notempty
- Local emails can be signed
Configuration of the Mailrelay
The Securepoint UTM appliance can receive emails using the mailrelay and forward them to a mail server in the internal network. The mail relay checks the received emails and divides them into an appropriate category. Based on the category, it is decided whether an email is forwarded to the internal mail server or not.
To protect against spam or to relieve the [Mailfilter] further options can be configured. More than 90% of spam does not come from regular mail servers, but rather from private and work computers compromised by viruses and Trojans. On the other hand, checking target email addresses, greylisting and the greeting pause have proven to be effective functions.
Preconditions
Settings on the provider side
Um eine reibungslose Teilnahme am Mailverkehr zu gewährleisten, müssen einige Voraussetzungen erfüllt sein:
- Die UTM muss über eine feste IP-Adresse verfügen. (z.B. 195.4.169.36)
- Auf dem Server des DNS-Providers existiert ein A-Record, der auf diese IP-Adresse auflöst. (Beispielabfrage für den A-Record: <span title=">nslookup -q=a ttt-point.de
Server: UnKnown
Address: 192.168.175.1
Nicht autorisierende Antwort:
Name: ttt-point.de
Address: 195.4.169.36" style="border-bottom: 1px dotted black;"
><span title="host -t a ttt-point.de
ttt-point.de has address 195.4.169.36" style="border-bottom: 1px dotted black;"
>)
- Auf dem Server des DNS-Providers existiert ein MX-Record, der auf diese Adresse auflöst. (Beispielabfrage für den MX-Record: >nslookup -q=mx ttt-point.de
Server: UnKnown
Address: 192.168.175.1
Nicht autorisierende Antwort:
ttt-point.de MX preference = 10, mail exchanger = mx01.ttt-point.dehost -t mx ttt-point.de
ttt-point.de mail is handled by 10 mx01.ttt-point.de.) - Auf dem Server des Internet-Providers existiert ein PTR-Record, der korrekt auf den DNS-A-Record auflöst, der im MX-Record verwendet wird (reverse DNS). (Beispielabfrage für den PTR-Record: >nslookup -q=ptr 195.4.169.36
Server: UnKnown
Address: 192.168.175.1
Nicht autorisierende Antwort:
36.169.4.195.in-addr.arpa name = mx01.ttt-point.dehost -t ptr 195.4.169.36
36.169.4.195.in-addr.arpa domain name pointer mx01.ttt-point.de.)
These are all settings that have to be made by the provider and NOT on the Securepoint Appliance!
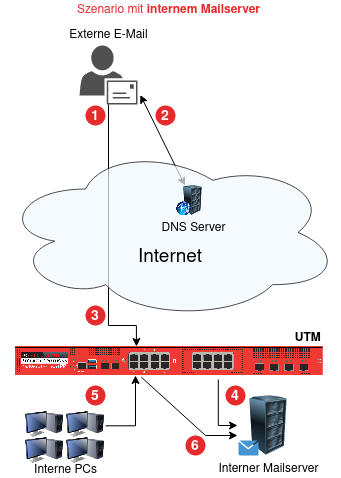
➊ E-Mail wird abgesendet
➋ DNS-MX-Record zeigt auf UTM
➌ E-Mail wird an die UTM zugestellt und verarbeitet (Mailfilter, Greylisting etc.)
- ➍
(gemäß Pfad unter Tab SMTP-Routen)
➎ E-Mail-Abfrage aus dem internen Netz
➏ Abfrage wird an den Mailserver weitergeleitet, der als SMTP-Route festgelegt wurde
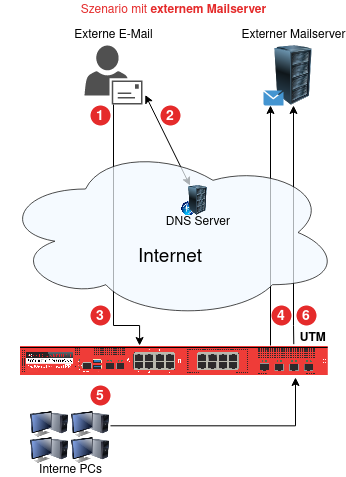
➊ E-Mail wird abgesendet
➋ DNS-MX-Record zeigt auf UTM
➌ E-Mail wird an die UTM zugestellt und verarbeitet (Mailfilter, Greylisting etc.)
