Last adaptation to the version: 12.6.0
- Updated to Redesign of the webinterface
Introduction
Firewall rules always apply to network objects.
To apply firewall rules to members of an SSL VPN group, they are created under as individual hosts or networks with IP addresses as Network Objects and then merged into network groups .
Alternatively, it is possible to automatically create network objects based on user groups and thus use identity-based port filtering rules.
If users are authenticated through an AD or LDAP, the administrative effort is significantly reduced.
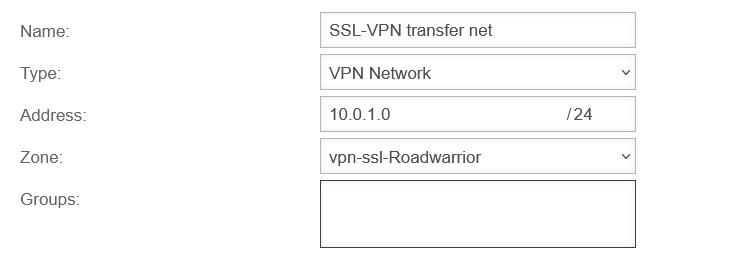
For the internal services (such as DNS), the transfer network must be created and the packet filter rules written from there.
Configuration on the UTM
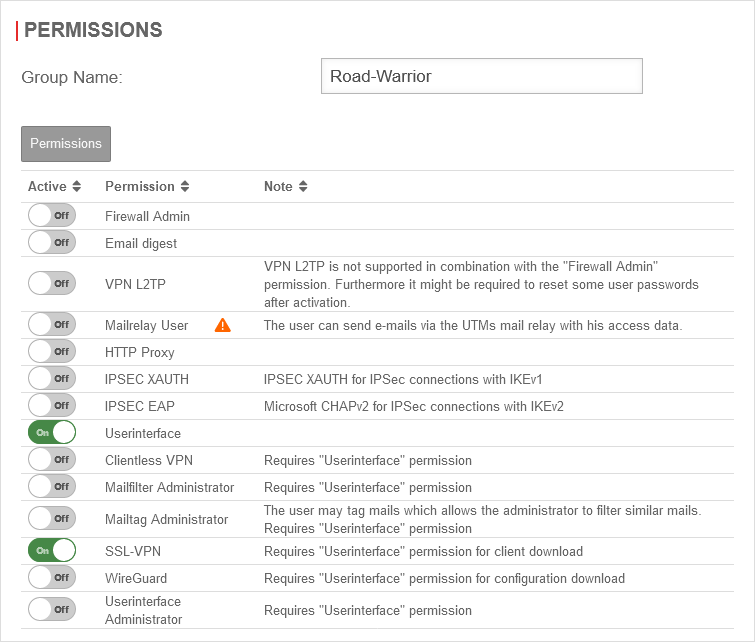
Configure group
Either a new group is created or an existing group is edited .
SSL-VPN
This is where to configure settings for the SSL VPN for an entire group.
All users share the same certificate when using the group settings!
SSL VPN settings of individual users override the group settings.
| Caption: | Value | Description: | UTMuser@firewall.name.fqdnAuthenticationUser 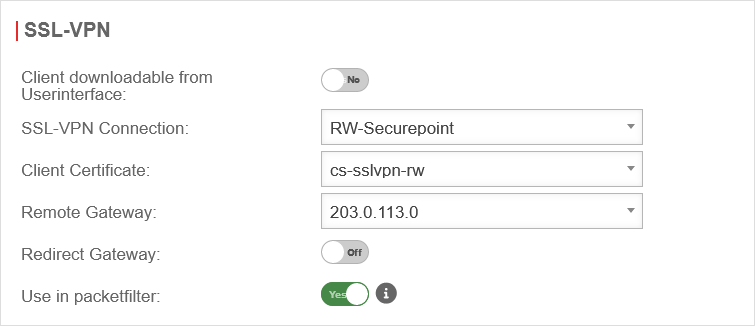 SSL VPN group settings SSL VPN group settings
|
|---|---|---|---|
| Client downloadable in the user interface: | No | If enabled, the VPN client can be downloaded in the user interface | |
| SSL VPN connection: | RW-Securepoint | Select the preferred connection (created under ) | |
| Client certificate: | cs-sslvpn-rw | Select the certificate for this group (created under Area Certificates) It is also possible to use ACME certificates. | |
| Remote Gateway: | 203.0.113.0 | IP address of the gateway on which the SSL VPN clients dial in. Free input or selection via drop-down menu. | |
| Redirect Gateway: | Off | Requests to destinations outside the local network (and thus also the VPN) are usually routed directly to the Internet by the VPN user's gateway. When the On button is activated, the local gateway is redirected to the UTM. This way, these packets also benefit from the protection of the UTM. This setting changes the configuration file for the VPN client. | |
| Use in packet filter: | No | By enabling Yes this option, rules for this group can be created in the packet filter. This can be used to control access for users who are members of this group connected via SSL VPN. | |
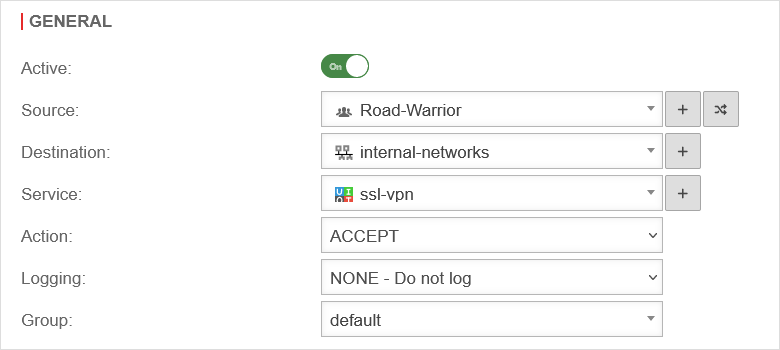
Create packetfilter rule
Result
Packet filter rule for internal services of the firewall
If a service is required that is provided by an interface network object (e.g. DNS or, as in the following example, the proxy), another filter rule is required with the network object of the transfer network.
Another rule is created in the port filter under button
Create network object
Create packetfilter rule
Another rule is created in the port filter under button