In dieser Seite werden die Variablen für unterschiedliche Sprachen definiert.
Diese Seite wird auf folgenden Seiten eingebunden
Settings and authorizations of the UTM for the Unified Security Console
Last adaptation to the version: 14.1.0 (08.2025)
New:
- Note on VPN configurations with an upcoming portal version
Last updated:
This article refers to a Beta version
-
Settings and authorizations of the UTM for the Unified Security Console
notemptyNote for cluster licenses In order for both cluster members to be assigned to each other, special new licenses must be registered on both devices. Menu Button Import license file To do this, two licenses must be downloaded from the reseller portal. If no license is marked as xynnnnn-SPARE in the reseller portal (matching licenses have an identical color marking on the left side of the table), please send an email to lizenzen@securepoint.de with customer name, customer number and the serial numbers of the devices or, in the case of VMs, with the license ID. Access by then Unified Security Console must first be enabled in the UTM itself in the menu .
The UTM reports to the license server after the update. Here, the availability of the service is indicated and the menu is activated.
notempty Attention: It usually takes a few minutes, in unfavorable cases up to an hour, before the menu is displayed for the first time. The process can be shortened by executing the command on the CLI after a few minutes of runtime (the UTM must have had the opportunity to report to the license server!). system restrictions update
|
|
|
|
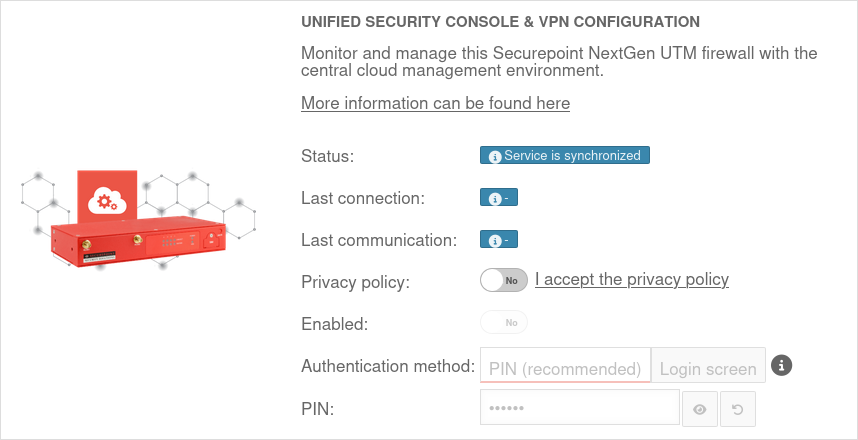
| Caption |
Value |
Description
|
|
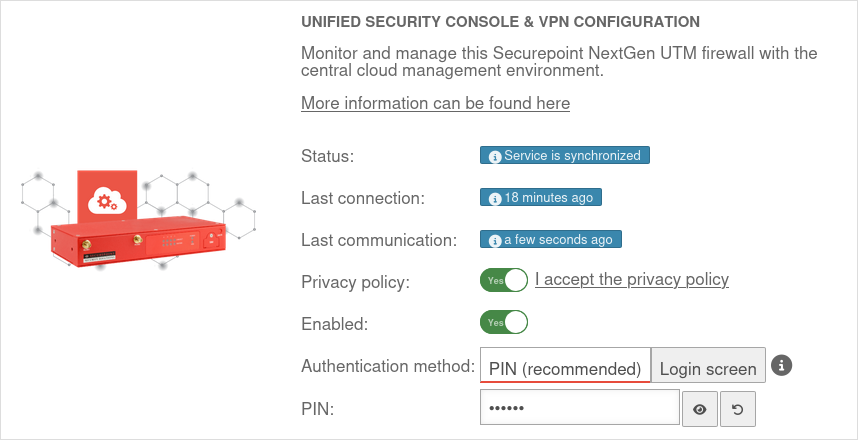
| Privacy Policy: |
Yes |
The privacy policy must be accepted
|
| Activated: |
Yes |
This activates the Unified Security Console - and thus the display, configuration and access via the Securepoint Unified Security portal.
|
| Authentication method: |
PIN (recommended)Login mask |
Authentication method for a web session
|
| PIN: |
•••••••• |
As authentication for a web session, a 6-digit PIN can be selected instead of the login mask with access data.
- The pin must not consist of equal numbers
- The pin must not consist of series of numbers (123456, 876543 etc.)
