Last adaptation to the version: 1.5 (11.2019)
- Added warning about missing operating modes
- Layout and design adjustments
- 07.2024
notempty
- Automatic enrollment after a factory reset
- Interaction-free installation and updates of apps without Apple ID
- Reenrollment
- The devices can be permanently removed from the MDM from the end device
Technical requirements
- iPhone / iPad (min. iOS 11)
- Access to the Securepoint Mobile Security Portal
- For security reasons, Apple provides the full functionality for iOS devices only in supported mode.
Requirements for this:- Apple Mac (min. macOS 10.14 or later)
- Apple Configurator 2 (at no charge in the App Store)
- It is possible to have notifications sent automatically as soon as a device is enrolled or unenrolled.
Further information in our Wiki article.
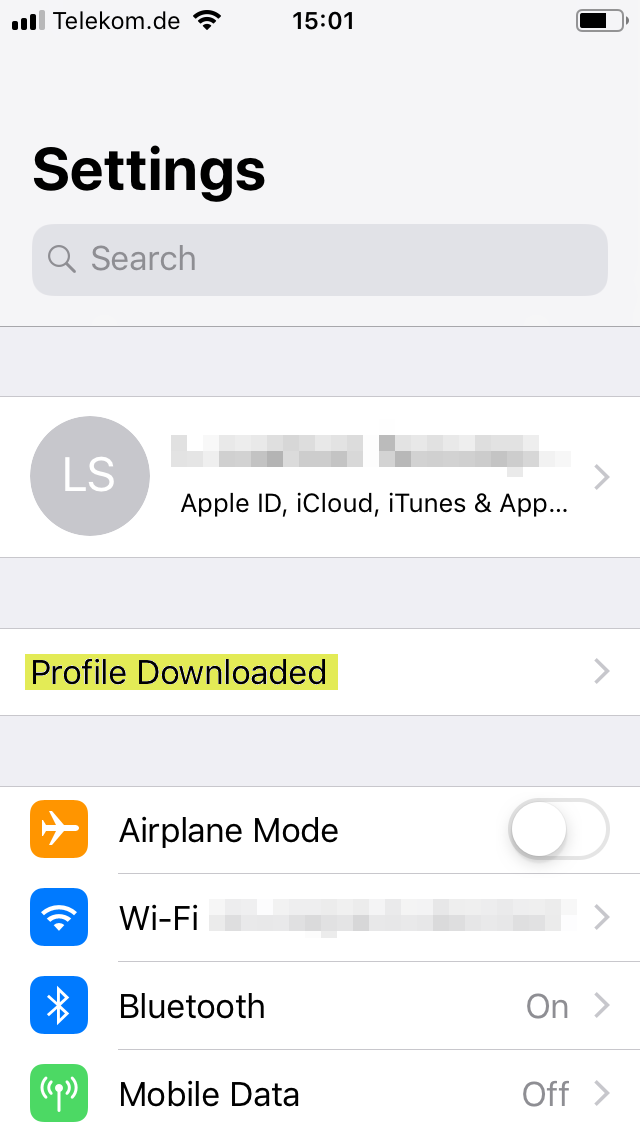
Prepare device
The onboarding of iOS can be performed in supervised or unsupervised mode. The differences are listed in a Functional Comparison Overview.
Unsupervised device
User without access to Securepoint Mobile Security Portal
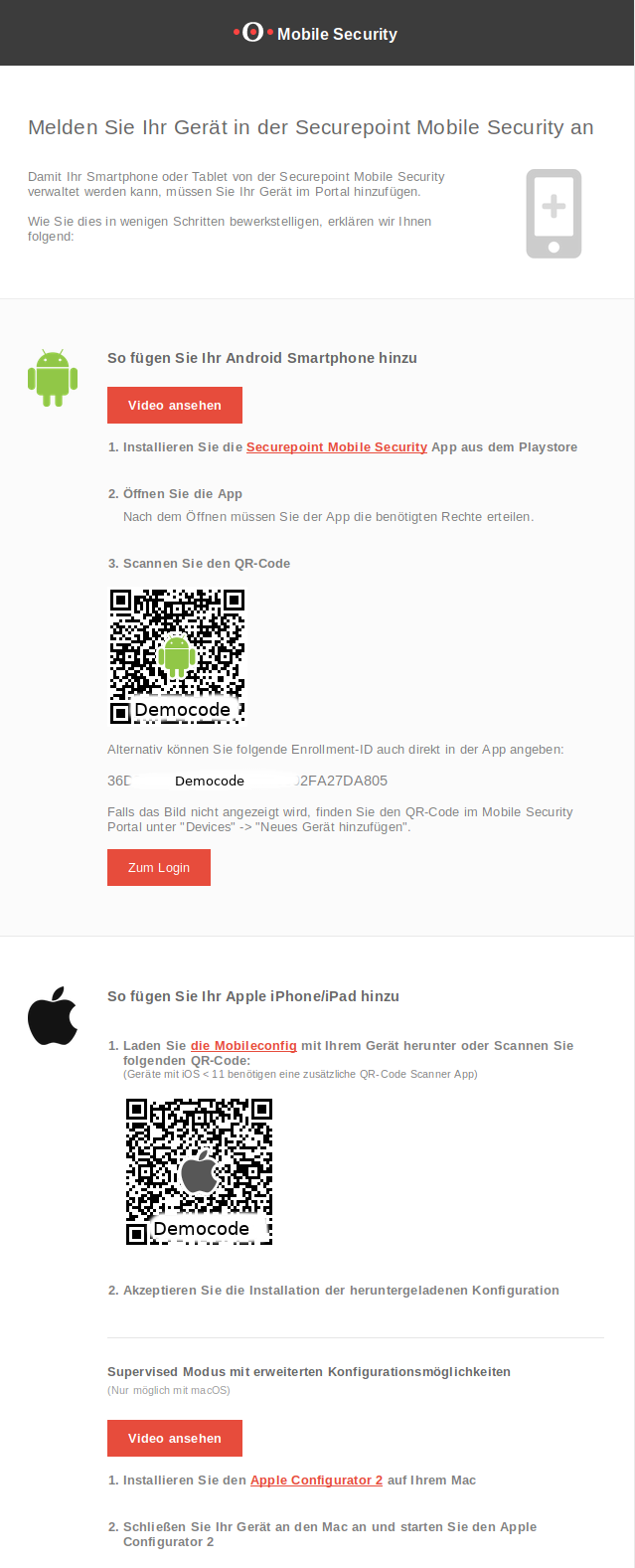
Administrator with access to the Securepoint Mobile Security Portal
| 1. | 2. | 3. |
| Abb.1 | Abb.2 | Abb.3 |
| Abbildungen | ||
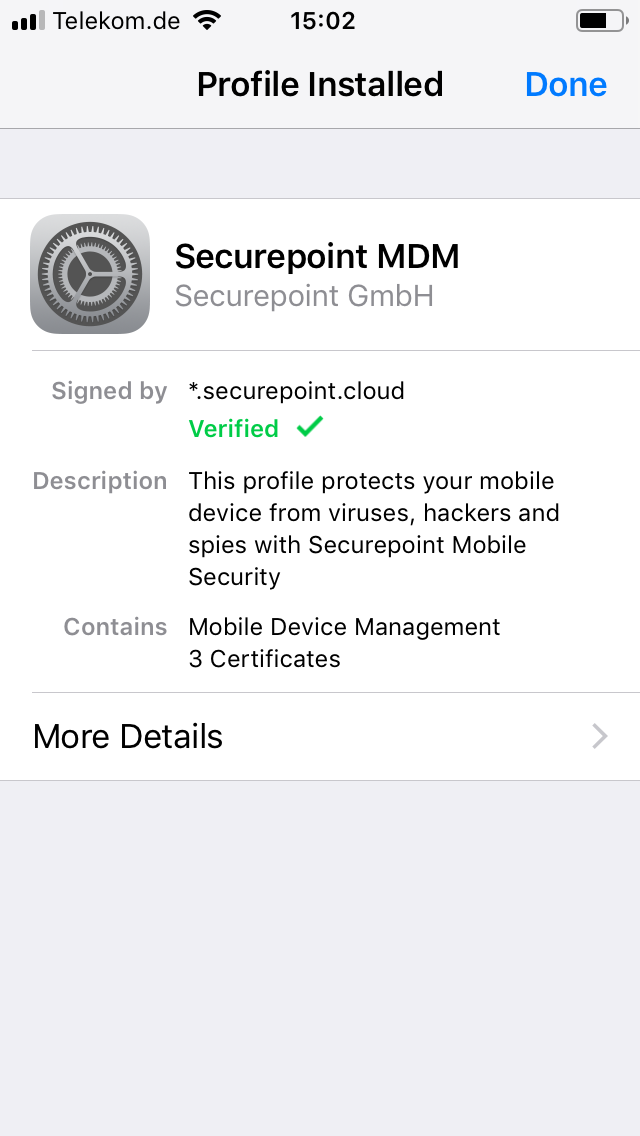
Supervised device
The device is reset to the factory settings. Operating system updates are kept. This process is required in iOS to ensure complete control over the device and to prevent unwanted apps from being allowed or uninstalled.
