Last adaptation to the version: 2.13 (01.2026)
Preamble
In a profile permissions, restrictions, password requirements, email settings and security settings are configured.
Several users or user groups (roles) can be assigned to a profile.
Several devices or device groups (devices designated by tags) can be assigned to a profile.
- Device registration is directly tied to a profile
- A profile must be created first' (and configured) before a device can be registered
In Android Enterprise profiles, numerous security-relevant settings can be made, e.g.
- Disable Kamara
- Disable microphone
- Disable USB file transfer
- Disable outgoing calls
- Disable Bluetooth
- Disable contact sharing
- Disable tethering
- Disable sms
- Enable network only with VPN
- and much more.
- Outdated Android profiles behave fundamentally different than Android Enterprise Profiles (EMM)
- It is no longer possible to assign a profile to a role, user or tag
Overview of profile management | ||||
| In the profile overview new profiles can be created, existing ones can be edited and deleted. The view of the profiles can be displayed in the list or tile view. You can also view details of existing profiles, update the list of profiles, and publish profiles. | 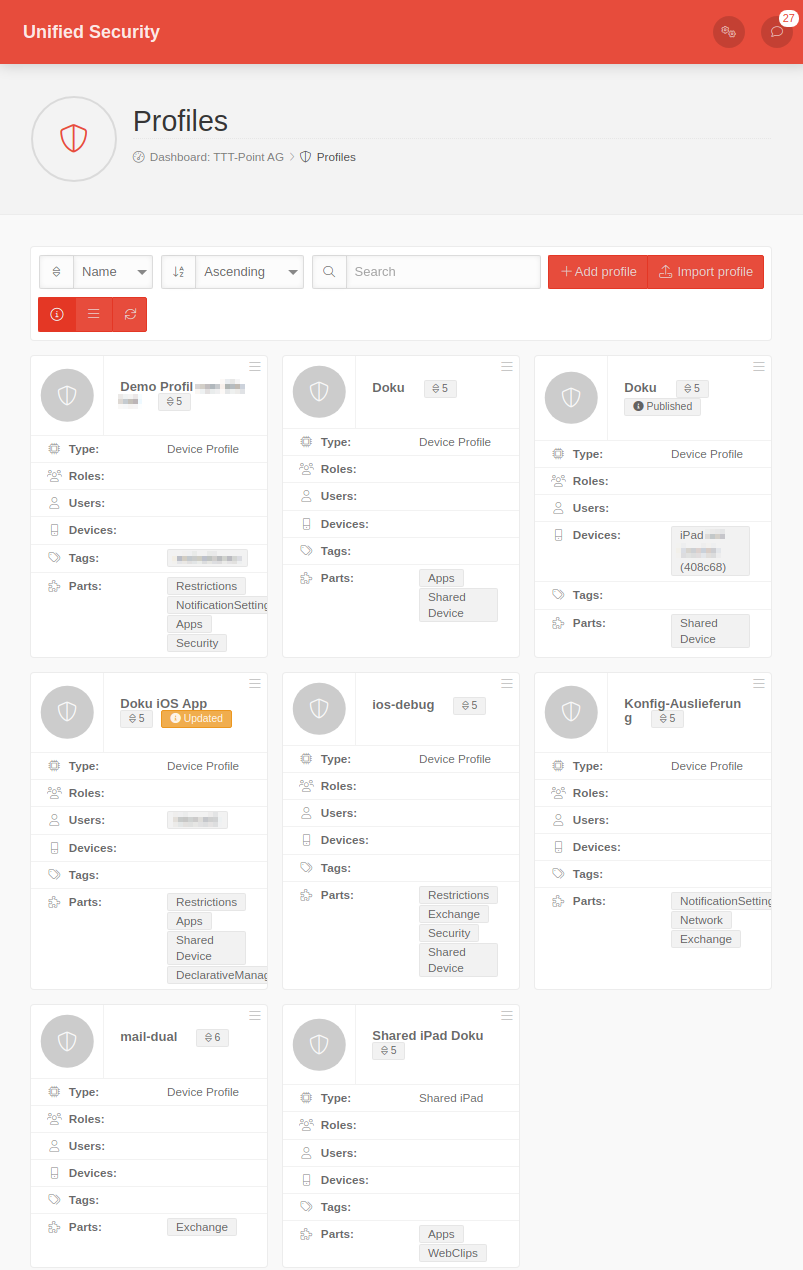 |
 | ||
General Options | ||||
| Sorts the tiles by profile name | ||||
| Sorts the tiles according to the priority of the profile | ||||
| Sorts the tiles in ascending or descending order according to the selected criterion | ||||
| Filters on profile tiles that contain the search text | ||||
| Add profile | Creates a new profile. The settings in the profile vary depending on the operating system. | |||
| Import profile | Existing profiles that were previously exported from the Securepoint Mobile Security Portal can be imported here | |||
| Hide generated profiles | Hides the generated profiles | |||
| Show details | Show / hide details: For a large number of profiles, it can be useful to hide the most important details for clarity. | |||
| / List view / Grid view | Switch between lists and grid view | |||
| Refresh | Refreshes the display | |||
Profile tile
| ||||
Profile-Options
| ||||
| The button at the top right of each profile tile provides the following options: | ||||
| Edit | Editing the settings (see below) | |||
| Copy | Copying the profile to the clipboard | |||
| Export | Exporting the settings | |||
| Delete | The profile is deleted notempty
New as of: 2.5 | |||
Details displayed in the profile tile: | ||||
| Updated | Changes have been made to the profile that have not yet been published! | |||
| Partially installed | Not all sub profiles were able to be installed | |||
Profile information | ||||
| Type | Profile type (see below) | |||
| Roles | Roles | |||
| Users | User | |||
| Devices | Devices | |||
| tags | Tags | |||
| Parts | Listing of the sub-profiles that make up the complete Mobile Security Profile. | |||
Copy & paste of profiles
| ||||
| Click on the logo of the profile tile to mark one or more profiles In the general options, another field now appears under the filter mask: | ||||
| Action for selected items | Execute the selected action with Ok | |||
| Copies one or more selected profiles to the clipboard | ||||
| Deletes one or more selected profiles notempty
New as of: 2.5 | ||||
| Paste | Inserts a copy of a profile from the clipboard
| |||
Android profile configuration
GeneralGeneral | |||