- Pins that resemble a date (230508) or contain very simple number combinations are marked as »very weak«.
|
|
Displays the Websession PIN
|
|
Creates a new PIN
|
| The entered PIN is incorrect |
After 5 (default value value can be changed in the CLI with the extc variable SESSIONAUTH_MAXRETRY extc value set application ‘spcloudpuppet’ variable ‘SESSIONAUTH_MAXRETRY’ value ‘5’
The PIN can be unblocked again when logging in to the UTM itself.
|
Actions that can only be executed with a PIN:
- Reboot
- Shut down
- Restore factory settings
- Cloud Backup Restore
- Start new websession
|
|
|
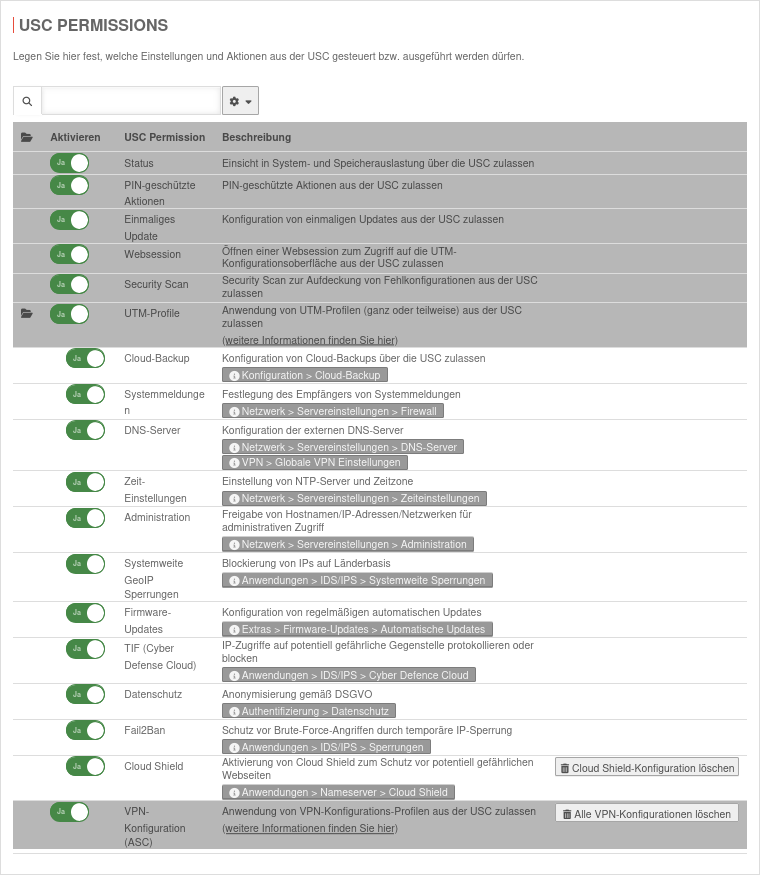
Detailed authorizations
| On the UTM under Authorizations, the authorizations of the Unified Security Console for the UTM can be activated On or deactivated Off in detail:
|
| USC authorization |
Description
|
 USC authorizations
|
| Status |
Allow insight into system and memory utilization via the USC
|
| PIN-protected actions |
Allow PIN-protected actions from the USC. These include:
- Restart
- Shutdown
- Restore factory settings
- Restore cloud backup
- Start new web session
|
| One-time update |
Allow configuration of one-off updates from the USC
|
| Websession |
Allow opening a web session to access the UTM configuration interface from the USC
|
| Security Scan |
Security Scan zur Aufdeckung von Fehlkonfigurationen aus der USC zulassen
|
| UTM profiles |
Allow the use of UTM profiles from the USC. Can be configured more precisely using the following authorizations:
|
|
|
| Open |
This icon next to UTM-Profile displays the individual UTM profiles tabs, which can then be activated On or deactivated Off
To do this UTM-Profile must be activated On
|
| Cloud-Backup |
Allow configuration of cloud backups via the USC
|
| Systemmeldungen |
Festlegung des Empfängers von Systemmeldungen über die USC zulassen
|
| DNS-Server |
Konfiguration der externen DNS-Server über die USC zulassen
|
| Zeit-Einstellungen |
Einstellung von NTP-Server und Zeitzone über die USC zulassen
|
| Administration |
Allow aconfiguration of dministrative access via the USC Host name, IP addresses or networks from which the admin station interface of the UTM may be accessed.
Configuration on the UTM in the menu Area Adminstration |
| Systemweite GeoIP Sperrungen |
Blockierung von IPs auf Länderbasis über die USC zulassen
|
| Firmware-Updates |
Konfiguration von regelmäßigen automatischen Updates über die USC zulassen
|
| TIF (Cyber Defense Cloud) |
IP-Zugriffe auf potentiell gefährliche Gegenstelle protokollieren oder blocken über die USC zulassen
|
| Data protection |
Allow configuration of the anonymization of UTM applications via the USC
|
| Fail2Ban |
Allow configuration of Fail2Ban via the USC
|
| Cloud Shield |
Allow configuration of Cloud Shield via the USC
|
Delete Cloud Shield configuration
Deletes the local Cloud Shield configuration The configuration is normally carried out via the USC to ensure synchronization and should only be carried out here in exceptional cases. If Cloud Shield is to be reactivated, it must be ensured that the authorization is set on the UTM side. A new transfer of the configuration to the UTM must then be triggered in the USC by changing the Cloud Shield or UTM profile. |
|
|
| VPN configuration (ASC) |
Allow the use of VPN configuration profiles from the USC
|
Alle VPN-Konfigurationen löschen
All VPN configurations for this UTM can be deleted using this button
|
|
|





