Last adaptation to the version: 14.1.1 (11.2025)
- BetaFor participants on the Beta Channel only:
- Beim Konfigurieren einer Verbindung können Benutzergruppen direkt mit ausgewählt und in der Tabelle angezeigt werden
- Die Übersichts-Tabelle der CVPN-Verbindungen wurde um zahlreiche Informationen ergänzt
- Wählbare Videoauflösungen wurden erhöht
Introduction
UTMuser@firewall.name.fqdnVPN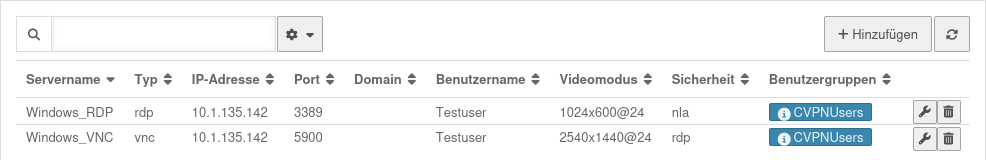 Übersicht der Clientless VPN Verbindungen notempty
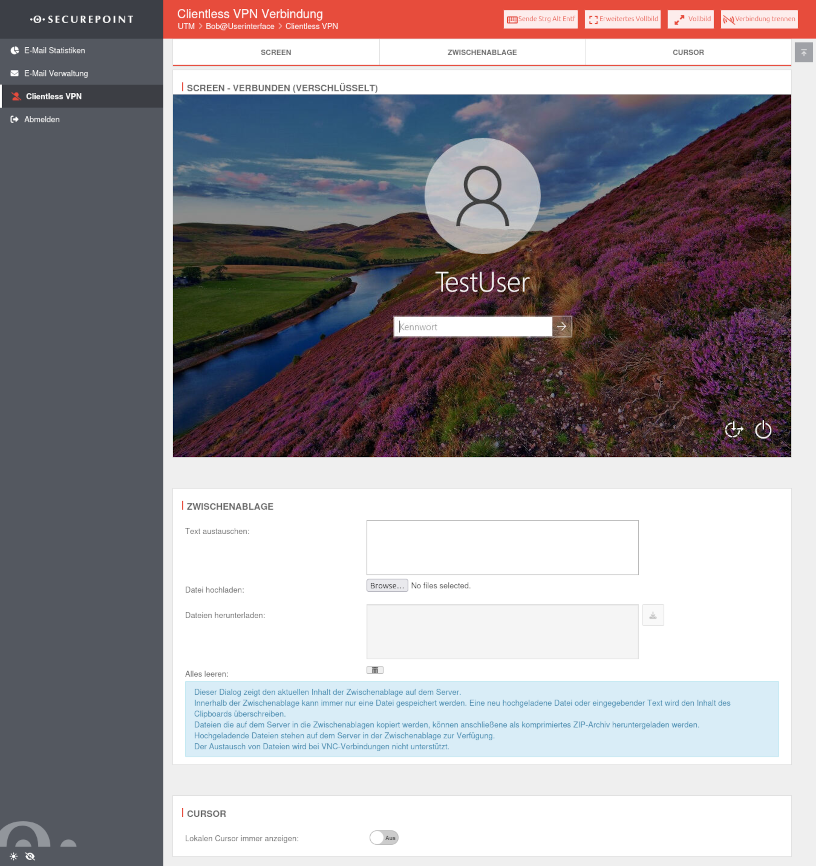
Übersicht der Clientless VPN Verbindungen notemptyClientless VPN provides the ability to connect to an RDP or VNC server on the corporate network via the browser. Users log in to the user interface and are then given the option to connect with a designated server. For this to work, the browser must have HTML5, Java or similar is not necessary.
