notempty
Creating and Configuring Users and Groups (Authorizations)
Last adaptation to the version: 11.8.8 (04.2020)
- New:
- Description: root user
- in 11.8.8 Default address for spam report from AD
- Expiration date for user accounts
- Preconfigured Support user can be created as required
Previous versions: 11.7 | 11.8.5
Preamble
Call user configuration in the navigation bar under
The users entered here are stored in a local database on the appliance.
The authentication configured at this point is also performed against the local database.
In addition, local user groups can be assigned to an AD/LDAP group.
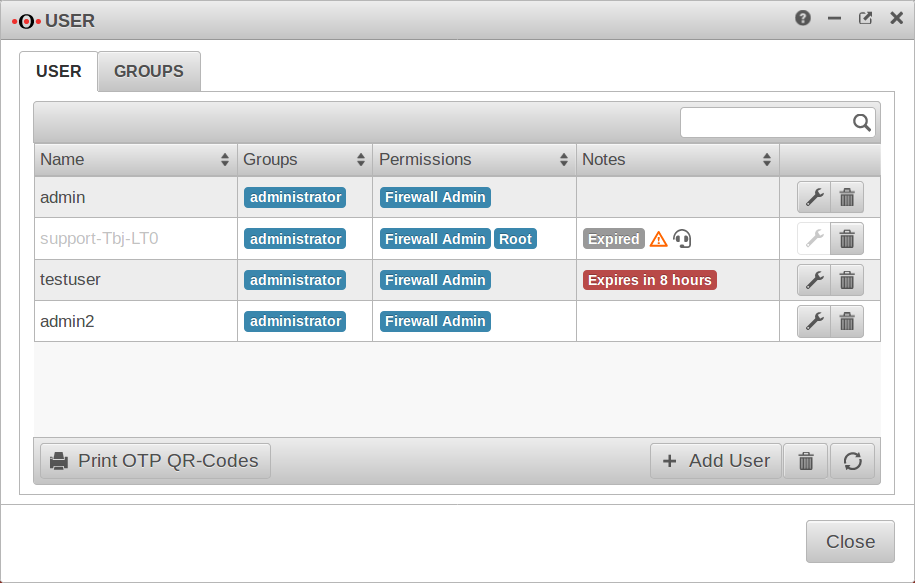
Users
| Caption | Value | Description |
|---|---|---|
| Name | admin |
Login name of the user |
| Groups | administrator | Group membership of the respective user |
| Permissions | Firewall Administrator | Authorizations, configuration under Groups] |
| Notes New from 11.8.5 |
Expires in 8 hours | After expiration the user can no longer log in. |
| Edit or delete the user |
Support user
New function as of 11.8.5
The support user is a temporary administrator who can be activated, for example, to be supported by Securepoint support.
The button for creating a support user is located in the upper right corner of the dashboard. (Headset icon)
Multiple support users cannot be created at the same time. If a support user already exists, you will be asked whether the existing user should be deleted!
| Caption | Value | Description | |
|---|---|---|---|
| Loginname: | support-N3e-oDt | An arbitrary name that begins with support- and can only be changed by . Manual input is not possible. | Datei:UTM v.11.8.6 Authentifizierung Benutzer Supportbenutzer-en.png |
| Password: | red-SZZ-sIa-dCB | An arbitrary name that begins with support- and can only be changed by . Manual input is not possible.
| |
| Expiration date: | 2019-08-20 11:11:11 | By default, the access for the support user expires after 24 hours. It is possible to extend this value up to 30 days. For support users, it is not possible to change this value afterwards. | |
| Groups: | ×administrator | By default, the first user group with the authorization Firewall Administrator is entered. You can select other groups that also have this permission. | |
| Root permission: | No | With Yes Activation gives the user additional root privileges. When connecting with SSH, the login is done directly on the root console! | |
Administration Enable access for the Securepoint support: Yes |
To enable access to the admin interface via the external interface, the entry support.de.securepoint.de is added under Administration. If the entry already exists, the button is active but cannot be disabled. | ||
Before saving, the login name must and the password should be noted !
The password can no longer be displayed after saving.
Both values can be copied from the clipboard.
Expired user accounts are automatically removed after a certain period of time.
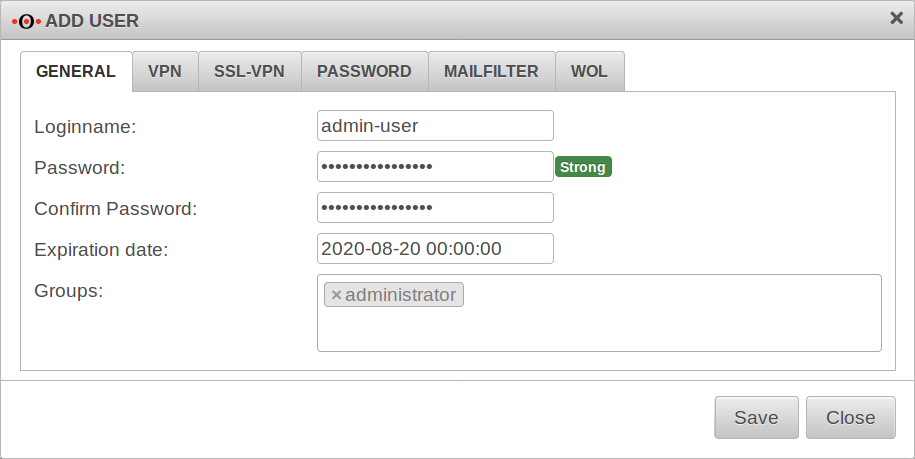
Add user
The dialog Add user opens. This dialog contains several tabs. There is no need to make entries in all tabs. With the entries are accepted.
User General
| Caption | Value | Description |
|---|---|---|
| Login name | admin-user | Login name of the user |
| root | root userA user with the name root must also be a member of a group with administrator privileges.This user will then automatically get root permission. After logging on to the appliance via ssh, this user does not end up on the CLI but immediately in the Linux console. This user has extensive diagnostic tools available there, e.g. tcpdump The root user reaches the Command Line Interface (CLI) with the command spcli and leaves it with exit. The root user should definitely be given a short-term expiration date or be removed immediately after the diagnostic work! | |
Password Confirm Password |
•••••••• | Strong New since 11.8
Passwords must meet the following criteria:
|
| Expiry date New since 11.8.5 |
2020-08-21 00:00:00 | After expiration the user can no longer log in. However, the expiration date can be extended again. (It cannot be set in the past in the web interface!) The expiration date can also be changed via CLI: user attribute set name testnutzer attribute expirydate value 1576553166 The value is given as Unixtime (time in seconds since 1.1.1970 00:00). |
| Groups | ×administrator | Group membership and therefore authorizations of this user |
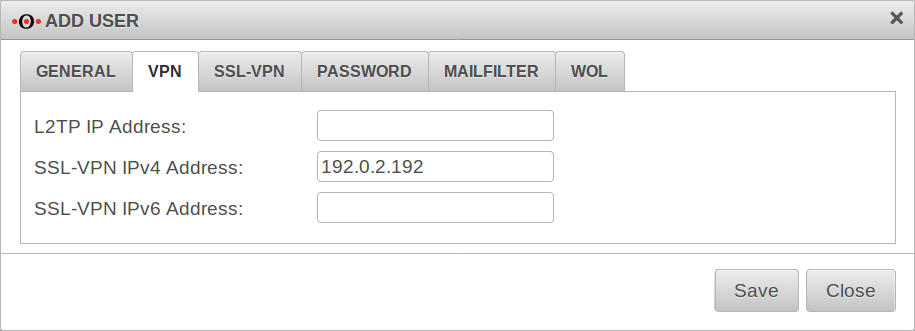
VPN
Here fixed IP tunnel addresses can be assigned to the users.
L2TP IP Address:
SSL-VPN IPv4 Address:
SSL-VPN IPv6 Address:
PPTP is no longer available because it has been proven to be an insecure protocol.