| Caption | Value | Description | 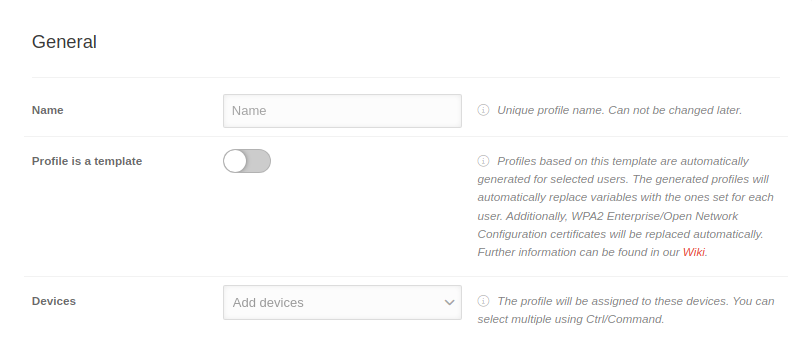 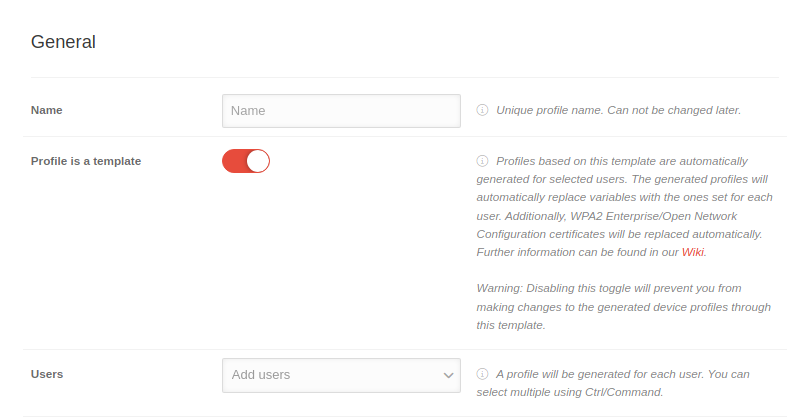 Allgemeine Einstellungen mit Profil ist eine Vorlage aktiv Allgemeine Einstellungen mit Profil ist eine Vorlage aktiv
|
|---|---|---|---|
| Name | Name | Displays or enter the profile name | |
| Profil ist eine Vorlage notempty New as of: 2.8 |
| ||
| Devices Eingeblendet, solange Profil ist eine Vorlage deaktiviert ist |
Add devices | For existing profiles: if available, display of the assigned devices | |
| Benutzernotempty New as of: 2.8 Eingeblendet, solange Profil ist eine Vorlage aktiviert ist |
Benutzer hinzufügen | Es wird für jeden Nutzer jeweils ein Profil generiert. | |
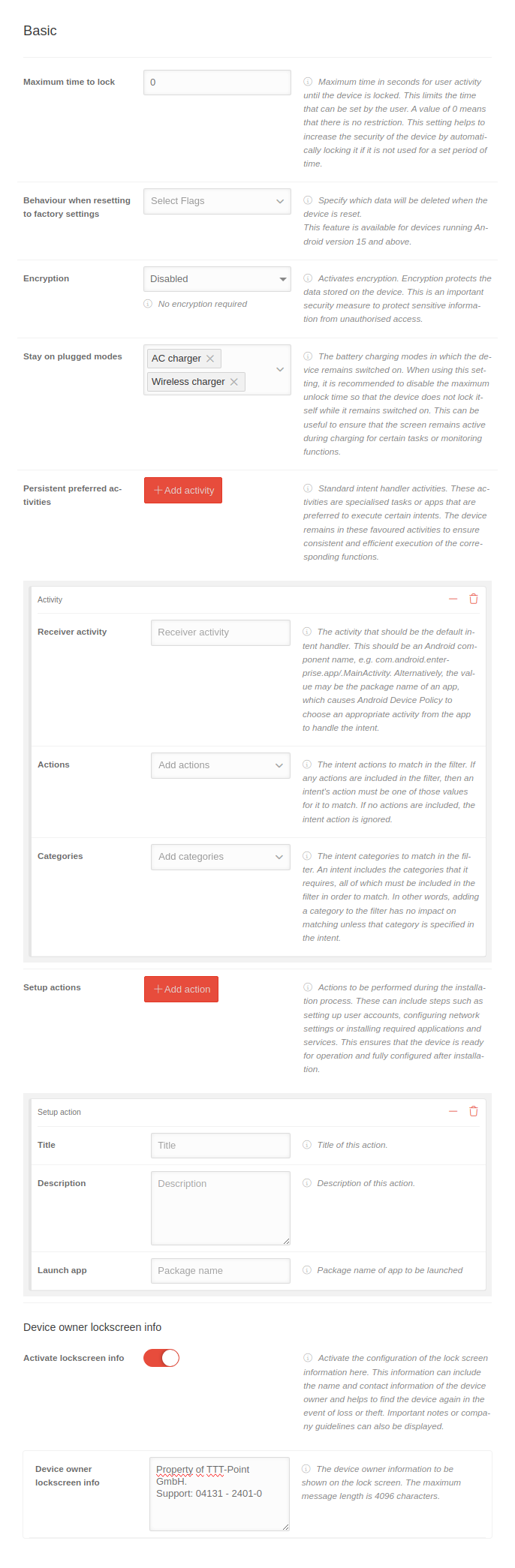
Basic settings
Restrictions
Personal use
| Caption | Value | Description | 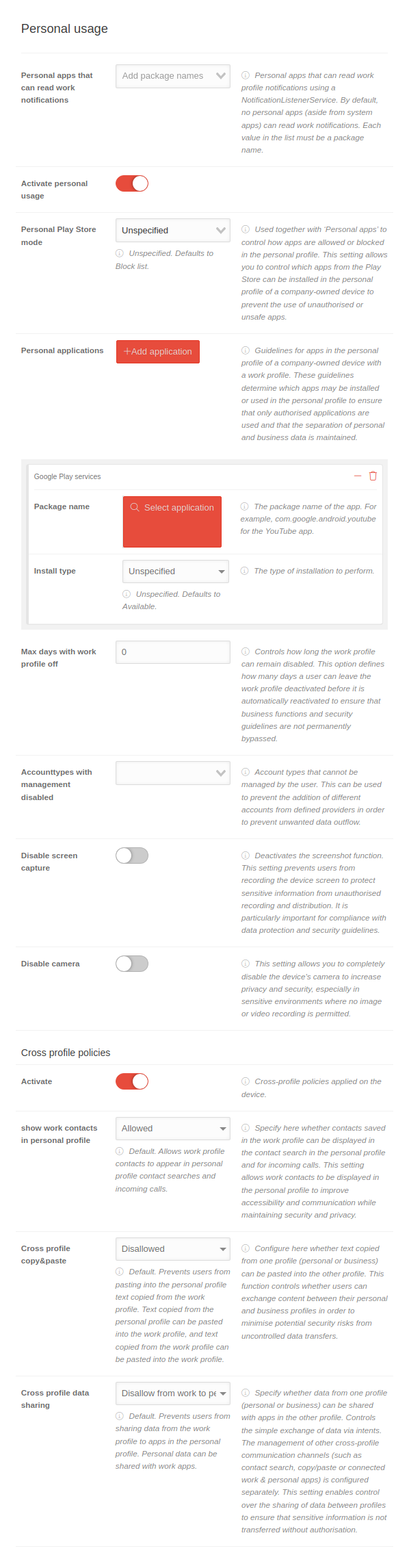 | ||||||
|---|---|---|---|---|---|---|---|---|---|
| Personal apps that can read work notifications | Add package name |
| |||||||
| Activate personal use | Activation allows you to configure the personal use of the Android device | ||||||||
| Personal Play Store mode | Not specified | Used together with "Personal apps" to control how apps are allowed or blocked in the personal profile. | |||||||
| |||||||||
| Personal applications | Add applications | Guidelines for apps in the personal profile of a company-owned device with a work profile. Each click on the button adds a section Application by customizing an app. | |||||||
| Package name | com.google.android.youtube Select application | The package name of the app. For example, com.google.android.youtube for the YouTube app. Clicking on the button Select application opens the Google Play Store to select the app. | |||||||
| Installation type Only appears when an app is selected in Package name. |
Not specified | The way the installation is performed. | |||||||
| |||||||||
| Max. days without work profile | 0 | Controls how long the work profile can remain switched off. | |||||||
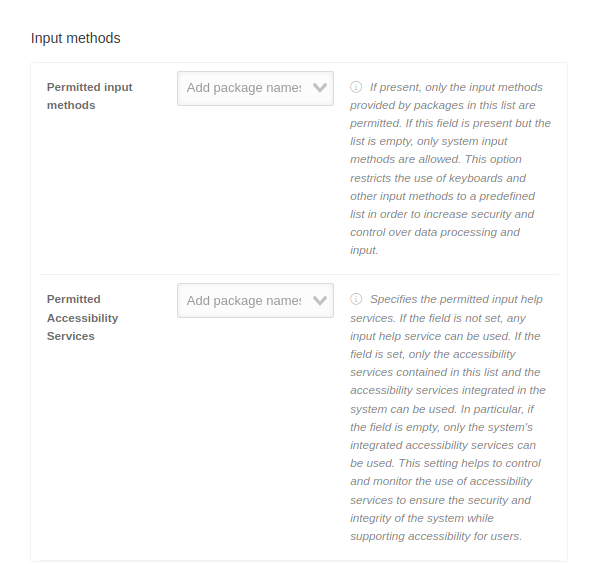
| Account types with management disabled | Account types that cannot be managed by the user | ||||||||
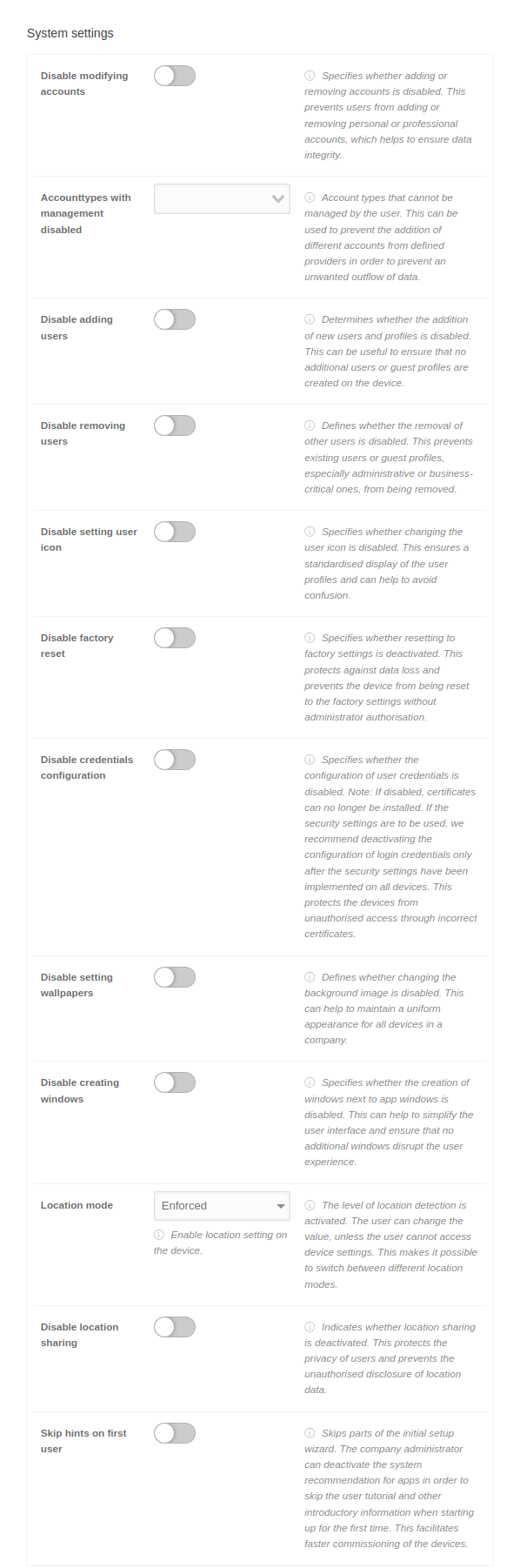
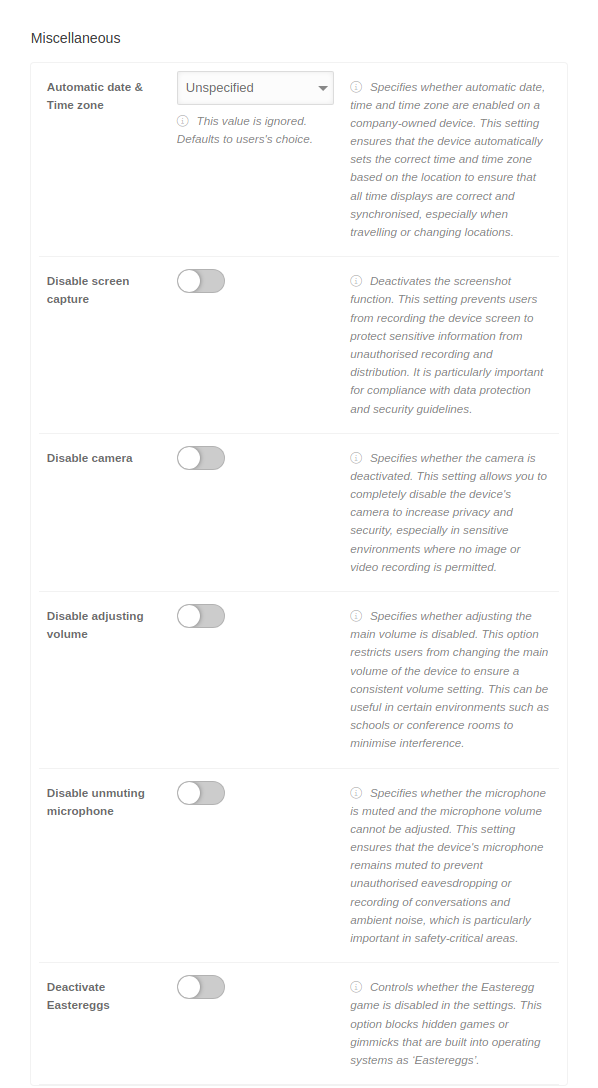
| Disable screen capture | If is activated, the screenshot function is deactivated.
This setting prevents users from recording the device screen to protect sensitive information from unauthorized recording and distribution. It is particularly important for compliance with data protection and security guidelines. | ||||||||
| Disable camera | When activated , the device's camera is completely deactivated.
This increases privacy and security, especially in sensitive environments where no image or video recording is permitted. | ||||||||
| Cross-profile guidelines | |||||||||
| Activate | If is activated, cross-profile policies are applied to the device | ||||||||
| Show work contacts in personal profile | Allowed |
| |||||||
| |||||||||
| Cross-profile copy & paste | Not allowed |
| |||||||
| |||||||||
| Cross-profile data sharing | Refuse from business to personal profile |
| |||||||
| |||||||||
PasscodePasscode | |||||||||||||||||
| Caption | Value | Description | 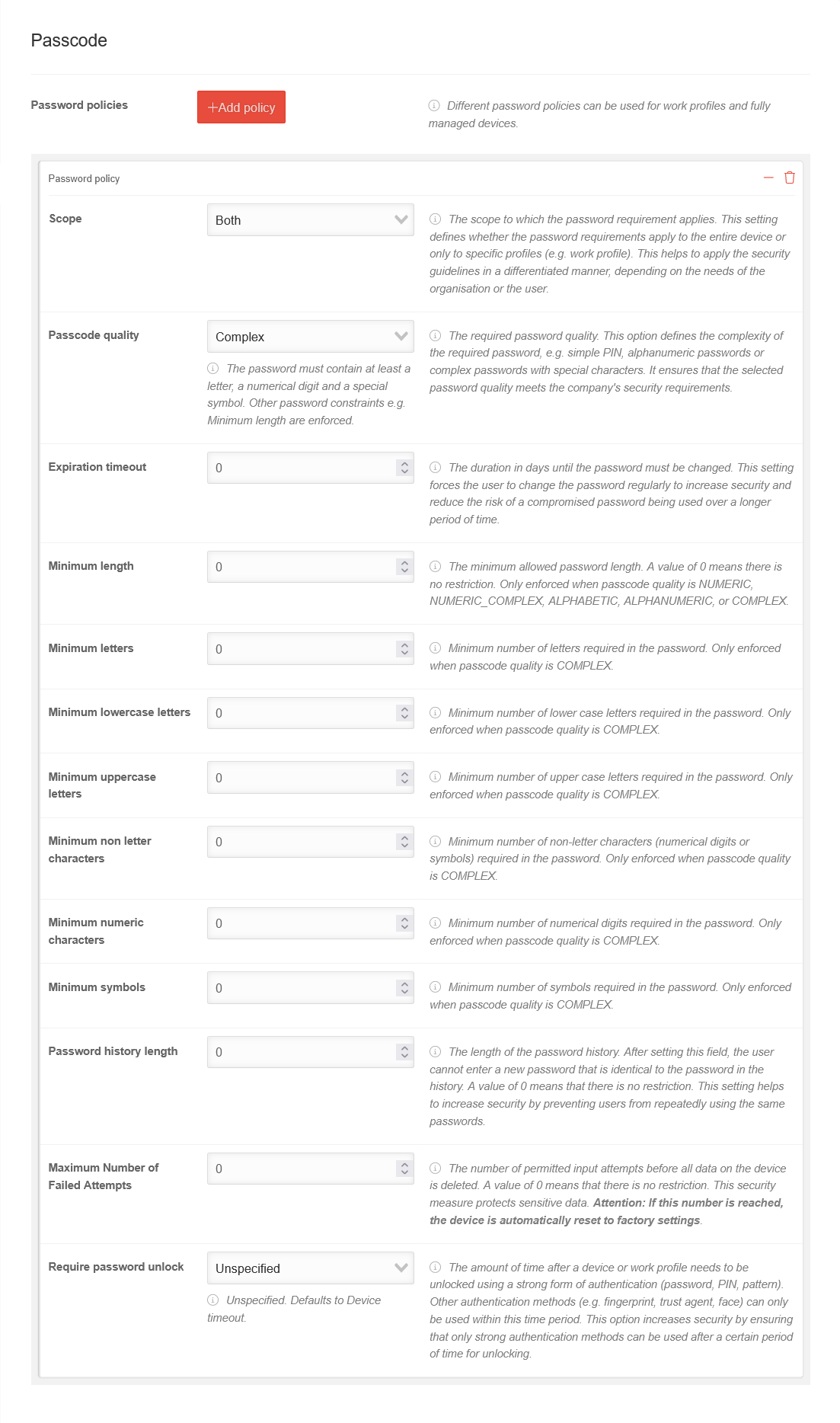 | ||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Password policies | Add policy | Password policies can be used for work profiles and fully managed devices. | |||||||||||||||
