notempty
Configuration of an End-to-Site-connection with IPSec for roadwarrior
Changelog
Last adaptation to the version: 11.8
- New:
- Design adaptation
- Translation
Previous versions: 11.6.12
Introduction
A roadwarrior connection connects individual hosts to the local network. This allows, for example, a field service employee to connect to the network of the headquarters.
This step-by-step guide shows how to configure an end-to-site connection. The selected connection type is native IPSec with IKEv1.
For native IPSec connections with IKEv1 the client needs a separate program.
Configuration of a native IPSec connection
After logging into the administration interface of the firewall (factory default: https://192.168.175.1:11115) an IPSec connection can be added in the menu Button .
Wizard
| Caption | Value | Description | |
|---|---|---|---|
Step 1 Connection Type | |||
| Selection of the connection type | The following connections are available:
|
For the configuration of an E2S / End-to-Site-connection roadwarrior is to be selected. | 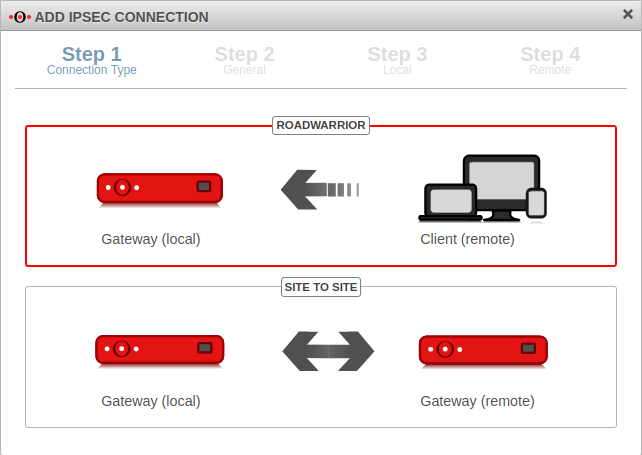 |
Step 2 General | |||
| Name: | IPSec Roadwarrior | Name for the connection | 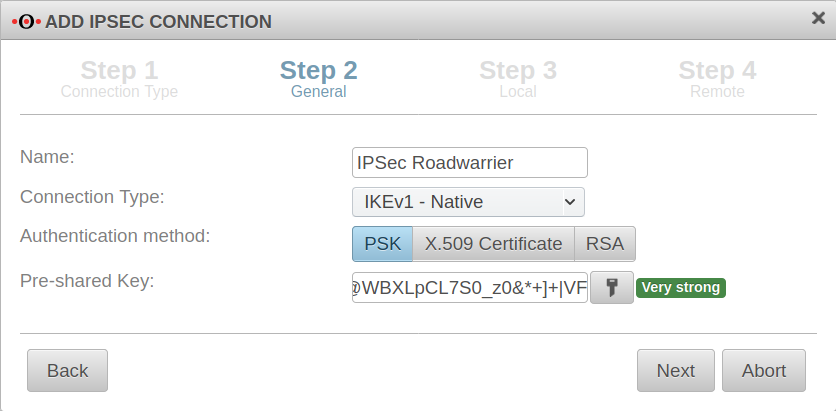 |
| Connection Type: |
Please note which type is supported by the operating system | ||
| Authentication method: | Alternatively:
| ||
| Pre-Shared Key: | 12345 | Any PSK. With the button a very strong key is generated. | |
| X.509 Certificate: | Selection of a certificate | ||
Step 3 Local | |||
| Local Gateway ID: | eth0 | The gateway ID is included in the authentication. This can be an IP address, a host name or an interface. | 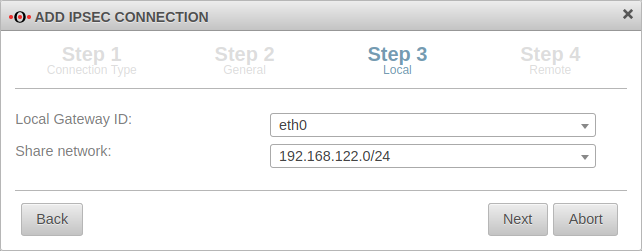 |
| Share networks: | 192.168.122.0/24 | The local network to be connected via the VPN connection | |
Step 4 Remote | |||
| Remote Gateway ID: | 192.0.2.192 or My_Roadwarrior |
If more than one IPSec connection is established, a unique ID should be entered here. The password of incoming connections is validated against the ID of the IPSec connection. If no IP address is specified as ID, further settings must be made for site-to-site connections. |
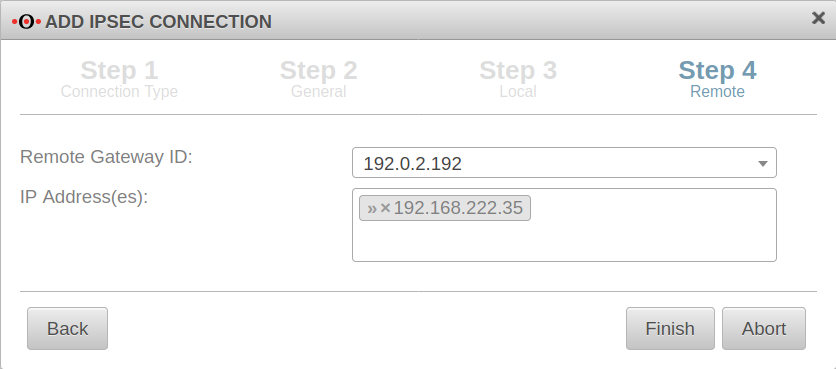 |
| IP Address(es): | 192.168.222.35 | Additional IP address for the roadwarrior with which the IPSec connection is established.