SSL-VPN
| Caption | Value | Description | UTMuser@firewall.name.fqdnAuthenticationUser 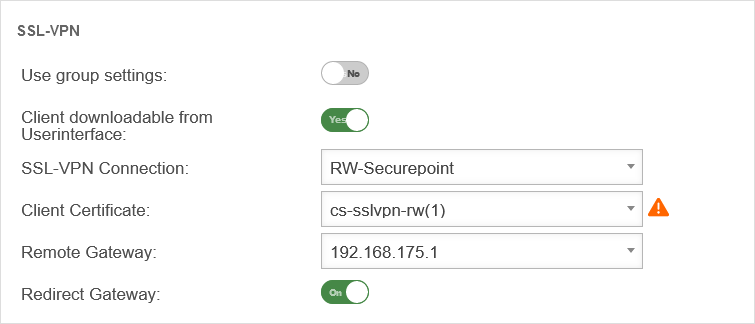 SSL-VPN settings for users SSL-VPN settings for users
|
|---|---|---|---|
| Use group settings: | No | If the user is a member of a group, the settings can be adopted from there. The following settings are then greyed out here and are to be configured in the Area Groups menu. | |
| Client downloadable in the user interface: | Yes | The Securepoint VPN Windows client can be downloaded from the user web interface (accessible via port 1443 by default). The port is configurable in the Tab Server settings Button / User Webinterface Port: : 1443. | |
| SSL VPN connection: | RW-Securepoint | Selection of a connection created in the menu. | |
| Client certificate: | cs-sslvpn-rw(1) | A certificate must be specified that the client uses to authenticate itself to the UTM. It is also possible to use ACME certificates. | |
| Remote Gateway: | 192.168.0.162 (Example-IP) | External IP address or DNS resolvable address of the gateway to which the connection is to be established. | |
| Redirect Gateway: | On | When enabled, all client network traffic is sent through the selected gateway. | |
Password:
The Password tab defines the strength of the password and whether the password can be changed by the user.
| Beschriftung | Default | Description |
|---|---|---|
| Password change allowed: | Off | Determines whether the user can change his or her password in the user interface. |
| Minimum password length: | 8 | The minimum password length can be set to more than 8 characters. |
Passwords must meet the following criteria:
| ||
Mailfilter
| Beschriftung | Default | Description |
|---|---|---|
| Use group settings: | No | If the user is a member of a group, the settings can be applied from there. The following settings are then hidden here and can be configured in the menu / Groups. |
| email address | ||
| user@ttt-point.de | E-mail accounts that can be viewed by this user to control the mail filter. Delete with | |
| email address | Adding an email address to the list | |
| Herunterladen von folgenden Anhängen erlauben: | (Default) | In the user interface, the user can download/u> attachments of mails that meet certain criteria. |
| This function may allow the downloading of viruses and should therefore only be allowed for experienced users! | ||
| This function may allow the downloading of viruses and should therefore only be allowed for experienced users! | ||
| Weiterleiten von folgenden E-Mails erlauben: | (Default) | In the user interface, the user can forward/u> attachments of mails that meet certain criteria. |
| This function may allow the forwarding of viruses and should therefore only be allowed for experienced users! | ||
| This function may allow the forwarding of viruses and should therefore only be allowed for experienced users! | ||
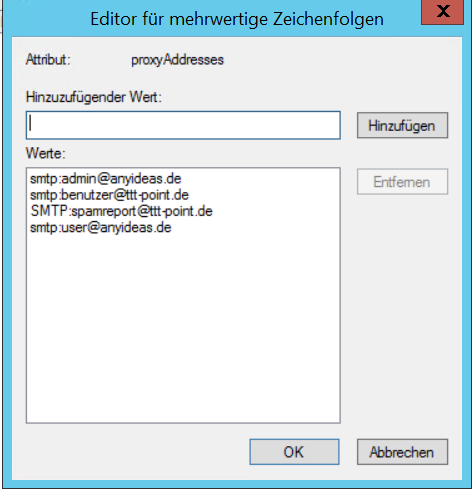
| Bericht E-Mail-Adresse: | E-Mail-Adresse, an die ein Spam-Report versendet wird. Wenn hier kein Eintrag erfolgt, wird der Spam-Report an die erste E-Mail-Adresse der Liste gesendet. New in 11.8.8 If several mail addresses for a user are stored in an AD, the entry configured there as Primary SMTP address is used as the default address.
