In dieser Seite werden die Variablen für unterschiedliche Sprachen definiert.
Diese Seite wird auf folgenden Seiten eingebunden
{{var | Nameserver der Firewall festlegen--desc
| Menü
Area
Servereinstellungen Abschnitt {{b|
DNS-Server
.
| Menu
Area
Server Settings section
DNS-Server
.
Configuration of a name server with DNS forwarding
Last adaptation to the version: 14.1.0 (08.2025)
New:
- If there is a Cloud Shield configuration via the USC, no DNS forwarding can be configured locally
This article refers to a Beta version
DNS Forwarding
A DNS forwarding is used to forward all DNS requests made to the firewall's name server to another IP.
|
|
If a Cloud Shield configuration is available via the USP (Unified Security Portal), a ‘’'configuration of ‘'DNS Forwarding’ on the UTM itself is not possible'
- The settings from the USP are displayed, but can only be changed here
- The section on the UTM is deactivated
|
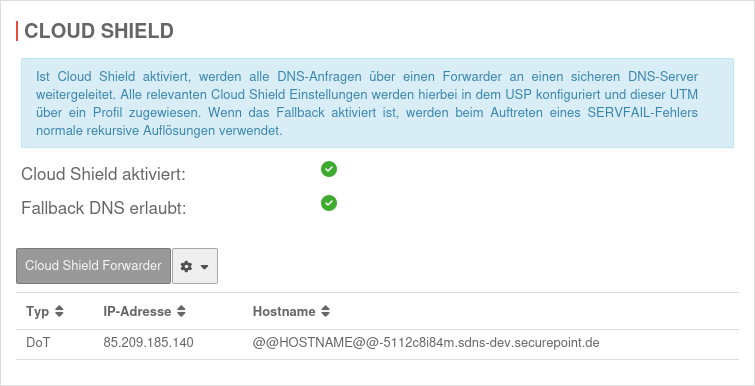 Cloud Shield configuration available in the USP Cloud Shield configuration available in the USP
|
|
|
|
|
Add DNS Forwarding Add DNS Forwarding Menu Area DNS Forwarding button + Add DNS Forwarding
|
| Caption |
Value |
Description
|
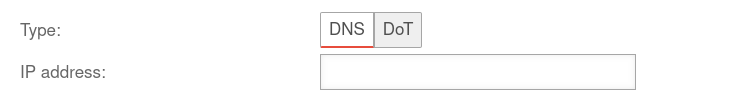 Creating a DNS Forwarding Creating a DNS Forwarding
|
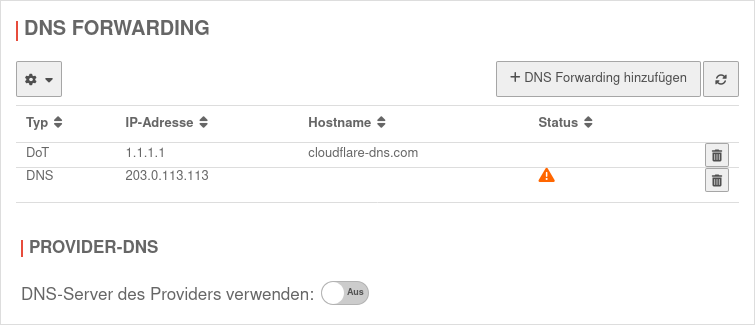
| Type: |
DNSDoT |
DNS: classic unencrypted DNS-resolution
|
| IP address: |
203.0.113.113 |
IP address of a DNS server to which the DNS requests should be forwarded.
|
|
|
| notempty
|
| Type: |
DNSDoT |
DoT: DNS over TLS DNS queries are encrypted with TLS
|
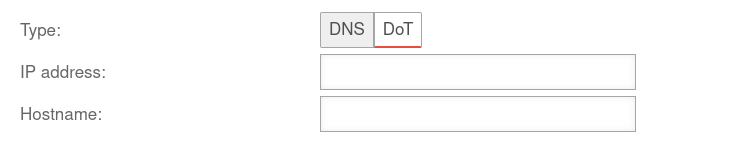 DNS over TLS notempty DNS over TLS notempty
|
| IP address: |
1.1.1.1
Example value |
IP address of a DNS server to which the DNS requests should be forwarded.
|
| Hostname |
cloudflare-dns.com
Example value |
The hostname is required fot thr verification of the TLS certificate
|
| |
Saves the entry
|
|
|
Provider-DNS Provider-DNS |
| Use the provider's DNS server |
Off |
When On is activated, the DNS server of the internet provider is used
|
|
If a TLS-Forwarder (DoT) is configured, DNS Forwarder will not be used
|
Domain forwarding through a VPN tunnel
Sometimes it is necessary to forward internal domain requests to a remote name server located in a VPN.