For this example, after the wizard has finished, the ip-address just dedicated is edited and for the Remote network the value 192.168.22.0/24 is entered. | |
| Exit the setup wizard with | |||
Set of rulesTo grant access to the internal network, the connection must be allowed. | |||
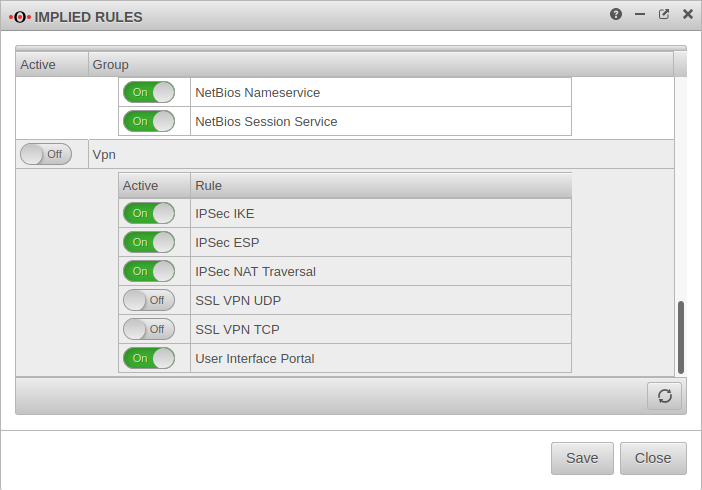
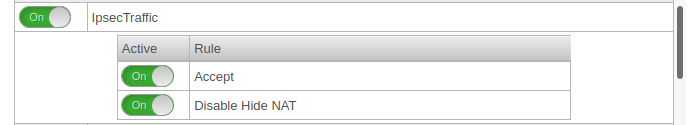
Implied rulesIt is possible, but not recommended to do this with implied rules in section VPN and section IPSec Traffic. However, these implied rules enable the ports used for IPSec connections on all interfaces. |
|||
Creating a network objectTab Network objects Button | |||
| Name: | ngrp-IPSec-Roadwarrior | Name for the IPSec network object | 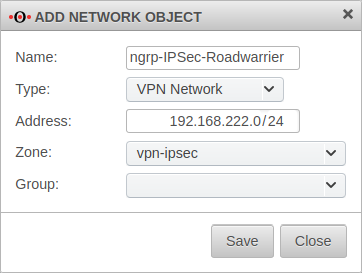 |
| Type: | VPN network | type to be selected | |
| Address: | 192.168.222.0/24 | roadwarrior IP address or the roadwarrior pool entered in the Installation Wizard in step 4 (or subsequently adjusted in phase 2). In this example the network 192.168.222.0/24. | |
| Zone: | vpn-ipsec | zone to be selected | |
| Group: | Optional: Group | ||
Port filter rules |
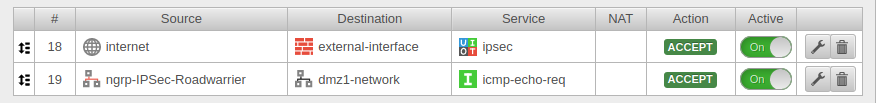 | ||
| The first rule allows the IPSec tunnel to be built at all. | |||
Source |
Source from which access to the internal network is to be made. | ||
Destination |
Interface on which the connection is received. | ||
Service |
Predefined service group for IPSec Service / Protocol, Port
isakmp / udp 500
nat-traversal / udp 4500
Protocol esp | ||
A second rule allows the roadwarrior to access the desired network, host or network group. | |||
Source |
Roadwarrior host or network | ||
Destination |
Network to be accessed. | ||
Service |
Desired service or service group | ||
Now a connection with a roadwarrior can be established.
A client may have to be used for this. Care must be taken to ensure that the parameters on both sides are identical in all phases of the connection.
When using an NCP client, for example, the parameters
- Diffie-Hellman Group: (UTM) or IKE-DH Group (NCP) and
- DH group (PFS) (UTM) or IKE DH group (NCP)
either in the UTM or in the NCP client.
When using IKEv1, the
- Exchange mode
can be set to the secure Main Mode (IKEv1) in the NCP client.
| Caption | Default values UTM | Default values NCP client |
|---|---|---|
Phase 1 | ||
| Encryption: | AES 128 Bit | |
| Authentication: | Hash: SHA2 256 Bit | |
| Diffie-Hellman Group: | IKE DH-Grupe: DH2 (modp1024) | |
| Strict: | Off | |
| IKE Lifetime: | ||
| Rekeying: | ||
Phase 2 | ||
| Encryption: | AES 128 Bit | |
| Authentication: | SHA2 256 Bit | |
| DH-Gruppe (PFS): | keine | |
| Key lifetime: | 8 hours | |
| Restart on abort: | Off | |
| Exchange mode | Main Mode (not configurable) | Agressive Mode (IKEv1) |