notempty
- Adding headers for greylisting can be disabled
Configuration of the Mailrelay
The Securepoint UTM appliance can receive emails using the mailrelay and forward them to a mail server in the internal network. The mail relay checks the received emails and divides them into an appropriate category. Based on the category, it is decided whether an email is forwarded to the internal mail server or not.
To protect against spam or to relieve the [Mailfilter] further options can be configured. More than 90% of spam does not come from regular mail servers, but rather from private and work computers compromised by viruses and Trojans. On the other hand, checking target email addresses, greylisting and the greeting pause have proven to be effective functions.
Preconditions
Settings on the provider side
In order to ensure a smooth participation in the mail traffic, some conditions must be fulfilled:
- A fixed IP address.
- An A record on the DNS server of the provider that resolves to this IP (e.g. mail.ttt-point.de).
- An MX record that determines the address at which the mail server of a domain can be reached (e.g. mail.ttt-point.de).
- A PTR record that resolves the fixed IP back to the MX record (reverse DNS).
These are all settings that have to be made by the provider and NOT on the Securepoint Appliance!
Note: Since a certain amount of storage space must be available for rejected mails or mails that could not yet be delivered to the internal mail server, the hardware recommendations should be considered without fail!
Set of rules
To enable other mail servers to deliver mails to the mail relay, access to the external interface with the SMTP protocol must be allowed in the port filter:
Note: If there is no other connection available besides the Internet connection with the IP over which the mail is sent, it must be ensured that ONLY the mail server is allowed to send mail via SMTP. Otherwise a single computer in the network compromised by a Trojan could seriously disrupt the sending of mails or even make it completely impossible, because it spreads spam and malware with the public IP and is listed on corresponding blocklists for spammers within a very short time.
Important: There must be no port forwarding for SMTP. This would ensure that the mails are forwarded past the mail relay!
Email address
