Configuring an IPSec VPN connection with a Sophos firewall as the remote peer
New article: 01.2023
This article refers to a Beta version
-
Preliminary note
- This best practice uses the software versions
- Securepoint UTM: v12.2.3.1 Version 12.2.5.1 or higher should be used
- Sophos: SFOS v19.0.0 GA-Build317
- Securepoint UTM: v12.2.3.1
- Setting options may change, be renamed or moved in future software versions.
This should not restrict the basic functionality
- Supported VPN types:
- IPSec with IKEv1
- IPSec with IKEv2
- SSL / OpenVPN is not supported:
- Sophos uses proprietary configuration files (.apc instead of .ovpn)
- There are only a few configuration options
The following network situations were tested:
- Sophos (Public, fixed IP) <-> UTM (Public, fixed IP)
- Sophos (Public, fixed IP) <-> UTM (NAT without port forwarding)
- Sophos (Public, fixed IP) <-> UTM (NAT with port forwarding)
- Sophos (NAT without port forwarding) <-> UTM (Public, fixed IP)
- Sophos (NAT with port forwarding) <-> UTM (NAT without port forwarding)
Additional routers
If the Securepoint UTM or Sophos Firewall is also behind another router (e.g. a Fritzbox that provides Internet access), the following ports must be forwarded there:
- No NAT on either side: Port 500/UDP (ISAKMP)
- NAT on one side: Port 500/UDP + 4500/UDP (NAT-T)
Configuration on the Securepoint UTM
The connection setup on the UTM is done as described in the Wiki article IPSec Site-to-Site.
The following parameters must be considered:
The following parameters must be considered:
AssistantSecurepoint UTM IPSec assistant: Tab Connections Button | ||
| Log view | Recommended setting | |
|---|---|---|
| IKE protocol: | IKEv2 (For unsolvable problems, use IKEv1) | |
