iOS Profile Configuration in the Menu Network
Last adaptation to the version: 2.7 (07.2025)
New:
- Changed menu navigation
This article refers to a Beta version
Partial configuration for profiles in the Mobile Security Portal.
Further information is displayed here:
- MS/deployment/user (← links)
- MS (← links)
- MS/deployment/profile-AppleTV (transclusion) (← links)
- MS/deployment/profile-Device (transclusion) (← links)
- MS/deployment/profile-User (transclusion) (← links)
Networks
Networks
In this section, access profiles for WiFi networks can be configured and pushed to the device.
Network configuration | |||
| Caption | Value | Description | 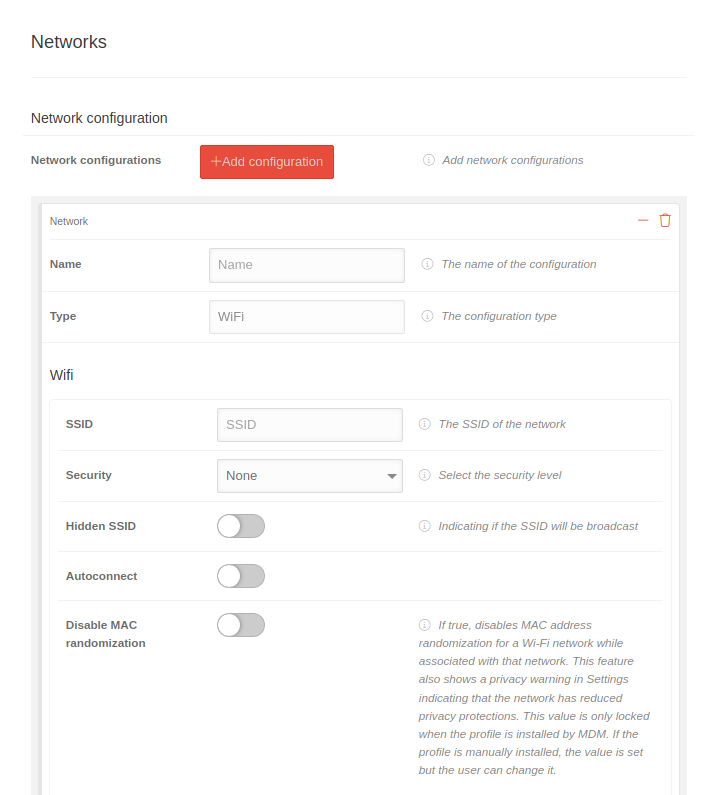 |
|---|---|---|---|
| Network configurations | Add configuration | Network configuration | |
| Name | Name | Name of the configuration | |
| Type | WiFi | Configuration type (WiFi predefined) | |
Wifi | |||
| SSID | SSID | The SSID of the network | |
| Security | Security level of the network key | ||
| None | No security | ||
| WEP-PSK | Insecure | ||
| WPA-PSK | Secure | ||
| Password | Password | Password of the account for the server | |
| Hidden SSID | When activated , the network's SSID is hidden | ||
| Autoconnect | When activated , the device automatically connects to the network | ||
| Deactivate MAC randomisation | When activated , the devices always identify themselves with the same MAC address in a network.