| Scope | The scope to which the password requirement applies. This setting defines whether the password requirements apply to the entire device or only to specific profiles (e.g. work profile). This helps to apply the security guidelines in a differentiated manner, depending on the needs of the organisation or the user. | ||||||||||||||||
| Device | The policy applies only to fully managed devices | ||||||||||||||||
| Work Profile | The policy only applies to work profiles | ||||||||||||||||
| Both | The policy applies to fully managed devices as well as devices with a work profile. | ||||||||||||||||
| Passcode quality |
Complex |
| |||||||||||||||
| |||||||||||||||||
New as of: 2.9 | |||||||||||||||||
| Expiration timeout | 0 | The duration in days until the password must be changed. This setting forces the user to change the password regularly to increase security and reduce the risk of a compromised password being used over a longer period of time. | |||||||||||||||
| Minimum length |
0 | The minimum allowed password length. A value of 0 means there is no restriction. Only enforced when Passcode quality is Numeric, Numeric (Complex), Alphabetic, Alphanumeric, or Complex. | |||||||||||||||
| Minimum letters | 0 | Minimum number of letters in the password Forced only if the Password quality is Complex. | |||||||||||||||
| Minimum lowercase letters | 0 | Minimum number of lowercase letters required in the password Forced only if the Password quality is Complex. | |||||||||||||||
| Minimum uppercase letters | 0 | Minimum number of capital letters in the password Forced only if the Password quality is Complex. | |||||||||||||||
| Minimum non letter characters | 0 | Minimum number of non-letters (numeric digits or symbols) required in the password. Forced only if the Password quality is Complex. | |||||||||||||||
| Minimum numeric characters | 0 | Minimum number of digits in the password Forced only if the Password quality is Complex. | |||||||||||||||
| Minimum symbols | 0 | Minimum number of symbols in the password Forced only if the Password quality is Complex. | |||||||||||||||
| Password history length | 0 | The length of the password history. After setting this field, the user won't be able to enter a new password that is the same as any password in the history. A value of 0 means there is no restriction. | |||||||||||||||
| Maximum failed attempts | 10 | The number of permitted input attempts before all data on the device is deleted. A value of 0 means that there is no restriction. This security measure protects sensitive data. notempty If this number is reached, the device is automatically reset to factory settings. | |||||||||||||||
| Password unlock required | The amount of time after a device or work profile is unlocked using a strong form of authentication (password, PIN, pattern) that can be unlocked using another authentication method (e.g., fingerprint, trusted agent, face). After the specified period, only strong authentication forms can be used to unlock the device or work profile. | ||||||||||||||||
| Not specified | Not specified. By default, the device-timeout is used. | ||||||||||||||||
| Device-timeout | The timeout is set to the default setting of the device. | ||||||||||||||||
| Daily | The timeout is 24 hours. | ||||||||||||||||
Passcode-Kombinationen
| |||||||||||||||||
| notempty New as of: 2.9
| |||||||||||||||||
| Geltungsbereich Gerät | Geltungsbereich Arbeitsprofil | Beispielkonfiguration Passcode-Qualität | |||||||||||||||