- ➍
(gemäß Pfad unter Tab SMTP-Routen)
➎ E-Mail-Abfrage aus dem internen Netz
➏ Abfrage wird an den Mailserver weitergeleitet, der als SMTP-Route festgelegt wurde
Set of rules
To allow access to the mail relay, the hosts authorized to send mail must be allowed access to the corresponding interface of the Securepoint appliance (depending on the zone in which the hosts are located) via the SMTP protocol. Depending on the requirements, this can be a single host (e.g. the mail server), a group of hosts or the entire network. It is important that all applications that are to send mails via the mail relay have entered the corresponding firewall interface as SMTP server or smarthost.
For example, to allow the internal network access to the mail relay, the set of rules can be created with the predefined network groups:
Email address
Under Global email address: a postmaster address should be configured. Otherwise undeliverable mails will remain on the disk space. This can cause the available memory to become insufficient at some point and mails to no longer be accepted.
Basic configuration of the mailrelay for receiving mails
The configuration of the mailrelay takes place under .
General
| Caption | Value | Description | 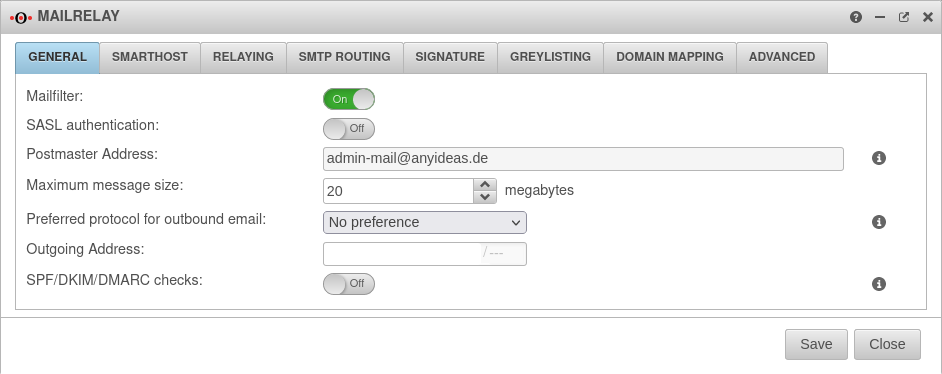 |
|---|---|---|---|
| Activate mail filter: | On | Activate | |
| SASL authentication: | Off | Enables SASL authentication, if activated | |
| Postmaster Address: | admin-mail@anyideas.de | A correct email address must be stored here. This email address is specified in the dialog in the Global email address field. Changes are only possible there. | |
| Maximum message size: | 20 Megabytes | Maximum size of the mails in megabytes accepted by the mail relay. A message appears in the mail filter view in the user interface about the rejection. | |
| Preferred protocol for outbound email: | Specifies whether the mail relay should preferentially establish outgoing connections with a certain protocol. This setting should only changed from its default in special cases (e.g., IPv4 behind NAT) and if problems to deliver mail arise. | ||
| IPv4 is preferred as protocol (e.g. IPv4 behind NAT) | |||
| IPv6 is preferred as protocol | |||
| Outgoing Address: | With multipath routing, an outgoing interface can be specified here by the IP address. Communication from the internal network then also runs via this IP address. Further settings must be made on the mail server and its firewall in order to accept mails from this IP address.
