Last adaptation to the version: 12.2.5.1
- Layout adjustments
Introduction
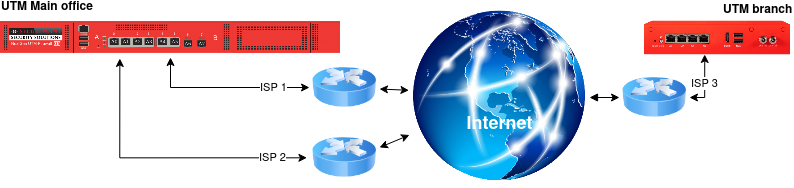
This wiki article describes how to set up a fallback for an SSL-VPN Site-to-Site tunnel. It is assumed that an existing SSL-VPN Site-to-Site server is in place.
The setup is as follows:
There is an internet connection at the remote location and on the firewall at the main location, a multipath routing is configured over two internet lines. The tunnel is now configured so that the remote location initiates a Site-to-Site tunnel with the central location over one of the two lines.
Configuration of the head office
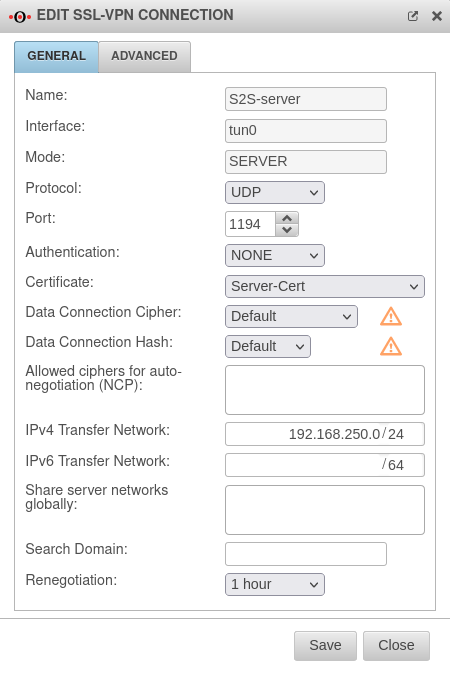
In the head office, multipath routing must be configured, so there are two interfaces each with a public IP and two default routes. If not already done, the OpenVPN server configuration can be done as described in the article SSL-VPN Site-to-Site.
Configuration of the branch office
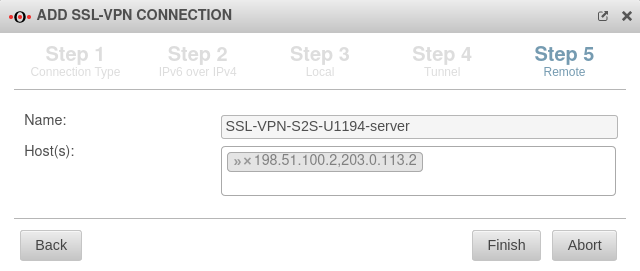
The Site-to-Site client is set up as usual, with one exception:
In step 5 in the Host(s): field, both IP addresses of the main offices must now be entered, separated by a comma.
198.51.100.2,203.0.113.2
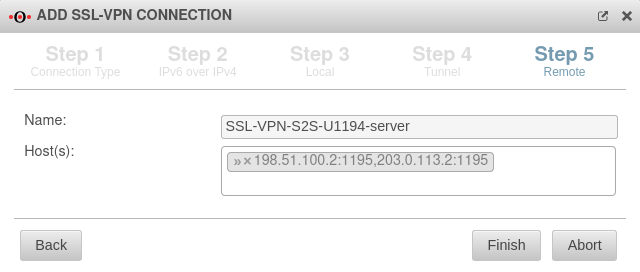
If the SSL-VPN server in the central location does not receive connections on port 1194, the port must be entered directly after the IP, separated by a colon.
198.51.100.2:1195,203.0.113.2:1195
Procedure in case of failure
- Site-to-Site Tunnel has been established (Branch office <-> Head office - Line 1).
- Line 1 in the head office loses the connection.
- The branch office tries to establish a tunnel through Line 1 of the head office for two minutes.
- The head office does not respond on Line 1 for two minutes.
- The branch office switches and now tries to initiate the tunnel through Line 2 of the head office.
- The tunnel is now established through Line 2 of the head office.
When will the tunnel be switched back to line 1?
The tunnel is not re-initiated on Line 1 without further action. This only happens when Line 2 of the head office loses the connection or the SSL VPN service at the branch office is restarted.