Under Global email address: a postmaster address should be configured. Otherwise undeliverable mails will remain on the disk space. This can cause the available memory to become insufficient at some point and mails to no longer be accepted.
Basic configuration of the mailrelay for receiving mails
The configuration of the mailrelay takes place under .
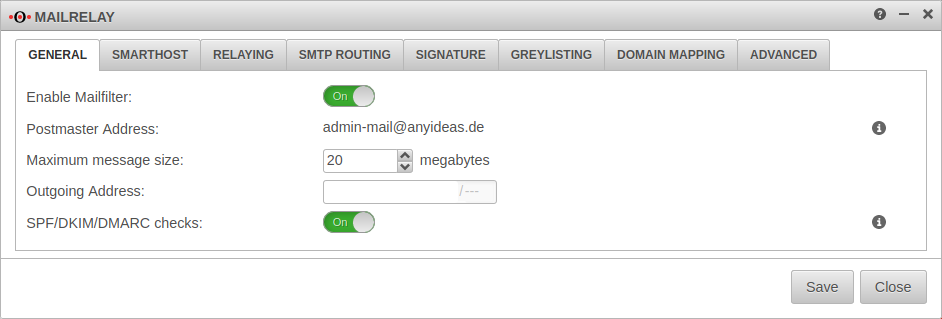
General
| Function | Value | Description |
|---|---|---|
| Activate mail filter: | On | Activate |
| Postmaster Address: | admin-mail@anyideas.de | Hier muss eine korrekte Mail-Adresse hinterlegt sein. Diese E-Mail-Adresse wird im Dialog im Feld Globale E-Mail Adresse festgelegt. Änderungen sind nur dort möglich. |
| Maximale Nachrichtengröße: | 20 Megabytes | Maximale Größe der Mails in Megabytes, die vom Mailrelay angenommen werden. |
| Ausgehende IP-Adresse: | Bei Multipath-Routing kann hier eine ausgehende Schnittstelle durch die IP-Adresse angegeben werden. Auch die Kommunikation aus dem internen Netz läuft dann über diese IP-Adresse. Auf dem Mailserver und seiner Firewall müssen weitere Einstellungen vorgenommen werden, damit Mails von dieser IP-Adresse angenommen werden. | |
| SPF in 11.8.7 |
Aus | Ermöglicht Mailfilter Adds RFC 8601 Authentication-Results Header to email. Not performed for mails sent by SASL-authenticated users or mails coming from "trusted hosts", i.e. hosts that have an entry in the relaying list with action RELAY and option "Connect" or no option. Weitere Hinweise im Artikel zum Mailfilter |
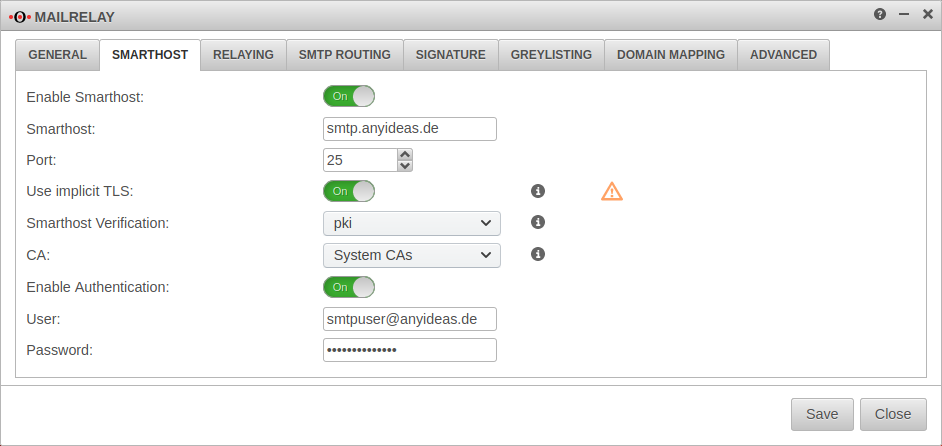
Smarthost
Settings for a Smarthost are only required if such a setting is required for outgoing mails. This is the case, for example, if no own mail server is operated or no fixed public IP address is available.
| Caption | Value | Description |
|---|---|---|
| Enable Smarthost: | On | activates the Smarthost function. |
| Smarthost: | Mail server that is to receive and send outgoing mails.(sample address) | |
| Port: | 465 | Mail port for external mail server 25: Default port for smtp (default) 465: default port for implicit TLS 587: default port for STARTTLS |
| Use implicit TLS: New from 11.8.4 |
Off | By default (deactivated), a connection is first established via smtp and then attempts to initiate TLS encryption with the remote terminal. |
