- Layout adjustment and port note for the mDNS-Repeater
- Updated to Redesign of the webinterface
Introduction
The nameserver of the UTM offers:
- Forward zones: Name resolution (FQDN) in IP addresses
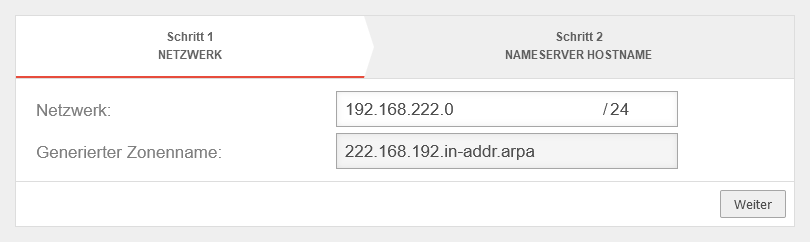
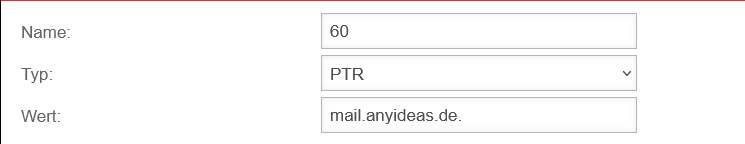
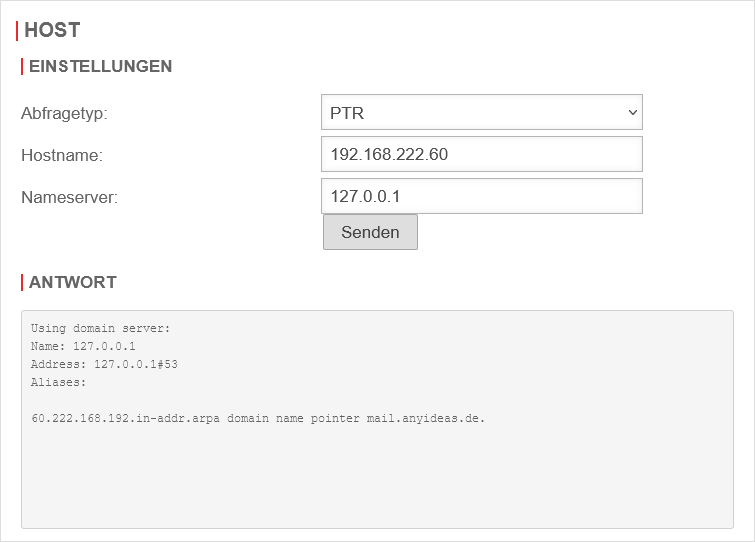
- Reverse zones: IP addresses into FQDN)
- Relay zones: Forwarding of queries belonging to a specific domain
- DNS Forwarding: Forwarding of all DNS queries
Als Dienst muss mindestens
Es empfiehlt sich in der Regel jedoch die Dienstgruppe
Prerequisites
Set Firewall as Namesever