| ||
| SPF/DKIM/DMARC checks: | Off | Enables filtering for corresponding DKIM/DMARC/SPF-results in Mailfilter rules when enabled On. Adds RFC 8601 Authentication-Results Header to email. Not performed for mails sent by SASL-authenticated users or mails coming from "trusted hosts", i.e. hosts that have an entry in the relaying list with action RELAY and option "Connect" or no option. Further information in the article about Mailfilter
| |
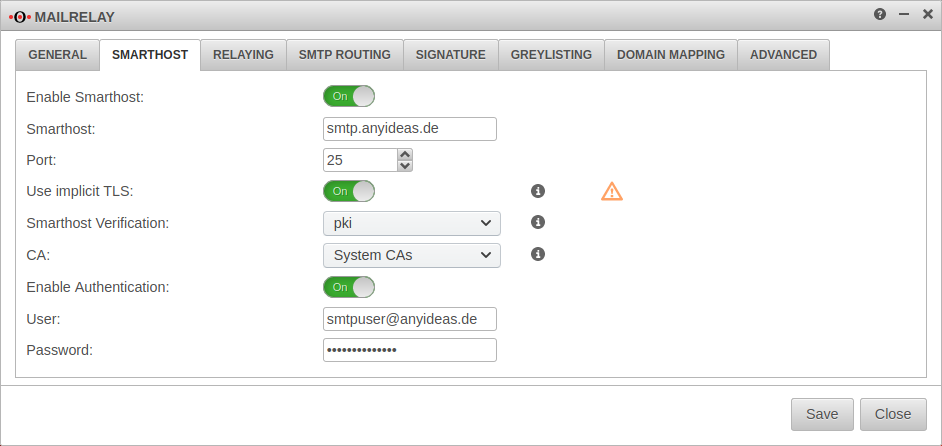
Smarthost
Settings for a Smarthost are only required if such a setting is required for outgoing mails. This is the case, for example, if no own mail server is operated or no fixed public IP address is available.
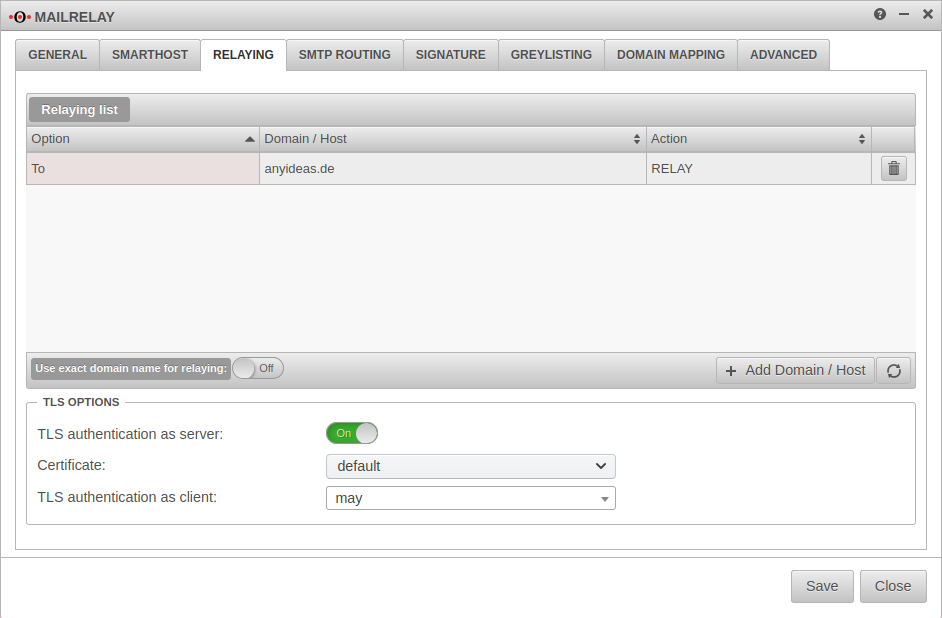
Relaying
Relaying list
Here it is configured which mails are accepted by the Securepoint appliance and forwarded to the internal mail server. Relaying can be allowed for certain hosts or certain domains.
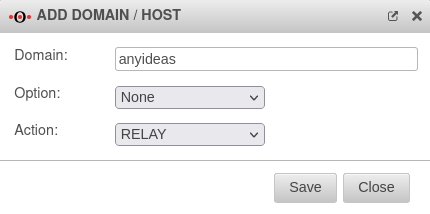
Add an entry with the button
In order to relay all mails intended for recipients of your own domain, the following entry must be configured:
| Domain / Host hizufügen | |
|---|---|
| Domain: | anyideas.de
|
| Option: | |
| Action: | |
Use exact domain name for relaying:
On The relay reacts only to the domain name entered in the list and not to unregistered subdomains or extensions.
