Installing applications via Android Packages (APKs) outside of the Google Play Store
Last adaption: 03.2025
New:
- Section closedTracks updated and revised
- Maximum size of private apps corrected from 250MB to 100MB
This article refers to a Beta version
Apps in the Play Store go through a review by Google.
APKs without this check pose a significant security risk. Be it through targeted malicious code that lands unchecked on the device due to installation from unknown sources, or even just bad code that contains unknown security vulnerabilities.
APKs without this check pose a significant security risk. Be it through targeted malicious code that lands unchecked on the device due to installation from unknown sources, or even just bad code that contains unknown security vulnerabilities.
Installation options
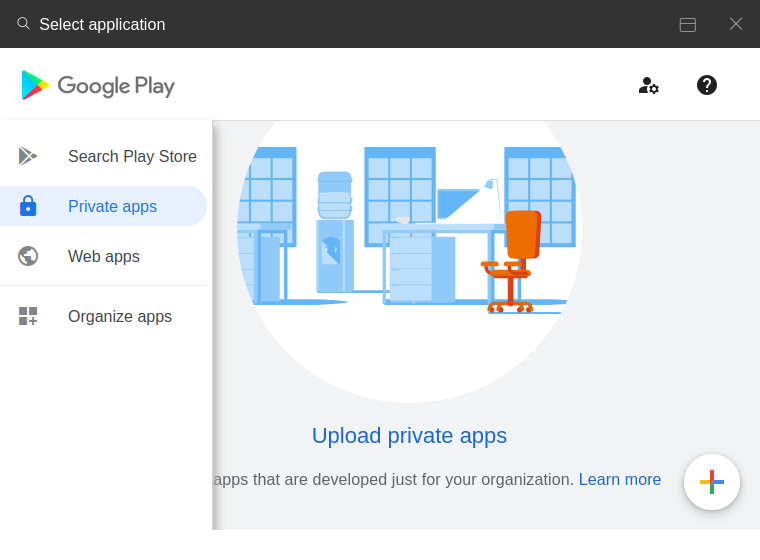
Private Apps
- Open profile
- Applications tab
- Add application
- Select application button (Google Play Store dialog opens)
- Menu left side: private Apps
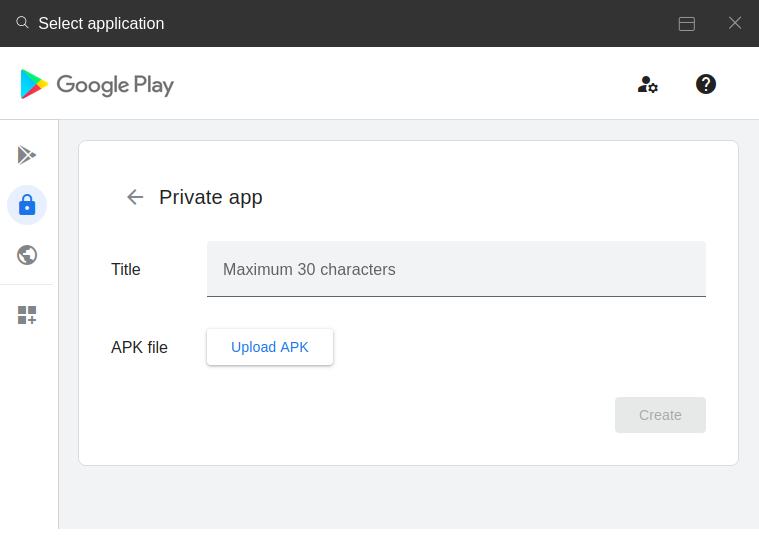
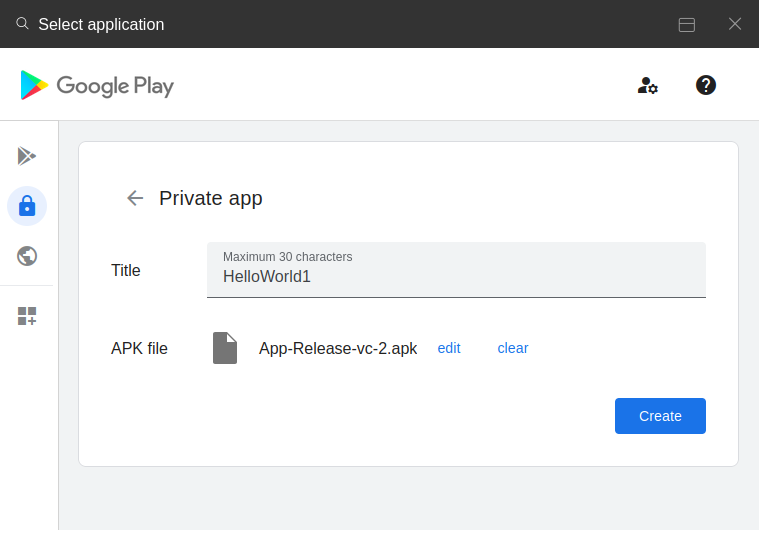
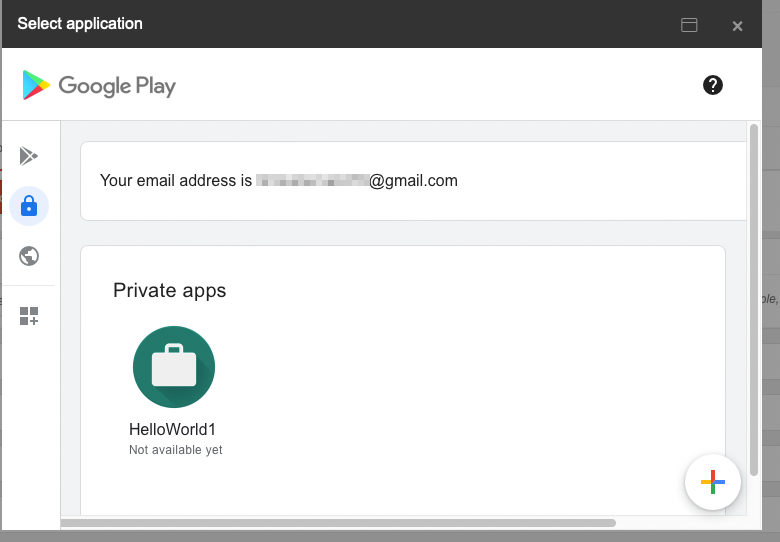
- Upload Private App
→ High developer effort: A separate APK must exist for each customer
