notempty
- DPD Timeout and DPD Interval can be configured
Introduction
This step-by-step guide shows how to configure an end-to-site connection. The selected connection type is native IPSec with IKEv1.
For native IPSec connections with IKEv1 the client needs a separate program.
Configuration of a native IPSec connection
Wizard
Connection Type Step 1 - Connection Type
| |||
| Caption | Value | Description | 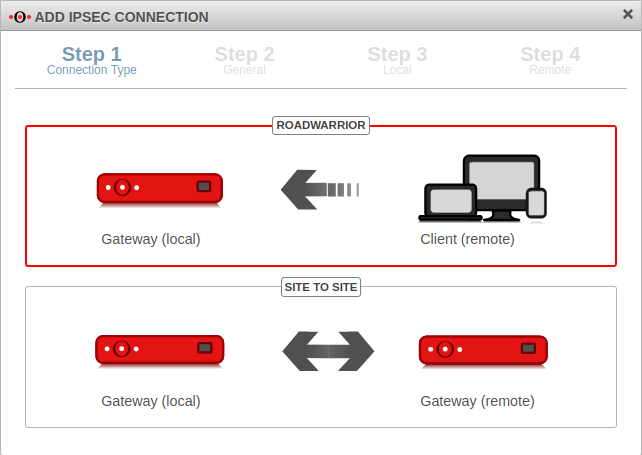 |
|---|---|---|---|
| Selection of the connection type | The following connections are available:
|
For the configuration of an E2S / End-to-Site-connection roadwarrior is to be selected. | |
General Step 2 - General
| |||
| Name: | IPSec Roadwarrior | Name for the connection | 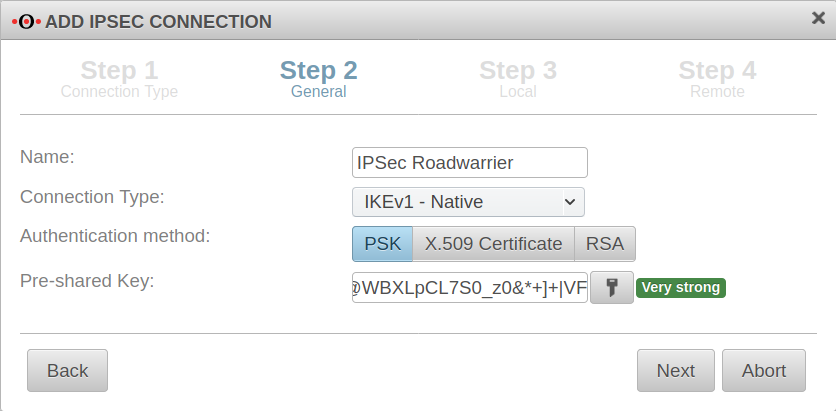 |
| Connection Type: |
Please note which type is supported by the operating system | ||
| Authentication method: | Alternatively:
| ||
| Pre-Shared Key: | 12345 | Any PSK. With the button a very strong key is generated. | |
| X.509 Certificate: | Selection of a certificate | ||
Local Step 3 - Local
| |||
| Local Gateway ID: | eth0 | The gateway ID is included in the authentication. This can be an IP address, a host name or an interface. | 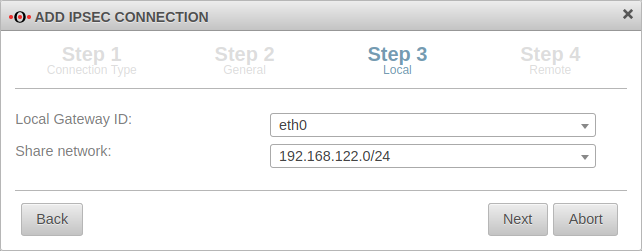 |
| Share networks: | 192.168.122.0/24 | The local network to be connected via the VPN connection | |
Remote Step 4 - Remote
| |||
| Remote Gateway ID: | 192.0.2.192 or My_Roadwarrior |
If more than one IPSec connection is established, a unique ID should be entered here. The password of incoming connections is validated against the ID of the IPSec connection. If no IP address is specified as ID, further settings must be made for site-to-site connections. |
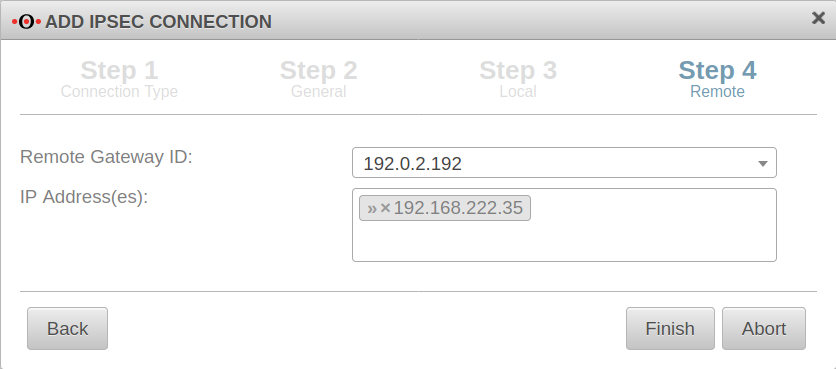 |
| IP Address(es): | 192.168.222.35 | Additional IP address for the roadwarrior with which the IPSec connection is established.
