notempty
- Renegotiation is configured exclusively in the UTM
- OTP token details added
- Password and OTP code entry possible in different formats
Foreword
If the OTP method is activated, login is only possible by entering a correct OTP.
SSL-VPN:
Since SSL VPN re-authenticates every hour, a new OTP must also be entered every hour.
Renegotiation can be increased or completely disabled in the menu in the settings of a connection in the
| General | {{{2}}} |
Of course, disabling is not recommended. A change is transmitted by the UTM to the SSL VPN clients.
Saving the password in the SSL VPN client is not possible because the password that is passed is composed of the static user password and the OTP.
In case of malfunction of the OTP generator (smartphone or hardware token), the OTP can only be generated if there is access to the QR code or the secret code. This can be found under
Printout of this code for the administrators as described in OTP Secret. File in the documentation.
The time of the UTM system can be checked in three ways:
- Using the administration web interface: The time is shown in the widget selection if it is not expanded or in the network menu under server settings in the time settings section.
- Using the CLI with the command system date get
- Using the root console with the command date
The system time can then be set using the following options:
- Using the administration web interface in the network menu under the menu item server settings in the section time settings
- Using the CLI with the command system date set date then seperated with spaces the current date and time in the format YYYY-MM-DD hh:mm:ss
OTP - One-Time-Password
Das One-Time-Password (OTP) ist ein zusätzlicher Authentifizierungs-Mechanismus der für zusätzliche Sicherheit bei der Anmeldung eines Benutzers sorgt.
In der UTM setzen wir das Zeit-Basierte-Verfahren ein (TOTP = Time-based One Time Password). Hierbei wird aus dem Sharedsecret Code und der aktuellen Uhrzeit alle 30 Sekunden ein neuer OTP errechnet.
Um dieses 6 stellige Passwort zu generieren, wird als Token eine Smartphone App gneutzt, wie z.B. der Google Authenticator. Dieser ist sowohl für Android als auch für iOS Geräte verfügbar.
Andere Apps wie z.B. FreeOTP für Android sind ebenfalls möglich.
Set up OTP
Activation procedure
- Ensure that the time of the UTM and the token runs synchronously
- Transmission of the secret code to the token
- Activating the OTP method on the UTM
- Testing the login before the current session has ended
If the method is activated, each user of the selected applications must additionally log in via OTP.
Exceptions are not possible.
Configure OTP user
First, the users are created under as usual.
See also User Management.
The OTP code for this user can only be displayed after the user's entries have been saved.
Display or change by clicking on the edit button in the user row in the tab
| OTP | {{{2}}} |
Create a code automatically
The code can be created automatically by the Securepoint UTM and is available in two formats.
On the one hand as a QR code, which can simply be photographed with the smartphone app, and on the other hand in text form to be entered using the keyboard.
The button can be used to regenerate the code.
Enter a code
It is also possible to manually enter a 16-digit base32 or HEX encoded key with . This is required, for example, for a hardware token such as the OTP c200. Here you receive a code from the supplier, which must then be registered to the user.
Note that when entering a HEX encoded key, the
- format
followed by the - validity period must be added in brackets
before the key, e.g. hex(60)A6ABBEF26746BC4242AE1764C2863826B98DD210.
OTP Secret
For distribution to the users there is a possibility to print the created codes.
A document in PDF format will then be generated.
Setting up Google Authenticator
First, the Google Authenticator must be downloaded from the app store, installed and opened.
The first window contains a description about the 2 levels of authentication to Google Account. Tap on the settings button.
In the Add account window that appears, in the Add account manually section, select either Scan barcode or Enter key.
For Scan barcode, an additional app for scanning barcodes called "Barcode Scanner" may be installed if it is not already on the smartphone.
In order to automatically create an account, simply point the smartphone camera into the area of the printed or on-screen QR code.
If the QR code is not to be scanned, the data can be entered manually under Enter key. Time-based must be selected here.
In the following window, the account is then displayed with the OTP code.
The code changes every 30 seconds.
The time display on the right gives an overview of how long this OTP password remains active.
Use of a hardware token
The use of a hardware token is also possible.
This should be a RFC 6238 compatible password generator.
We currently support the https://www.mtrix.de/portfolio/feitian/otp/ Feithan OTP c200].
A download link for the HEX code is sent by the supplier for this purpose, which must be registered with the user as described above.
The following parameters must be used:
- SHA algorithm: SHA1
- Time interval: 30 seconds
The ID is a serial number of the token and the key is a 32 to 40 character code as shown in the figure.(Here with a time interval of 60 seconds).
Check OTP
The can be used to test whether the app generated OTP works.
In the newly opened window, enter the password that the app displays for this user and click .
Please enter OTP code OTP Code
If everything is set up correctly, a message will appear.
Info:
For locally created users, a user group must be selected. The permissions of this user group are not significant.
Assign OTP to applications
Under you can select for which applications the users should additionally authenticate themselves with the one-time password.
Off Admin Web Interface
Off User web interface
Off IPSec
Off SSL-VPN
Off SSH (console)
Use OTP
Web interface
When logging in to the administration or user web interface, there is now an additional authentication field for the OT code.
Here, in addition to the user name and password, the generated code is entered.
VPN
If the remote terminal allows a separate transmission of the OTP password (UTM from version 11.8), the following procedure can be followed:
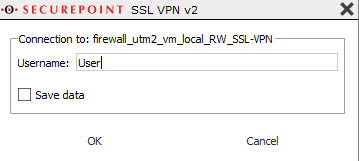
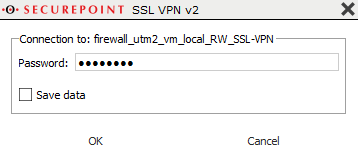
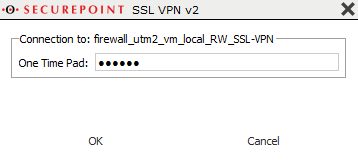
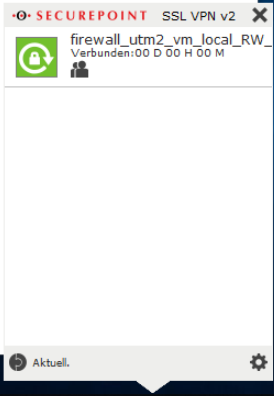
Start the SSL VPN connection on the client (on Windows: double-click the lock icon in the taskbar).
Establish the connection by clicking on Datei:SSL-VPN-v2 Verbindung-aufbauen-en.png
The connection is established in three steps:
If OTP is used in combination with an SSL VPN or Xauth VPN connection and the remote terminal does not support the separate transmission of the OTP code, the OTP code must be entered directly after the user password without spaces during the password query.
This option is not available in UTM versions 11.8.0 to 11.8.3.4.
Example:
- Password:
- insecure
- OTP:
- 123456
- password
- insecure123456
Saving the password in the SSL VPN client is not possible because the password that is passed is composed of the static user password and the OTP.
SSH connection
If access is used with an SSH console and OTP, the OTP code is requested in a separate row Pin.
When accessing with an SSH console and OTP, and the counterpart does not allow separate transmission of the OTP code, the OTP code is entered without spaces directly after the user password.
This option is not available in UTM versions 11.8.0 to 11.8.3.4.
Example:
- Password in UTM:
- insecure
- OTP:
- 123456
- Password
- insecure123456