| On | When activated, the connection is first encrypted with TLS before smtp communication is established. If the remote terminal does not control TLS, no connection is established. The TLS version is configured under . | |
| Smarthost Verification: | There is no verification of the smarthost. | |
| The smarthost is verified by default installed root CAs or a self-signed CA. CA: (Default) Alternatively, a CA (previously created or imported under ) can be selected for authentication. | ||
| The Smarthost is only verified using the DANE protocol (RFC 6698) and must support this protocol.. The DANE protocol requires the mandatory activation of DNSSEC | ||
| Enable Authentication: | On | Enables authentication on the smarthost mail server. |
| User: | Credentials | |
| Password: | Credentials |
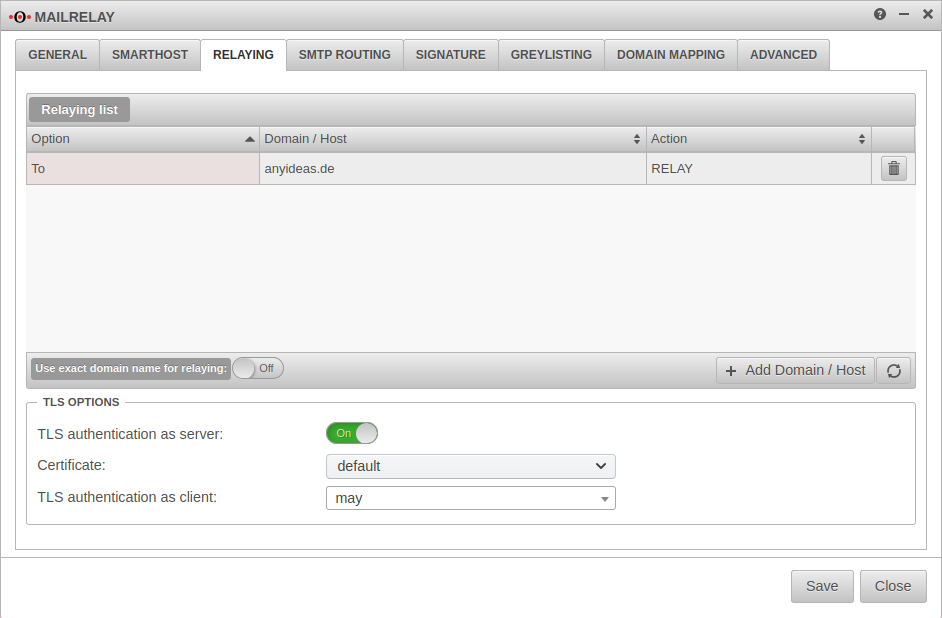
Relaying
Relaying list
Here it is configured which mails are accepted by the Securepoint appliance and forwarded to the internal mail server. Relaying can be allowed for certain hosts or certain domains.
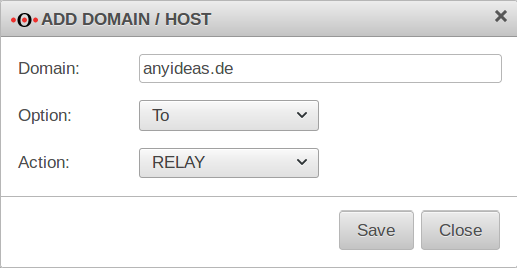
Add an entry with the button
| Caption | Value | Description |
|---|---|---|
| Domain: | Email domain name or IP address | |
| Option | The action is applied to all events. | |
| The sender domain is evaluated here. Example: Domain: ttt-point.de - This applies to all mails with the domain ttt-point.de in the sender. Since the sender domain can easily be faked, this option is to be used only after careful examination. | ||
| The recipient domain is evaluated here. Example: Domain: anyideas.de - This concerns all mails with the domain anyideas.de in the recipient. | ||
| Here the IP, hostname or domain of the mail server that wants to deliver the mail is evaluated. Example: Domain: ttt-point.de - Affects all mails from mail servers in the domain ttt-point.de - regardless of the sender or recipient of the mail. | ||
| Action | Mails that meet the relevant conditions will be accepted and forwarded. | |
| Mails are rejected. | ||
| Mails are accepted and delivered to a local mailbox, but not forwarded. |
In order to relay all mails intended for recipients of your own domain, the following entry must be configured:
| Domain / Host hizufügen | |
|---|---|
| Domain | anyideas.de
|
| Option | |
| Aktion | |
Use exact domain name for relaying:
On The relay reacts only to the domain name entered in the list and not to unregistered subdomains or extensions.