For this example, after the wizard has finished, the ip-address just dedicated is edited and for the Remote network the value 192.168.222.0/24 is entered. | |
| Exit the setup wizard with | |||
Set of rulesTo grant access to the internal network, the connection must be allowed. | |||
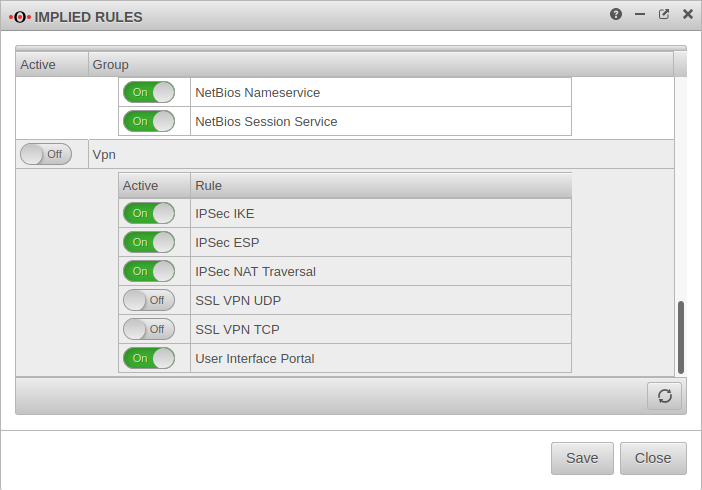
Implied rulesIt is possible, but not recommended to do this with implied rules in section VPN and section IPSec Traffic. However, these implied rules enable the ports used for IPSec connections on all interfaces. |
|||
Creating a network objectTab Network objects Button | |||
| Name: | ngrp-IPSec-Roadwarrior | Name for the IPSec network object | 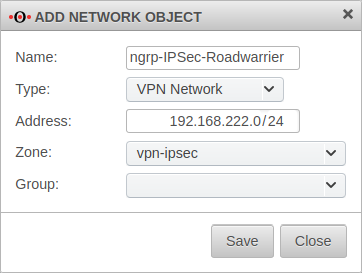 |
| Type: | VPN network | type to be selected | |
| Address: | 192.168.222.0/24 | roadwarrior IP address or the roadwarrior pool entered in the Installation Wizard in step 4 (or subsequently adjusted in phase 2). In this example the network 192.168.222.0/24. | |
| Zone: | vpn-ipsec | zone to be selected | |
| Group: | Optional: Group | ||
Port filter rules |
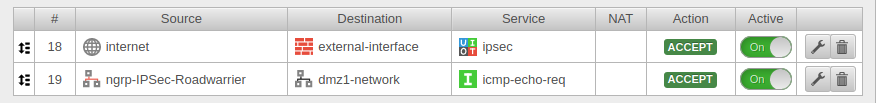 | ||
| Add portfilter rule at Tab Portfilter Button The first rule allows the IPSec tunnel to be built at all. | |||
| Source | Source from which access to the internal network is to be made. | ||
| Destination | Interface on which the connection is received. | ||
| Service | Predefined service group for IPSec Service / Protocol, Port
isakmp / udp 500
nat-traversal / udp 4500
Protocol esp | ||
A second rule allows the roadwarrior to access the desired network, host or network group. | |||
| Source | Roadwarrior host or network | ||
| Destination | Network to be accessed. | ||
| Service | Desired service or service group | ||
Now a connection with a roadwarrior can be established.