Preparation
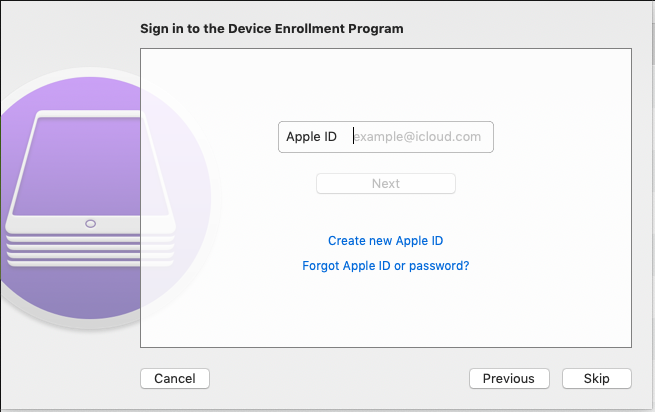
- Log on to https://appleid.apple.com with the login data, used on the device.
- In the Devices section, remove the device in question.
Configuring the device
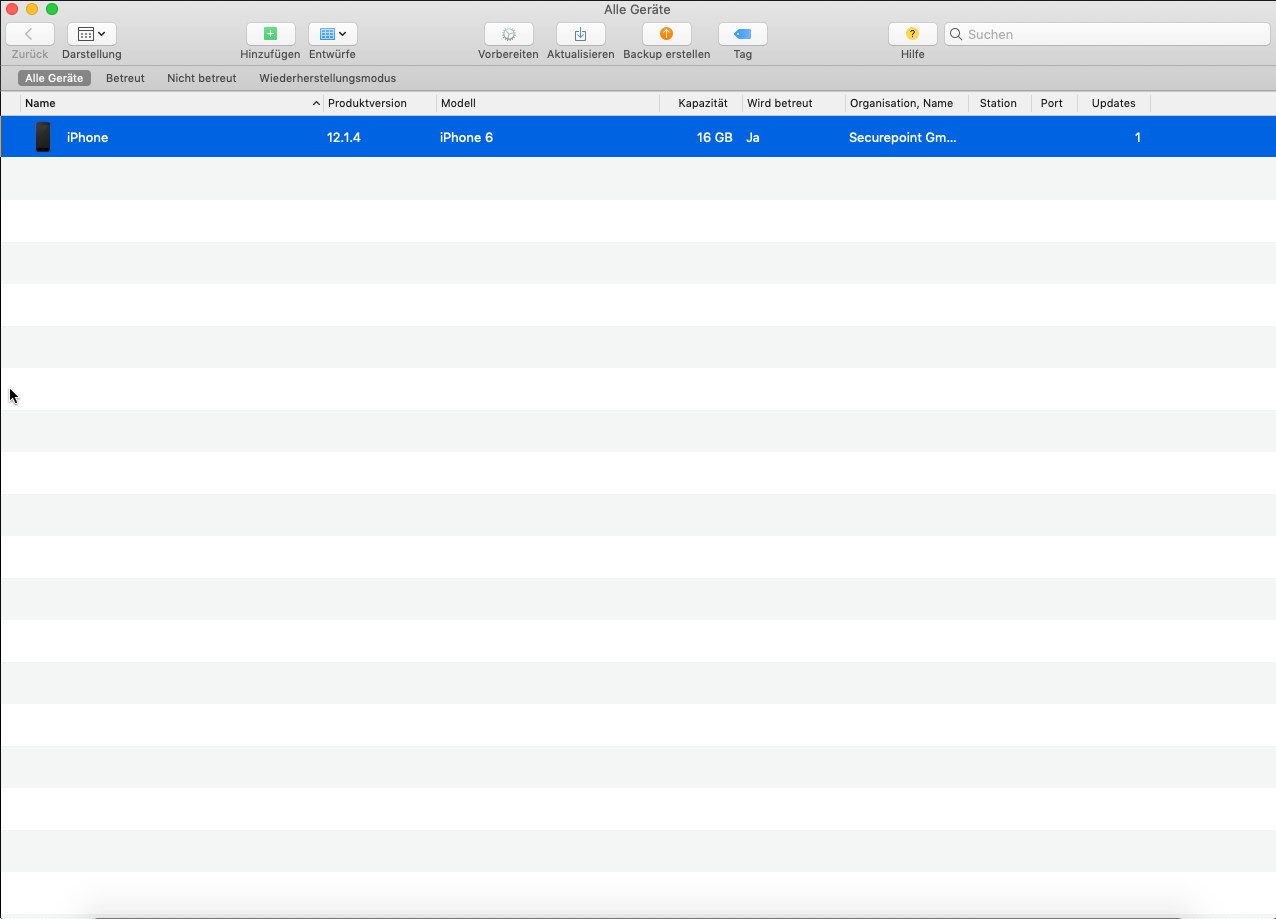
- Preparation in Apple Configurator2:
- Connect your iPhone / iPad to your Mac
- Ignore the message "A new network connection was found" with .