| |
| Report language: | Default under → Firewall → language of reportsIt can be specifically selected: or |
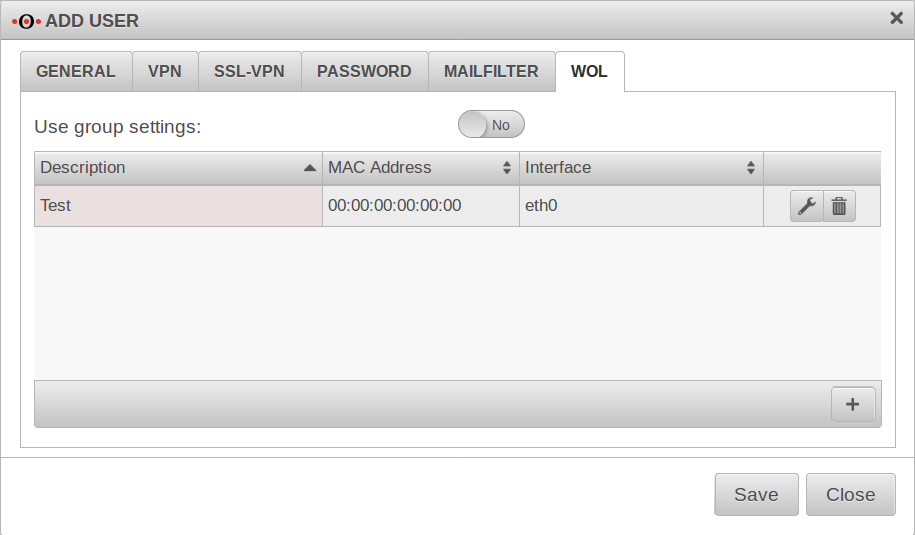
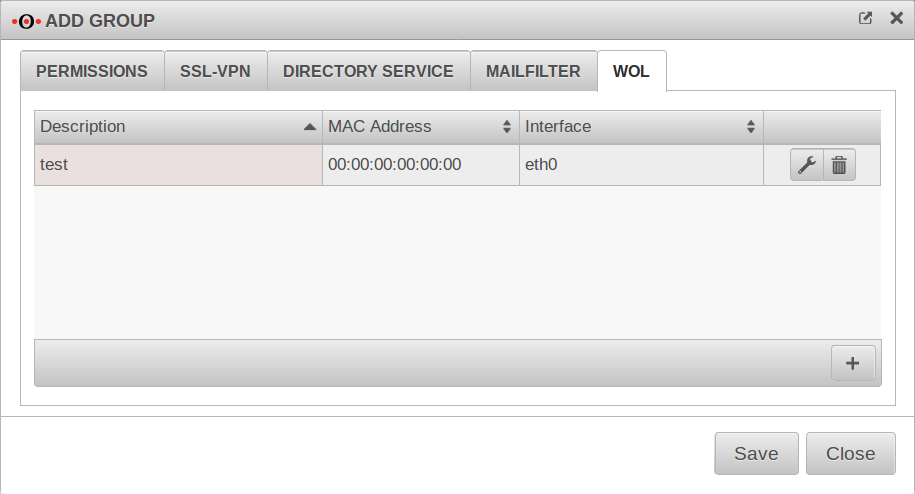
WOL
WOL stands for Wake on LAN and switches on a computer via the network card. In order to start the computer via data packet, the computer must also support this. This is usually configured in the BIOS or UEFI.