per closedTrack in cooperation with the developer
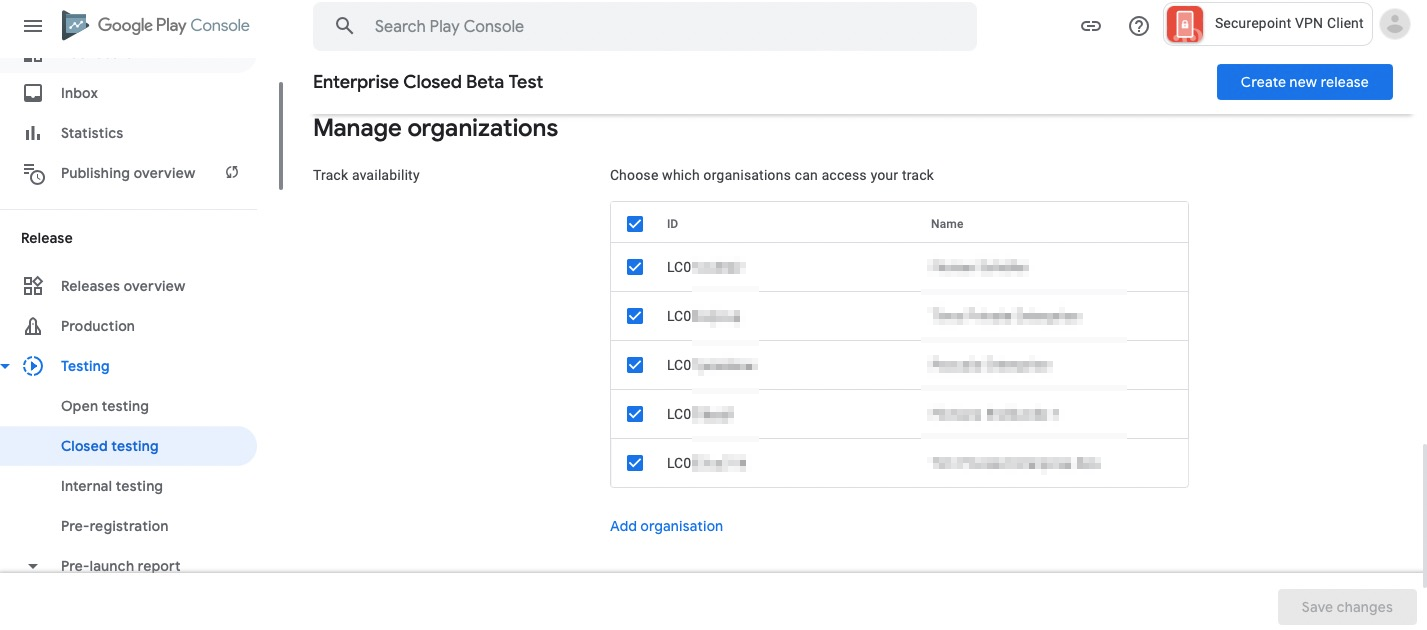
Use of closedTracks | |||
| Google explicitly provides for the use of closed tracks not only for beta versions with a closed circle of testers, but also "... customers may need more granular control over which versions of an app reaches end users." Managed Google Play Help | |||
| This procedure offers the following advantages:
| |||
| Requirements (developer-side steps) |
 | ||
|---|---|---|---|
| |||
Before app release in the Play Store
| |||
| Before the app is released in the Google Play Store, it can go through different testing phases
