Add peer (remote terminal)
|
If a WireGuard connection already exists in which the UTM serves as a server, an additional peer can be added that runs on the same port. It uses the same certificate to authenticate the connection as an existing connection.
For additional remote terminals (peers), their own public key is required, as well as their own PSK.
|
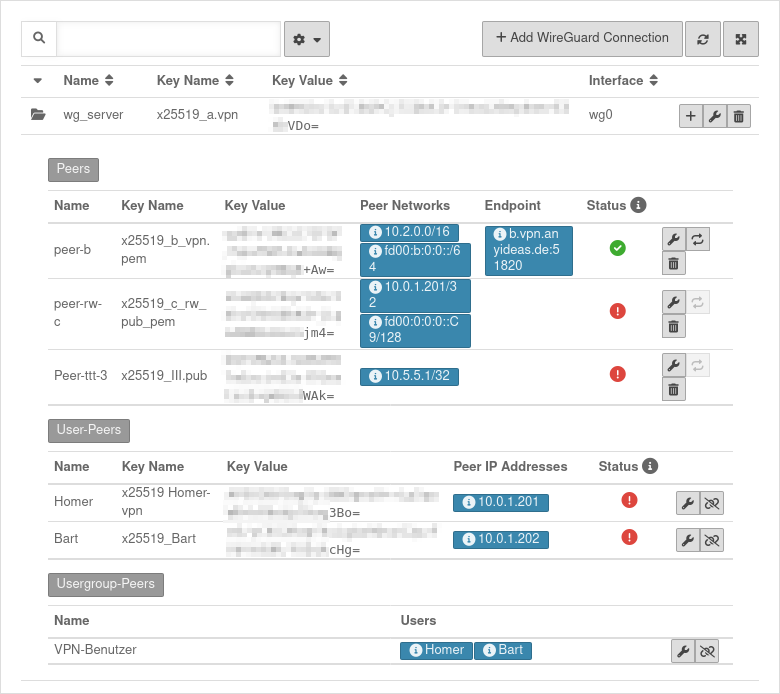 WireGuard Dashboard WireGuard Dashboard
|
Button Add peer of the connection you want to use
The connection status refers exclusively to the WireGuard tunnel, not to the actual reachability of the hosts on the other side of the tunnel (firewall rules, network configuration)!
|
| Status |
Description
|
|
The tunnel is active
|
|
No indication of status can be made until a data packet is transmitted or the keepalive is activated.
The connection status of peers for which no endpoint is defined is basically only updated in case of incoming traffic/keepalive from the client side, i.e. an unknown status in this case does not necessarily mean a misconfiguration, but possibly only an inactive client. |
|
An error has occurred. The connection cannot be established.
|
|
|
| Caption |
Value |
Description
|
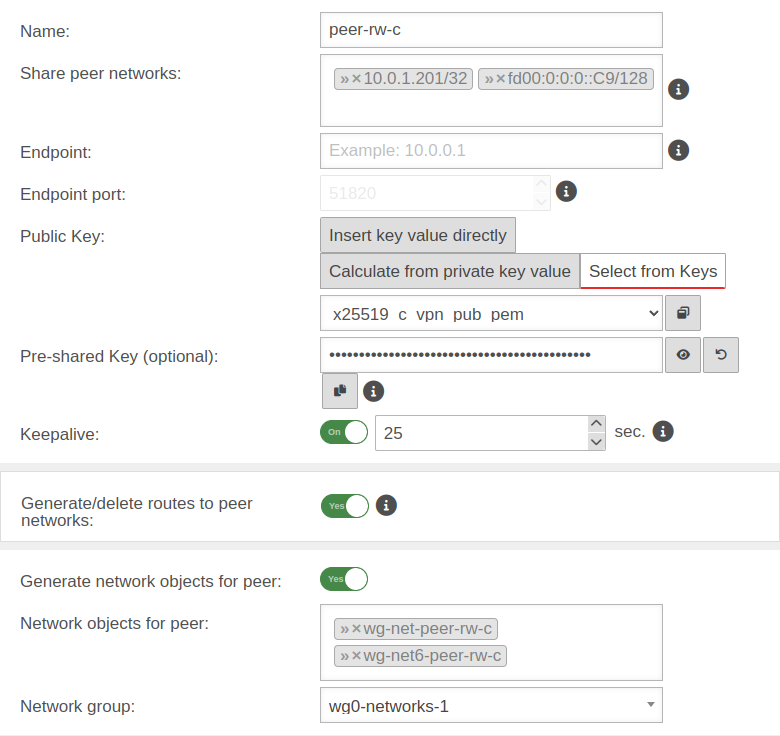 As an example, a WireGuard peer is added to a Roadwarrior connection. As an example, a WireGuard peer is added to a Roadwarrior connection.
