Warnung: Der Anzeigetitel „“ überschreibt den früheren Anzeigetitel „Captive Portal mit einem lokal generierten Zertifikat“.
- No changes to the Server Settings are required any more
- ACME wildcard certificates can be used for the landing page
12.1.9 (externe & lokale Zertifikate) 11.8.7 (externe Zertifikate) 11.8.7 (lokale Zertifikate) 11.7.3 (externe Zertifikate) 11.7.3 (lokale Zertifikate) 11.7
Preliminary remark
The captive portal redirects an HTTP client in a network to a special web page (so-called landing page) before it can connect normally to the Internet. Thus, acceptance of the condition of use must take place and additional authentication can be configured.
Planning
The following aspects should be considered before configuration:
- For which networks should the captive portal be configured?
Will all potential users be reached exclusively? - How and by whom will the terms of use be written?
- Should authentication take place?
- Which internal web servers are not allowed to be reached from the network behind the captive portal?
Jus a few preparations must be made to use the captive portal:
- A certificate must be available for the landing page
- Implicit and port filter rules must allow access
The host name of the portal page is configured under Area General.
Generate local certificate
The landing page of the captive portal is an HTTPS website. A certificate is required for a browser to classify this page as trustworthy.
- At Area CA a CA must be created
- At Area Certificates a Server- certificate must be created. A separate certificate should be created for the captive portal so that it can be revoked if necessary without affecting other connections or applications.
How to create a certificate on the UTM can be read here.
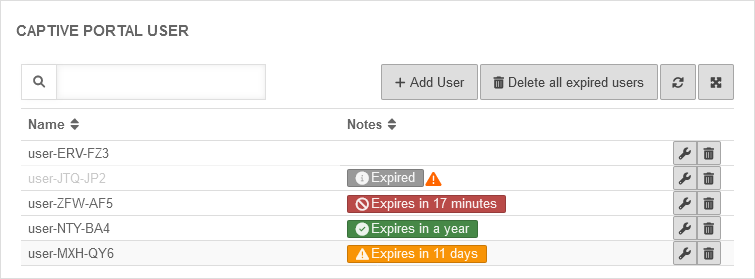
Captive Portal User
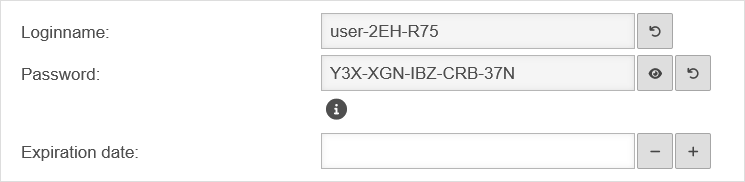
Add user
Captive Portal users can be managed by:
- Administrators
- Users who are members of a group with the permission Userinterface Administrator .
They reach the user administration via the user interface.