UTMuser@firewall.name.fqdnNetwork 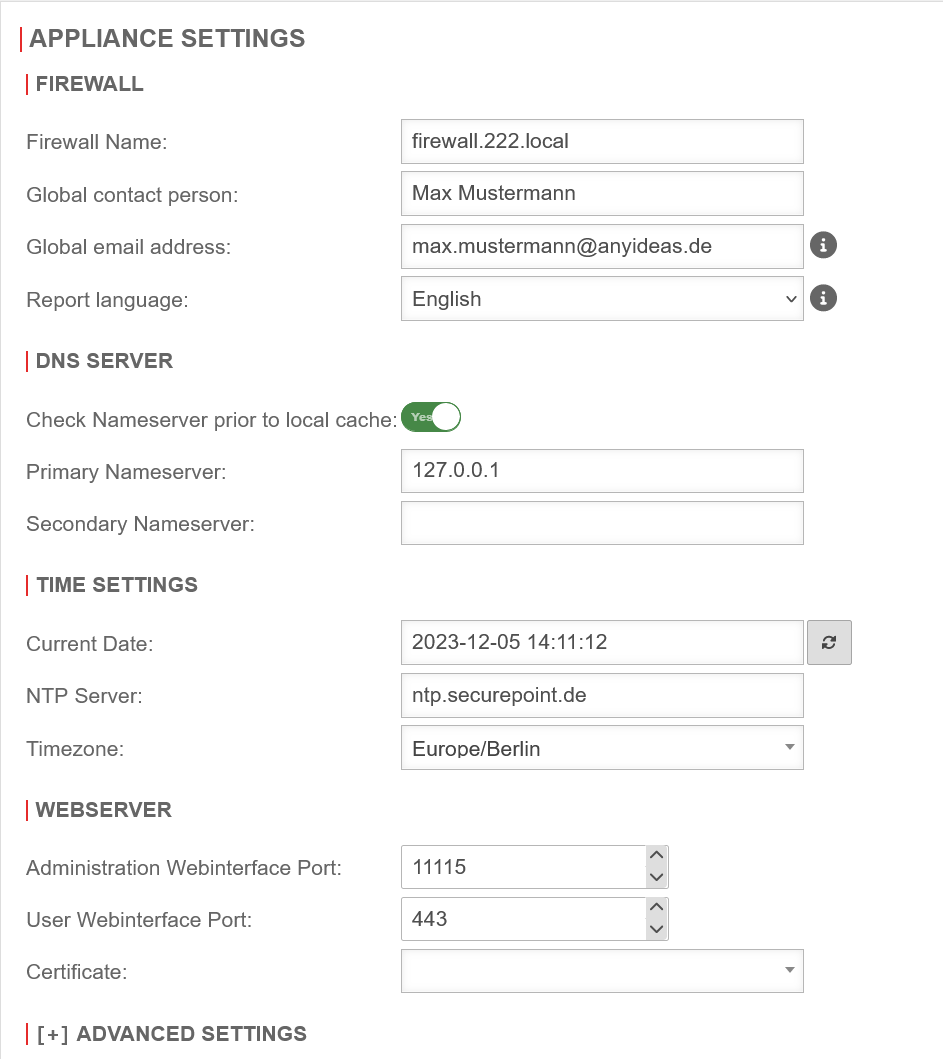 Nameserver IP
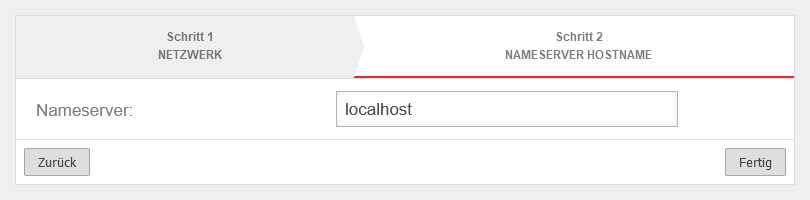
The first step is to define the UTM itself as the nameserver of the firewall.
Nameserver IP
The first step is to define the UTM itself as the nameserver of the firewall.
- Configuration under Area Server settings section DNS Server
- Field Primary nameserver set the IP to 127.0.0.1 (localhost) as IP.
- Save with
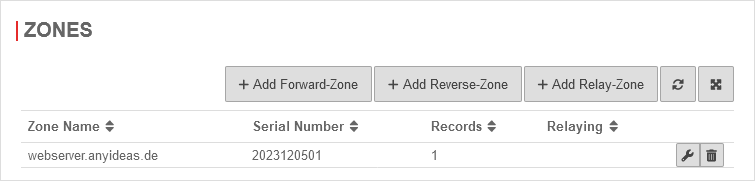
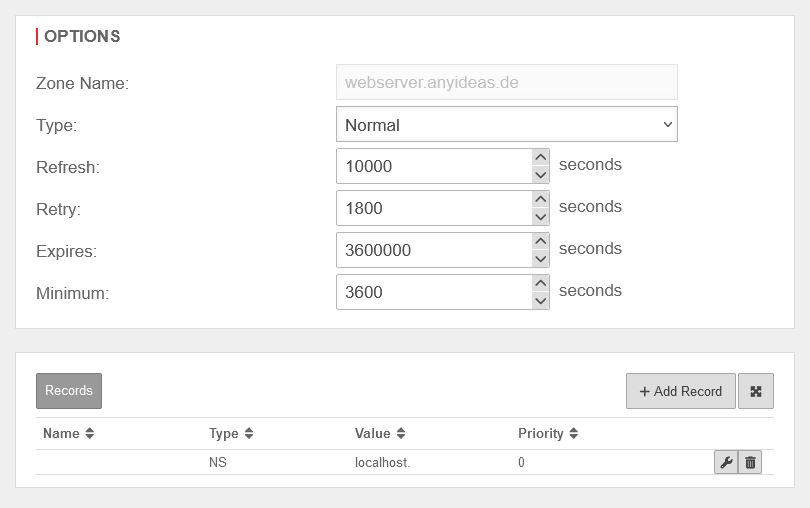
Forward-Zone
A forward zone is used to convert domain names into IP addresses.