Example: Domain entered in the relay list: anyideas.de
TLS Settings
| Caption | Default | Description |
|---|---|---|
| TLS encryption as server: | On | If TLS is deactivated, mails are sent over unencrypted connections! |
| Certificate: | The mailrelay uses a self-signed certificate for transport encryption. Optionally, a certificate whose CN corresponds to the UTM host name can be imported under . | |
| TLS authentication as client: | Uses TLS if it is offered. | |
| Always uses TLS. Connection with servers that do not offer TLS will be cancelled. | ||
| Authenticates and uses TLS to DANE-compliant servers, if offered. |
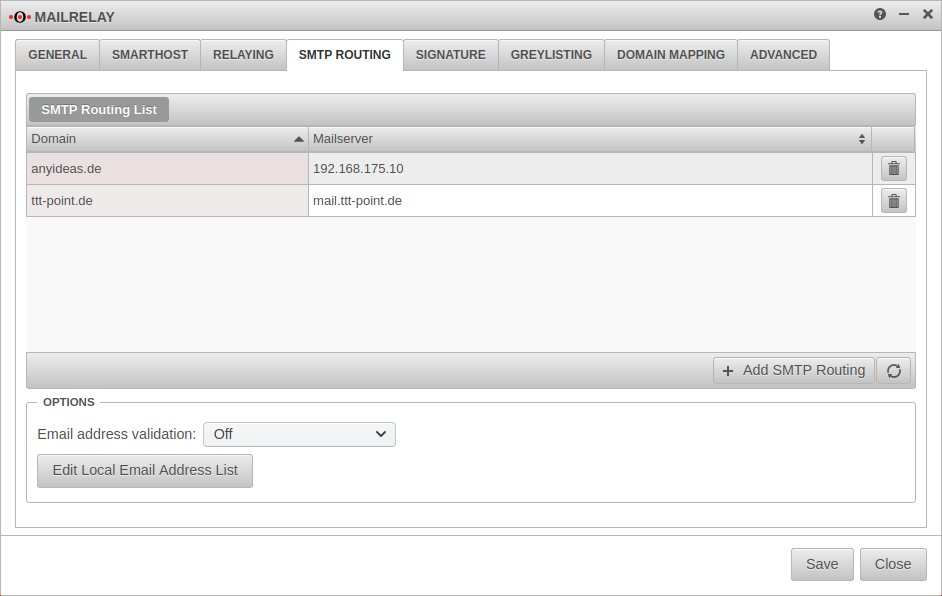
SMTP Routen
SMTP Routing List
Here you have to set to which mail server a received mail should be forwarded. If this does not happen, the mail relay evaluates the MX record of the recipient domain - which points to the relay itself! A so-called "loopback" is then detected, which cancels the acceptance of the mail with a corresponding error message. In the following, further domains can be forwarded to the same or to other mail servers.
With the button further routes are created.
| Required information: | |
|---|---|
| Domain: | anyideas.de (or the corresponding mail domain)
|
| Mailserver: | either as FQDN or the IP address
|
Options
In this section you can configure the verification of the destination email address. It causes mails to unknown recipients to be rejected. On the one hand the attempt to deliver spam to "invented" recipients is effectively prevented, on the other hand legitimate senders receive feedback that their mail could not be delivered, for example because they have committed themselves to the recipient address.
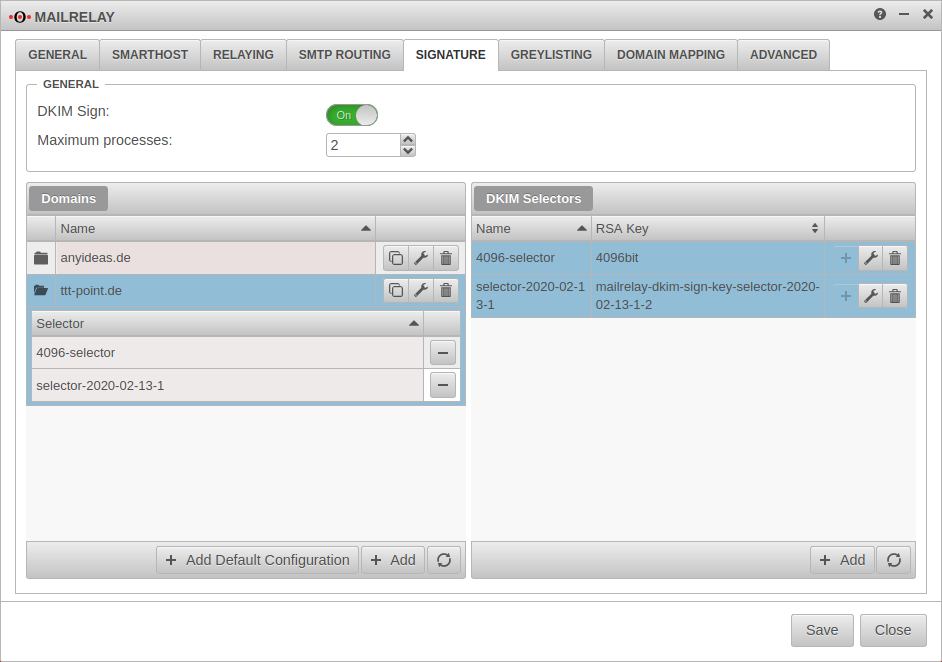
Signing
New in 11.8.8 Outgoing emails can be signed using DomainKeys Identified Mail. The individual segments in the header and the body are signed separately, so that forwarding a mail via a mail server and changing the mail header does not destroy the signature.