It should be noted here that, by default, all direct requests addressed to external name servers are sent from the firewall with the external IP. However, a public IP is not routed into a VPN tunnel.
Set the name server of the firewall
| Caption |
Value |
Description
|
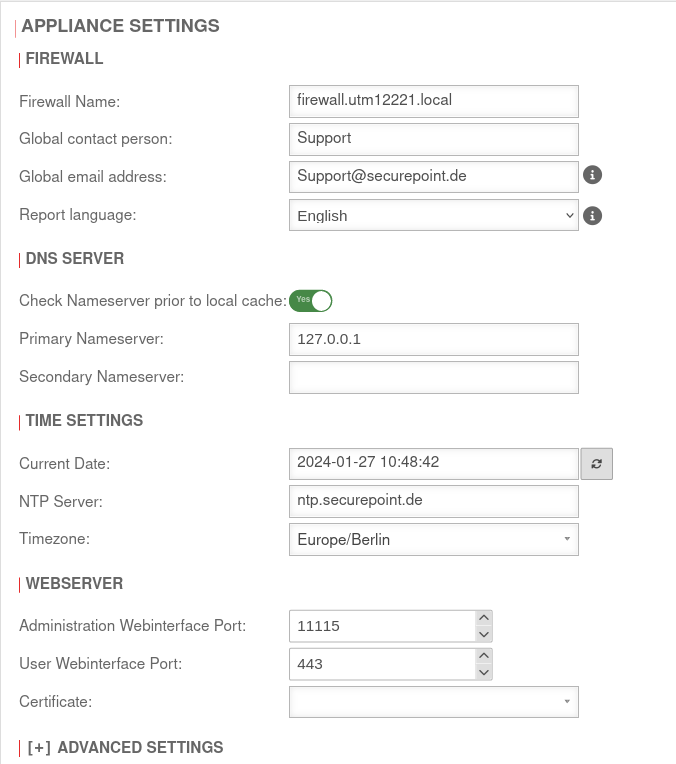 Name server IP Name server IP
|
| Check name server before local cache: |
Yes |
Should be enabled
|
| Primary name server: |
127.0.0.1 |
The IP of the UTM itself (localhost=127.0.0.1)
|
| Secondary name server: |
|
Can remain empty or designate another DNS in the VPN
|
| |
Saves the entry
|
|
|
Create relay
notemptyFor this example, an IPSec connection was used. For SSL-VPN, the setup is done in the same way.
Menu Area Zones button + Add Relay-Zone.
| Caption |
Value |
Description
|
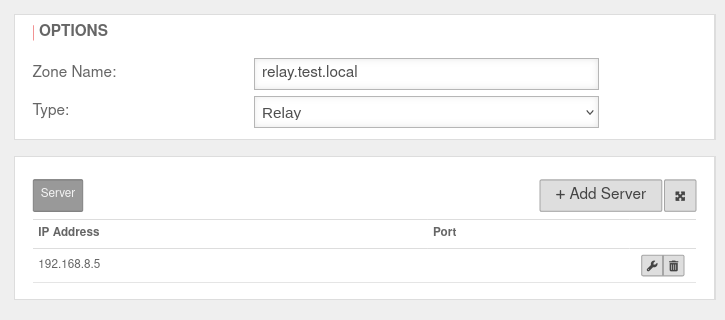 Creating the relay zone Creating the relay zone
|
| Zone name: |
relay.test.local |
Zone name of the desired domain
|
| Type:: |
Relay |
Select this type
|
| IP address: |
192.168.8.5 |
Click on Add server and in the IP address field the address of the remote name server is entered
Edit the entry
trash Delete the entry
|
| |
Saves the entry
|
|
|
Create network object
Menu button + Add Object. A network object must be created for the IPSec network.