| Passcode quality: Komplexität & Qualität | Passcode quality: Komplexität & Qualität | Device: Hohe Komplexität & Simple Arbeitsprofil: Geringe Komplexität & Complex | |||||||||||||||
| Passcode quality: Komplexität & Qualität | Passcode quality: Qualität | Device: Hohe Komplexität & Simple Arbeitsprofil: Alphabetic | |||||||||||||||
| Passcode quality: Komplexität & Qualität | Passcode quality: Nicht vorhanden | Device: Hohe Komplexität & Simple | |||||||||||||||
| Passcode quality: Qualität | Passcode quality: Qualität | Device: Numeric Arbeitsprofil: Alphabetic | |||||||||||||||
| Passcode quality: Qualität | Passcode quality: Nicht vorhanden | Device: Numeric | |||||||||||||||
| Passcode quality: Nicht vorhanden | Passcode quality: Komplexität & Qualität | Arbeitsprofil: Hohe Komplexität | |||||||||||||||
| Passcode quality: Nicht vorhanden | Passcode quality: Qualität | Arbeitsprofil: Alphabetic | |||||||||||||||
| Passcode quality: Nicht vorhanden | Passcode quality: Nicht vorhanden | Nicht vorhanden | |||||||||||||||
| Folgende Kombinationen sind ebenfalls nicht erlaubt | |||||||||||||||||
| Geltungsbereich Gerät | Geltungsbereich Arbeitsprofil | Mögliche Lösung | |||||||||||||||
| Passcode quality: Komplexität | Passcode quality: Komplexität | Jeweils eine Passwortrichtlinie mit der Passcode-Qualität Qualitätsbasiert müssen angelegt werden | |||||||||||||||
| Passcode quality: Komplexität | Passcode quality: Nicht vorhanden | Eine Passwortrichtlinie mit der Passcode-Qualität Qualitätsbasiert muss angelegt werden | |||||||||||||||
| Passcode quality: Nicht vorhanden | Passcode quality: Komplexität | Eine Passwortrichtlinie mit der Passcode-Qualität Qualitätsbasiert muss angelegt werden | |||||||||||||||
| Passcode quality: Qualität | Passcode quality: Komplexität & Qualität | Passwortrichtlinien von Arbeitsprofilen dürfen nicht mit ausschließlich qualitätsbasierten Passwortrichtlinien von Geräteprofilen kombiniert werden
| |||||||||||||||
| Passcode quality: Qualität | Passcode quality: Komplexität | Eine Passwortrichtlinie mit der Passcode-Qualität Komplexitätsbasiert für das Geräteprofil und eine mit der Passcode-Qualität Qualitätsbasiert für das Arbeitsprofil müssen angelegt werden | |||||||||||||||
ApplicationsApplications | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Caption | Value | Description | 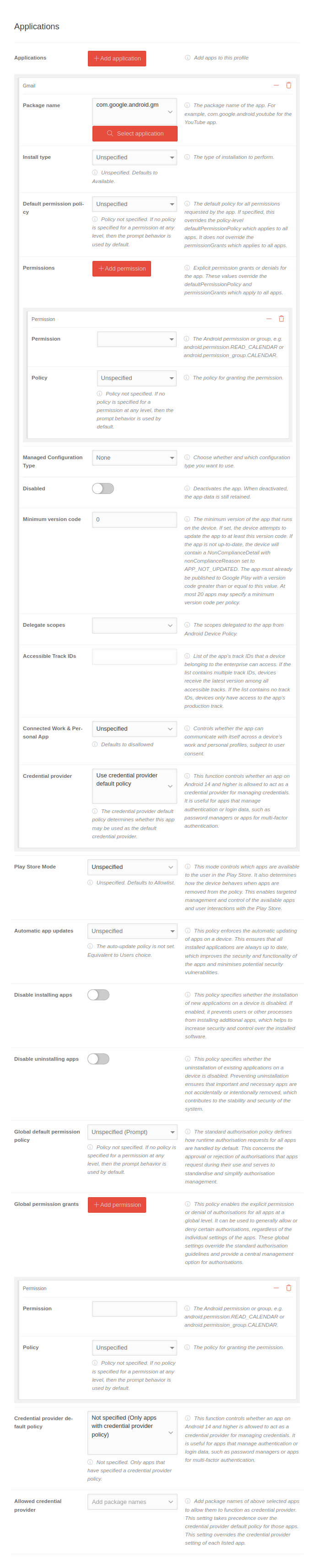 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Applications | Add applications | Adds apps to this profile notempty Apps on EMM-managed devices are configured within the profiles! | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Play Store Mode | Mit diesem Modus wird gesteuert, welche Apps dem Benutzer im Play Store zur Verfügung stehen. Zusätzlich bestimmt er, wie sich das Gerät verhält, wenn Apps aus der Richtlinie entfernt werden. Dies ermöglicht eine gezielte Verwaltung und Kontrolle der verfügbaren Anwendungen und der Benutzerinteraktionen mit dem Play Store. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Automatic App Updates | Always | The policy enforced on a device to automatically update apps depending on the network connection: Apps should also be updated on devices that rarely or never return to a wireless network. The volume of data usually has little effect with standard volume tariffs. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Disable installation of apps | Diese Richtlinie gibt an, ob die Installation von neuen Anwendungen auf einem Gerät deaktiviert ist. Wenn aktiviert, verhindert sie, dass Benutzer oder andere Prozesse zusätzliche Apps installieren können, was zur Erhöhung der Sicherheit und Kontrolle über die installierte Software beiträgt. notempty If activated , no installations or Updates are possible. Also not via the portal! | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Disable uninstalling apps | The user should not be able to uninstall any apps. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Global default authorization policy | Not specified (prompt) | The default authorization policy for runtime authorization requests. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Global permission granting | Add permission | Explicit permission or group grant or deny for all apps. These values override the Default permission policy. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Anmeldedatenanbieter-Standardrichtlinie | Not specified (Only apps with a login provider policy) | This feature determines whether an app on Android 14 and above is allowed to function as a login provider for managing login credentials. If it is relevant for apps that handle authentication or login data, such as password managers or multi-factor authentication apps. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Erlaubte Anmeldedaten-Anbieter notempty New as of: 2.12 |
Paketnamen hinzufügen | Füge Paketnamen der oben ausgewählten Apps hinzu, um zu erlauben, dass diese als Anmeldeanbieter fungieren dürfen. Apps priorieseren diese Einstellung über der Anmeldedaten-Anbieter-Richtlinie. Diese Einstellung überschreibt die Anmeldedatenanbieter-Einstellung der einzelnen Apps. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Notes on using login providers | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Option | Value | Description | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Anmeldedatenanbieter | Anmeldedatenanbieter | Diese App kann (z.B. als Passwort-Manager) genutzt werden | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Anmeldedatenanbieter-Standardrichtlinie benutzen | Auswahlmöglichkeit s.u. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Anmeldedatenanbieter-Standardrichtlinie Nur wenn App nicht selbst als Anbieter fungiert! |
Nicht spezifiziert (Nur Apps mit Anmeldedatenanbieter-Richtlinie) | Die App kann nicht verwendet werden | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Nur Apps mit Anmeldedatenanbieter-Richtlinie | Die App kann nicht verwendet werden | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Nur Apps mit Anmeldedatenanbieter-Richtlinie oder OEM-Standardanmeldedatenanbieter | Sowohl die ausgewählte App als auch von Google als Anmeldedatenanbieter klassifizierte Apps können genutzt werden | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Verwalteter Konfigurationstyp
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Managed configuration
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| The format for the configuration depends on the ManagedProperty values supported by the app. Each field name in the managed configuration must match the key field of the managed property. The field value must be compatible with the ManagedProperty type. Bei jeder Konfiguration wird eine bestimmte Schaltfläche angezeigt:
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Caption | Value | Description | 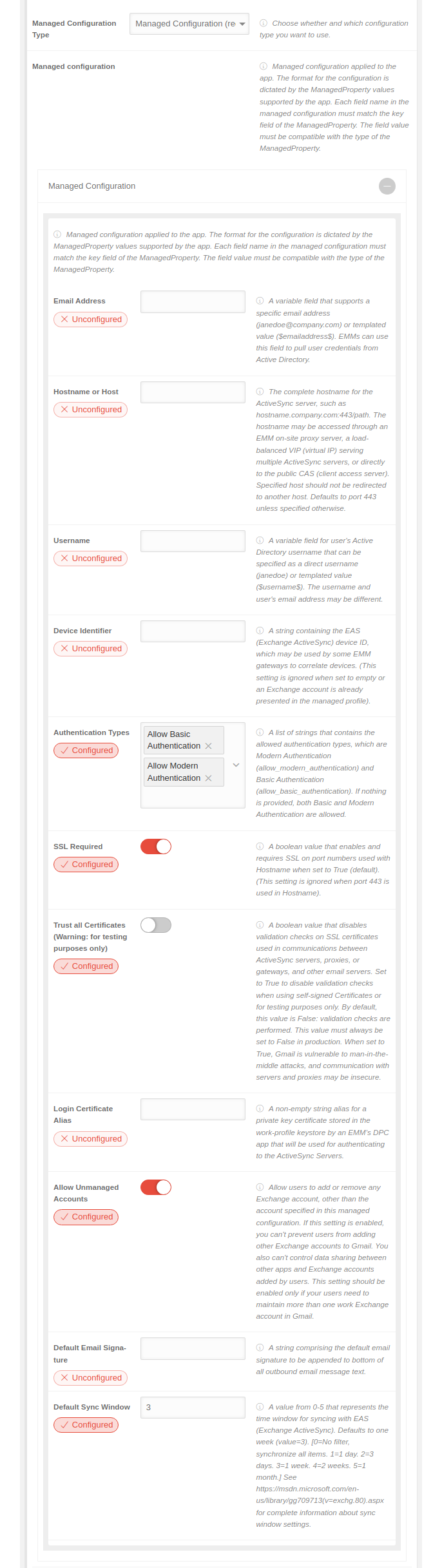 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| E-Mail-Adresse |