For a user to be able to use WOL, it must be configured here!
| Beschriftung | Default | Description |
|---|---|---|
| Description: | Free text | |
| MAC address: | __:__:__:__:__: | MAC address of the computer to be activated via Wake on Lan. |
| Interface: | Interface of the appliance via which the WOL packet must be sent. |
Calls the entry for editing.
Deletes the item
Groups
Some settings described in the Users section can also be set for the entire group. However, the settings for the individual user replace the group settings.
Permissions
| Beschriftung | Description |
|---|---|
| Group Name: | Freely definable name |
| Permissions | |
| Firewall Admin | Members of this group can call the admin interface (by default accessible on port 11115. There must always be at least one firewall administrator. |
| Spamreport | Members of this group can receive a spam report |
| VPN-L2TP | Members of this group can establish a VPN-L2TP connection. |
| Mailrelay User | Members of this group can use the Mailrelay |
| HTTP Proxy | Members of this group can use the HTTP proxy. |
| IPSEC XAUTH | Members of this group can authenticate themselves with IPSEC. |
| Userinterface | Members of this group have access to the user interface |
| Clientless VPN | Members of this group can use Clientless VPN |
| Mailfilter Administrator | Members of this group have access to all emails cached in the UTM's mail archive with the User Web Interface right - regardless of whether they are legitimate recipients or senders of these emails. |
| SSL-VPN | Members of this group can establish an SSL VPN connection. |
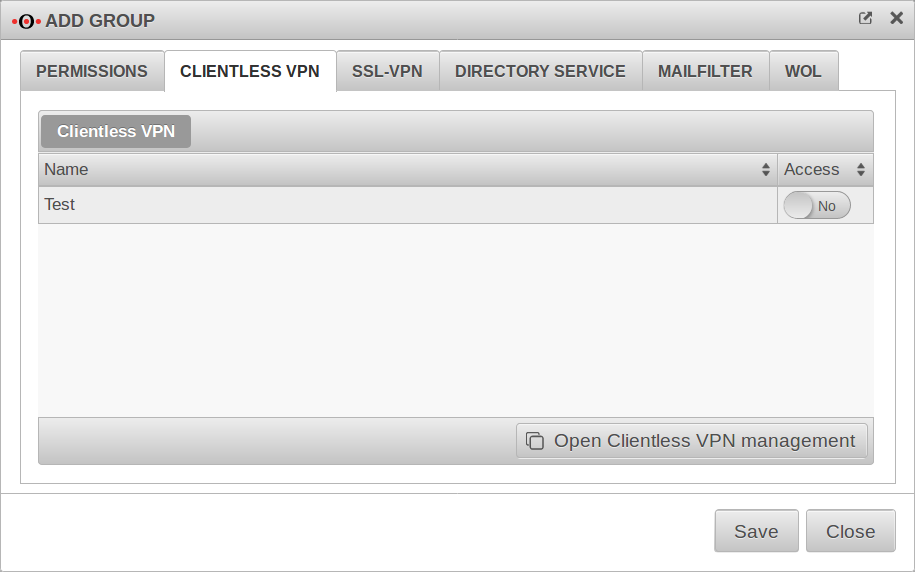
Clientless VPN
This tab is only displayed if Permissions Clientless VPN has been activated Ein in the Permissions tab.
Connections created under are displayed here.
| Clientless VPN | ||
|---|---|---|
| Name | Name of the connection | |
| Access | No | If Yes is activated, members of this group can use this connection. |
Here you can configure and add connections.
Call alternatively via
Further information in the article to Clientless VPN.
SSL-VPN
notempty
This is where to configure settings for the SSL VPN for an entire group.
All users share the same certificate when using the group settings!