| Caption | Value | Description | |
|---|---|---|---|
General
| |||
| DKIM Sign: | Off (Default) | At On activation, DKIM signing can be used. | |
| Maximum processes: | 2 | determines the number of filter processes and smtp instances used for DKIM signing | |
Domains | |||
| Adds a default configuration. For this purpose, an RSA key is generated (Selector) and assigned to each mail domain entered as SMTP route | |||
| Adds a domain name record | |||
| / | Opens / closes the overview that shows the selectors for a domain that are used for signing. | ||
| Removes a selector from a domain entry | |||
| Displays the DNS Settings | |||
| Plain text | Nein | With Yes activation the DNS settings will be displayed in one window. If a separate authoritative DNS server is operated, this value can be copied directly into a BIND zone file. | |
| Copies the entry to the clipboard To assign the subdomain at the DNS hoster. | |||
| Copies the entry to the clipboard This is the public part of the RSA key, which must be stored in the TXT record of the mail domain. Can also be found under Public part (of the associated key) | |||
| Edits the respective domain name | |||
| Deletes the entry | |||
DKIM Selectors | |||
| Adds a DKIM selector | |||
| Adds the selector to the active (blue highlighted) domain entry. | |||
| Edits the entry | |||
| Name: | selector-2020-02-13-1 | Name of the selector | |
| RSA Key | Key name | Select existing key or create a new key pair with the button | |
| Hash algorithm: | sha256 | Algorithm used | |
Advanced settings
| |||
| Email Header Canonicalization: | Canonicalize the email headers. Since various sources (like relaying mailservers) might alter the email headers, it is possible to use a canonicalized version of those headers before creating the signature and also before validating it - the headers itself will stay unaffected. This will make the digital signing more reliable. | ||
| Do not canonicalize the email headers. | |||
| Email Body Canonicalization: | Remove trailing blank lines and cleanup whitespaces. Since various sources (like relaying mailservers) might alter the email body, it is possible to use a canonicalized version of the body before creating the signature and also before validating it - the body itself will stay unaffected. This will make the digital signing more reliable. | ||
| Remove trailing blank lines only. | |||
| Sign default email headers: | Yes | Default: h=From:Reply-To:Subject:Date:To:Cc:Resent-Date:Resent-From:Resent-To:Resent-Cc:In-Reply-To:References:List-Id:List-Help:List-Unsubscribe:List-Subscribe:List-Post:List-Owner:List-Archive; | |
| Email headers to be signed: | » ✕From » ✕Date » ✕Subject » ✕To » ✕List-Unsubscribe » ✕List-ID |
Email headers to be signed. | |
Optional Settings
Further settings are recommended, but not mandatory for operative use:
Greylisting
Greylisting causes the delivery attempt of an unknown mail server to be initially rejected. Usually, spambots do not make any further delivery attempts, so that the delivery of spam was already successfully prevented before the mail had to run through the spam filter engine.
A regular mail server, on the other hand, will make another successful delivery attempt after a certain period of time.
