New article with version: 12.7.0
General configuration
Radius with 2FA
With 2-factor authentication, it may be necessary to increase the timeout.
To adjust this, the Extc variable GLOB_RADIUS_TIMEOUT must be adjusted. This is possible via the Admin Interface or the CLI.
Admin Interface
UTMuser@firewall.name.fqdnExtras 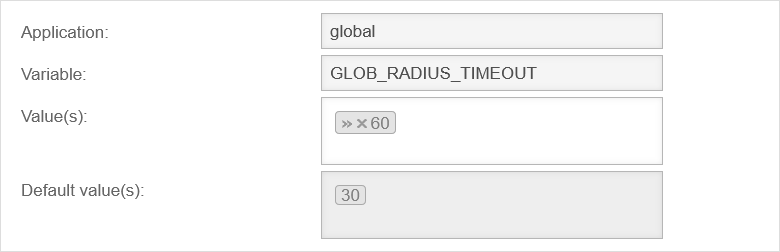
In the admin interface, the advanced settings must first be displayed with Ctrl + Alt + A.
The variable GLOB_RADIUS_TIMEOUT can then be adjusted under Area Extc-Variables. To ensure smooth use, it is recommended to set this to 60(seconds).
CLI
The following command can be used to adjust the variable GLOB_RADIUS_TIMEOUT using the CLI:
extc global set variable "GLOB_RADIUS_TIMEOUT" value 60
notempty
spcli extc global get | grep RADIUS
A successful output could look like this:
GLOB_RADIUS_SERVER |192.168.1.1
GLOB_RADIUS_SERVER_KEY |insecure
GLOB_RADIUS_TIMEOUT |60