Example: Domain entered in the relay list: anyideas.de
| On accepted by mailrelay: |
@anyideas.de |
|---|---|
| Off accepted by mailrelay: |
@anyideas.de @support.anyideas.de @anyideas.de.com |
| On accepted by mailrelay: |
Off accepted by mailrelay: |
|---|---|
| @anyideas.de | @anyideas.de @support.anyideas.de @anyideas.de.com |
TLS Settings
| Caption | Default | Description |
|---|---|---|
| TLS encryption as server: | On | If TLS is deactivated, mails are sent over unencrypted connections! |
| Certificate: | The mailrelay uses a self-signed certificate for transport encryption. Optionally, a certificate whose CN corresponds to the UTM host name can be imported under . | |
| TLS authentication as client: | Uses TLS if it is offered. | |
| Always uses TLS. Connection with servers that do not offer TLS will be cancelled. | ||
| Authenticates and uses TLS to DANE-compliant servers, if offered. |
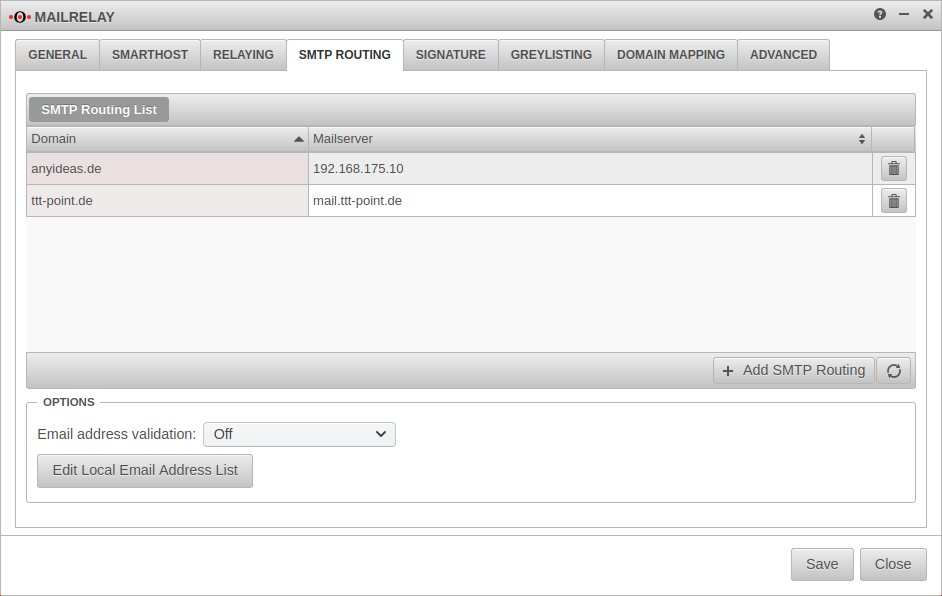
SMTP Routen
SMTP Routing List
Here you have to set to which mail server a received mail should be forwarded. If this does not happen, the mail relay evaluates the MX record of the recipient domain - which points to the relay itself! A so-called "loopback" is then detected, which cancels the acceptance of the mail with a corresponding error message. In the following, further domains can be forwarded to the same or to other mail servers.
With the button further routes are created.
| Required information: | |
|---|---|
| Domain: | anyideas.de (or the corresponding mail domain)
|
| Mailserver: | either as FQDN or the IP address
|
Settings
In this section you can configure the verification of the destination email address. It causes mails to unknown recipients to be rejected. On the one hand the attempt to deliver spam to "invented" recipients is effectively prevented, on the other hand legitimate senders receive feedback that their mail could not be delivered, for example because they have committed themselves to the recipient address.