A client may have to be used for this. Care must be taken to ensure that the parameters on both sides are identical in all phases of the connection.
Necessary changes, when using an NCP client:
- UTM
- Diffie-Hellman Group (Phase 1)
- DH-Group (PFS) (Phase 2)
oder
- NCP-Client:
- IKE-DH-Group
- NCP-Client:
- Exchange mode: Main Mode (IKEv1)
Weitere Einstellungen
notempty
Phase 1 | |||
Tab Connections Button GeneralTab General | |||
| Caption | Value | Description | 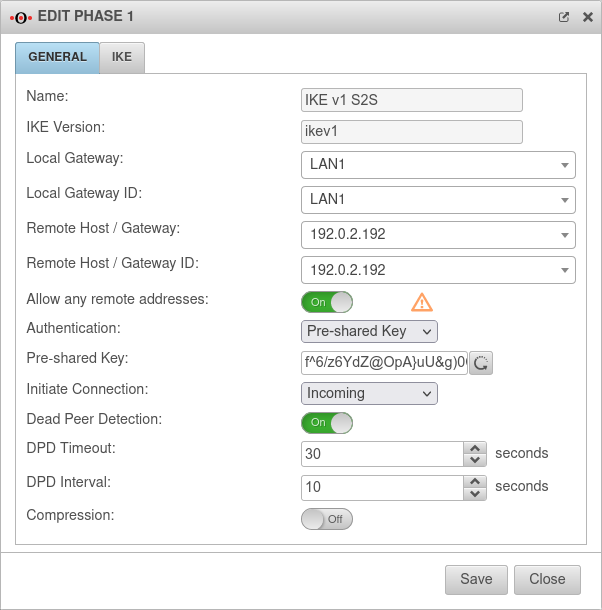 |
|---|---|---|---|
| Allow any remote addresses: | On Default |
Disable this option for site-to-site connections with DynDNS hosts if multiple IPsec connections with a priori unknown addresses (DynDNS S2S, Roadwarrior) are configured. | |
| Initiate Connection: | The tunnel is initiated by the UTM even if no packets are sent. Incoming requests are accepted. | ||
| The UTM accepts incoming tunnel requests. No outgoing connection is created. | |||
| The tunnel is initiated by the UTM only when packets are to be sent. | |||
| Deactivates the tunnel | |||
| Dead Peer Detection: | On | Checks at a set interval whether the tunnel still exists. If the tunnel was terminated unexpectedly, the SAs are dismantled. (Only then it is also possible to reestablish a new tunnel). | |
| DPD Timeout: Only with IKEv1 New as of 12.2.3 |
30 seconds | Period before the state under Startup behavior is restored. The same values are used here as for regular packets. | |
| DPD Interval: New as of 12.2.3 |
10 seconds | Testing interval | |
| Compression: | Off | Compression is not supported by all remote stations | |
Tab IKE Settings that must be identical in the UTM and in the client: IKE | |||
| Caption | Default values UTM | Default values NCP client | 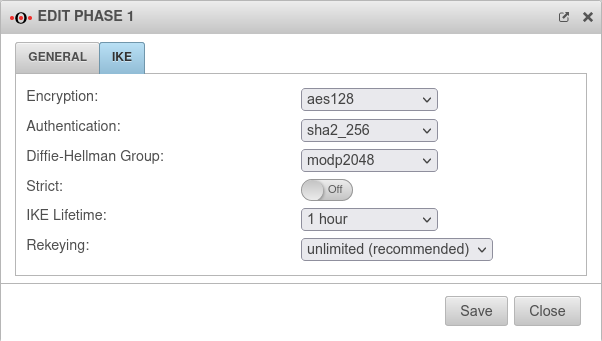 |
| Encryption: | AES 128 Bit | ||
| Authentication: | Hash: SHA2 256 Bit | ||
| Diffie-Hellman Group: | IKE DH-Grupe: DH2 (modp1024) | ||
| Tab IKE More settings: | |||
| Caption | Value | Description | |
| Strict: | Off | The configured parameters (authentication and encryption algorithms) are preferred for connections | |
| On | No further proposals are accepted. A connection is only possible with the configured parameters. | ||
| IKE Life time: | Validity period of the Security Association: Agreement between two communicating entities in computer networks. It describes how the two parties apply security services to communicate securely with each other. When using multiple services, multiple security connections must also be established. (Source: Wikipedia 2022) in phase 1 | ||