Die Übersicht zeigt zahlreiche Informationen an:
- Servername
- Typ
- IP-Adresse
- Port
- Domain
- Benutzername
- Videomodus
- Sicherheit
- BenutzergruppenCVPN-Benutzer Zugeordnete Gruppe mit Clientless VPN-Berechtigung
CVPN-Benutzer Zugeordnete Gruppe ohne Clientless VPN-Berechtigung
Configuration of the UTM
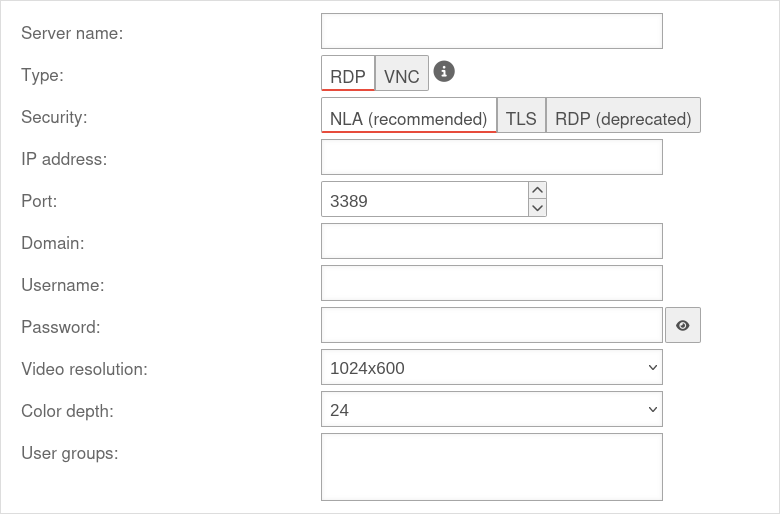
Add Clientless Host
Under click the button.
All servers that are to be made available to users via the user interface using Clientless VPN are entered here.
Gruppenberechtigung
UTMuser@firewall.name.fqdnAuthenticationUser 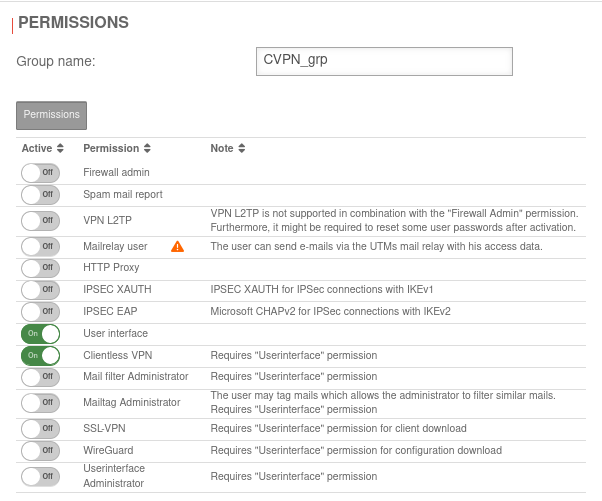 Group permissions
Group permissions
- Click Area Groups button or existing group
- in the Permissions section:
- Enable Userinterface with the On button
- Enable Clientless VPN with the On button
- Assign a unique name in the Group name: field.
Subsequent assignment of the group
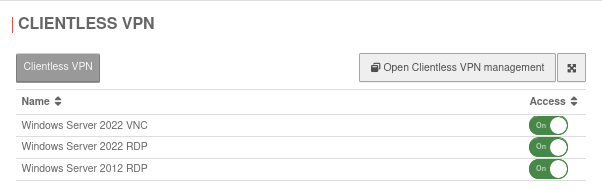
- Switch to the Clientless VPN tab.
- Activate desired clientless VPN connection with On
- Apply the changes with
Allow access
UTMuser@firewall.name.fqdnFirewall 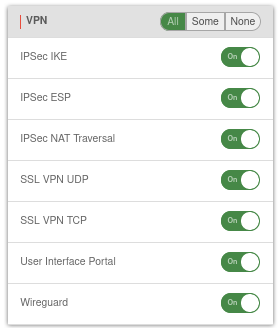 Group permissions
Group permissions
Now it must be ensured that the clientless VPN user is also allowed to log in to the user web interface via the browser. This can be done either by Implicit Rules or by manually creating a corresponding Packetfilter Rule on the interface.
In this case it is sufficient to activate the User Interface Portal VPN rule with On in the menu under Area VPN.