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Hostname oder Host |
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Nutzername |
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Geräte-ID |
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Authentifizierungstypen | Basisauthentifizierung zulassen Moderne Authentifizierung zulassen |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| SSL erforderlich |
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Allen Zertifikaten vertrauen (Achtung: nur für Testzwecke) |
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Alias für Anmeldezertifikat |
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Nicht verwaltete Konten zulassen |
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Standard-E-Mail-Signatur |
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Standardsynchronisierungsfenster | 3 |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Managed Configuration Template
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Caption | Value | Description | 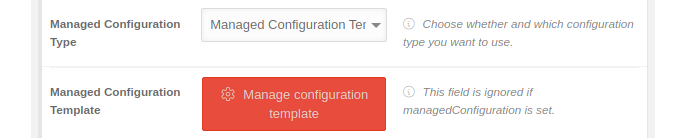 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Managed Configuration Template | Manage configuration template | This field is ignored if the managed configuration is set. Calls up a template from the app manufacturer in which various parameters can be transferred to the app, depending on what the manufacturer specifies. These can be fixed parameters and variables in email apps: | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Example for Gmail app: | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Email Address | $emailaddress$ | Variable | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Hostname or Host | m.google.com | Fixed parameter | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Username | $emailaddress$ | Variable (for Gmail accounts the username is the email address.) With other accounts / apps the variable $username$ can be used here. notempty New as of: 2.8 For a correct function, in the tab General the button Profile is a template must be activated and the users must be selected! The values are taken from the user settings of the user to whom the respective device is assigned
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
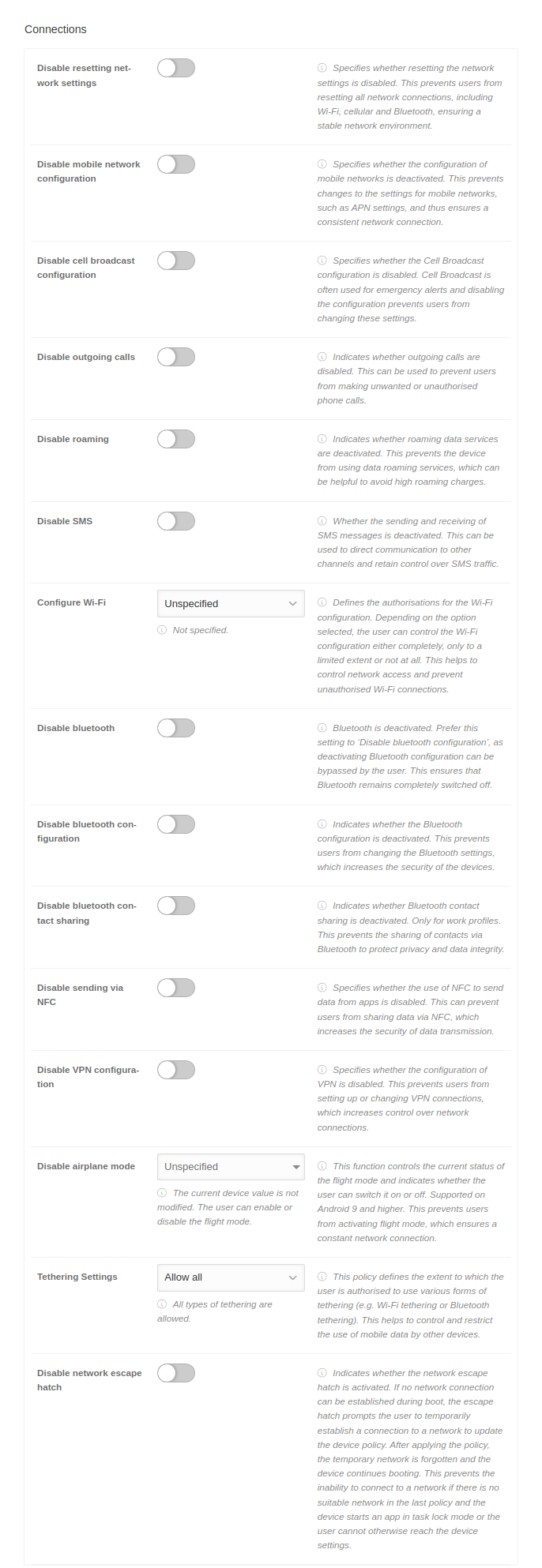
NetworksNetworks | ||||||
| Caption | Value | Description | Datei:MS 2.11 Android Profile Netzwerke-en.png | |||
|---|---|---|---|---|---|---|
| Always on VPN | ||||||
| Enable "Always-On-VPN" |
| |||||
| Package name | de.securepoint.ms.agent | The package name of the VPN app. | ||||
| Lockdown enabled |
| |||||
| Recommended global proxy | ||||||
| Activate the global proxy |
| |||||
| Host | Hostname |
| ||||
| Port | Port number | The network port of the direct proxy that is used together with the host to route the data traffic | ||||
| Excluded host | Hostnames |
| ||||
| PAC URI | URI |
| ||||
| Network configuration | ||||||
| Network configurations | Add configuration | Configuring Access Profiles for WiFi Networks | ||||
| Name | ttt-point Headquarters | The name of the configuration gives the specific network configuration a unique and meaningful identifier | ||||
| Type | WiFi | The configuration type is predefined | ||||
| Wifi | ||||||
| SSID | ttt-point-headquarter-WIFI |
| ||||
| Security |
WPA-EAP |
| ||||
