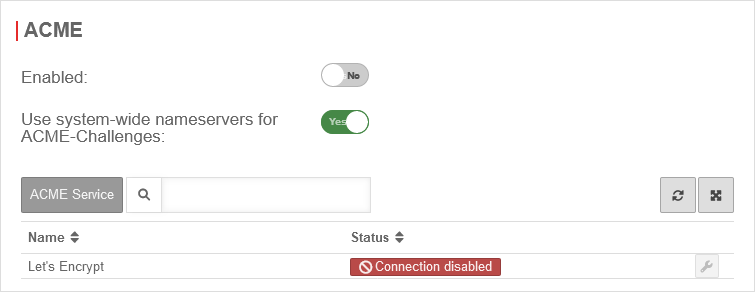
| Activated: | Yes | Enables the use of ACME certificates. For more information see below Activate ACME service. | |
| Use system-wide nameservers for ACME challenges: | Yes | If the addresses for the servers for the extension of the ACME challenges cannot be resolved via the system-wide nameserver (e.g. due to configured relay or foreward zones), alternative nameservers can be entered by deactivating No. | |
| Nameserver for ACME challenges: Can be used for ACME challenges when system-wide nameserver is disabled |
»85.209.185.50»85.209.185.51»2a09:9c40:1:53::1»2a09:9c40:1:53::2 | Here you can enter the nameservers for the ACME-Challenges. | |
Activate ACME service
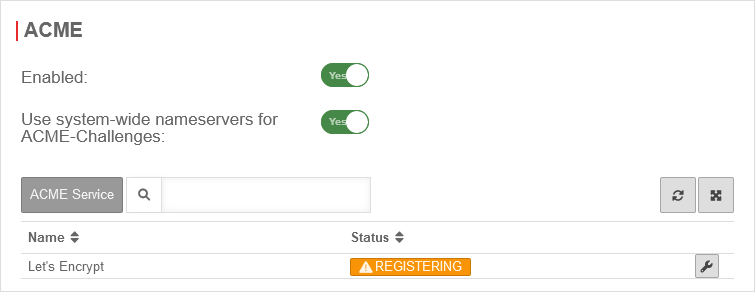
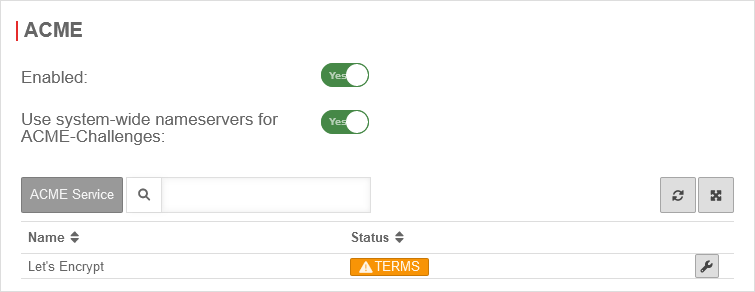
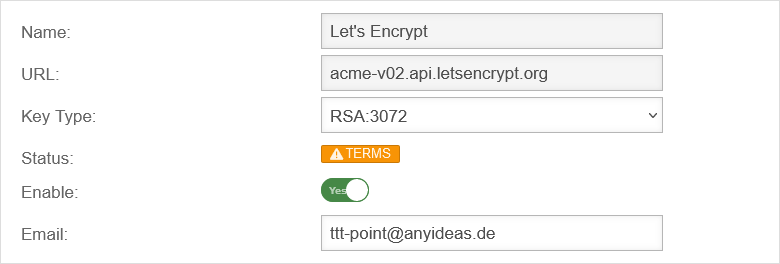
To be able to use ACME certificates, this must be activated under Area ACME Enabled: Yes.
- As soon as the service has been activated and this has been saved with , the link to the terms of use is loaded and the settings can be called up.
- With the button Activate Yes and the storage of an Email address for notifications by the ACME service provider (here: Let's Encrypt), the information can be saved with
- A dialog will appear with a link to the Terms of Use, which must be accepted Yes.