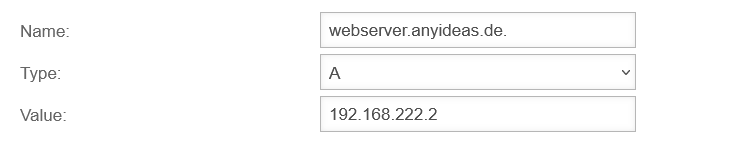
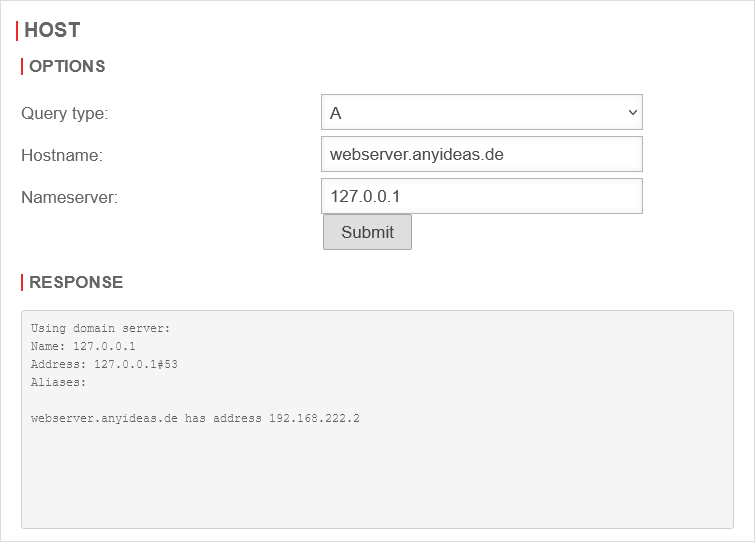
This implementation is possible in both IPv4 (A) and IPv6 (AAAA). The following setup example shows the creation of an A-RR for a public domain.
If the DNS of the firewall is used for resolution, a private IP from the internal network should be returned.
This setting is required, among other things, if a domain whose public IP is that of the firewall is accessed from the internal network.
Without this entry, a complicated port forwarding would be required, but this way the request can be sent directly to the server without any detours.
Setup under Area Zones Button .
Create A-RR
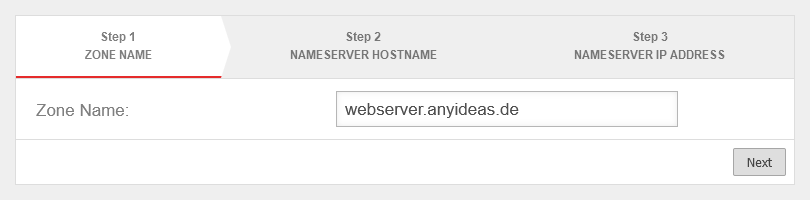
Domain that is managed by an internal DNS server
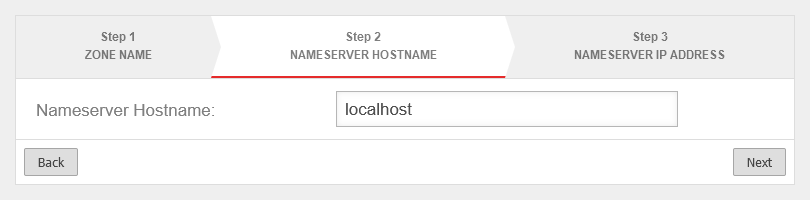
The UTM itself serves as the nameserver
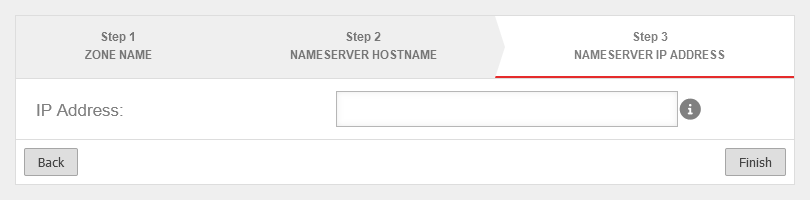
DNS Forwarding
A DNS forwarding is used to forward all DNS requests made to the firewall's name server to another IP.