| Rekeying: | Number of attempts to establish the connection (initial or after abort). For E2S connections (Roadwarrior), the setting 3 times can avoid endless attempts to connect to devices that are not correctly logged out. | ||
Phase 2 | |||
Tab Connections Button GeneralTab General : Settings that must be identical in the UTM and in the client: | |||
| Caption | Default values UTM | Default values NCP client | 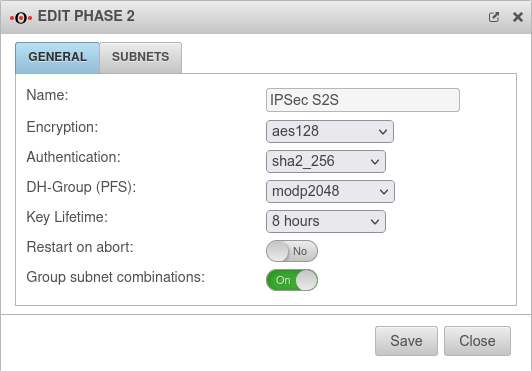 |
| Encryption: | AES 128 Bit | ||
| Authentication: | SHA2 256 Bit | ||
| DH-Gruppe (PFS): | keine | ||
| Key lifetime: | Validity period of the key in phase 2 | ||
| Exchange mode | Main Mode (not configurable) | Aggressive Mode (IKEv1) The UTM does not support Aggressive Mode for security reasons. | |
Tab General: More settings | |||
| Caption | Value | Description | |
| Restart after abort: | No | If the connection was terminated unexpectedly, activating will restore the state configured under Startup behavior in phase 1. | |
| Group subnet combinations: Only with IKEv2 |
Yes |
If more than one network is configured on the local side or at the remote gateway, a separate SA is negotiated for each subnet combination when it is deactivated. This results in numerous subnet combinations and thus many SAs, especially with multiple subnets, and leads to limitations and losses in the stability of the connections due to the design of the IPSec protocol. | |
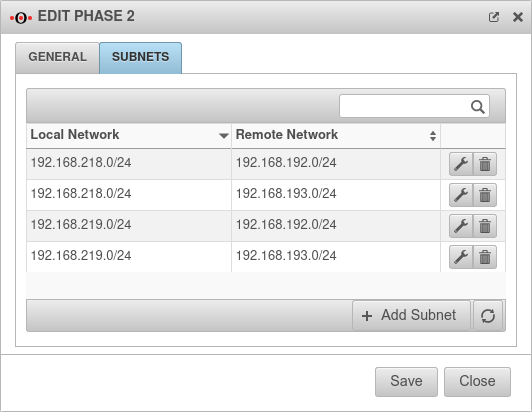
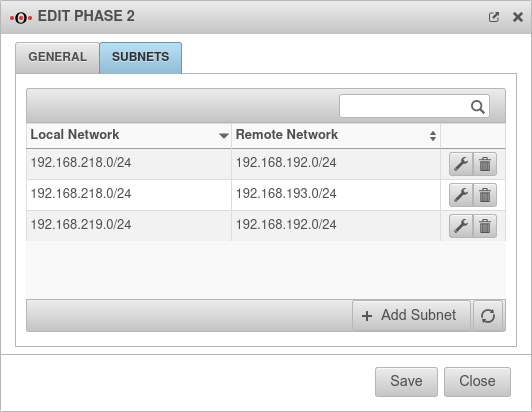
SubnetsTab Subnets Only with IKEv2 | |||
| Scenario: All subnets have access to each other
With an SSH login as root, the behavior can be understood particularly well.
|
 | ||
| Scenario: Not all subnets may access every network of the remote gateway
If in phase two a local network is not connected to all remote networks (or a remote network is not connected to all local ones), this will not be taken into account if the option Group subnet combinations is active! The Group subnet combinations option will connect all local networks to all remote networks!
Port filter rules make it possible to control access.
With an SSH login as root, the behavior can be understood particularly well.
|
 | ||
TroubleshootingDetailed Troubleshooting instructions can be found in the Troubleshooting Guide If an email address should be used as gateway ID, it is necessary to insert a double @@ in front of the ID (mail@... becomes @@mail@...). Otherwise the ID will be treated as FQDN
| |||