Last adaptation to the version: 12.6.0
- Updated to Redesign of the webinterface
Introduction
This guide explains in which case authentication exceptions are used and how they can be stored in the proxy.
What are authentication exceptions used for?
Authentication exceptions are often required in connection with virus scanners or other programs that do not support NTLM authentication. In order for these programs to be able to communicate with the Internet despite this, it must be defined in the proxy that the requested URL can be called without previous authentication.
Example
Exception for subdomains
UTMuser@firewall.name.fqdnApplications 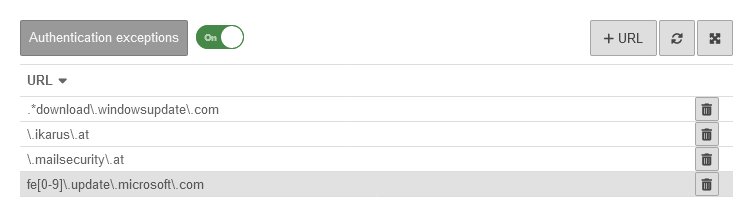 Authentication exceptions
To exclude a website from the authentication exceptions, the URL must be entered as a regex in the list.
Authentication exceptions
To exclude a website from the authentication exceptions, the URL must be entered as a regex in the list.
The default entries \.ikarus\.at and \.mailsecurity\.at are required for our solution Securepoint Antivirus Pro.
| Regex | Exception from the authentication for |
|---|---|
| .*download\.windowsupdate\.com | all subdomains of windowsupdate.com ending in download all subdomains of download.windowsupdate.com |
| updateserver\.anyideas\.de | One dedicated address |
| \.update\.microsoft\.com | all subdomains of a website |
| fe[0-9]\.update\.microsoft\.com | fe0.update.microsoft.com fe1.update.microsoft.com fe2.update.microsoft.com . . fe9.update.microsoft.com |
Further notes on regex notation can be found in this Wiki article.
The default entries are available for a new UTM installation from v12.5. If an existing UTM before v12.5 is updated, the entries remain as .*\.ikarus\.at and .*\.mailsecurity\.at
Examples of exceptions for Windows update servers
Further examples for setting up authentication exceptions, virus scanners, web filters and SSL interception regarding Windows Updates can be found in the Knowledge Base article Windows Updates with HTTP-Proxy and Web Filter