The following configurations are possible:
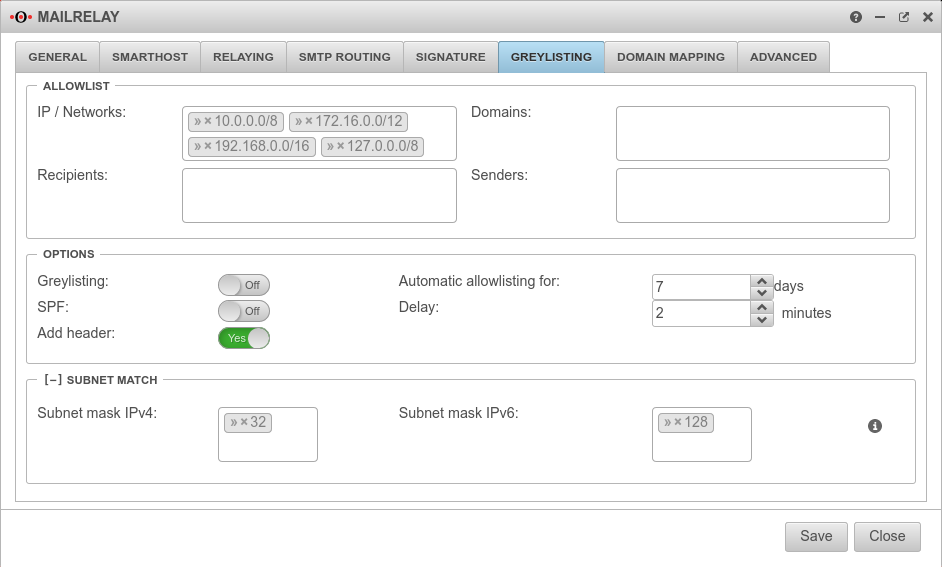
Allowlist Allowlist | ||
| Caption | Default | Description |
|---|---|---|
| IP / Networks | » ✕10.0.0.0/8 » ✕172.16.0.0/12 » ✕192.168.0.0/16 » ✕127.0.0.0/8 | The default are the private IP address ranges and the loopback address. With a click into the clickobx you can add further networks and single hosts (e.g.:» ✕203.0.113.113/32) |
| Domains | Here single Mailserver domains can be added e.g.: smtp.anyideas.de The domain of the mail server does not have to be identical with the e-mail domain of the sender. Example: Sender user@ttt-point.de sends via the mail server » ✕smtp.anyideas.de | |
| Recipient | Individual recipients can be added here, e.g: » ✕MailUser@ttt-point.de | |
| Sender | Individual senders can be added here e.g.:{cb | |
Settings Settings | ||
| Greylisting: | Aus | An activates the function Delivery attempts from unknown mail servers are initially rejected. |
| SPF: | Aus | If the Sender Policy Framework of the sender domain is correctly entered in the DNS, the mail will be delivered without delay if On is activated. |
| Add header: New as of v12.2.2 | Yes | By default, an additional greylisting entry is added for each recipient listed in the mail header. This can cause problems in case of many recipients. When disabled no, no greylisting headers are inserted. |
| Automatic allowlisting for: | 7 Days(Default) | days(Default) : For this period, after a successful delivery mails will be accepted immediately. |
| Delay: | 2 Minutes (Default) | minutes(Default): The period of time that the sending mail server is given to make another delivery attempt. |
Subnet MatchSubnet Match | ||