| 1. | 2. | 3. |
| Abb.1 | Abb.2 | Abb.3 |
| Abbildungen | ||
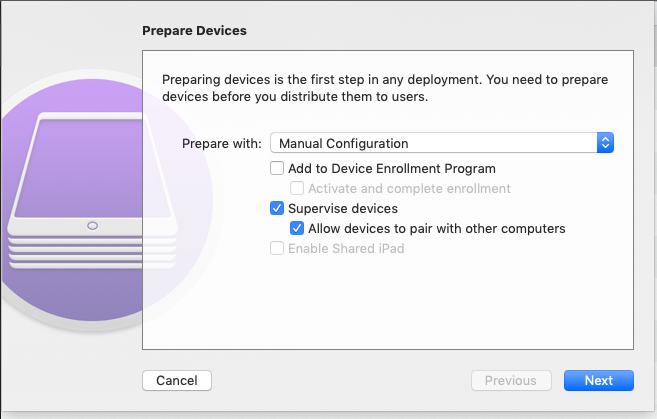
activation of:
Supervise devices
Allow devices to pair with other computers
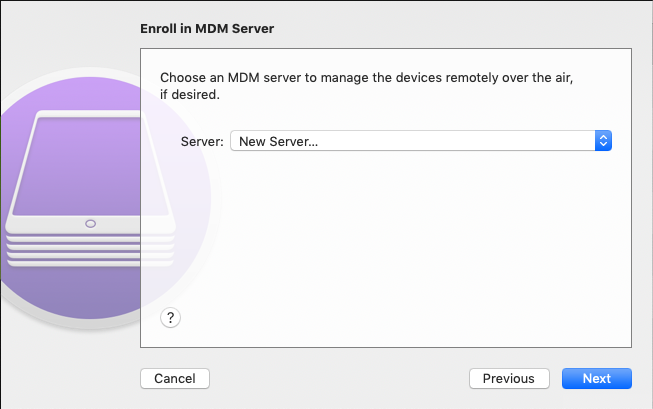
Server: New Server…
If another device has already been enrolled, the server can be selected here. Otherwise the configuration is done in the next step.
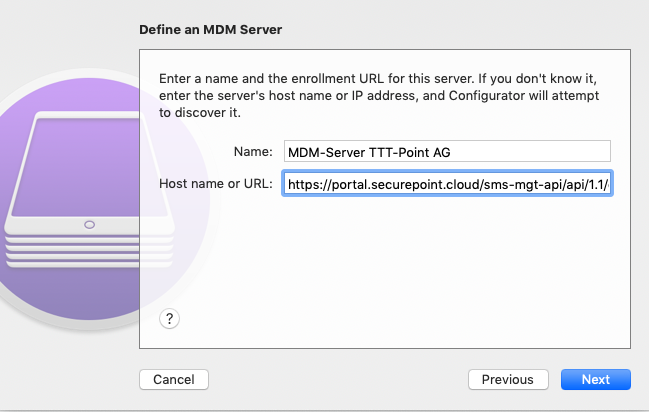
A meaningful name can be assigned here.
This configuration can be selected directly for other devices that are to be registered for the same customer (or tenant).
Name: Unique name (customizable)
Hostname or URL: Insert the URL from the dialog in the Securepoint Mobile Security Portal (see previous step)
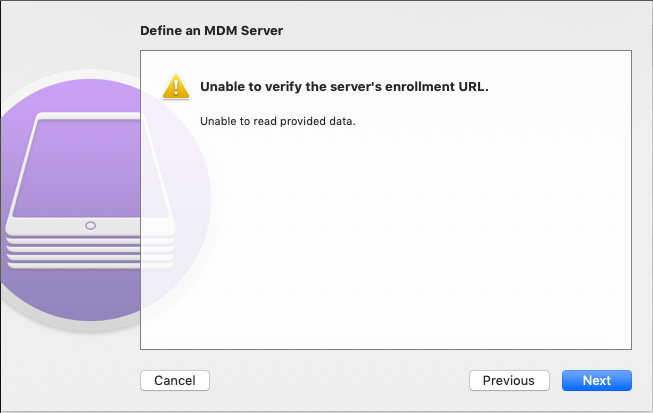
Unable to verify the server's enrollment URL
Since macOS does not know the certificate of the individual customer access to the Securepoint Mobile Security Portal, the certificate cannot be checked, but is still correct!
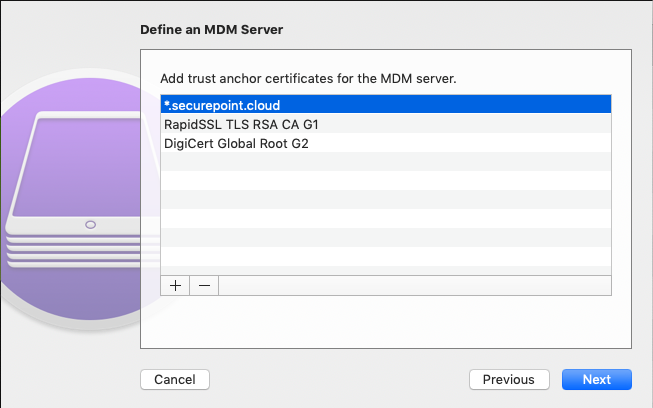
Add trust anchor for the MDM server:
The certificate *.securepoint.cloud is already installed.