These closed tests offer the option to deliver app updates via email lists or Enterprise IDs Organisationen in EMM context
|
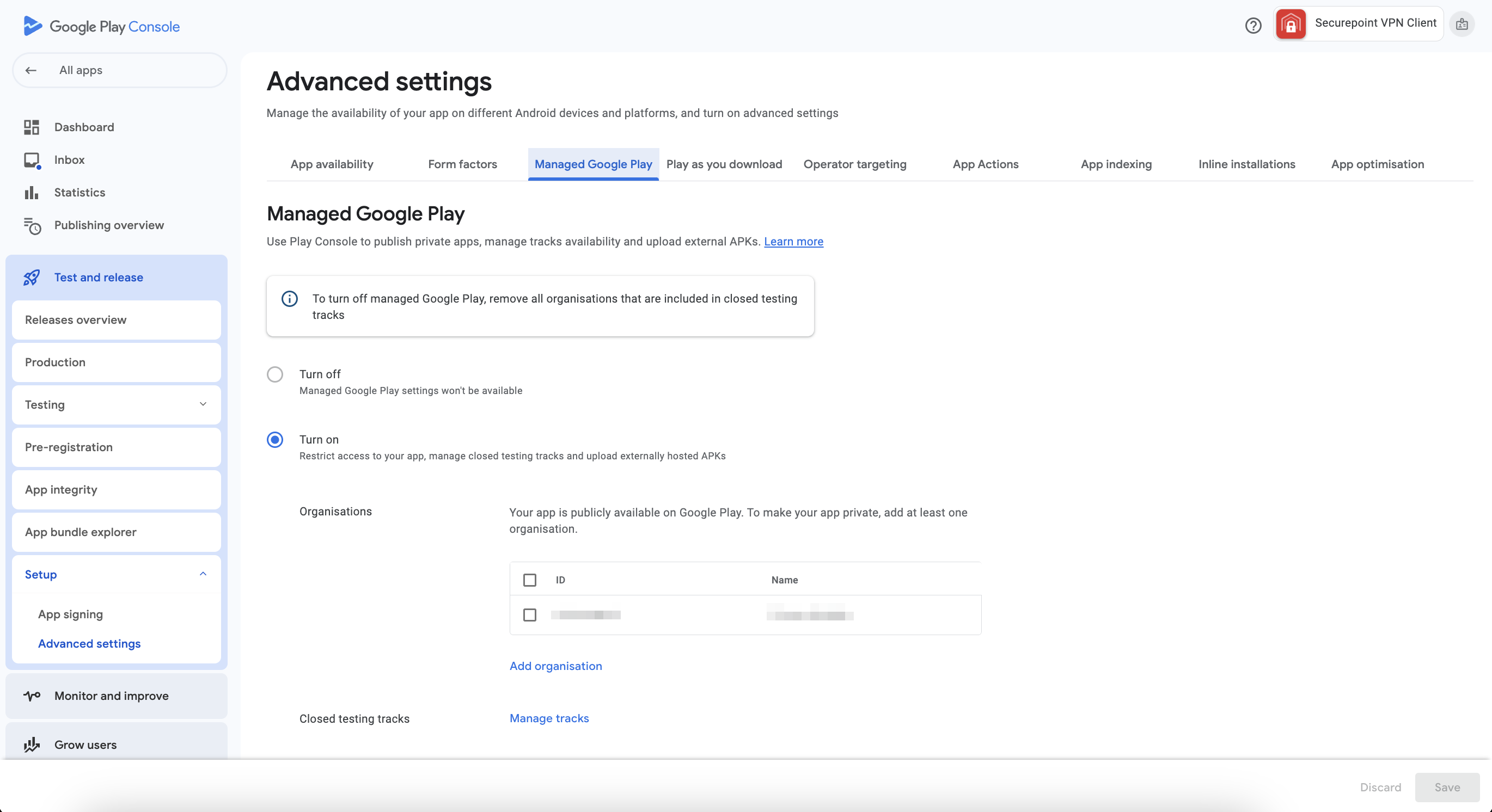 | ||
| If the app is not intended to manage APKs via Google's automatic developer account, but instead should be managed through a custom developer account, there are two options for this: | |||
| Make app public |
| ||
| Set app to private |
App access is restricted to Enterprise IDs
| ||
Integrate into the portal | |||
| Unified Security Portal → Open profile → Tab Applications | |||
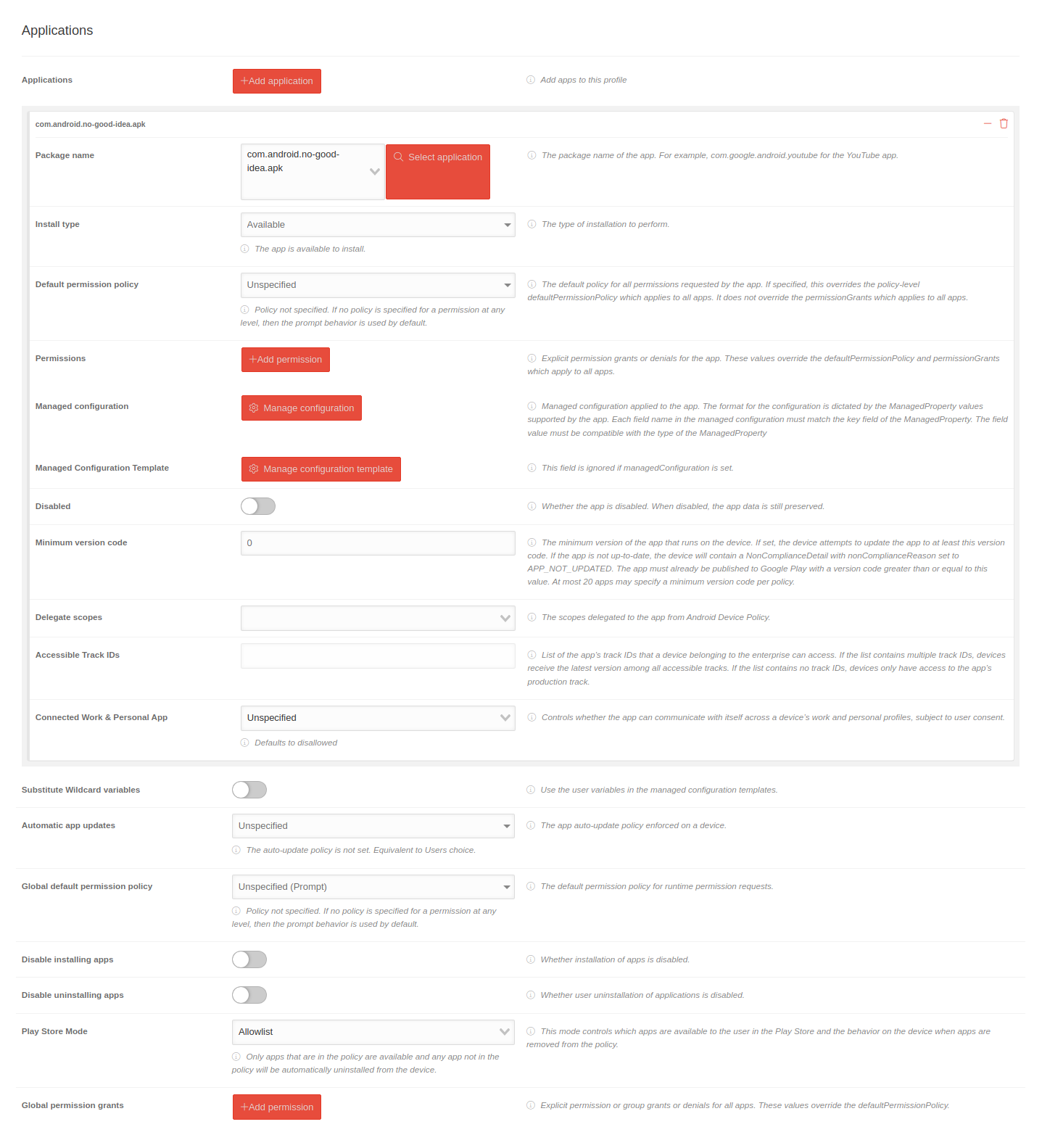