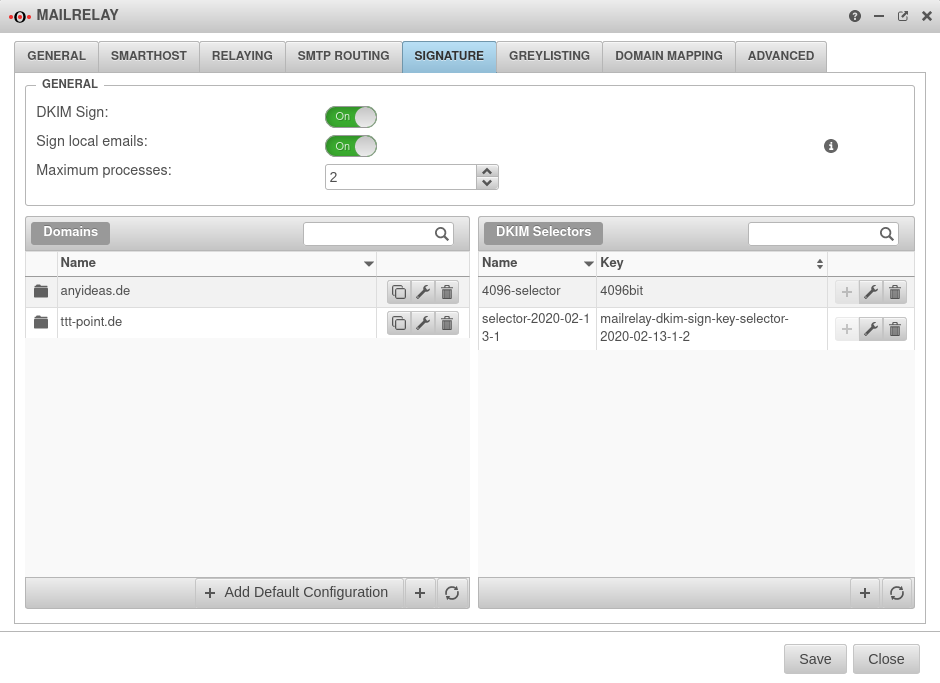
Signing
Outgoing emails can be signed using DomainKeys Identified Mail. The individual segments in the header and the body are signed separately, so that forwarding a mail via a mail server and changing the mail header does not destroy the signature.
Optional Settings
Further settings are recommended, but not mandatory for operative use:
Greylisting
Greylisting causes the delivery attempt of an unknown mail server to be initially rejected. Usually, spambots do not make any further delivery attempts, so that the delivery of spam was already successfully prevented before the mail had to run through the spam filter engine. A regular mail server, on the other hand, will make another successful delivery attempt after a certain period of time.
The following configurations are possible:
AllowlistAllowlist | |||
| Caption | Default | Description | 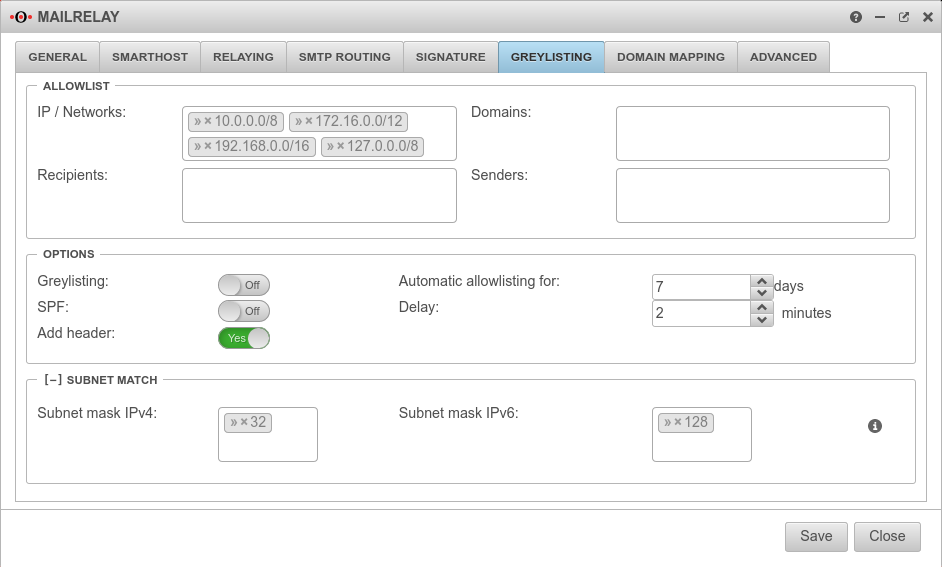 |
|---|---|---|---|
| IP / Networks: | » ✕10.0.0.0/8 » ✕172.16.0.0/12 » ✕192.168.0.0/16 » ✕127.0.0.0/8 | The default are the private IP address ranges and the loopback address. With a click into the clickobx you can add further networks and single hosts (e.g.:» ✕203.0.113.113/32) | |
| Domains: | Here single Mailserver domains can be added e.g.: smtp.anyideas.de The domain of the mail server does not have to be identical with the e-mail domain of the sender. Example: Sender user@ttt-point.de sends via the mail server » ✕smtp.anyideas.de | ||
| Recipient: | Individual recipients can be added here, e.g: » ✕MailUser@ttt-point.de | ||
| Sender: | Individual senders can be added here e.g.:{cb | ||