| Subnet mask IPv4: | » ✕32 | Instead of the sending server having to have the exact IP address as before, this can be changed so that, for example, only the first 2 or 3 octets have to match. This enables whitelisting even if the sender has several mail servers. Possible values: (Only one value can be entered.) » ✕32 (Single Host) » ✕24 Subnet, with match of first three octets » ✕29 Any value via keyboard input. |
| Subnet mask IPv6: | » ✕128 | |
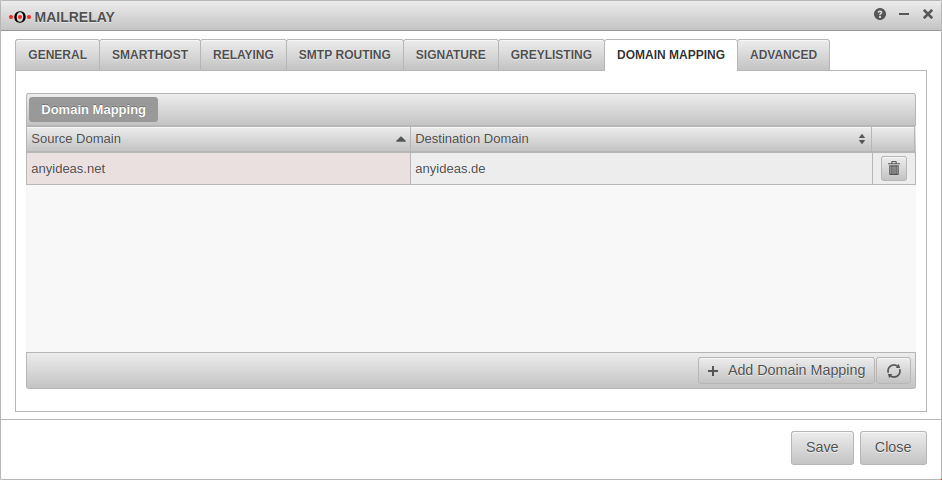
Domain Mapping
Domains can be mapped to receive incoming mails to e.g. user@anyideas.net also under user@anyideas.de.
With the mapping between two domains can be activated.
To do this, a Source-Domain: and a Destination Domain: must be specified.
Advanced Settings
Here some further options to avoid spam can be found, each of which can be activated individually:
| Function | Description |
|---|---|
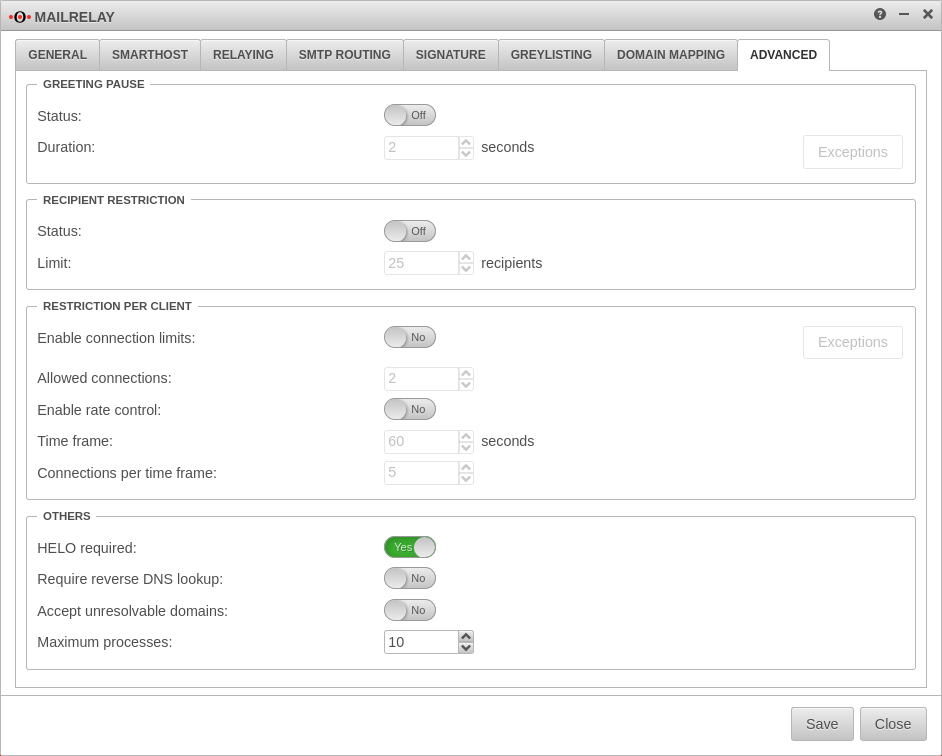
Greeting Pause
| |
Greeting Pause Status:
|
On activates the function. |
| Duration: | 2000 Miliseconds (default value). Time the mail relay delays the greeting message. If the connected client sends SMTP commands before this time has elapsed, its request is rejected at the RCPT TO command with a "Protocol Error". can be defined as network or host IP address for known mail servers. Successfully waiting mail servers are also automatically whitelisted for one day. |
Recipient Restriction Recipient Restriction | |
| Status: | Off |
| Limit: | 25 recipients This option blocks mails that have more than one configurable number of recipient addresses. |
Restriction per client Restriction per client | |
| Enable connection limits: | Off can be defined as network or host IP address for known mail servers.