Add DNS Forwarding
Menu Area DNS Forwarding Button
| Caption | Value | Description | UTMuser@firewall.name.fqdnApplicationNameserver 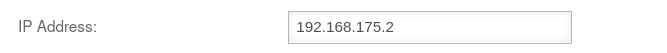 Creating a DNS Forwarding Creating a DNS Forwarding
|
|---|---|---|---|
| IP address: | 192.168.175.2 | Click on and in the IP address field the address of the remote name server is entered
| |
| Saves the entry | |||
Domain forwarding through a VPN tunnel
Sometimes it is necessary to forward internal domain requests to a remote name server located in a VPN.
It should be noted here that, by default, all direct requests addressed to external name servers are sent from the firewall with the external IP. However, a public IP is not routed into a VPN tunnel.
Set the name server of the firewall
| Caption | Value | Description | UTMuser@firewall.name.fqdnNetwork  Name server IP Name server IP
|
|---|---|---|---|
| Check name server before local cache: | Yes | Should be enabled | |
| Primary name server: | 127.0.0.1 | The IP of the UTM itself (localhost=127.0.0.1) | |
| Secondary name server: | Can remain empty or designate another DNS in the VPN | ||
| Saves the entry | |||
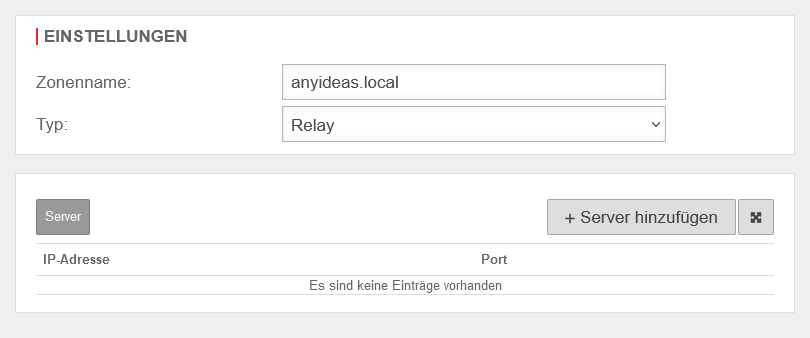
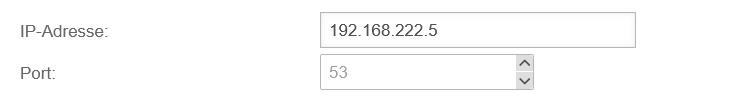
Create relay
Menü Menu Area Zones Button .
| Caption | Value | Description | UTMuser@firewall.name.fqdnApplicationNameserver 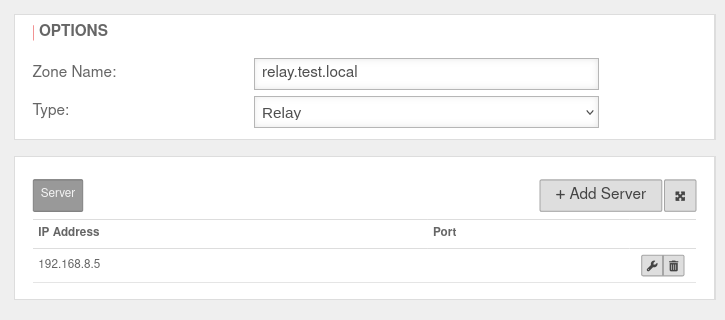 Creating the relay zone Creating the relay zone
|
|---|---|---|---|
| Zone name: | relay.test.local | Zone name of the desired domain | |
| Type: | Select this type | ||
| IP address: | 192.168.8.5 | Click on and in the IP address field the address of the remote name server is entered
| |
| Saves the entry | |||
Create network object
Menu Button . A network object must be created for the IPSec network.