CVPN anwenden
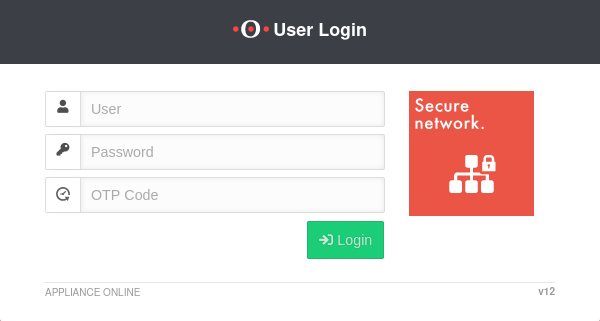
Login to the user interface
- The user login to the user interface is called up via the IP address or URL of the UTM, possibly followed by a port specification
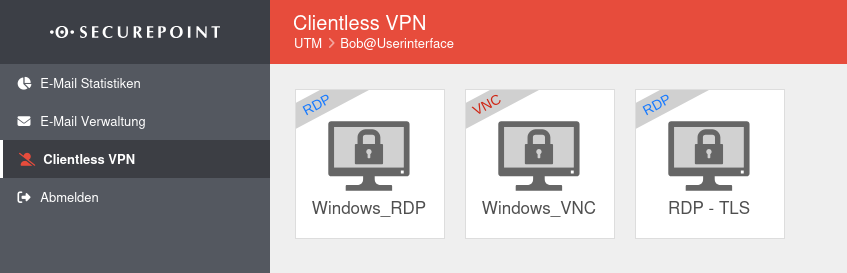
- Depending on the assigned permissions, various functions are made available
- Click on the corresponding tile to access the desired function
| Configured | Port | Example call with IP | Example call with URL |
|---|---|---|---|
| Default | 443 | i.e. https://192.168.175.1 | i.e. https://utm.ttt-point.de |
| Port changed bei administrator Menu: Network / Appliance Settings / Appliance Settings / Webserver / User Webinterface Port |
4443 | i.e. https://192.168.175.1:4443 | i.e. https://utm.ttt-point.de:4443 |
notempty
After entering the IP address, the user login page of he Securepoint UTM is loaded. The login credentials are entered there.
CVPN starten
CVPN ausführen
Hints
Windows 2012R2 with enabled terminal services
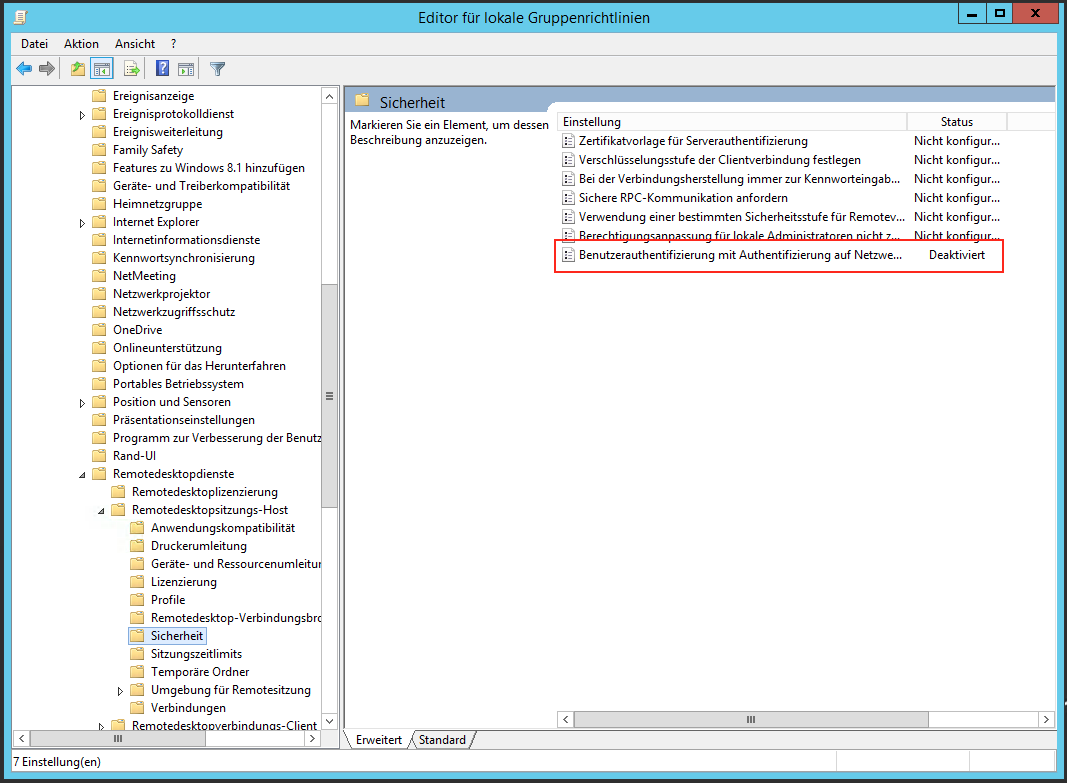
If a 2012R2 server is to be used as the RDP server for the clientless VPN, the establishment of the RDP connection fails due to the "Authentication at network level".
When using the terminal services, this function can also no longer be deactivated via the familiar way.
However, it is possible to force the disabling of ""Authentication at network level"" via the GPO (Group Policy).
Adjusting the registry
However, it may also be necessary to adjust a registry entry. This must have a value of 1.
Computer\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp
SecurityLayer