notempty
Last adaption: 03.2022
- Note for Well-Known Ports
Keyboard and screen on the UTM
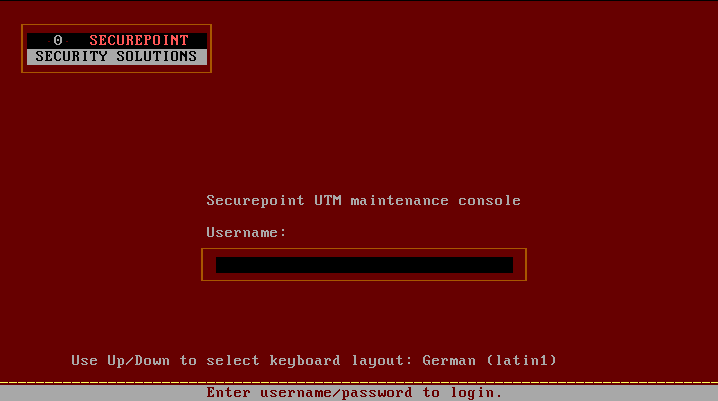
The built-in VGA port and a USB port allow direct access to the UTM with monitor and keyboard:
- Username: admin
- Password: insecure
web interface
Open the web interface via the IP address of the UTM (factory setting: https://192.168.175.1) and the according port
Administration Interface
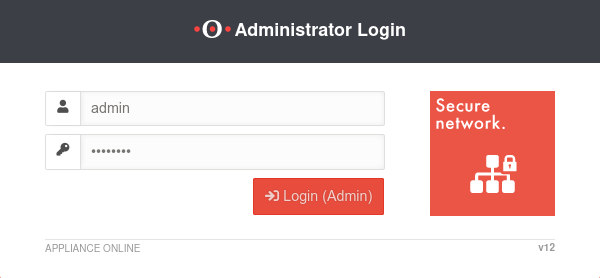
- Administration interface: Port 11115 (factory setting)
Setting in menu Tab Appliance Settings
Box
- The start of e.g. Google Chrome or Edge is done with the start parameter --explicitly-allowed-ports=xyz.
- For Firefox, a string variable with the value of the port to be released is created in the configuration (about:config in the address bar) under network.security.ports.banned.override.
- It is possible to create a temporary policy for chromium-based browsers to allow its use.
This is strongly discouraged for safety reasons!
- Administration Web Interface: Port 11115 (Factory Default)
Setting in Menu Tab Appliance Settings
BoxWebserverAdministration Webinterface Port: 11115
- Username: admin
- Password: insecure
Change in menu Tab Administration Button
or via CLI:
name.firewall.local> manager new hostlist 192.0.192.192/32
User-Webinterface
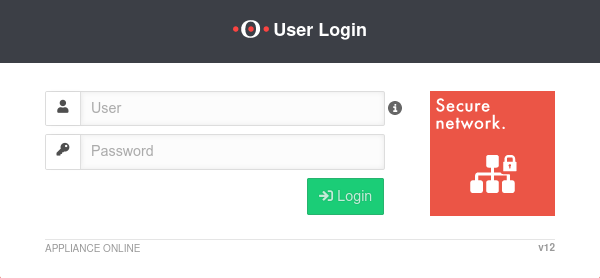
- User web interface: Port 443 (factory setting)
Setting in menu Tab Appliance Settings
Box
Factory setting: https://192.168.175.1:443
In order for the user interface to be displayed at all, must:
- A user must be created
- The user must be a member of a group that has the permission Userinterface (see User Management)
- If the access is not from the internal network (zone internal) a firewall rule or an implicit rule is required Section Vpn
CLI
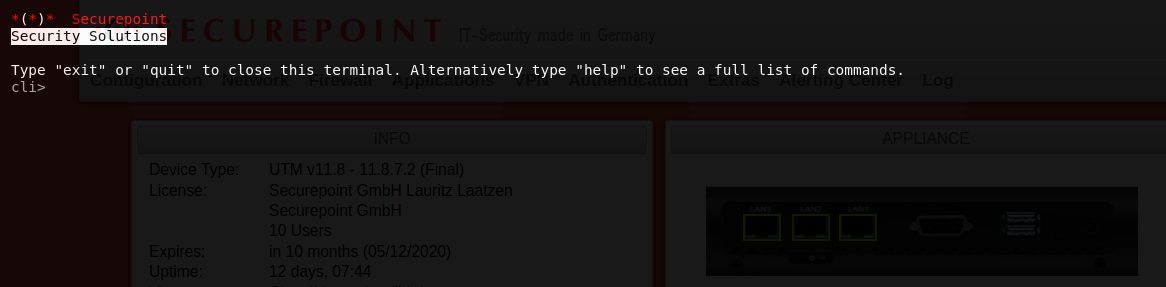
Command Line Interface
Command overview here.
Webinterface
SSH
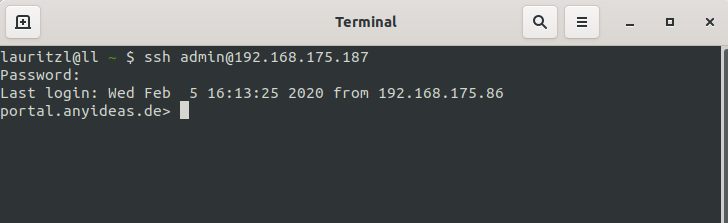
Access as an administrator is also possible via SSH.
With the SSH client under Linux, the command ssh user@<IP address>
Further notes in the article about access with SSH is sufficient.
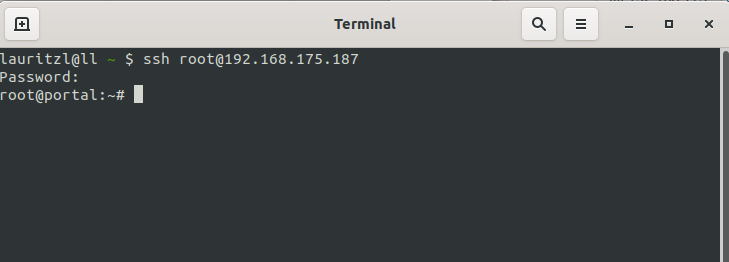
Call Command Line Interface with the command spcli.
Root permission is given to
- Support-User, if it was specified when creating
- Users with the user name root and membership of a group with Administrator permission
Serial interface
The following settings must be used to use the serial interface:
- 38400 baud (for CLI)
- 115200 baud (for Bios)
- 8 data bits
- 1 stop bit
- No parity/handshake
Monitor failed logins
The log can be viewed in the web interface under .
Alternatively, the data can also be retrieved with the following CLI command:
alertingcenter alerts get