SettingsSettings | |||
| Greylisting: | Off | On activates the function. Delivery attempts from unknown mail servers are initially rejected. | |
| SPF: | Off | If the Sender Policy Framework of the sender domain is correctly entered in the DNS, the mail will be delivered without delay if On is activated. | |
| Add header: | Yes | By default, an additional greylisting entry is added for each recipient listed in the mail header. This can cause problems in case of many recipients. When disabled No, no greylisting headers are inserted. | |
| Automatic allowlisting for: | 7 Days (Default) | For this period, after a successful delivery mails will be accepted immediately. | |
| Delay: | 2 Minutes (Default) | The period of time that the sending mail server is given to make another delivery attempt. | |
Subnet MatchSubnet Match | |||
| Subnet mask IPv4: | » ✕32 | Instead of the sending server having to have the exact IP address as before, this can be changed so that, for example, only the first 2 or 3 octets have to match. This enables whitelisting even if the sender has several mail servers. Possible values: (Only one value can be entered.) » ✕32 (Single Host) » ✕24 Subnet, with match of first three octets » ✕29 Any value via keyboard input. | |
| Subnet mask IPv6: | » ✕128 | ||
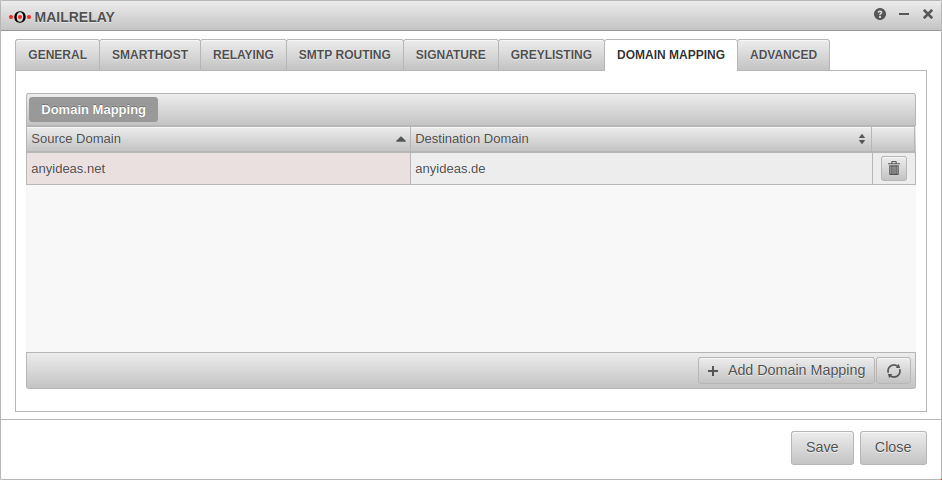
Domain Mapping
Domains can be mapped to receive incoming mails to e.g. user@anyideas.net also under user@anyideas.de.
With the mapping between two domains can be activated.
To do this, a Source-Domain: and a Destination Domain: must be specified.