| Passwort Nur bei WEP-PSK und WPA-PSK |
•••••••••• | Passwort für die Authentifizierung beim inneren Protokoll Even if it sounds trivial: WIFI.MyCompany.123 or Location.HouseNumber are no secure passwords! Also 1234 and abcd or qwerty are not' really secure passwords! | ||||
| EAP notempty New as of: 2.11 Nur bei WPA-EAP und WEP-8021X | ||||||
| Äußeres Protokoll | EAP-TLS |
| ||||
| Inneres Protokoll Nur bei EAP-TTLS und PEAP |
MSCHAPv2 |
| ||||
| Identität | Identität | Identität für die Authentifizierung beim inneren Protokoll | ||||
| Passwort Nur bei EAP-TTLS und PEAP |
Passwort | Passwort für die Authentifizierung beim inneren Protokoll | ||||
| Anonyme Identität | Anonyme Identität | Identität für die Authentifizierung beim äußeren Protokoll | ||||
| Valide Server-Domains | Valide Server-Domains | Eine Liste an Domains, welche zur Validierung des Authentifizierungs-Servers dient | ||||
| Client-Zertifikat Nur bei EAP-TLS |
Das Client-Zertifikat | |||||
| Valide CAs | Liste an CAs | Eine Liste an CAs, welche vom Client zur Validierung des Server-Zertifikats verwendet werden | ||||
| Hidden SSID |
| |||||
| Autoconnect | The device should automatically connect to the network | |||||
Status reportingStatus reporting | ||||||
| Caption | Value | Description | 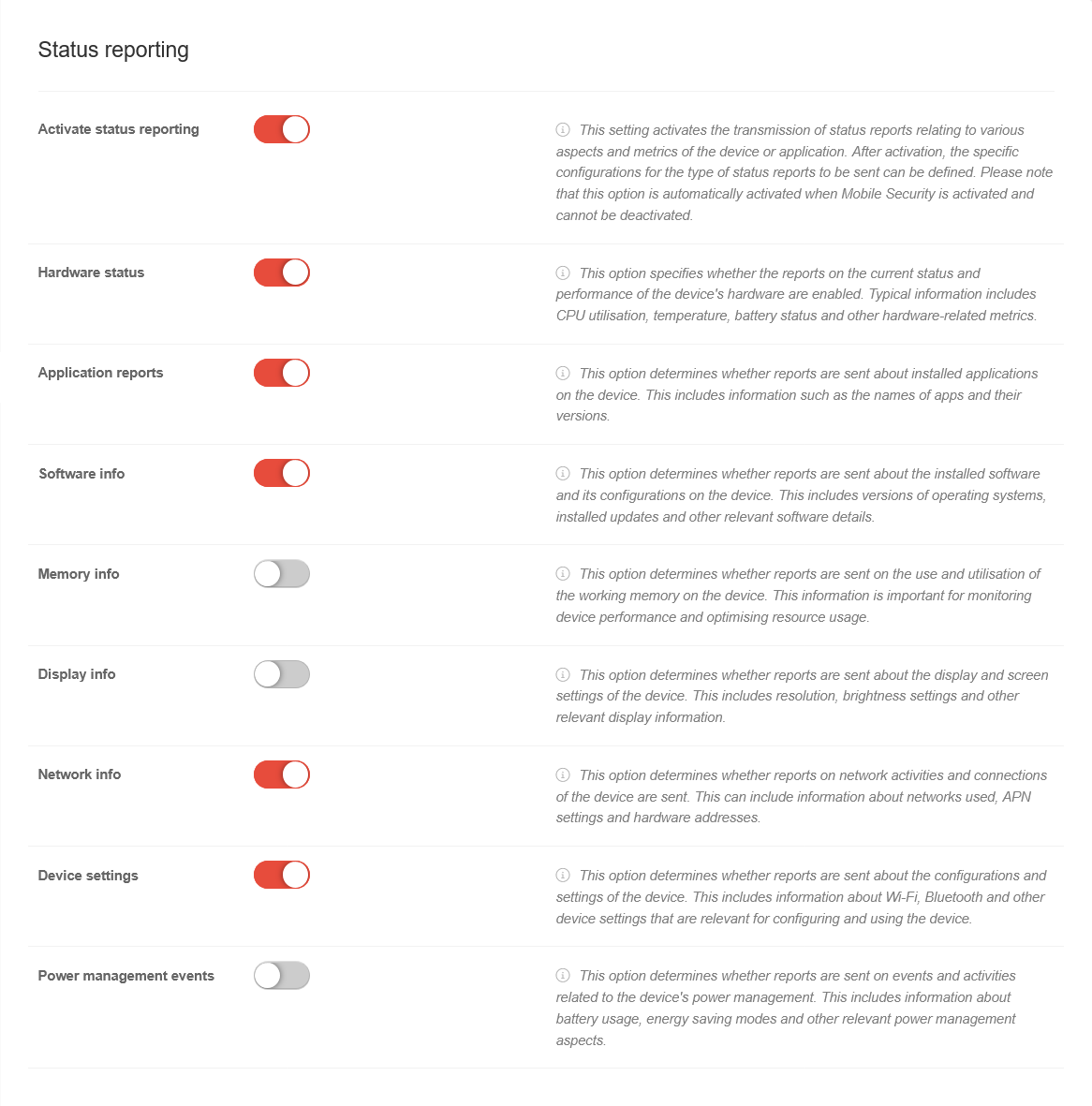 | |||
|---|---|---|---|---|---|---|
| Activate the status message |
| |||||
| Hardwarestatus |
| |||||
| Application Reports |
| |||||
| Software information |
| |||||
| Working memory information |
| |||||
| Display information |
| |||||
| Network information |
| |||||
| Device Settings |
| |||||
| Power Management Events |
| |||||
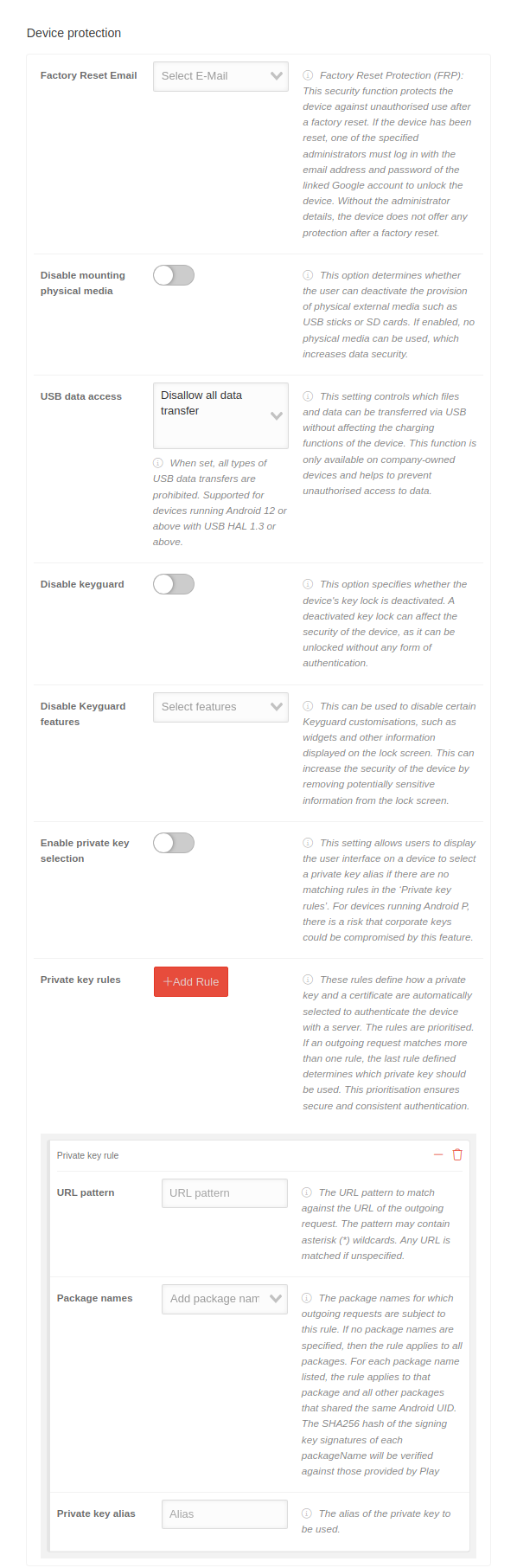
ComplianceCompliance | |||||||
| Rules can be defined for when the telephone or work profile is locked and when it is deleted (factory reset). The user is prompted to activate the selected policy on the device. Otherwise, the device / work profile will be blocked or set to factory defaults / deleted. | |||||||
| Caption | Value | Description | 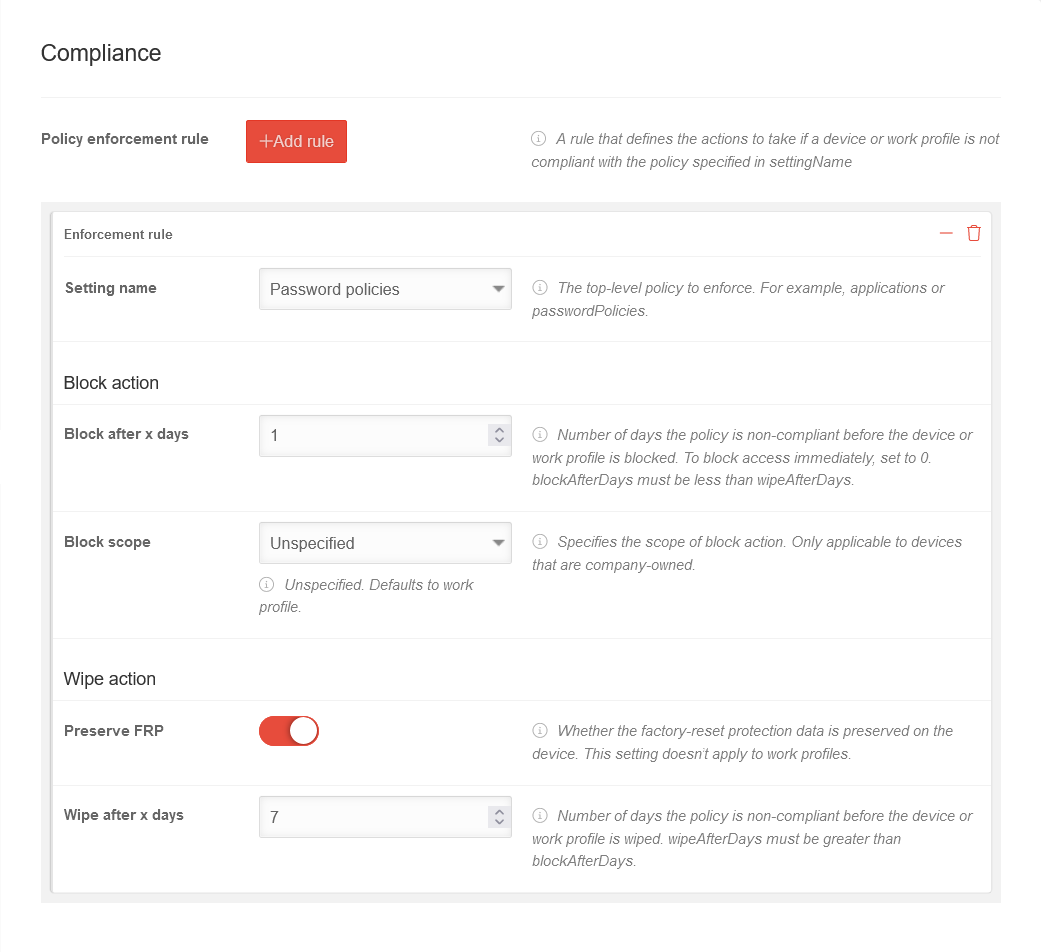 | ||||
|---|---|---|---|---|---|---|---|
| Rules for enforcing the profile | Add rule | A rule that defines the actions to be taken when a device or a work profile does not comply with the policy specified in "Setting name". | |||||
| Preference name | Password policy | The password policies must be applied to the phone. | |||||
| Block action | |||||||
| Block after x days | 1 | Number of days on which the policy is not compliant before the device or work profile is blocked. To block access immediately, the value is set to 0. | |||||
| Block scope | Not specified | Specifies the scope of the blocking action. Applies only to devices owned by the company. | |||||
| |||||||
| Delete | |||||||
| Get factory reset protection |
| ||||||
| Wipe after x days | 7 |
| |||||
Security / VPNSecurity / VPN | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| notempty The Security tab is only available if a Mobile Security license is present. EMM licenses do not have VPN functionality that enables these security functions. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Caption | Value | Description | 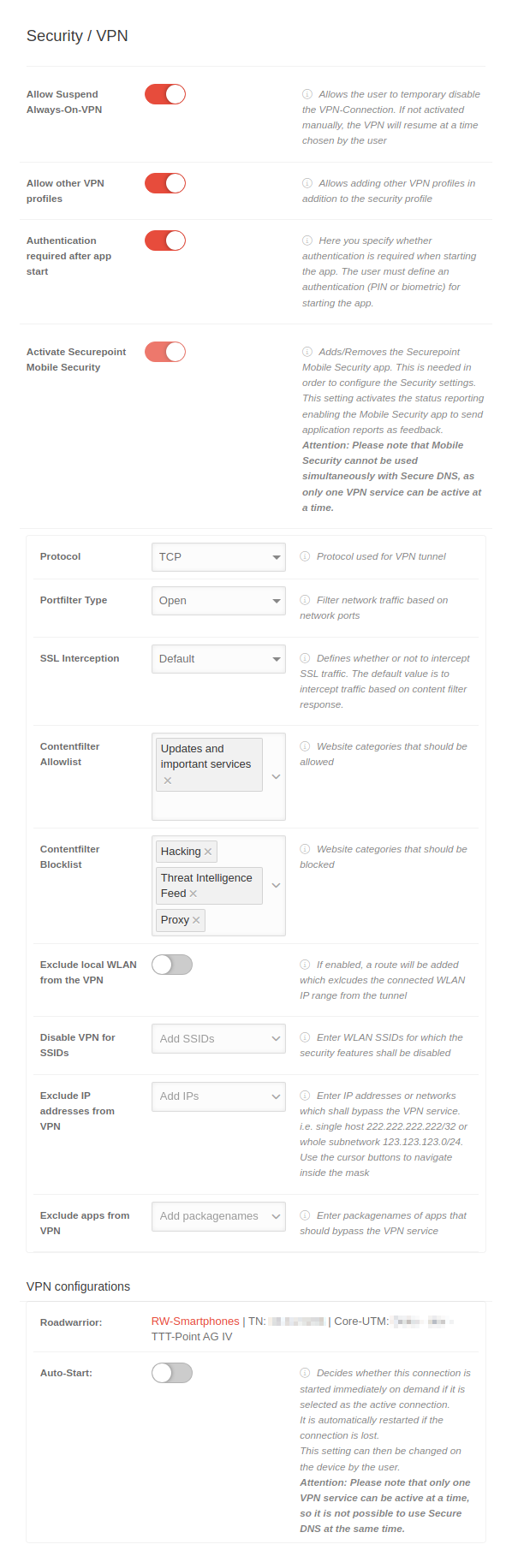 | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Allow Suspend Always-On-VPN |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Allow other VPN profiles | When activated , the addition of other VPN profiles, in addition to the security profile, is permitted | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Authentication required after app start |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Activate Securepoint Mobile Security |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Protocol | TCP | The protocol TCP or UDP used for the VPN tunnel | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Portfilter Type | Open | Filter network traffic based on network ports. Closed Open Selection | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Port filter rule selection Appears when Port filter type Selection is selected |
Communication VPN | Specify which port collections are open for network traffic
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| SSL-Interception | Default | SSL traffic from web pages listed in the content filter allowlist is not intercepted, other pages are checked using SSL interception. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Content-Filter Allowlist | Updates and important services | Click box: Web pages that are to be added to a allowlist. Possible entries: Contentfilter | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Content-Filter Blocklist | HackingProxyThreat Intelligence Feed | Click box: Websites that are to be added to a blocklist. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Exclude local WLAN from VPN | If enabled , a route is added that excludes the local WLAN IP range from the tunnel | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Disable VPN for SSIDs | Add SSIDs | Enter WiFi SSIDs for which the security features shall be disabled. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Exclude IP addresses from VPN | Add IPs | Enter IP addresses or networks for which the security functions are to be bypassed, i.e. the individual host 222.222.222/32 or the entire subnet 123.123.123.0/24. Use the cursor keys to navigate within the mask | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Exclude apps from VPN | Add package name | Enter the package names of the apps that are to bypass the VPN service | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
VPN Configurations | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Displays a list of all Roadwarrior connections that are connected to this profile. New connections can be created via . For more information, see the following Wiki article. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Roadwarrior: |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Autostart: |
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Cloud Shield
| Caption | Value | Description | 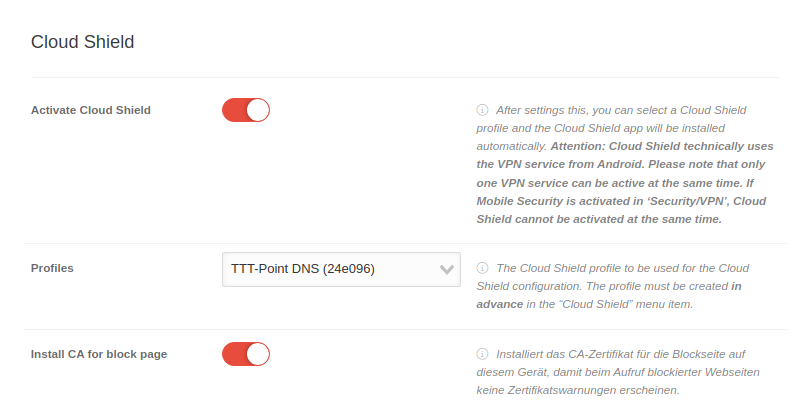 | |
|---|---|---|---|---|
| Activate Cloud Shield | After enabling a Cloud Shield Profile can be selected, and the Cloud Shield App for Android will be installed automatically. In the
| |||
| Profile |
Select Profile | The Cloud Shield profile to be used for the Cloud Shield configuration.
| ||
| Install CA for block page | If is activated, the CA certificate for the block page is installed on the device so that certificate warnings are no longer displayed if a page is blocked. In the
| |||
LocalizeLocalize | ||||||
| Caption | Value | Description | 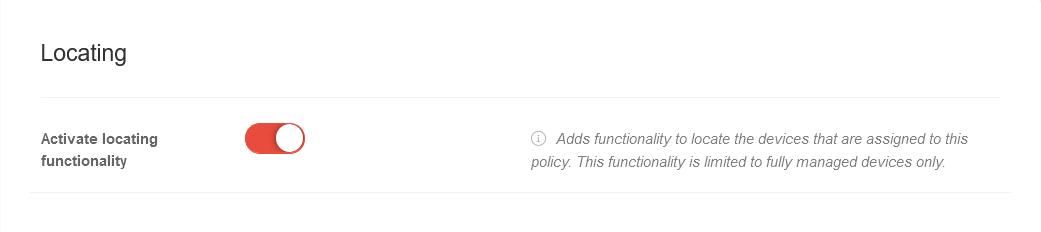 | |||
|---|---|---|---|---|---|---|
| Enable localization function | Adds functionality to find the devices assigned to this policy. This functionality is limited to fully managed devices only. | |||||