notempty
Settings in the UTM firewall for VoIP devices if the VoIP server is behind the UTM
If there is a UTM between VoIP end devices and a VoIP server, it is necessary to create an additional port filter rule that enables VoIP with NAT.
The connection is established via SIP, the device logs on to the VoIP server with its local IP. The voice packets themselves are then sent via rtp on other ports. In order to make the VoIP client and the rtp ports in the local network available from outside - in this case accessible for the VoIP server - it is necessary to create a port filter rule for this:
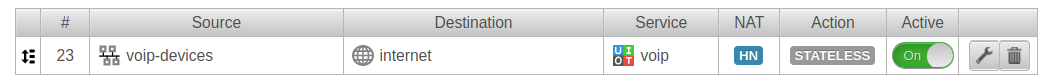
Tab Portfilter Button
Action |
||
Source |
voip-devices | An appropriate group should be defined. For example: Phones and workstations or VoIP-devices Internal Network allows all network devices VoIP ! For reasons of network security, devices that do not require VoIP (e.g. printers or IoT devices) should not be allowed VoIP either. |
Destination |
Internet | |
Service |
voip | VoIP service group: Enables the following ports:
|
NAT |
Type |
|
Networkobject |
Additionally, it may be necessary to execute the following commands in the CLI:
debug kmod load module nf_nat_sip debug kmod load module nf_nat_h323 debug kmod load module nf_conntrack_sip debug kmod load module nf_conntrack_h323
Then as root-user via ssh execute the command
conntrack -F
run several times