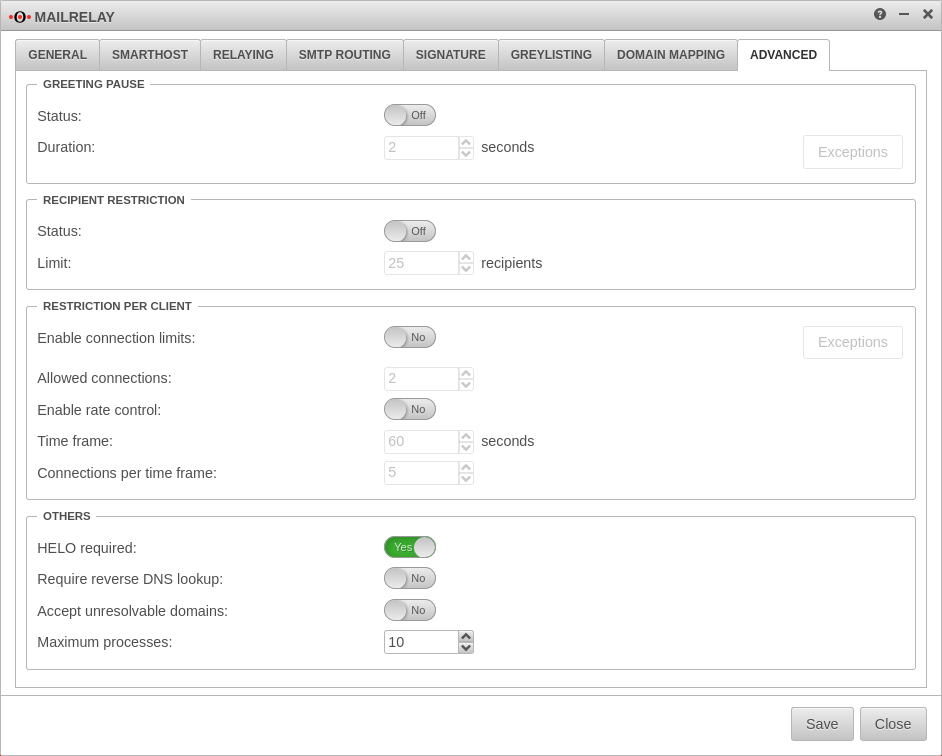
Advanced Settings
Here some further options to avoid spam can be found, each of which can be activated individually:
Configuration of the mailrelay for outgoing mails
To make sure that no spam or malware can be sent from your own network, the mail relay can also be used for outgoing mails.
Set of rules
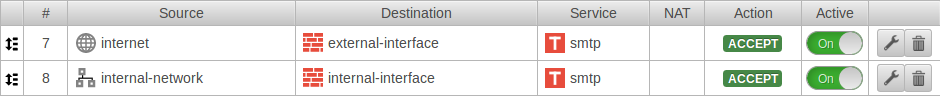
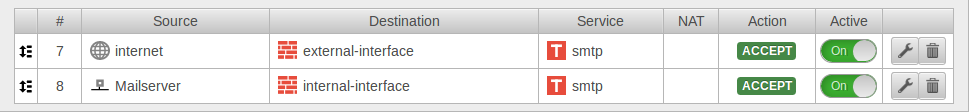
To allow access to the mail relay, the hosts authorized to send mail must be allowed access to the corresponding interface of the Securepoint appliance (depending on the zone in which the hosts are located) via the SMTP protocol. Depending on the requirements, this can be a single host (e.g. the mail server), a group of hosts or the entire network. It is important that all applications that are to send mails via the mail relay have entered the corresponding firewall interface as SMTP server or smarthost.
For example, to allow the internal network access to the mail relay, the set of rules can be created with the predefined network groups:
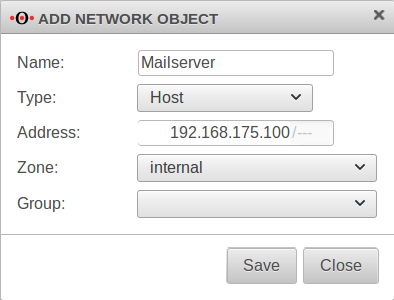
If only the mail server is to be able to send mails, it must first be created as a network object:
This object can then be used in the firewall rule:
If a certain group of computers in the internal network is to be allowed to use the mail relay, these computers must be created as network objects. These can then be combined in a group (e.g. "SMTP Authorized").
Configuration Relaying
In order for the mailrelay to accept mails from the internal network or from the mail server, the settings in the Relaying} tab must be supplemented by a corresponding entry. The network address of the corresponding subnet or the IP address of the relevant computer serves as criterion:
| Domain: | 192.0.2.0/30 or 192.0.2.192 notempty These are sample IPs for the internal mail servers. These have to be replaced by individual addresses!
|
| Option: | |
| Action: |
Conclusion
The UTM can now check incoming and outgoing mails for spam and viruses.