| Application | Add application | 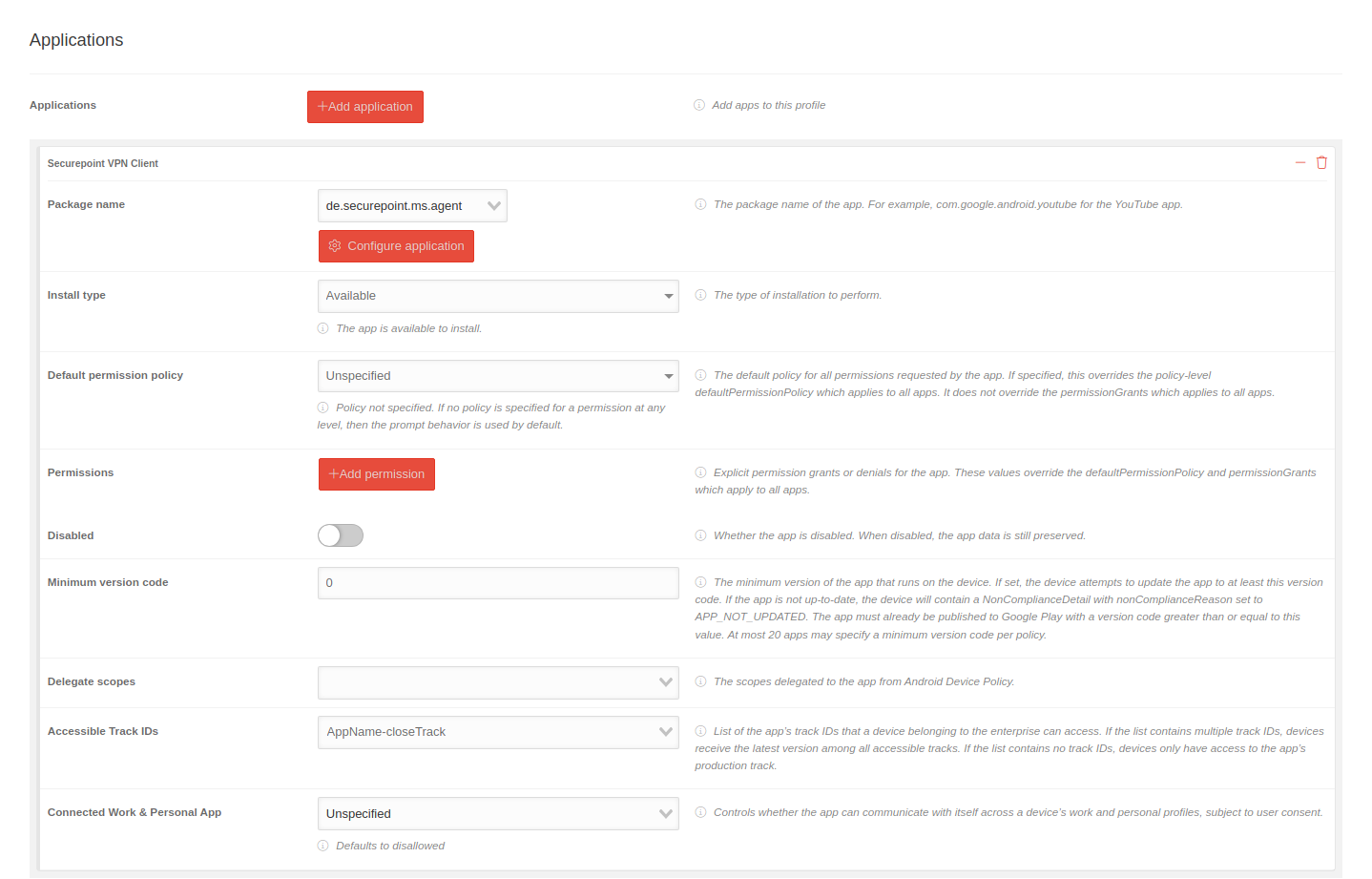 | |
| Package name | de.securepoint.ms.agent | Add package name (must be provided by the app developer) | |
| Installation type | Available Force installation |
Select appropriate installation type: Available or Force installation | |
| Accessible Track IDs | AppName-closedTrack |
| |
Installation via sideloading (not recommended!)
- Open profile → Restrictions tab:
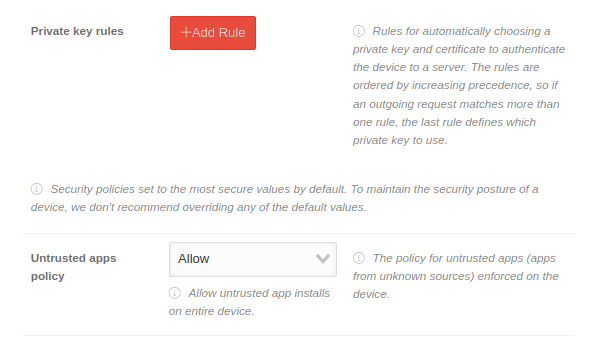
- Untrusted apps policy → "Allow"
- Applications tab (if Play Store Mode is on Approval List)
- Add package name
- Installation type Available or Force installation
- Install APK manually on the devices
- Untrusted apps policy → "Do Not Allow"
- No review by Google → No quality assurance
- No verification by Google Play Protect → Changes to the original source code are not detected
- No update channel → New versions must be installed manually again
- Each device must be updated individually
Error message / Troubleshooting
| Error message | Cause | Solution |
|---|---|---|
| APK has been signed with an insecure key size | Google classifies the key length as too insecure | Google requires a key length of at least 2048 bits. Create new key with at least this bit length. |