Phase 1Tab General | ||
| Start behavior: Outgoing / Incoming | Incoming, on the side where the device is most "directly" connected to the Internet. Ranking:
| |
| DPD | On Active | |
| Encryption: | Recommended values:
| |
| Authentication: | Recommended values:
| |
| Diffie-Hellman Group: | ecp521, ecp384, ecp256, modp8192, modp6144, modp4096 | |
| Strict | On Active | |
| IKE Lifetime: | Child_SA Lifetime ≦ IKE_SA Lifetime < 8 Hours Reason: On Sophos, the Child_SA Lifetime must be less than or equal to the IKE_SA Lifetime | |
| Rekeying | unlimited | |
Phase 2 | ||
| Encryption: | AES256, AES198, AES128 | |
| Authentication: | SHA2_512, SHA2_384, SHA2_512 | |
| Diffie-Hellman Group: | ecp512, ecp384, ecp256, modp8192, modp6144, modp4096 | |
| IKE_SA Lifetime: | Child_SA Lifetime ≦ IKE_SA Lifetime < 8 Hours Reason: On Sophos, the Child_SA Lifetime must be less than or equal to the IKE_SA Lifetime | |
| Reboot after abort: | If necessary: On Active (Only on the outgoing side) | |
| Group subnet combinations: | Option is not supported by Sophos or is not available | |
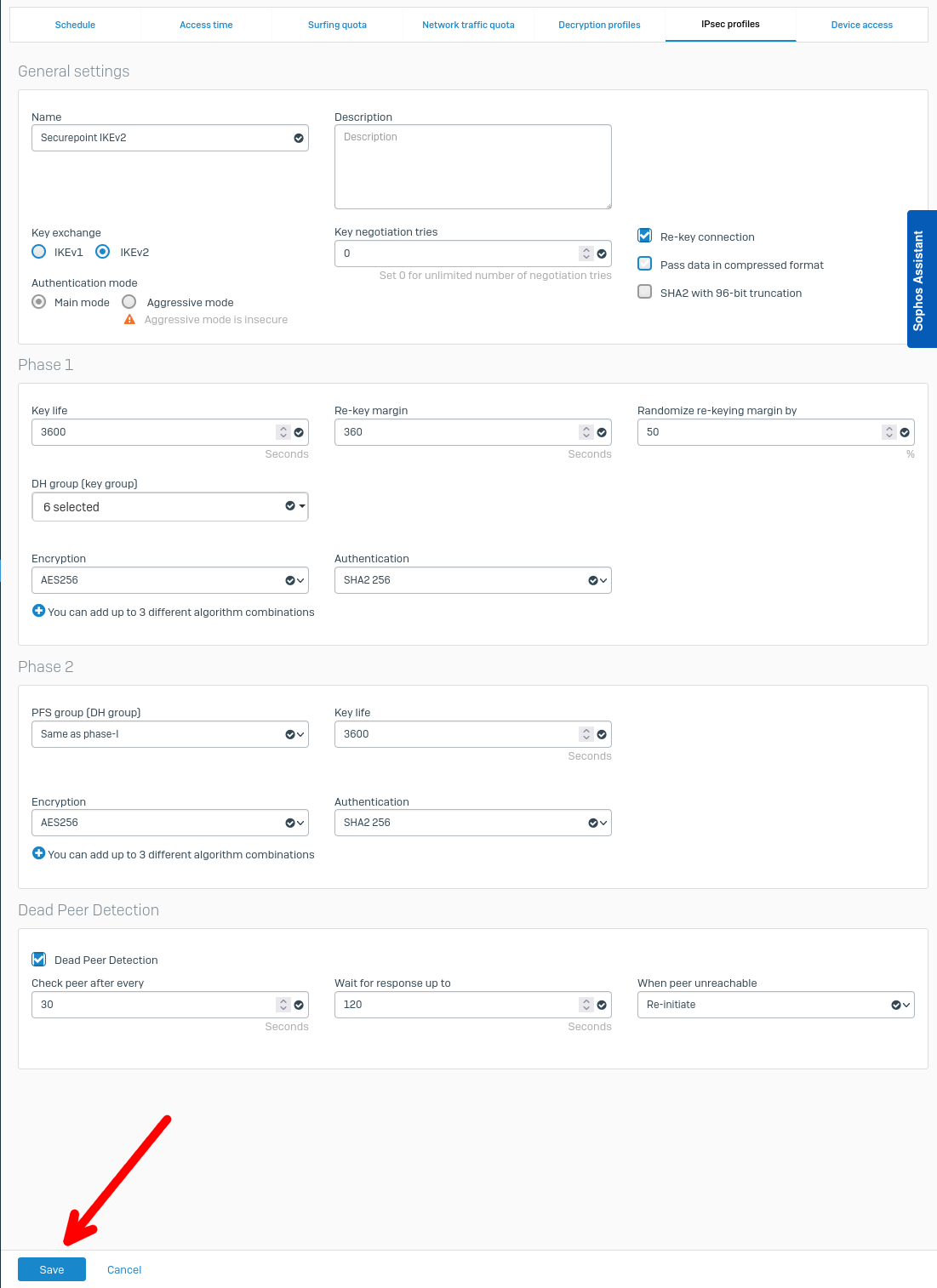
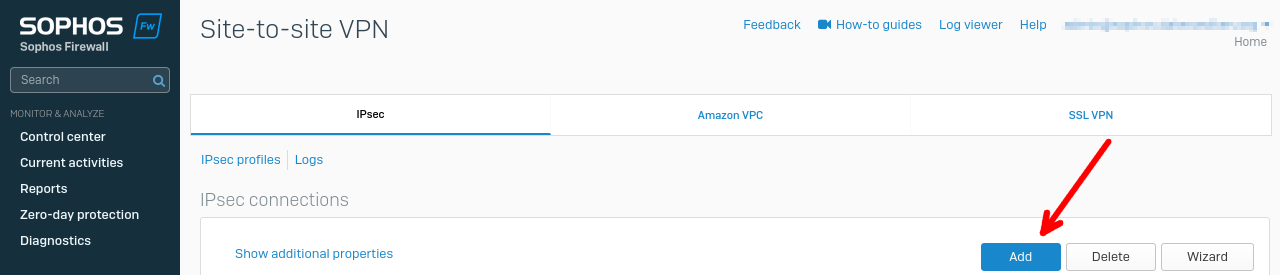
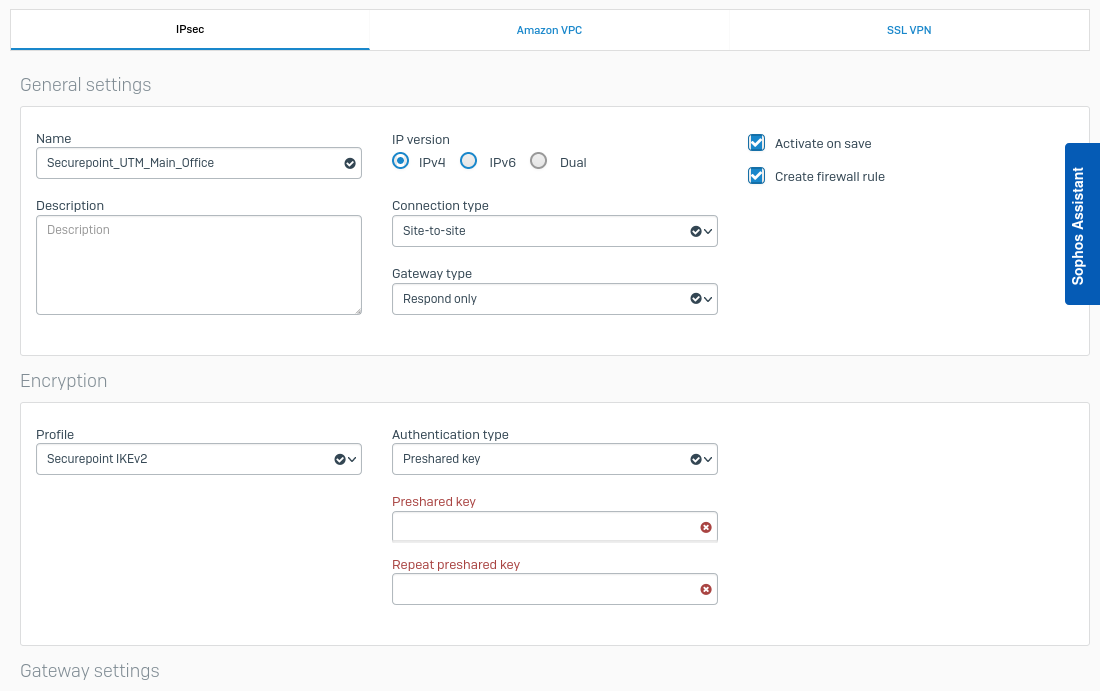
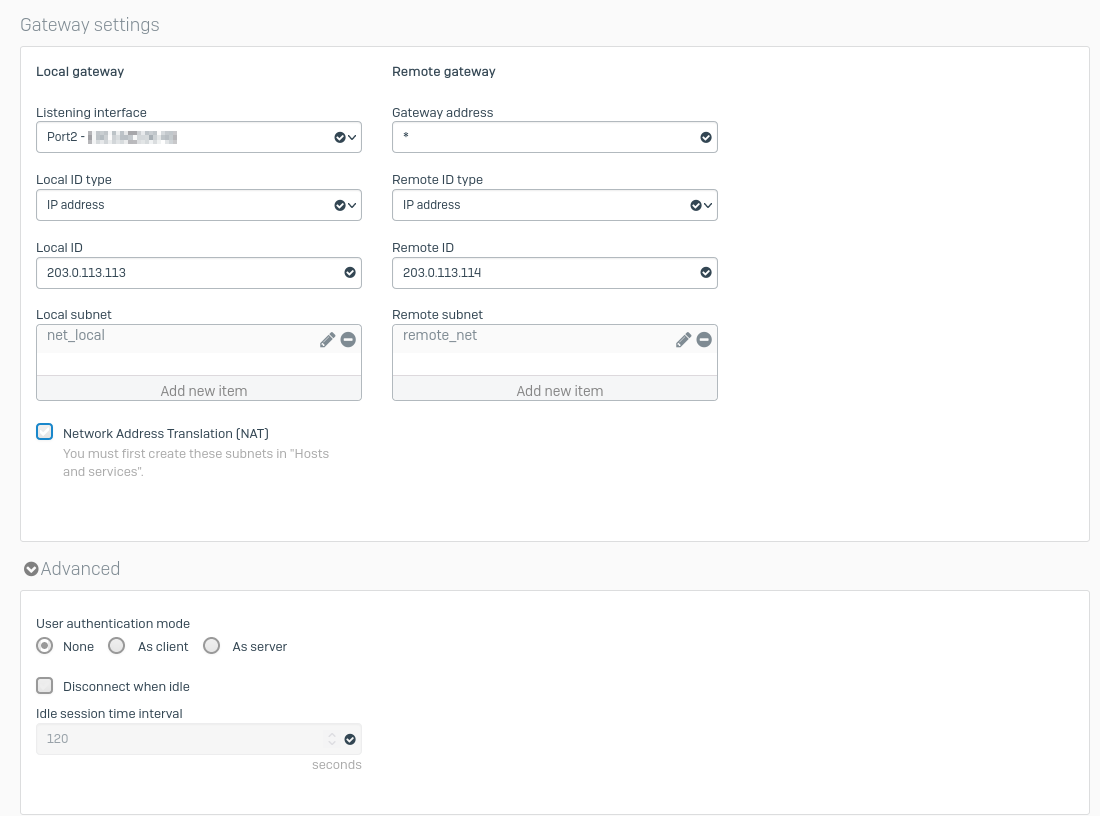
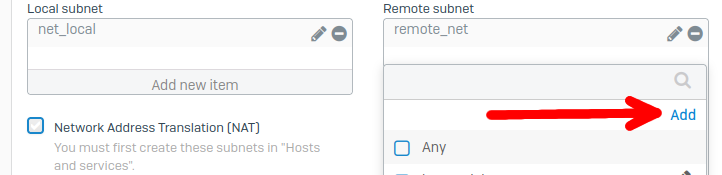
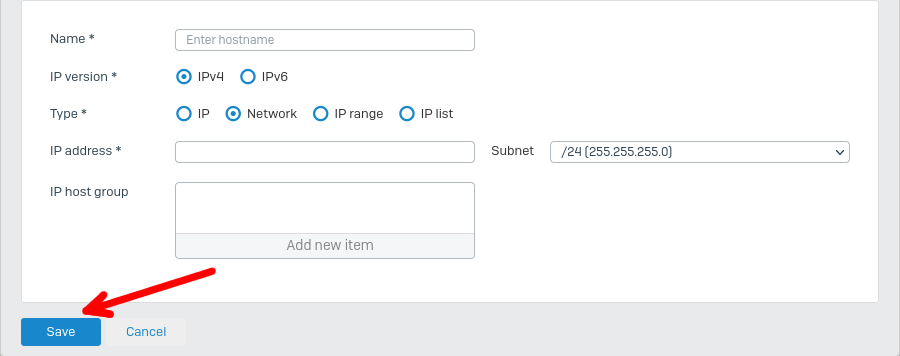
Configuration on the Sophos Firewall
Troubleshooting
IPsec Log

Viewable under the Control Center menu item in the Monitor & Analyze section, link Log view at the top right of the Sophos Admin Panel.
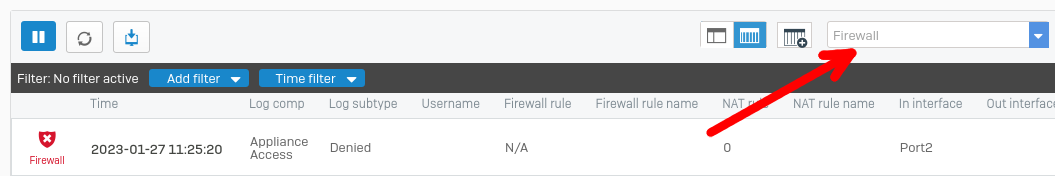
- After selecting this option a popup window opens
- Select the log category Firewall in the dropdown menu here.

- Now it is possible to select the log category VPN in the drop-down menu.