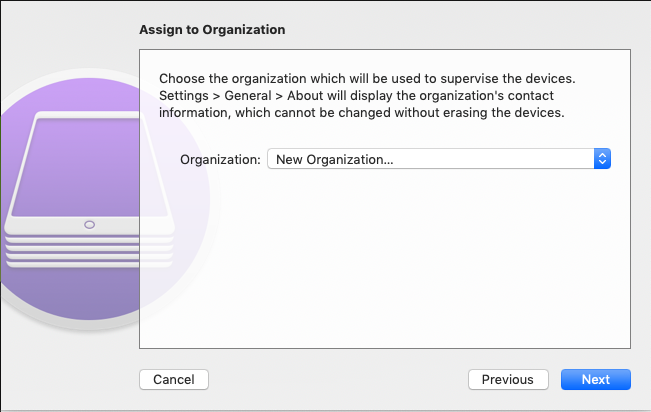
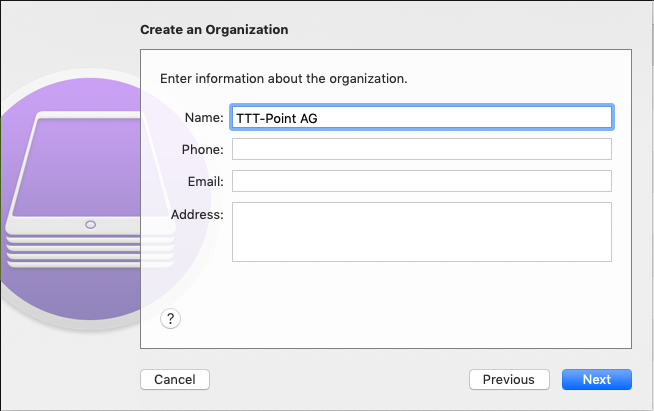
Create an organization, if necessary:
If this is the first device for this organization to be registered in the portal, information about the organization should be entered.
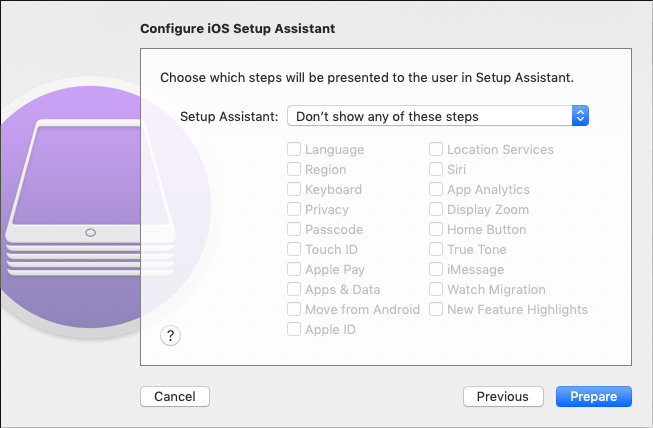
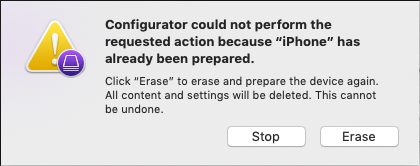
If this message appears, this device has already been configured once and the System Assistant settings cannot be transferred directly.
With all contents and settings are deleted and the device is prepared for an (initial) configuration with connection to the Securepoint Mobile Security Portal.
- Configuration of the smartphone with the steps previously configured for the iOS installation wizard.