| Caption | Value | Description | UTMuser@firewall.name.fqdnFirewallNetwork object 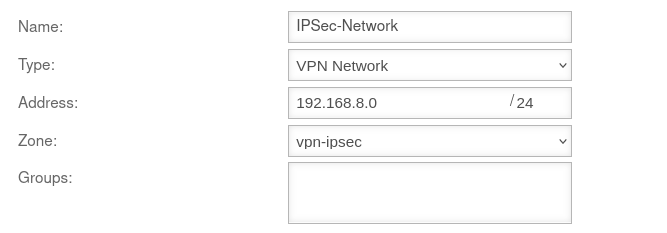 Network object Network object
|
|---|---|---|---|
| Name: | IPSec-Network | Choose unique name | |
| Type: | Select this type | ||
| Address: | 192.168.8.0/24 | The IP address corresponds to that of the IPSec network | |
| Zone: | Suitable zone must be selected | ||
| Saves the entry | |||
Add Rule
In the last step, a firewall rule with a Hide NAT must be created. This causes the DNS forwarding to also go into the tunnel, and not directly into the Internet.
Menu Button .
| Caption | Value | UTMuser@firewall.name.fqdnFirewallPacketfilter 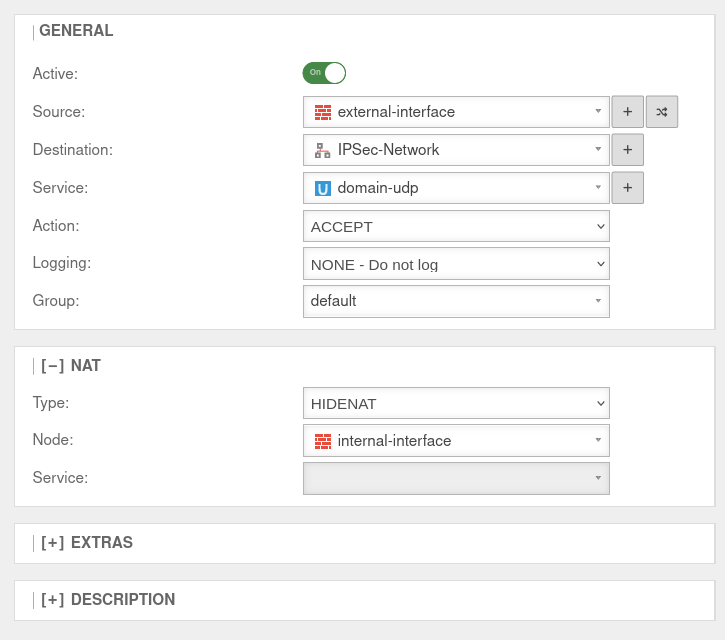
|
|---|---|---|
| Aktive: | On | |
| Source: | ||
| Destination: | ||
| Service: | ||
[-] NAT
| ||
| Type: | ||
| Network object: | ||
| Saves the rule and closes the dialogue. The rules must then be updated. | ||
Safe Search with external DHCP server
If an external DHCP server is used, the active web filter Safe Search often does not work for search engines, especially Google, when searching for images.
In order for this web filter to take effect there as well, the following forward zones must be set up for all ccTLDs (see https://www.google.com/supported_domains : www.google.de, www.google.ch, ...).
Menu Button .