|
| Allowed connections: | 1 Number of (client) connections, per connected mail server. |
| Enable rate control: | Limits the number of (client) connections per connected mail server within a time frame. |
| Time frame: | 60 seconds |
| Connections per time frame: | 5 |
Others Others | |
| HELO required: | On Should absolutely remain activated (default). This switch exists to ensure backward compatibility. |
| Require reverse DNS lookup: | Off Requires a reverse lookup (address) to exist for connected mail servers. The forward lookup must return the IP address. |
| Accept unresolvable domains: | Off Allows sender addresses whose domain cannot be resolved via DNS. |
| Maximum processes: | 10 Controls global number of concurrent connections to mail relay (and attached filtering and anti-spam processes) |
Configuration of the mailrelay for outgoing mails
To make sure that no spam or malware can be sent from your own network, the mail relay can also be used for outgoing mails.
Set of rules
To allow access to the mail relay, the hosts authorized to send mail must be allowed access to the corresponding interface of the Securepoint appliance (depending on the zone in which the hosts are located) via the SMTP protocol. Depending on the requirements, this can be a single host (e.g. the mail server), a group of hosts or the entire network. It is important that all applications that are to send mails via the mail relay have entered the corresponding firewall interface as SMTP server or smarthost.
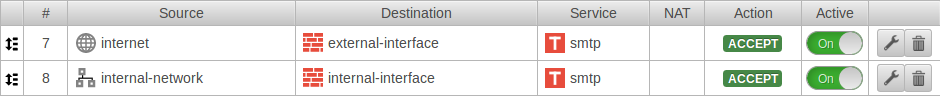
For example, to allow the internal network access to the mail relay, the set of rules can be created with the predefined network groups:
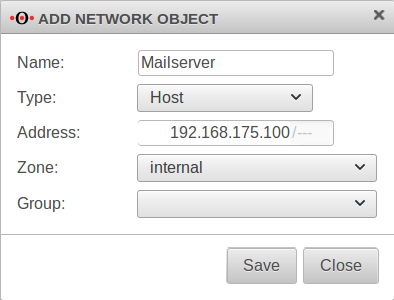
If only the mail server is to be able to send mails, it must first be created as a network object:
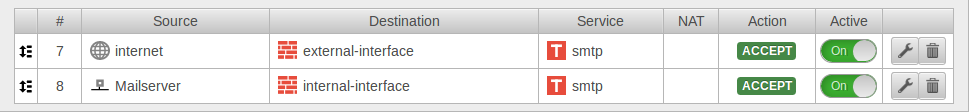
This object can then be used in the firewall rule:
If a certain group of computers in the internal network is to be allowed to use the mail relay, these computers must be created as network objects. These can then be combined in a group (e.g. "SMTP Authorized").
Configuration Relaying
In order for the mailrelay to accept mails from the internal network or from the mail server, the settings in the Relaying} tab must be supplemented by a corresponding entry. The network address of the corresponding subnet or the IP address of the relevant computer serves as criterion:
| Domain | 192.0.2.0/30 or 192.0.2.192 These are sample IPs for the internal mail servers. These have to be replaced by individual addresses! |
| Option | |
| Action |
Conclusion
The UTM can now check incoming and outgoing mails for spam and viruses.