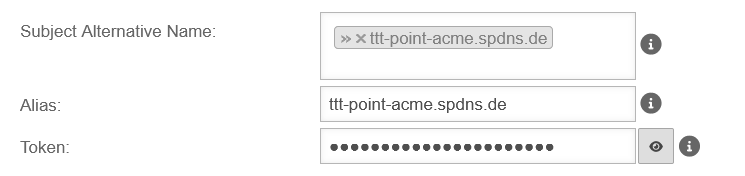
Generate token
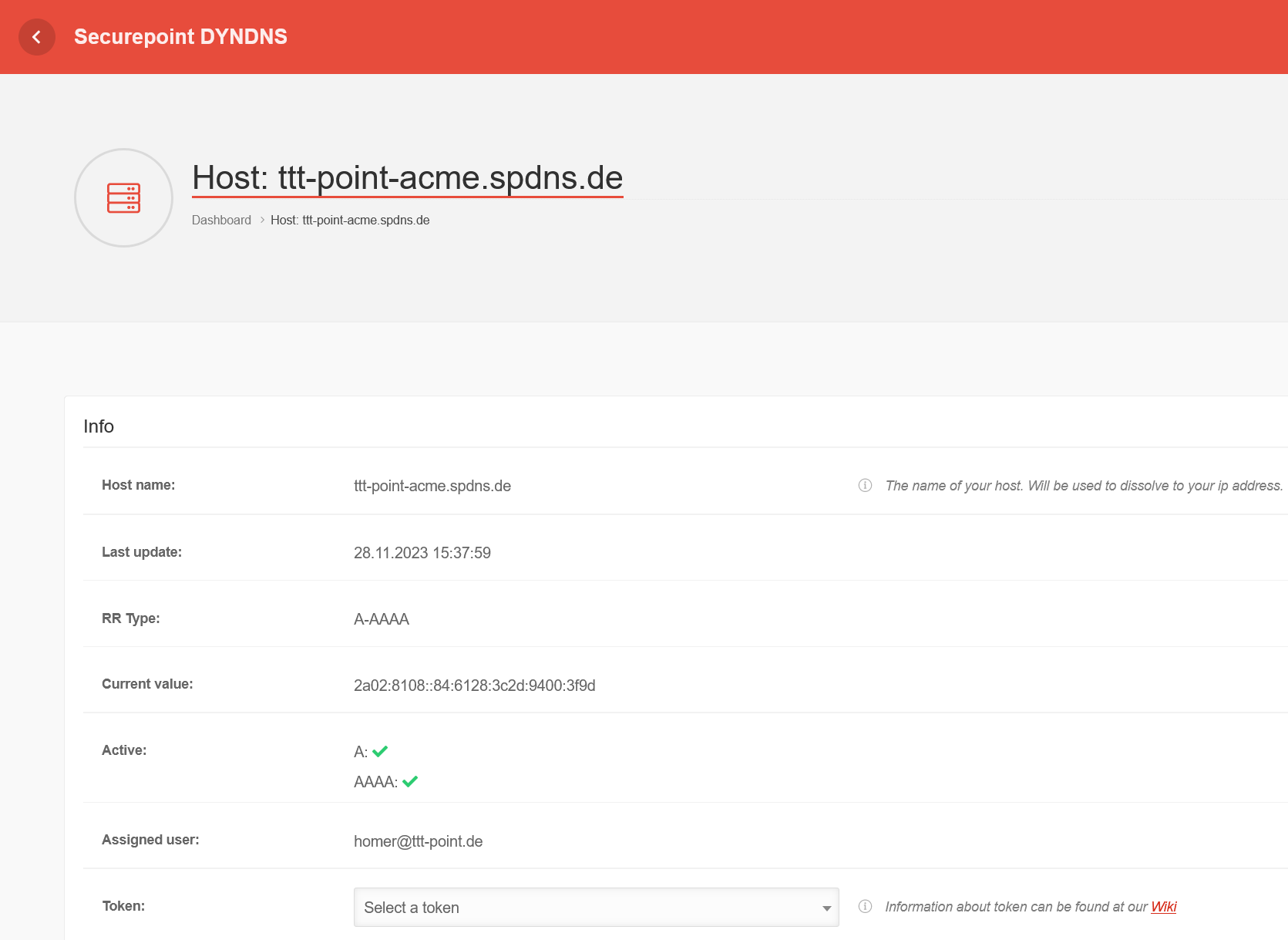
spDYN To generate the certificates, the ACME token must first be generated in the spDYN portal.
Within the spDYN portal, the corresponding host must be opened.
- Call up spDyn Host
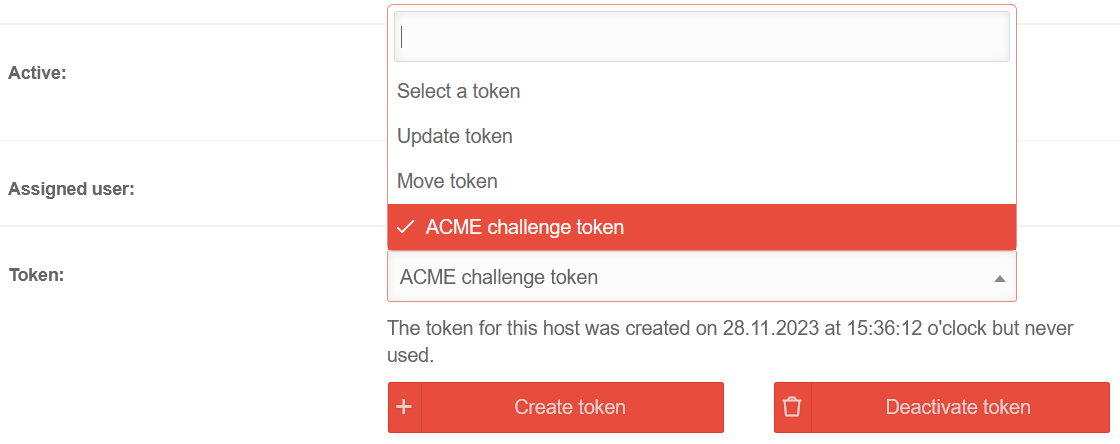
- Select the ACME Challenge Token from the Token drop-down menu.
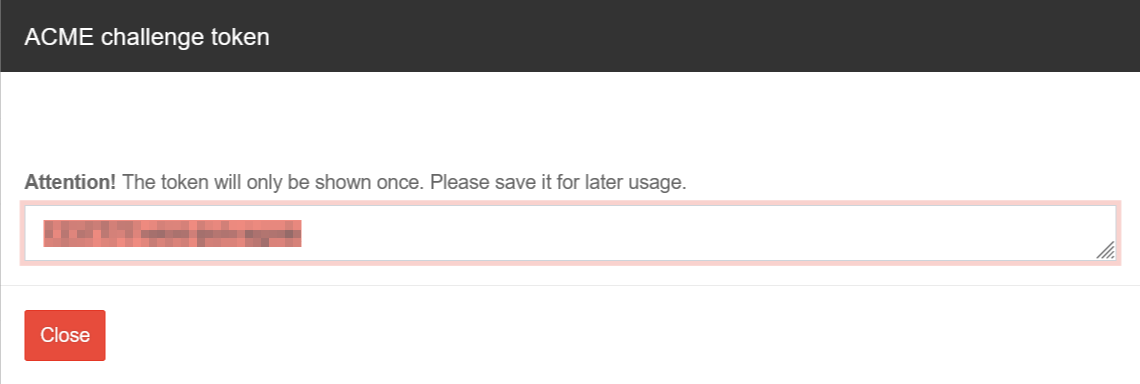
- Generate token
notempty The token is displayed once during generation and cannot be displayed again.
The token should be noted and stored safely.
Renewal of ACME certificates
The renewal of the ACME/Let's Encrypt certificates takes place via the nameservers used, which are configured under Area ACME (see above)
ACME Certificates
After completing the previous steps, the actual certificate can now be generated. A click on in the Certificates tab opens the corresponding dialog.
Import certificates / CAs
Certificates and CAs can be imported with the or button.
Import format
Certificates and CAs to be imported into a UTM must be in the format .pem or .p12 (pkcs12).
Certificates can be converted with the tool openssl - available for all common platforms (part of Linux, call via console) - and the following commands:
| Certificate | Command |
|---|---|
| X509 to PEM | openssl x509 -in certificatename.cer -outform PEM -out certificatename.pem |
| DER to PEM | openssl x509 -inform der -in certificate.cer -out certificate.pem |
| P7B to PEM | openssl pkcs7 -print_certs -in certificate.p7b -out certificate.pem |
Error message during import
During import, the error message "The certificate format is not supported..." may appear.