Cannot be changed by the user. This function also displays a data protection warning in the settings that the network has limited data protection. This value is only locked if the profile is installed via an MDM. If the value is set with the Apple Configurator, for example, it can be changed by the user. | ||
EAP-Client / WPA2 Enterprise
| |||
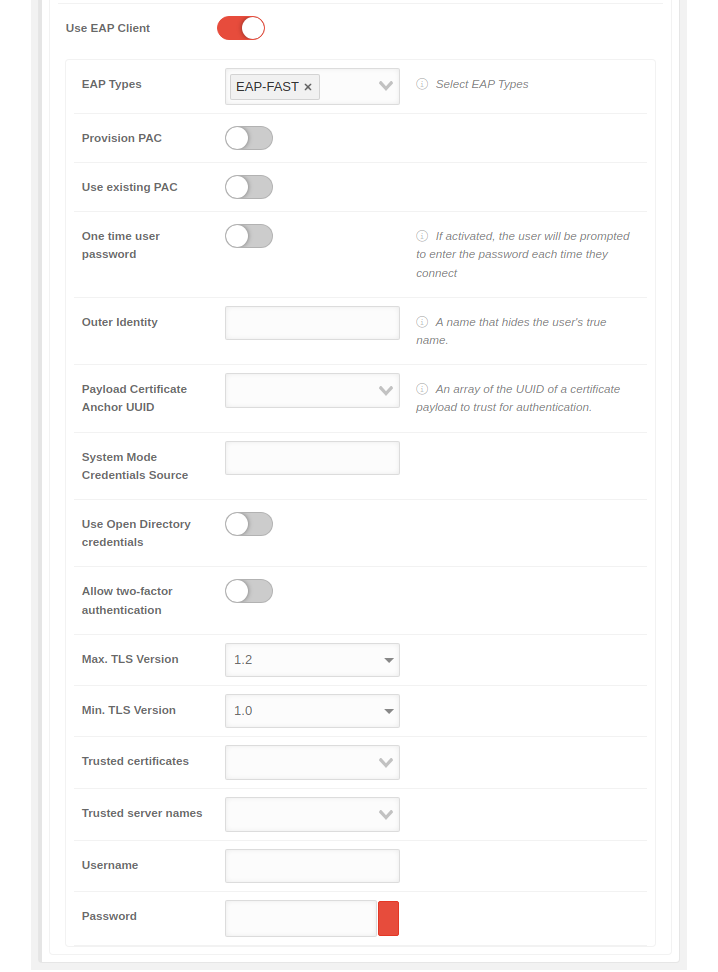
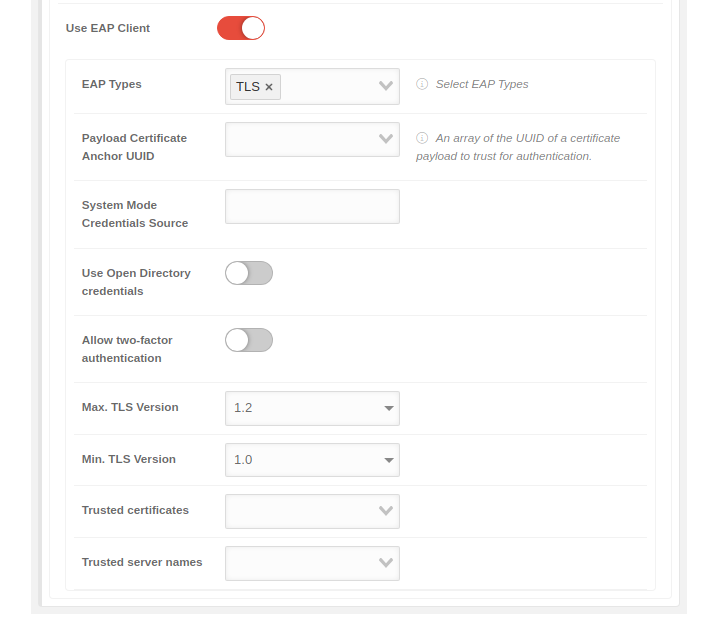
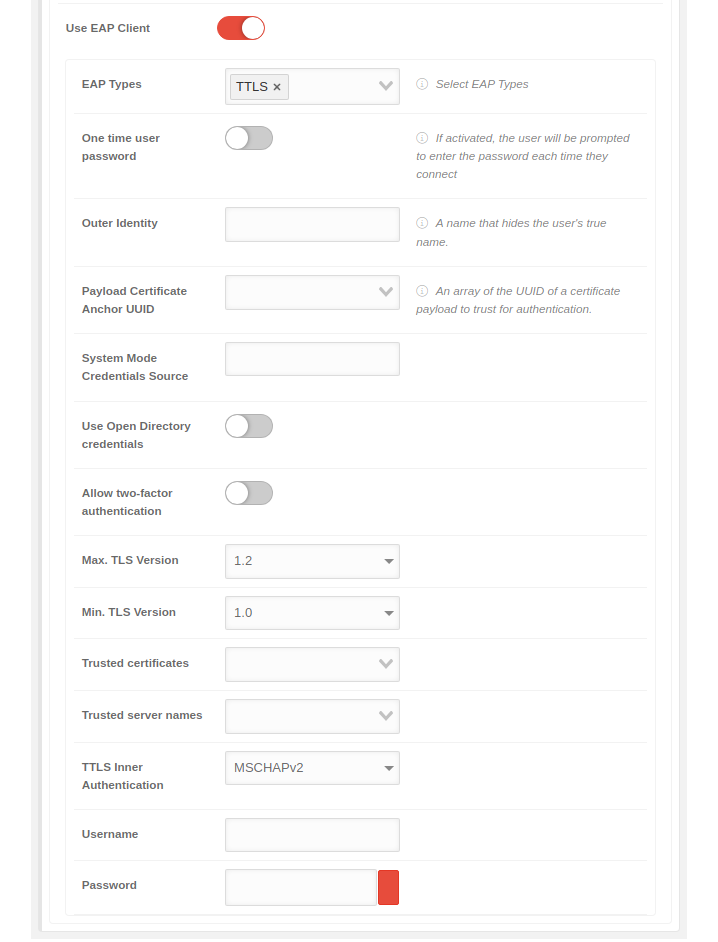
| Use EAP Client | When activated , the EAP client, the WPA2 Enterprise, can be used | 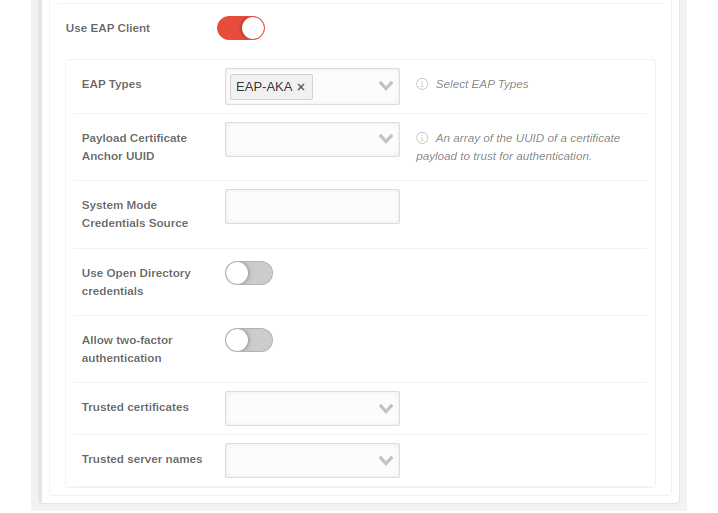 | |
| EAP Types | Select EAP Types | The EAP type is selected. Several types can be selected. The choices are: | |
| Payload Certificate Anchor UUID |
The certificate that is handed to the server by the client as authentication when logging on to the WLAN. Apple: An array of the UUID of a certificate payload to trust for authentication notempty New as of: 2.7 | ||
| System Mode Credentials Source | The server for the system mode credentials | ||
| Use Open Directory credentials | When activated logging in through Open Directory is possible | ||
| Allow two-factor authentication | When activated , two-factor authentication is possible | ||