| Caption |
Value |
Description
|
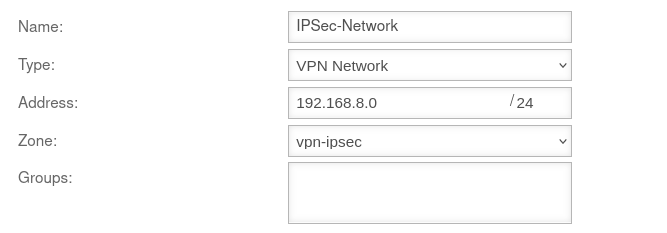 Network object Network object
|
| Name: |
IPSec-Network |
Choose unique name
|
| Type:: |
VPN network |
Select this type
|
| Address: |
192.168.8.0/24 |
The IP address corresponds to that of the IPSec network
|
| Zone: |
vpn-ipsec |
Suitable zone must be selected
|
| |
Saves the entry
|
|
|
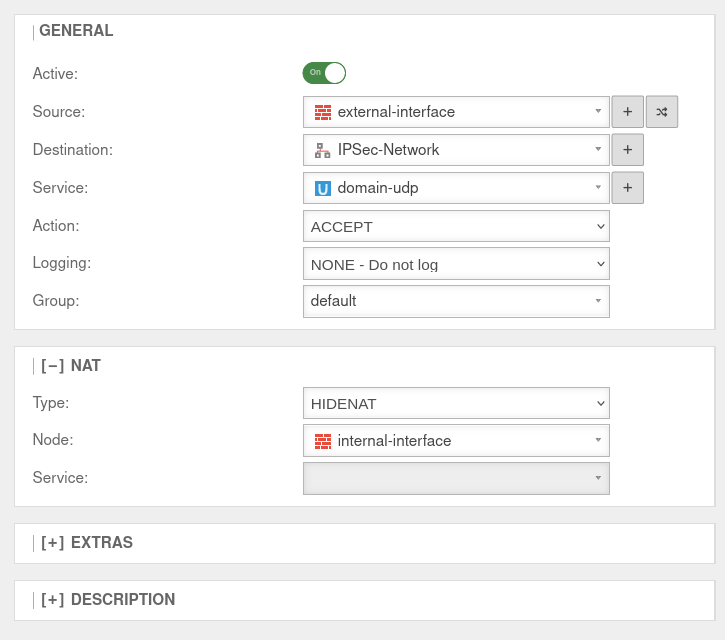
Add Rule
In the last step, a firewall rule with a Hide NAT must be created. This causes the DNS forwarding to also go into the tunnel, and not directly into the Internet.
Menu button + Add Rule.
Safe Search with external DHCP server
If an external DHCP server is used, the active web filter Safe Search often does not work for search engines, especially Google, when searching for images.
In order for this web filter to take effect there as well, the following forward zones must be set up for all ccTLDs (see https://www.google.com/supported_domains : www.google.de, www.google.ch, ...).
Menu button + Add Forward Zone.
| Caption |
Value
|
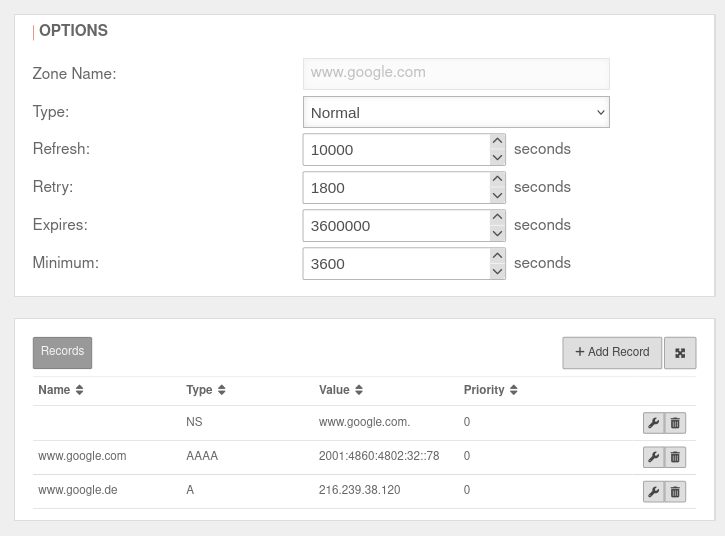 The forward zone set up for www.google.com The forward zone set up for www.google.com
|
| Zone name: |
www.google.com
|
| Name server hostname: |
localhost
|
| Name server IP address: |
|
In the Name server window, click in the www.google.de zone.
In the Edit Zone window click Add entry.
|
| Name: |
www.google.com
|
| Type:: |
A
|
| Value: |
216.239.38.120
|
| Save and click again on Add entry.
|
| Name: |
www.google.com
|
| Type:: |
AAAA
|
| Value: |
2001:4860:4802:32::78
|
| |
Saves the entry
|
|
|