| Caption | Value | UTMuser@firewall.name.fqdnApplicationNameserver 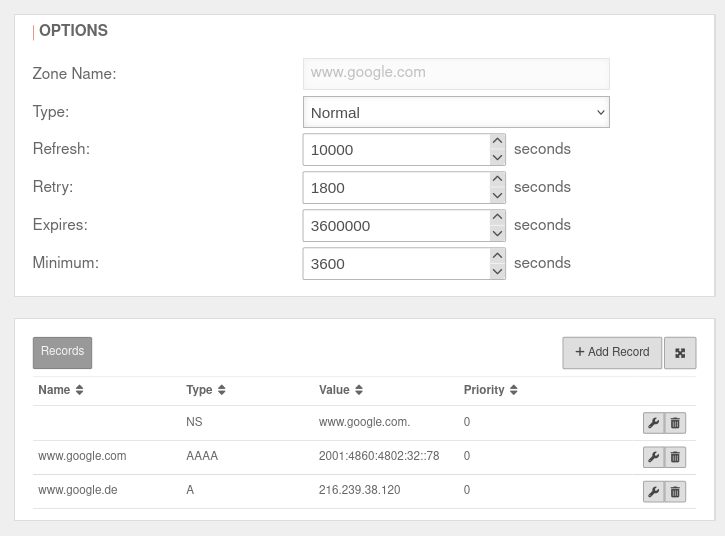 The forward zone set up for www.google.com The forward zone set up for www.google.com
|
|---|---|---|
| Zone name: | www.google.com | |
| Name server hostname: | localhost | |
| Name server IP address: | ||
| In the Name server window, click in the www.google.de zone. In the Edit Zone window click . | ||
| Name: | www.google.com | |
| Type: | A | |
| Value: | 216.239.38.120 | |
| and click again on . | ||
| Name: | www.google.com | |
| Type: | AAAA | |
| Value: | 2001:4860:4802:32::78 | |
| Saves the entry | ||
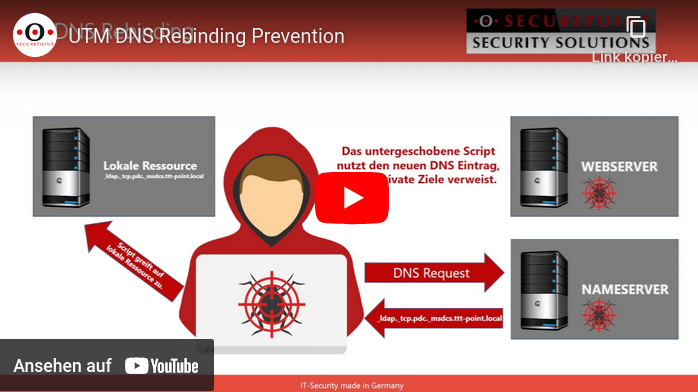
DNA rebinding attack and prevention
This type of attack attempts to gain access to internal resources using falsified DNS responses.
The attacker needs nothing more than a domain with malicious code and a name server that answers all DNS queries for the attacker site.
1. the victim is lured to a prepared website whose IP address is only marked as valid for a few seconds.
2. Malicious code is loaded on the website, which starts a new call after the IP address has expired,
3. but which now uses a modified, proprietary DNS server to display an address from the victim's local network as the destination
4. The attacker now has access to the host with the internal IP through his malicious code (e.g. Java script)
DNS rebinding prevention prevents internal IP addresses from the local network from being issued in response to a DNS query.
Configuration
DNS Rebinding Prevention is configured under Area DNS Rebinding Prevention.
| Caption | Value | Description | UTMuser@firewall.name.fqdnApplications 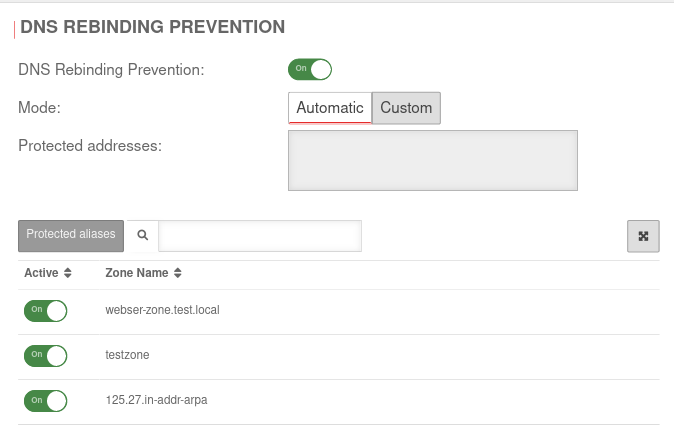 DNS Rebinding Prevention tab DNS Rebinding Prevention tab
|
|---|---|---|---|
| DNS Rebinding Prevention: | On default |
Activates DNS rebinding prevention | |
| Mode: | In the factory settings, all private IP addresses (class A, B and C) are blocked. The corresponding private IPv6 addresses and the unique local unicast address are also protected in automatic mode. | ||
| The addresses can be set manually. | |||
| Protected addresses: | All addresses that are protected by the prevention are displayed here. | ||
| Saves the settings | |||
| ' | |||
mDNS-Repeater
Area mDns-Repeater
The multicast DNS repeater forwards mDNS queries between interfaces and networks without the need to configure an extra DNS server.