SSL VPN settings of individual users override the group settings.
| Caption: | Value | Description: | 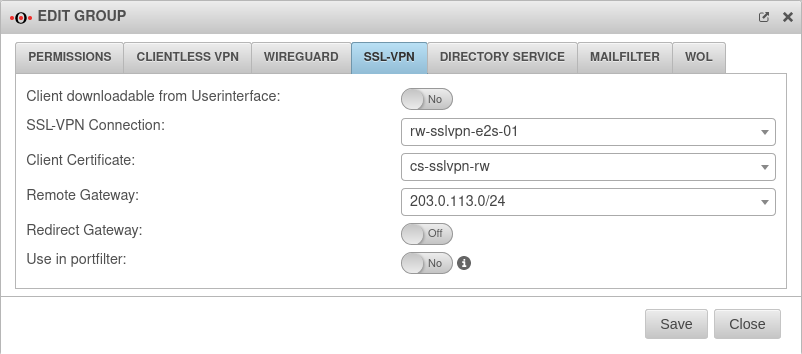 |
|---|---|---|---|
| Client downloadable in the user interface: | No | If enabled, the VPN client can be downloaded in the user interface | |
| SSL VPN connection: | rw-sslvpn-e2s-01 | Select the preferred connection (created under ) | |
| Client certificate: | cs-sslvpn-rw | Select the certificate for this group (created under Tab Certificates) It is also possible to use ACME certificates. | |
| Remote Gateway: | 203.0.113.0/24 | IP address of the gateway on which the SSL VPN clients dial in. Free input or selection via drop-down menu. | |
| Redirect Gateway: | Off | Requests to destinations outside the local network (and thus also the VPN) are usually routed directly to the Internet by the VPN user's gateway. When the On button is activated, the local gateway is redirected to the UTM. This way, these packets also benefit from the protection of the UTM. This setting changes the configuration file for the VPN client. | |
| Use in portfilter: | No | By enabling Yes this option, rules for this group can be created in the portfilter. This can be used to control access for users who are members of this group connected via SSL VPN. | |
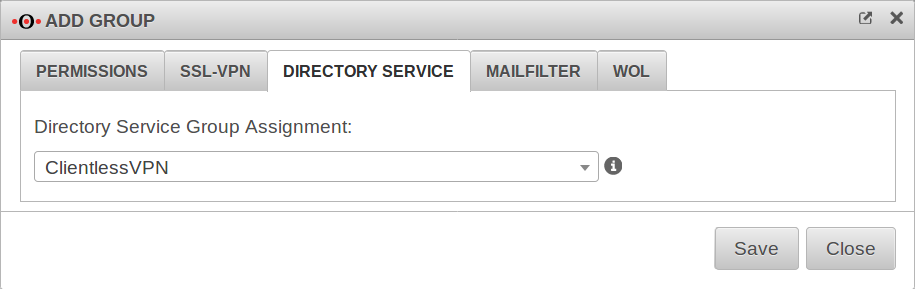
Directory Service
Here you can specify which directory service group the members of this user group should belong to.
In order for a group to be selected here, a corresponding connection must be configured under .
Selection of an AD/LDAP group
Mailfilter
The authorization Userinterface Ein} is required.
| Email address | ||
| Caption | Default | Description |
|---|---|---|
| support@ttt-point.de | Email accounts that can be viewed by members of this group to control the mail filter. Delete with | |
| Email address | Adding a mail address to the list | |
| Allow downloads of following attachments: | (Default) | Members of this group can download attachments from mails in the user interface that meet certain criteria. |
| Allow forwarding of following emails: | (Default) | Members of this group can forward emails in the user interface that meet certain criteria |
| Report email address: | Email address to which a spam report is sent. If no entry is made here, the spam report is sent to the first email address in the list. If several mail addresses for a user are stored in an AD, the entry configured there as Primary SMTP address is used as the default address..
| |
| Report language: | Default under → Firewall → language of reportsIt can be specifically selected: or |
WOL
WOL stands for Wake on LAN and switches on a computer via the network card. In order to start the computer via data packet, the computer must also support this. Usually this is configured in the BIOS or UEFI.
Members of this group may switch on hosts entered here by WOL.
| Beschriftung | Default | Description |
|---|---|---|
| Description | Free text | |
| MAC address: | __:__:__:__:__: | MAC address of the computer to be activated via Wake on Lan. |
| Interface: | Interface of the appliance via which the WOL packet must be sent. |
Calls the entry for editing.
Deletes the item