| Trusted certificates |
The certificates that are to be trusted are entered. These certificates must first be stored in the notempty New as of: 2.7 | ||
| Trusted server names | The names of the servers that are to be trusted are entered | ||
Global HTTP proxy | |||
| A Global HTTP proxy can be configured, for example, if devices are permanently on the same network and a local proxy is to be used on the device. Especially recommended for devices that only have an MDM license. These can then use, for example, the protection functions of a Securepoint UTM with web filter, etc. |
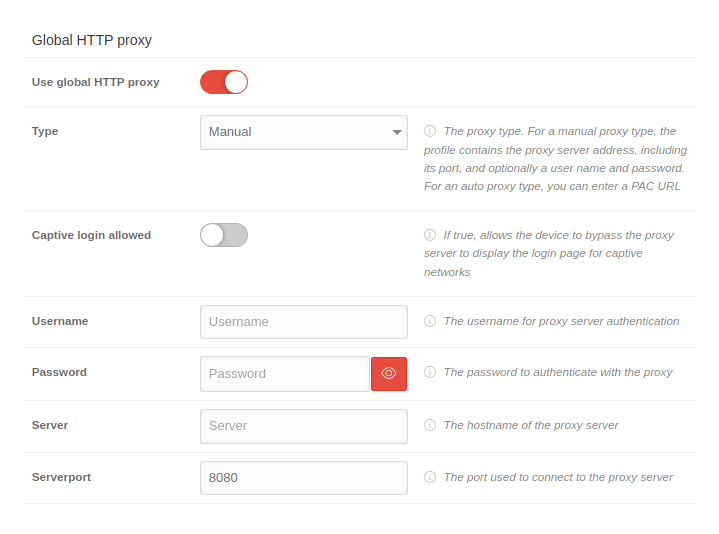 | ||
| Use global HTTP proxy | When activated the global HTTP proxy is used | ||
| Type | Manual Automatic |
For a manual proxy type, the profile contains the proxy server address, including the port, and optionally a user name and password. For an auto proxy type, you can enter a PAC URL. | |
| Allow captive login | |||
| Username | Username | The username used to authenticate to the proxy server | |
| Password | Password | The password used for authentication to the proxy server | |
| Server | Server | The network address of the proxy server | |
| Server port | 8080 | The port used to connect to the proxy server | |