Multicast-capable devices, such as printers, can be made visible across different networks.
| Caption | Value | Description | UTMuser@firewall.name.fqdnApplications 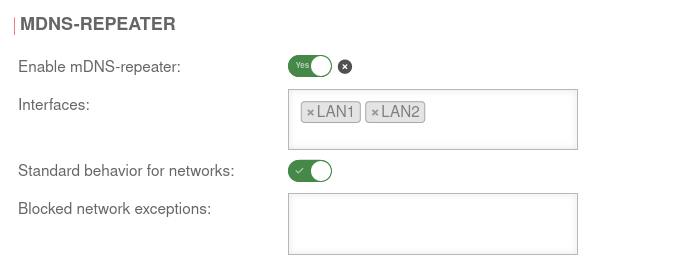 mDNS repeater configuration mDNS repeater configuration
|
|---|---|---|---|
| Activate mDNS repeater: | Yes | Activates the multicast DNS repeater | |
| |
The mDNS repeater is active | ||
| |
The mDNS repeater is deactivated | ||
| Interface: | ×LAN1 ×LAN2 | Selection of the interfaces between which mDNS requests are to be forwarded. At least two interfaces must be entered.
| |
| Default behavior for networks: | default | All networks connected to the interfaces use the mDNS repeater | |
| Blocked network exceptions: | Networks from which mDNS requests are not forwarded | ||
| Allowed network exceptions: Only if Default behavior for all networks is deactivated | Explicit specification of the networks from which mDNS requests are forwarded | ||
General Settings | |||
| General settings are made under Area General. | |||
| Caption | Value | Description | UTMuser@firewall.name.fqdnAnwendungen 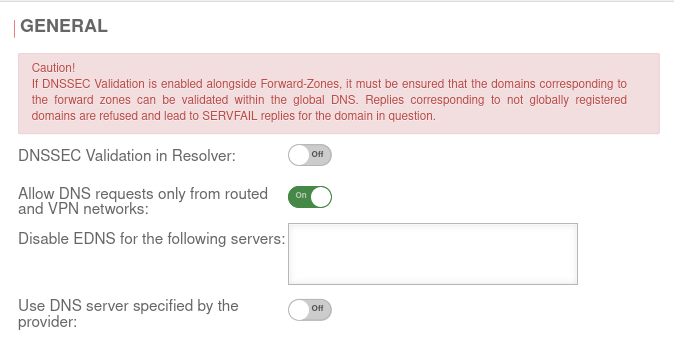 Tab General Tab General
|
|---|---|---|---|
| DNSSEC validation in resolver: | Off | notempty Caution! If DNSSEC Validation is enabled alongside Forward-Zones, it must be ensured that the domains corresponding to the forward zones can be validated within the global DNS. Replies corresponding to not globally registered domains are refused and lead to SERVFAIL replies for the domain in question. When this function is activated, all DNS entries are resolved with DNSSEC without exception. This would also attempt a validation in the DNS hierarchy for only local addresses. However, due to the lack of uniqueness of the local address, it cannot be registered with higher-level DNS servers. An error message appears, the address is not resolved and the zone is therefore not accessible (using DNS). This applies, for example, to .local domains! Further information on the implementation of DNSSEC can be found here. | |
| Allow DNS queries only from routed and VPN networks: | On Default |
By default, only DNS queries from the following sources are answered:
| |
| Off | If DNS queries are to be answered from other external networks as well, this option must be disabled | ||
| Disable EDNS for the following servers: | EDNS can be disabled for servers that do not comply with RFC 6891. Old or misconfigured name servers sometimes do not use or do not correctly use Extended DNS and as a result do not accept DNS queries that use these protocol extensions. The DO flag (DNSSEC OK) can no longer be placed in the standard header. | ||
| notempty New as of v12.6.0 Use DNS server specified by the provider: |
Off | When activated, the DNS server of the Internet provider is used. | |