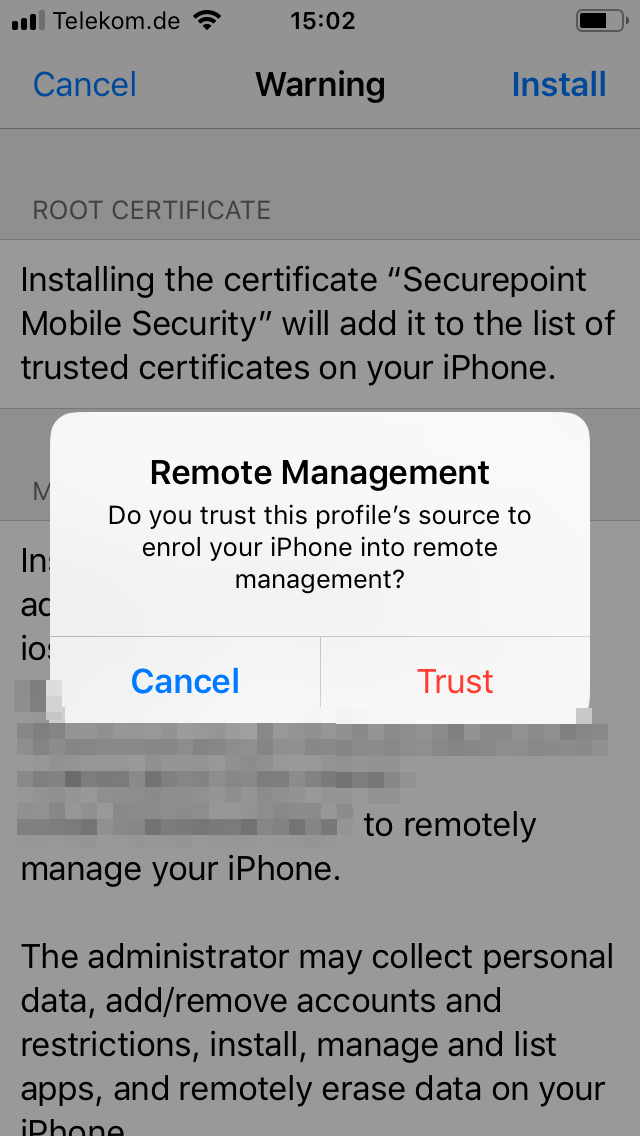
- Allow remote management
Login to the portal
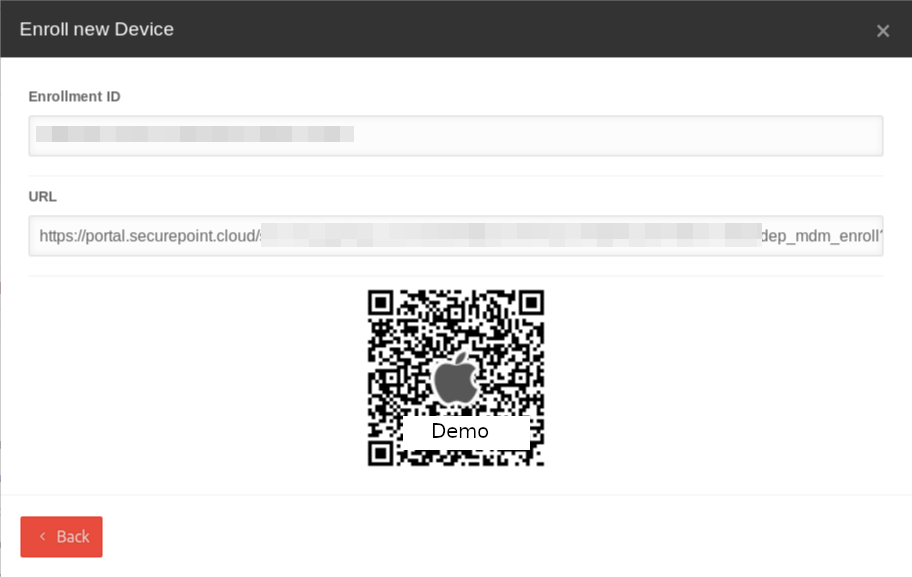
The device is now displayed in the portal and the enrollment must be completed by clicking on the device tile.
Device Alias
For better identification, the device should be given an alias name:
a0a0 (4-digit ID) (in the upper part of the device tile)
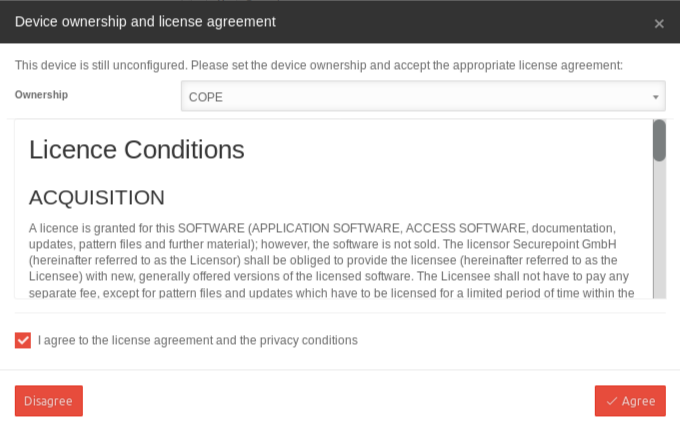
Ownership Selection
There are two different installation options for the Securepoint Mobile Security App, which result in significant differences in administration:
| Owner COPE |
| ||||||||
| Owner BYOD | Standard functional range
| ||||||||