|
| Name: |
peer-rw-c |
Description of the remote terminal (here: a roadwarrior)
|
| Share peer networks: |
Site-to-Site »10.2.0.0/16 »fd00:b:0:0::/64 |
Site-to-Site
Local net IP of the remote terminal
|
| Roadwarrior »10.0.1.201/32»fd00:0:0:0::C9/128
|
Roadwarrior
IP of the transfer network (»…/32 or »…128)A roadwarrior uses only the tunnel IP
|
| Endpoint: |
Site-to-Site
c.vpn.anyideas.de |
Site-to-Site
Public IP or within the public DNS resolvable FQDN with listening-port of the remote terminal
|
Roadwarrior
|
Roadwarrior
Can remain blank if no connection is to be initiated from the UTM
|
| Endpoint Port: |
Site-to-Site
51820
Default |
Site-to-Site
Set the port of the parent connection
|
Roadwarrior
51820
|
Roadwarrior
The port is already defined by the settings of the parent connection and is predefined here
|
| Public key:
|
| Enter key value directly |
|
The key value is entered directly.
|
| Calculate from private key value |
|
Calculates the key value from the private key value used
|
|
Views / hides the key value
|
|
The key value is generated
|
|
The key value is copied to the clipboard
|
| Select from keys |
x25519_c_vpn_pub_pem |
Public key of the remote terminal in the x25519 format.
Only keys that have no private key can be selected.Public key present but not selectable?
Only keys for which there is not yet a connection on this interface can be selected. The PublicKey must be unique within a connection, as the routing of incoming packets is carried out via it.
If the same PublicKey is to be used for a peer, e.g. for a fallback, another WireGuard connection must be created for this.
|
|
Site-to-Site
If the public key of the remote terminal is not yet known, this button can be used to open the import of the key management.
|
Roadwarrior
If the public key of the roadwarrior is not yet known, this button can be used to open the import of the key management.
We recommend creating the key pair for the Roadwarrior on the UTM and then storing it securely. Approach:
- Press the button. This will open the Add Key dialog.
- Choose a meaningful name in Name:.
- As Type: select the X25519 form and Save and close
- The key created will be inserted and is listed under
|
| Pre-Shared Key (optional): |
…QxJqz22W4/FWipaxs= |
Pre-shared key for further securing the connection
|
|
The pre-shared key is displayed
|
|
Generates a very strong pre-shared keyThe pre-shared key must be identical at both ends of the VPN connection! It may only be generated on one side and must then be inserted on the other side.
|
|
The pre-shared key is copied to the clipboard
|
| Keepalive: |
Off Default |
Regularly sends a signal. This keeps connections open on NAT routers. On Activation is recommended.
|
| 25 |
Interval in seconds at which a signal is sent
|
|
|
| Create / remove routes to the peer's networks: |
No Default |
Creates on activation routes to the peer's networks
CLI command for each element from Allowed IPs: route new src "" router "wg0" dst "»Allowed IP" |
|
|
| Generate network objects for peer: |
No Default |
When activated Ja network objects (IPv4 and if necessary IPv6) for the remote terminal are generated
|
| Network objects for the peer: |
»wg-net-peer-rw-c »wg-net6-peer-rw-c |
The automatic default name (wg-net-Peer-Name) can be changed
|
| Network group: |
wg0-networks |
Assigns the newly created network objects to a network group
|
|
|