Password protected certificates in pkcs12 format (.p12 , .pfx , .pkcs12) in conjunction with older ciphers can trigger this error.
Import is usually possible if in the tab General the option Support legacy cryptographic algorithms On is enabled.
notempty Requires a This will interrupt all connections (incl. VPN connections) to the UTM!
Options for importing certificates:
- Convert certificate to *.pem
Certificates can be converted with the tool openssl - available for all common platforms (part of Linux, call via console) - and the following commands:
openssl pkcs12 -in Zertifikat.pfx -out Zertifikat.pem -nodes
Alternatively with the help of an online service
- CLI commands to allow certificate import with obsolete ciphers in the UTM
extc global set variable GLOB_ENABLE_SSL_LEGACY value 1
appmgmt config application "securepoint_firewall"
appmgmt config application "fwserver"
system reboot
notemptyRequires a This will interrupt all connections (incl. VPN connections) to the UTM!
cli> extc global get variable GLOB_ENABLE_SSL_LEGACY variable |value ----------------------+----- GLOB_ENABLE_SSL_LEGACY|0 cli> extc global set variable GLOB_ENABLE_SSL_LEGACY value 1 OK cli> extc global get variable GLOB_ENABLE_SSL_LEGACY variable |value ----------------------+----- GLOB_ENABLE_SSL_LEGACY|1 cli> appmgmt config application "securepoint_firewall" cli> appmgmt config application "fwserver"
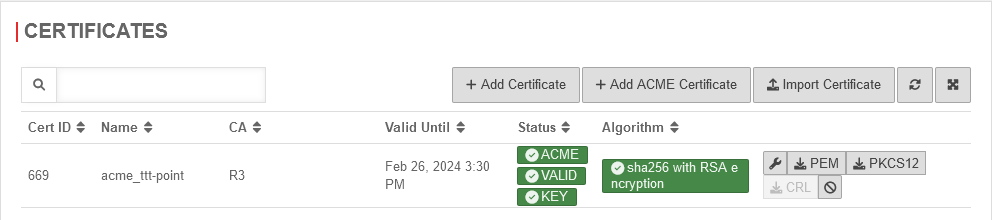
Frequent status messages:
| Status | Description | Note |
|---|---|---|
| KEY | The public and private key are present | It can be encrypted and decrypted: |
| VALID | The certificate is valid | It can be encrypted and decrypted: |
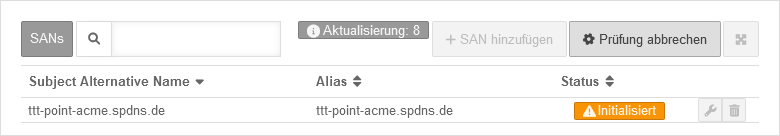
| INIT | The certificate is being initialized (ACME certificates only) | |
| KEY | The private key is not present | It can only be encrypted, but not decrypted. |
| UNABLE TO GET CERTIFICATE CRL | No current CRL could be found. | |
| UNABLE TO GET LOCAL ISSUER CERTIFICATE | The local issuer cannot be found. This occurs when the issuer certificate of an untrusted certificate cannot be found. |
|
| certificate has expired | The certificate has expired. The notAfter date is before the current time. |
|
| certificate is not yet valid | The certificate is not yet valid: the notBefore date is after the current time. | |
| CRL is not yet valid | CRL is not yet valid | |
| CRL has expired | CRL has expired | |
| certificate revoked | The certificate has been revoked. | In production environments, revoked certificates should not be restored. In this case, creating a new certificate is usually the better solution. |
| unsupported or invalid name syntax UNSUPPORTED_CONSTRAINT_SYNTAX |
Unsupported or invalid name constraint syntax | The name constraint format is not considered: for example, an email address format of a form not mentioned in RFC3280. For example, a -. |
| CRL lokal generiert | The CRL was created on this device | Either it is a certificate that was created locally, or no matching CRL has been imported (yet). |
| CRL importiert | The CRL was imported |
notempty Further status messages can be found in the Documentation of OpenSSL©.
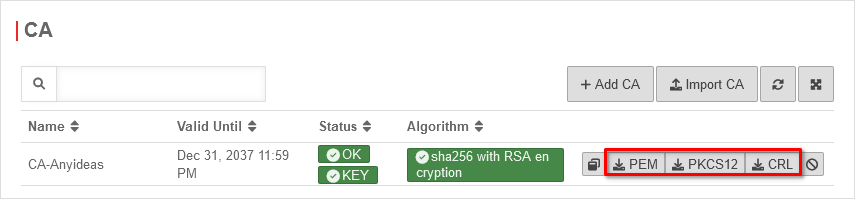
Export certificates / CAs
Revoke certificates / CAs
| Tab CA / Certificates | ||
| Revokes a certificate or a CA. The security prompt must be confirmed with Yes. If multiple certificates are to be revoked, the display of the security prompt can be temporarily disabled.
|
UTMuser@firewall.name.fqdnAuthentifizierung 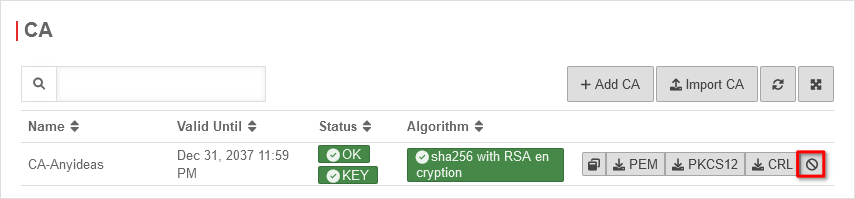 Revoke certificates / CAs Revoke certificates / CAs
| |
| Revoke | ||
| Displays all revoked CAs and certificates with associated CAs | 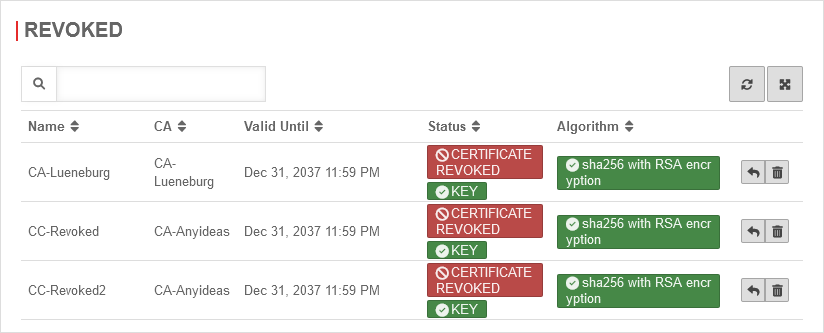 | |
| Unblocks a CA or certificate and restores it. This should only be done for local CAs or certificates whose CRL has not yet been exported! | ||
| Deletes the certificate. This should only be done for local CAs or certificates that have not been used in production environments! | ||
| CRLs | ||
| Displays all CAs and certificates with their status and the type of CRL | 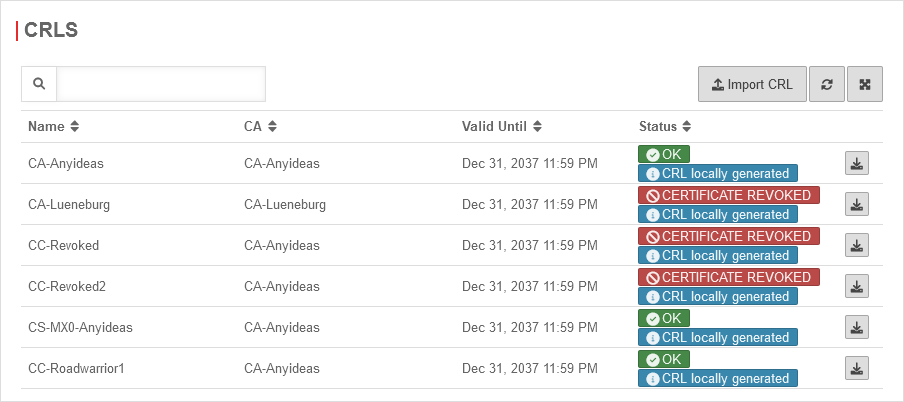 | |
| Exports the CRL of a CA or certificate | ||
| Imports a CRL | ||
| ACME | ||
| On | Enables ACME services (Automatic Certificate Management Environment) See ACME Certificates | |