Last adaptation to the version: 14.0.1 (01.2025)
- Individual peers can be deactivated in the Dashboard
- Additional options for table display in the Dashboard settings
notemptyThis article refers to a Beta version
General
Overview
Wireguard® is a modern and simple VPN protocol, which additionally convinces by its performance.
Advantages
The OpenVPN integration in the Securepoint UTM is also very performant.
The speed disadvantage of SSL-VPN connections compared to WireGuard connections is therefore not as serious as can be observed with competitors.
Disadvantages
Connection
Communication takes place via a freely selectable UDP port and uses IPv4 and IPv6 to transport the data packets.
The handling between the two peers is very similar to OpenSSH.
"Peers" must first exchange their PublicKeys and can then "simply" exchange data further on.
The exchange of PublicKeys is explicitly not part of the WireGuard specification and must be performed manually.
A PublicKey must identify a peer unmistakably.
Multiple uses are not practical.
For better protection, a preshared key can also be used.
NAT
This keeps connections open on NAT routers.
Since the communication only runs via a UDP port, WireGuard is not susceptible to NAT related problems.
Widget
There is a widget in the admin interface for the overview of WireGuard connections. Further information can be found in the Wiki article for UTM Widgets.
Dashboard
The dashboard displays the connection status of each peer in a connection, as well as the name, key, public key value, IP address of a user, and the associated user groups. notemptyNew as of v14.0.1 Activeon: Peers that are not managed by the cloud can be deactivated Off.
UTMuser@firewall.name.fqdnVPN 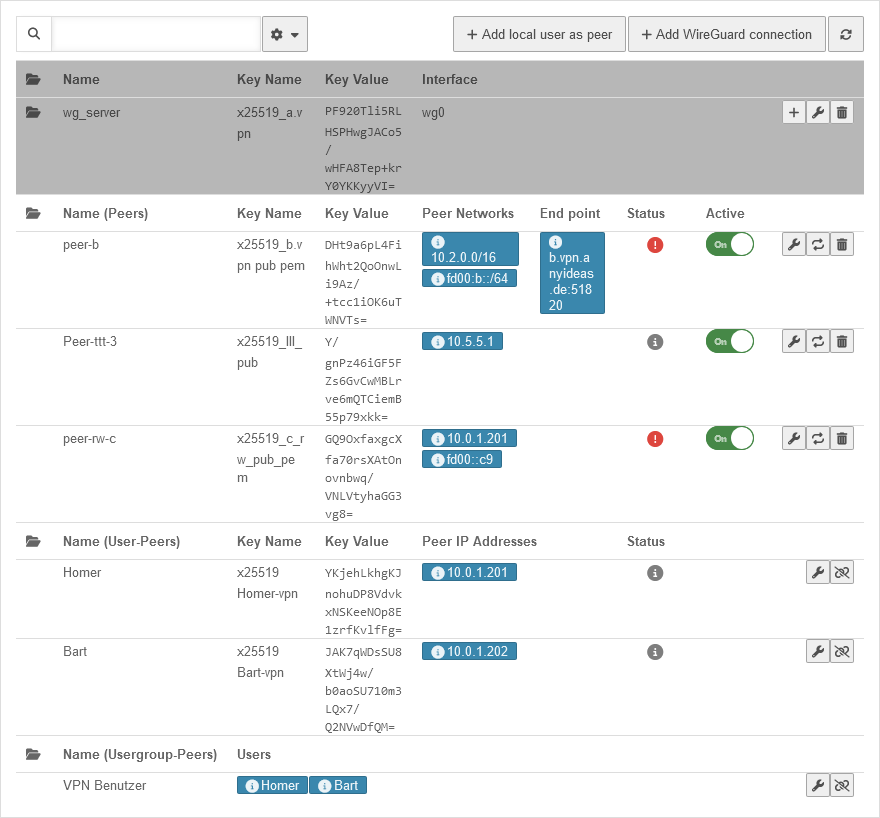 WireGuard Dashboard WireGuard Dashboard
|
Dashboard settings
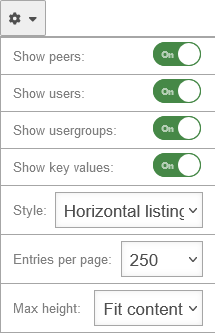
For a better overview, individual sections can be hidden in the overview if necessary: