Last adaptation to the version: 1.28 (07.2024)
- Changed menu navigation
- Updated option for restrictions: Tethering settings (v1.27)
- Updated option for restrictions: WLAN configuration (v1.27)
notemptyThis article refers to a Beta version
Preamble
In a profile permissions, restrictions, password requirements, email settings and security settings are configured.
Several users or user groups (roles) can be assigned to a profile.
Several devices or device groups (devices designated by tags) can be assigned to a profile.
notempty For a large number of devices and users it is recommended to map the assignment via groups.
- Device registration is directly tied to a profile
- A profile must be created first' (and configured) before a device can be registered
In Android Enterprise profiles, numerous security-relevant settings can be made, e.g.
- Disable Kamara
- Disable microphone
- Disable USB file transfer
- Disable outgoing calls
- Disable Bluetooth
- Disable contact sharing
- Disable tethering
- Disable sms
- Enable network only with VPN
- and much more.
notempty Android Enterprise Profiles are used immediately and do not need to be published!
- Outdated Android profiles behave fundamentally different than Android Enterprise Profiles (EMM)
- It is no longer possible to assign a profile to a role, user or tag
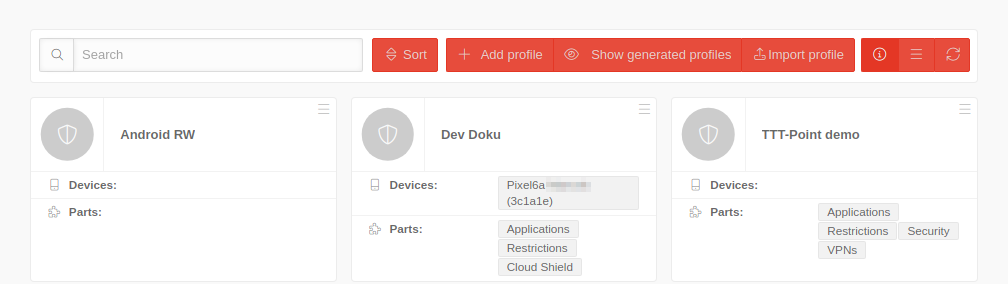
Overview of profile management | ||||
| In the profile overview new profiles can be created, existing ones can be edited and deleted. The view of the profiles can be displayed in the list or tile view. You can also view details of existing profiles, update the list of profiles, and publish profiles. |  |
 | ||
General Options | ||||
| Filters on profile tiles that contain the search text | ||||
| Sortieren | Per Klick auf diese Schaltfläche öffnet sich ein Menü, indem nach bestimmten Kriterien die Kacheln sortiert werden können | |||
| Sortieren | Per Klick auf diese Schaltfläche öffnet sich ein Menü, indem nach bestimmten Kriterien die Kacheln sortiert werden können | |||
Sorts the tiles by profile name | ||||
Sorts the tiles according to the priority of the profile | ||||
Sorts the tiles in ascending or descending order according to the selected criterion | ||||
| Add profile | Creates a new profile. The settings in the profile vary depending on the operating system. | |||
| Import profile | Existing profiles that were previously exported from the Securepoint Mobile Security Portal can be imported here | |||
| Hide generated profiles | Hides the generated profiles | |||
| Show details | Show / hide details: For a large number of profiles, it can be useful to hide the most important details for clarity. | |||
| / List view / Grid view | Switch between lists and grid view | |||
| Refresh | Refreshes the display | |||
Profile tile
| ||||
Profile-Options
| ||||
| The button at the top right of each profile tile provides the following options: | ||||
| Edit | Editing the settings (see below) | |||
| Copy | Copying the profile to the clipboard | |||
| Export | Exporting the settings | |||
| Delete | The profile is deleted notemptyNew as of: 2.5 Android Profile, die mind. ein zugewiesenes Gerät haben, können nicht gelöscht werden.
| |||
Details displayed in the profile tile: | ||||
| Updated | Changes have been made to the profile that have not yet been published! | |||
| Partially installed | Not all sub profiles were able to be installed | |||
Profile information | ||||
| Type | Profile type (see below) | |||
| Roles | Roles | |||
| Users | User | |||
| Devices | Devices | |||
| tags | Tags | |||
| Parts | Listing of the sub-profiles that make up the complete Mobile Security Profile. | |||
Copy & paste of profiles
| ||||
| Click on the logo of the profile tile to mark one or more profiles In the general options, another field now appears under the filter mask: | ||||
| Action for selected items | Execute the selected action with Ok | |||
| Copies one or more selected profiles to the clipboard | ||||
| Deletes one or more selected profiles notemptyNew as of: 2.5 Android Profile, die mind. ein zugewiesenes Gerät haben, können nicht gelöscht werden.
| ||||
| Paste | Inserts a copy of a profile from the clipboard
| |||
Android Enterprise Profile
GeneralGeneral | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Caption | Value | Description | 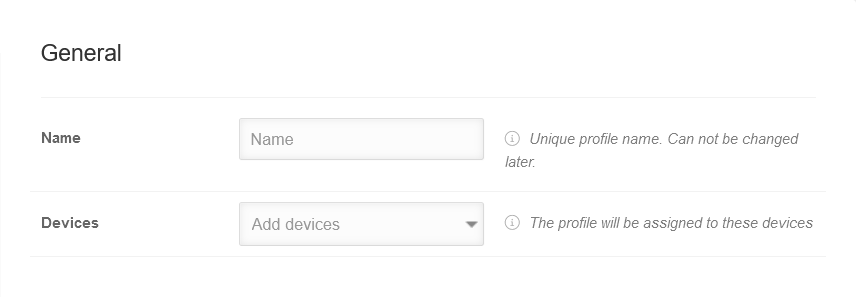 | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Name | Name | Displays or enter the profile name | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Devices | Add devices | For existing profiles: if available, display of the assigned devices | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Save | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Basic settingsBasic settings | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| notemptyThe settings shown here are examples that provide a most comprehensive basic protection. Adjustment to local requirements must be carried out! | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Caption | Value | Description | 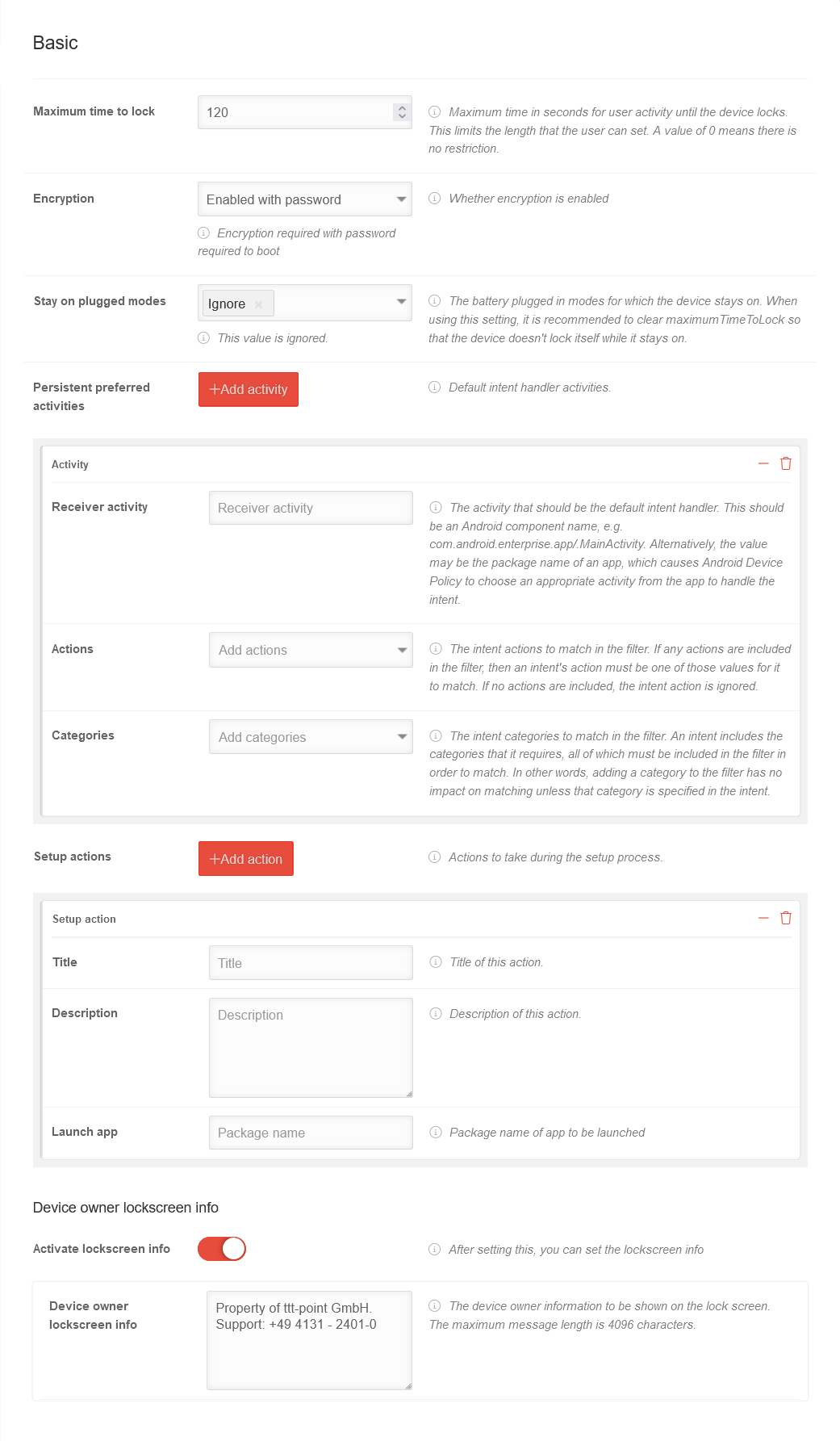 | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Maximum time to lock | 120 | This setting allows you to limit the maximum screen lock time that can be selected. The default setting is 10 minutes. (=600 sec.). | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Encryption | Enable with password | Requires a password before starting the device to override encryption. Encryption takes place at the file system level and prevents data from being read when physically accessing a locked device (turned off or not booted yet). It prevents 'not reading data from an unlocked device. Activating this option also deactivates the possibility to restart the device in "safe mode". In addition, a pin or password with the option "Safe start" is required as display lock. This means that the pin or password must be entered before the device is started. This means that no calls, messages or notifications (including wake-up calls) can be received before the device is unlocked and started. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Stay on plugged modes | Ignore Select modes | The battery charge mode should have no effect on whether the device remains switched on. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Sustained preferred activities | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Sustained preferred activities | Add activity | Opens the section for setting the default intent handler activities | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Receiver activity | Receiver activity | Enter the activity that should be the default intent handler. Either the Android component name (com.android.enterprise.app/.MainActivity) or the app package name. Android device policy selects an appropriate activity from the app. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Actions | Add action | Select the intentional actions to be matched in the filter. If no action is selected, the intentional action will be ignored. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Categories | Add categories | Select the intent categories to match in the filter. An intent contains the required categories, all of which must be included in the filter to match. In other words, adding a category to the filter will not affect the match unless that category is specified in the intent. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Setup actions | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Setup actions | Add action | Opens the section for setting the actions to be performed during the installation process | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Titel | Titel | Enter the title, name of the action | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Description | Description | A description of the action | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Launch the app | Package name | Package name of the app to be launched during setup | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Device Owner lockscreen info | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Activate lockscreen info | Information is to be displayed in the lock screen. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Device Owner lockscreen info | Property of ttt-point GmbH. Support: +49 4131 - 2401-0 |
The device owner information to be displayed on the lock screen. The maximum message length is 4096 characters. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Save | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
RestrictionsRestrictions | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Caption | Value | Description | 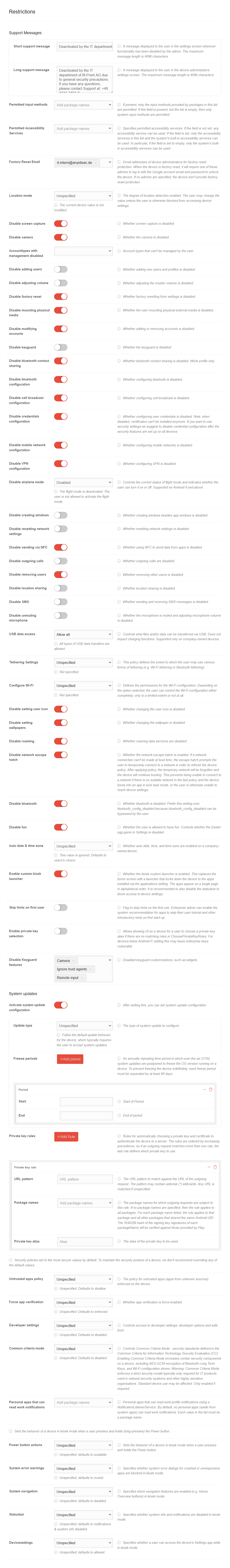 | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Support Messages | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
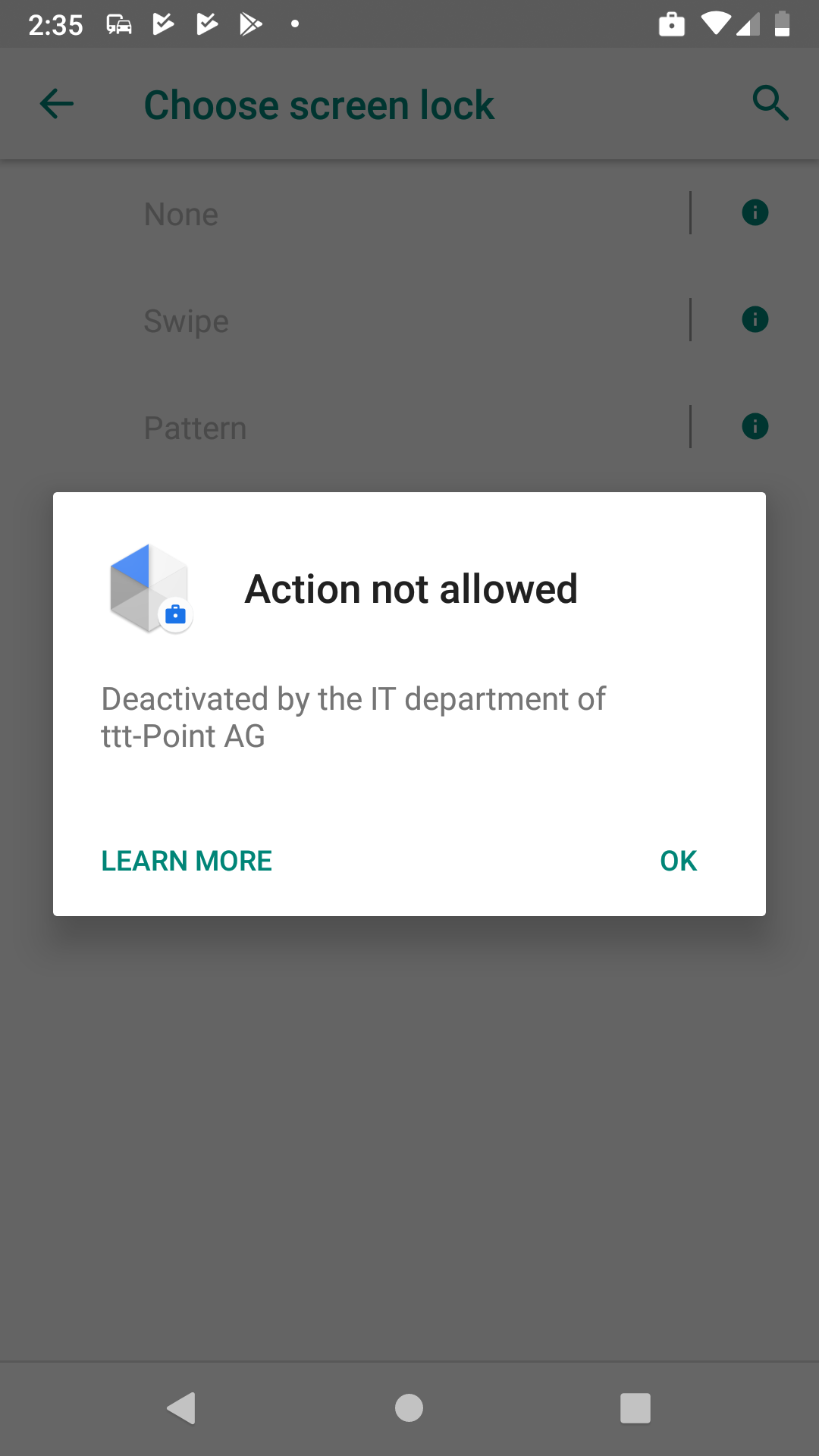
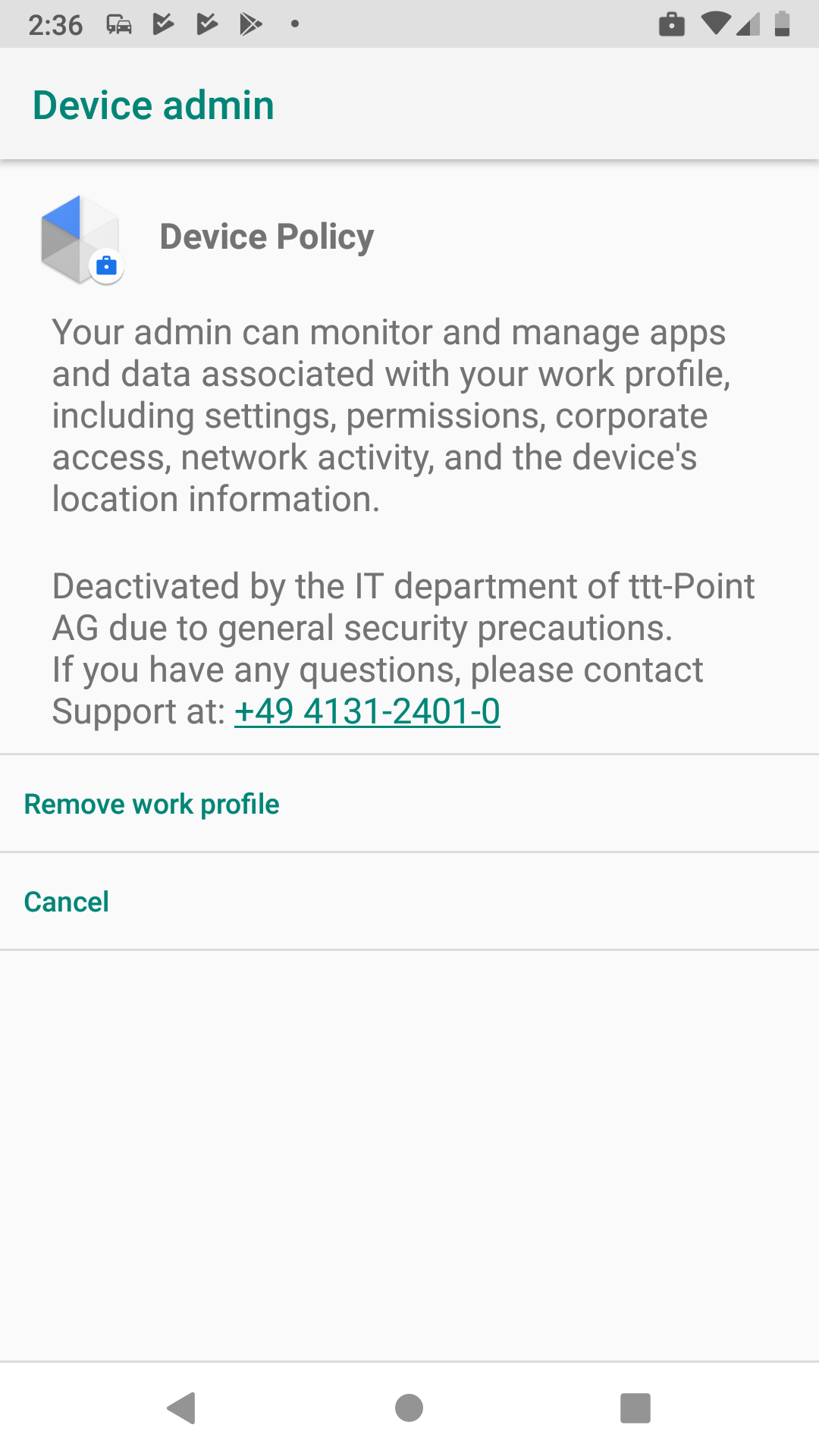
| Short support message | Deactivated by the IT department of ttt-Point AG | A message that is displayed to the user on the settings screen when the functionality has been disabled by the administrator. The maximum message length is 4096 characters. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Long support message | Deactivated by the IT department of ttt-Point AG due to general security precautions. If you have any questions, please contact Support at: +49 4131-2401-0 | A message displayed to the user. The maximum message length is 4096 characters. See figure above. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Permitted input methods | Add package name | If available, only the input methods provided by packages in this list are allowed. If this field exists, but the list is empty, only system input methods are allowed. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Approved input support services | Add package name | Specifies the allowed input accessibility services. If the field is not set, any input accessibility service can be used. When the field is set, only the input assistance services included in this list and the input assistance services integrated in the system can be used. In particular, if the field is empty, only the system's built-in input accessibility services can be used. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Accounts to unlock after factory reset | it-intern@anyideas.de | Factory Reset Protection (FRP). Email addresses of device administrators to protect against resetting to factory defaults. When the device is reset to factory defaults, one of these administrators must log in with the Google Account email address and password to unlock the device. If no administrators are specified, the device provides no protection against resetting to factory defaults. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Location mode | Unspecified |
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Disable screen capture | In order to provide data protection, it should not be possible to take screenshots. This also includes blocking screen sharing applications and similar applications (e.g. Google Assistant) that use the system's screenshot functions. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Disable camera | The camera should be deactivated by default. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Account types with management disabled | Account types that cannot be managed by the user | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Disable adding users | Shows whether adding new users and profiles is disabled | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Disable the volume setting | Shows whether adjusting the main volume is disabled | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Deactivate factory reset | The reset to factory settings should be deactivated. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Disable mounting physical media | The mounting of external physical media by the user is to be deactivated. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Disable modifying accounts | Add or remove accounts should be disabled.notemptyIf this item is not enabled, the user can create another Google Account, log into the Playstore and install any software. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Deactivate key lock | Indicates whether the key lock is deactivated | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Disable Bluetooth contact sharing | No contact data should leave the device via Bluetooth. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Disable Bluetooth configuration | The Bluetooth configuration should be deactivated. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Disable cell broadcast configuration | The configuration of Cell Broadcast should be disabled. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Disable credentials configuration | The configuration of user credentials should be disabled. notemptyIf disabled, certificates can no longer be installed. If these security settings are to be used, it is recommended to deactivate the configuration of the login credentials only after the security settings have been implemented on all devices. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Disable mobile network configuration | The configuration of mobile radio networks should be disabled. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Disable VPN configuration | The configuration of VPN should be disabled. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Disable airplane mode | Disabled | Controls the current status of flight mode and indicates whether the user can turn it on or off. notemptyAvailable from Android 9 or higher
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Disable creating windows | Specifies whether creating windows next to app windows is disabled. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Disable resetting network settings | Indicates whether network settings reset is disabled. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Disable sending via NFC | The use of NFC to transfer data from apps should be disabled. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Disable outgoing calls | Indicates whether outgoing calls are disabled. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Disable the removal of users | Shows whether the removal of other users is disabled. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Disable location sharing | Indicates whether location sharing is disabled. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Disable SMS | Shows whether sending and receiving SMS messages is disabled. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Prevent microphone from being switched on | Shows whether the microphone is muted and the microphone volume cannot be adjusted. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| USB data access notemptyNew as of:1.24 | Allow all | Controls what files and/or data can be transferred via USB. notemptyDoes not impact charging functions. notemptySupported only on company-owned devices.
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Tethering settings notemptyUpdated | Unspecified | The configuration of tethering (e.g. WLAN tethering or Bluetooth tethering) can be restricted. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Configure WLAN notemptyUpdated | Unspecified | Configuration of WLAN networks by users | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Disable setting user icon | Indicates whether changing the user icon is disabled. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Disable the background settings | Shows whether changing the background image is disabled. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Disable roaming | Indicates whether roaming data services are disabled. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Disable the Network Escape Hatch | Indicates whether the Network Escape Hatch is enabled. If a network connection cannot be established at boot time, the Escape Hatch prompts the user to temporarily connect to a network to update the device policy. After applying the policy, the temporary network is forgotten and the device continues booting. This prevents not being able to connect to a network if there is no suitable network in the last policy and the device launches an app in task lock mode or the user cannot otherwise reach the device settings. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Disable Bluetooth | Shows whether Bluetooth is disabled. This setting is preferable to Bluetooth Configuration because Bluetooth Configuration can be bypassed by the user. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Disable easter eggs | Whether the user is allowed to have fun. Controls whether the easter egg game is disabled in the settings. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Automatic date & time zone | Unspecified | Indicates whether automatic date, time, and time zone are enabled on a company-owned device.
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Activate the custom kiosk launcher | Indicates whether the custom kiosk launcher is enabled. This replaces the home screen with a launcher that locks the device to the apps installed via the application setting. The apps are displayed on a single page in alphabetical order. It is recommended to disable the status bar to block access to the device settings. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Skip hints on first user | Flag to skip first time use hints. The company administrator can enable the system recommendation for apps to skip the user tutorial and other introductory notes on first launch. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Enable private key selection | Allows the user interface to be displayed on a device so that a user can select a private key alias if there are no matching rules in ChoosePrivateKeyRules. For Android P devices, this setting can attack company keys. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Disable keyguard | Camera Ignore trust agents Remote input | Functions that are not available to the user in the lock screen. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| System Update | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Activate the status message | After you have activated this, you can set the system update configuration. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Update type | Unspecified | The type of system update to configure.
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Start Only with update type in window |
0 | If the type is windowed, the start of the maintenance window, measured as the number of minutes after midnight in the device's local time. This value must be between 0 and 1439, inclusive. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| End Only with update type in window |
0 | If the type is WINDOWED, the end of the maintenance window, measured as the number of minutes after midnight in device's local time. This value must be between 0 and 1439, inclusive. If this value is less than start_minutes, then the maintenance window spans midnight. If the maintenance window specified is smaller than 30 minutes, the actual window is extended to 30 minutes beyond the start time. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Freeze periods | Add period | An annually recurring period of time when over-the-air (OTA) system updates are pushed to freeze the operating system version running on a device. To prevent the device from freezing indefinitely, each freeze period must be at least 60 days apart. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Start | Start of the period | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| End | End of period | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Rules for private keys | Add rule | Rules for automatically selecting a private key and certificate to authenticate the device to a server. The rules are ordered by priority. Thus, if an outgoing request matches more than one rule, the last rule defines which private key to use. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| URL-pattern | URL-pattern | The URL pattern to match with the URL of the outgoing request. The pattern may contain wildcards with asterisks (*). Any URL matches if it is not specified. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Package names | Paketnamen hinzufügen | The package names for which outgoing requests are subject to this rule. If no package names are specified, the rule applies to all packages. For each listed package name, the rule applies to that package and all other packages that used the same Android UID. The SHA256 hash of the signature key signatures of each package name is compared to those provided by Play. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Alias for private key | Alias | Der Alias des zu verwendenden privaten Schlüssels. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Untrusted apps policy | Unspecified | The policy for untrusted apps (apps from unknown sources) enforced on the device.
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Force app verification through 'Google Play Protect' | Unspecified | Specifies whether app verification is enforced by 'Google Play Protect'.
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Developer settings | Unspecified | Controls access to developer settings: Developer Options and Safe Launch.
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Common Criteria mode | Unspecified | Controls Common Criteria mode - security standards defined in the Common Criteria for Information Technology Security Evaluation (CC). Enabling Common Criteria mode increases certain security components on a device, including AES-GCM encryption of Bluetooth long keys and Wi-Fi configuration warning: Common Criteria mode enforces a strict security model that is normally only required for IT products used in national security systems and other highly sensitive organizations. The use of standard devices may be affected. Activate only when required.
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Personal apps that can read work notifications | Add package name | Personal apps that can read work profile notifications with a NotificationListenerService. By default, no personal apps (except system apps) can read work notifications. Each value in the list must be a package name. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Power-Button-Actions | Unspecified | Sets the behavior of a device in kiosk mode when a user presses and holds the On / Off button.
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| System error warnings | Unspecified | Specifies whether to block system error dialogs for crashed or unresponsive apps in kiosk mode.
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| System navigation | Unspecified | Indicates which navigation functions are enabled in kiosk mode (e.g. Home, overview keys).
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Status bar | Unspecified | Specifies whether system information and notifications are disabled in kiosk mode.
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Device Settings | Unspecified | Indicates whether reporting is enabled for device settings.
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Save | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Personal usePersonal use | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Caption | Value | Description | 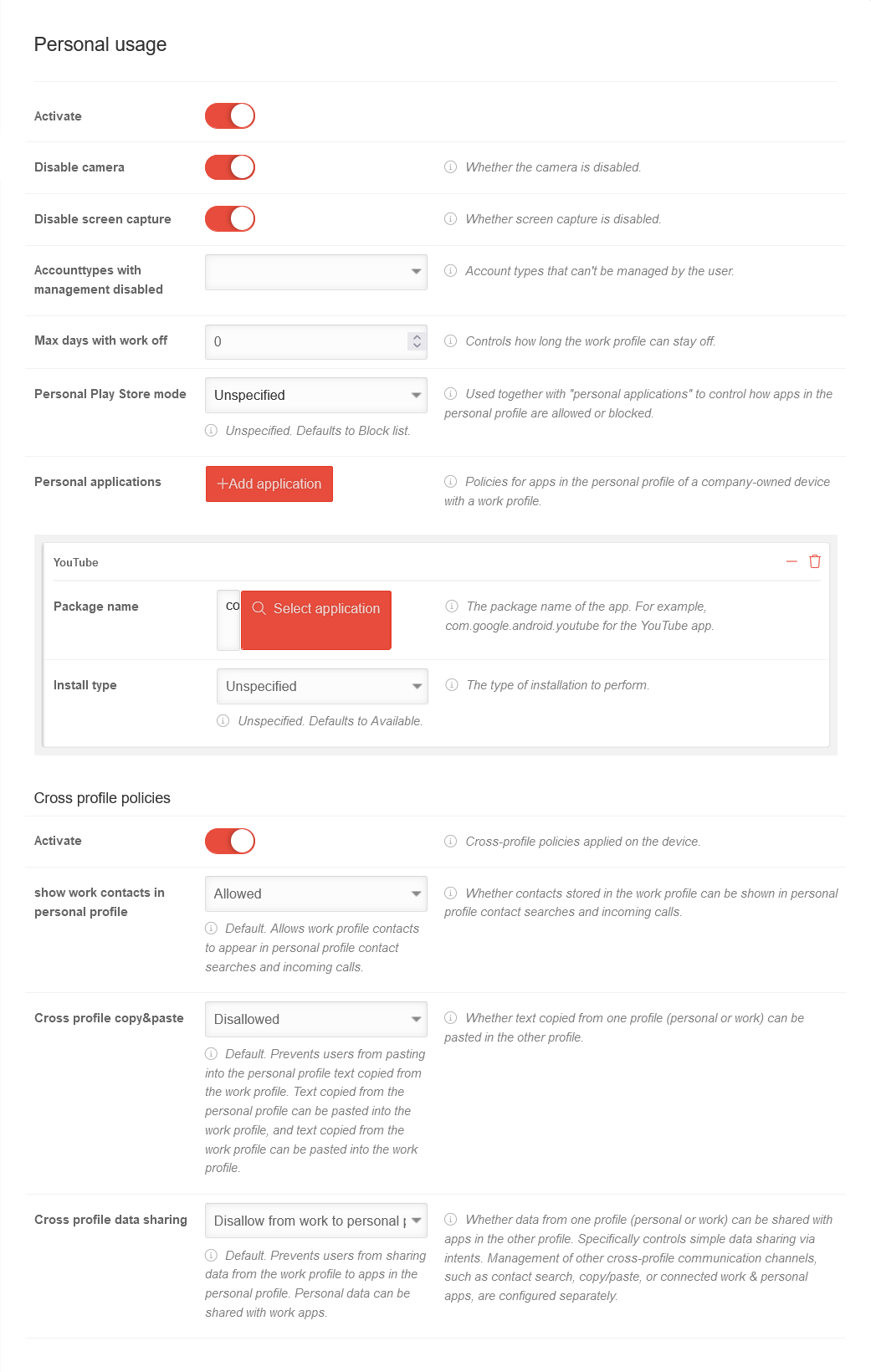 | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Activate | Activation allows you to configure the personal use of the Android device. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Disable camera | The camera should be deactivated by default. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Disable screen capture | In order to provide data protection, it should not be possible to take screenshots. This also includes blocking screen sharing applications and similar applications (e.g. Google Assistant) that use the system's screenshot functions. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Account types with management disabled | Account types that cannot be managed by the user | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Max. days without work | 0 | Controls how long the work profile can remain off. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Personal Play Store mode | Unspecified | Used together with "Personal apps" to control how apps are allowed or blocked in the personal profile.
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Personal applications | Add applications | Guidelines for apps in the personal profile of a company-owned device with a work profile. Each click on the button adds a section Application by customizing an app. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Package name | com.google.android.youtube Select application | The package name of the VPN app. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Install type Only appears when an app is selected in Package name. |
Unspecified | The way the installation is performed.
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Cross-profile guidelines | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Activate | Cross-profile policies applied to the device. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Show work contacts in personal profile | Allowed | Whether contacts stored in the work profile can be displayed in the contact search in the personal profile and on incoming calls.
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Cross-profile copy & paste | Not allowed | Whether text copied from one profile (personal or business) can be pasted into the other profile.
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Cross-profile data sharing | Refuse from business to personal profile | Whether data from one profile (personal or business) can be shared with apps in the other profile. Specifically controls simple data sharing via intents. Management of other cross-profile communication channels, such as contact search, copy/paste or connected work & personal apps, are configured separately.
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Save | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
PasscodePasscode | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Caption | Value | Description | 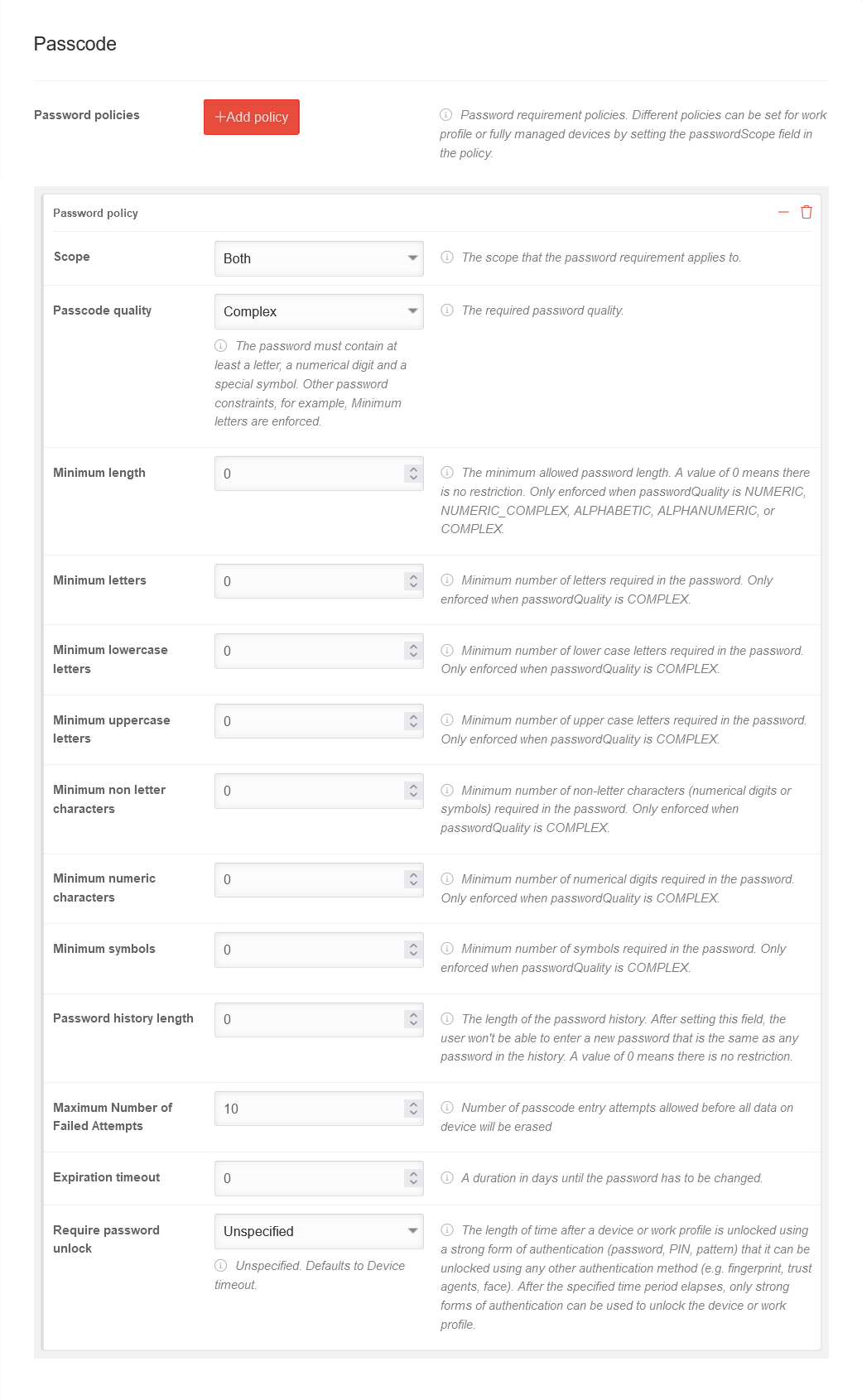 | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Password policies | Add policy | Password policies can be used for work profiles and fully managed devices. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Scope | The scope that the password requirement applies to. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Device | The policy applies only to fully managed devices | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Work Profile | The policy only applies to work profiles | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Both | The policy applies to fully managed devices as well as devices with a work profile. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Passcode quality | Complex | The required password quality.
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Minimum length | 0 | The minimum allowed password length. A value of 0 means there is no restriction. Only enforced when Passcode quality is Numeric, Numeric (Complex), Alphabetic, Alphanumeric, or Complex. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Minimum letters | 0 | Minimum number of letters in the password Forced only if the Password quality is Complex. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Minimum lowercase letters | 0 | Minimum number of lowercase letters required in the password Forced only if the Password quality is Complex. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Minimum uppercase letters | 0 | Minimum number of capital letters in the password Forced only if the Password quality is Complex. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Minimum non letter characters | 0 | Minimum number of non-letters (numeric digits or symbols) required in the password. Forced only if the Password quality is Complex. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Minimum numeric characters | 0 | Minimum number of digits in the password Forced only if the Password quality is Complex. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Minimum symbols | 0 | Minimum number of symbols in the password Forced only if the Password quality is Complex. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Password history length | 0 | The length of the password history. After setting this field, the user won't be able to enter a new password that is the same as any password in the history. A value of 0 means there is no restriction. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Maximum failed attempts | 10 | Number of permitted input attempts before all data on the device is deleted. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Validity | 0 | A duration in days until the password must be changed. A value of 0 means that the password never needs to be changed. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Password unlock required | The amount of time after a device or work profile is unlocked using a strong form of authentication (password, PIN, pattern) that can be unlocked using another authentication method (e.g., fingerprint, trusted agent, face). After the specified period, only strong authentication forms can be used to unlock the device or work profile. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Unspecified | Not specified. By default, the device-timeout is used. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Device-timeout | The timeout is set to the default setting of the device. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Daily | The timeout is 24 hours. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Save | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
ApplicationsApplications | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| notemptyThe settings shown here are examples that provide a most comprehensive basic protection. Adjustment to local requirements must be carried out! | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Caption | Value | Description | 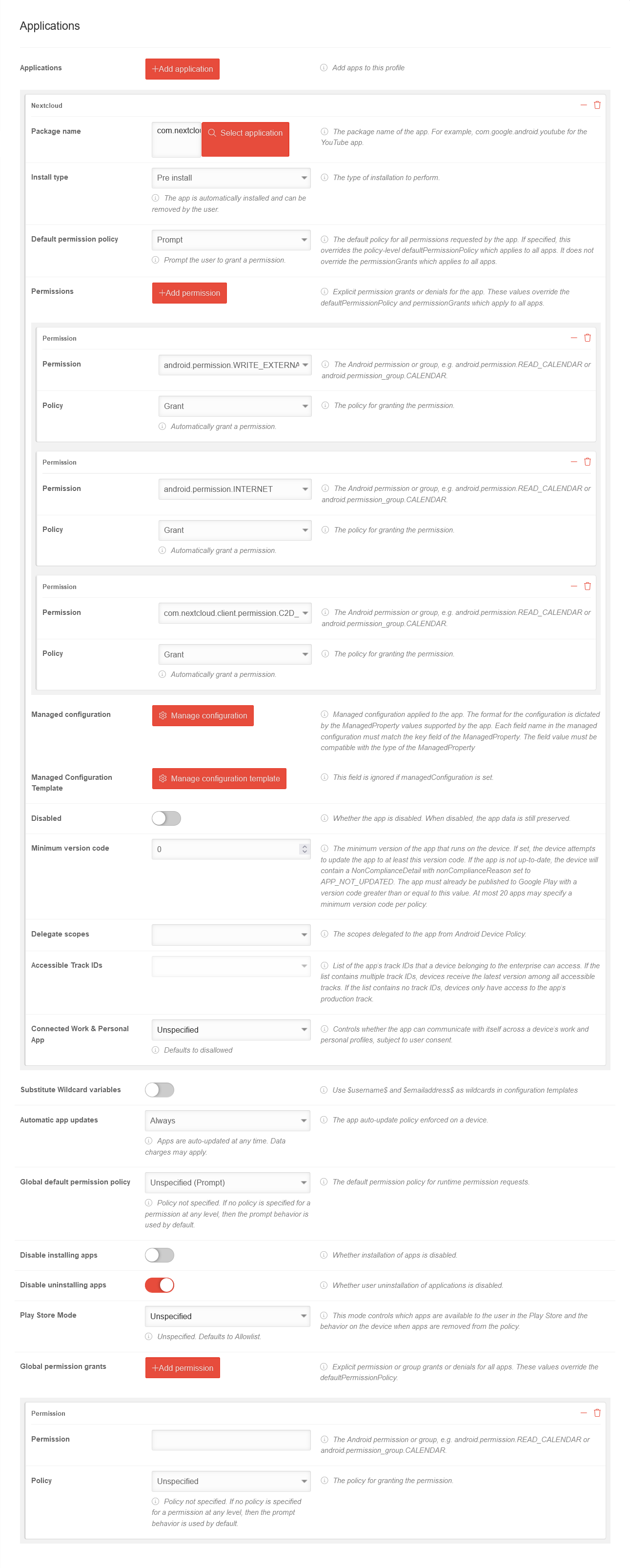 | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Applications | Add applications | Adds apps to this profile notemptyApps on EMM-managed devices are configured within the profiles! | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Package name | com.google.android.youtube Select application | The package name of the VPN app. For our example: Nextcloud If a message appears next to the app logo, certain values can be passed to the app. (Not available on Nextcloud) See Manage configuration template | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Save | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Install type | Pre install | The way the installation is performed.
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Default permission policy | Prompt | The default policy for all permissions requested by the app. If set, overrides the default policy-level permission policy that applies to all apps. It does not override the global permission grant, which applies to all apps.
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Permissions | Add permission | Grants explicit permission or denial for the app. These values override the default permission policy and global permission restrictions that apply to all apps. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Permission | android.permission.WRITE_EXTERNAL_STORAGE | The app needs access to the memory (this means internal memory and an additional SD card). | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Policy | Grant | The policy for granting authorization. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Permission | android.permission.INTERNET | The app should get access to existing internet connections. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Policy | Grant | The policy for granting authorization. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Permission | com.nextcloud.client.permission.C2D_MASSAGE | The app should be able to receive push messages via Firebase Cloud Messaging (formerly Google Cloud Massage) (Cloud to Device → C2D) | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Policy | Grant | The policy for granting authorization. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| If necessary, further authorizations must be granted or denied here. Note: In the »Approval« field, only the authorizations that the respective app requires and is usually required for proper operation appear. It is recommended to grant necessary permissions in advance and to allow all other permissions only on request (prompt). The »deny« option should only be used for selected authorizations where it is clear that the desired function of the app is not affected by this. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Managed configuration | Manage configuration | Managed configuration applied to the app. The format for the configuration depends on the ManagedProperty values supported by the app. Each field name in the managed configuration must match the key field of the managed property. The field value must be compatible with the ManagedProperty type. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Managed Configuration Template | Manage configuration template | This field is ignored if the managed configuration is set. Calls up a template from the app manufacturer in which various parameters can be transferred to the app, depending on what the manufacturer specifies. These can be fixed parameters and variables in email apps:
The values are taken from the user settings of the user to whom the respective device is assigned
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Disabled | Whether the app is disabled. When deactivated, the app data is still retained. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Minimum version code | 0 | The minimum version of the app that will run on the device. If set, the device will attempt to update the app to at least this version code. If the app is not up to date, the device contains a non-compliance detail with the non-compliance reason APP_NOT_UPDATED. The app must already be published in Google Play with a version code greater than or equal to this value. A maximum of 20 apps can set a minimum version code per policy. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Delegate areas | The permissions selected here are delegated to the app by the Device Policy Controller.
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Accessible Track IDs | List of track IDs of the app that an enterprise device can access. If the list contains multiple track IDs, devices get the latest version among all accessible tracks. If the list does not contain any track IDs, devices have access only to the production track of the app. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Connected Work & Personal App | Unspecified | Controls whether the app can communicate with itself through a device's work and personal profiles with the user's permission.
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Substitute Wildcard variables | (Default) | If activated , the content of the variables $username$ and $emailaddress$ is read from the user settings of the user to whom the respective device is assigned. A click box will appear in which all Users to which this function is to be applied must be selected. If the button is deactivated again, the generated user profiles become editable profiles. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Automatic App Updates | Always | The policy enforced on a device to automatically update apps depending on the network connection: Apps should also be updated on devices that rarely or never return to a wireless network. The volume of data usually has little effect with standard volume tariffs.
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Global default authorization policy | Not specified (prompt) | The default authorization policy for runtime authorization requests.
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Disable installation of apps | notemptyIf activated, no installations or Updates are possible. Also not via the portal! | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Disable uninstalling apps | The user should not be able to uninstall any apps. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| App Tracks | The app track that the device can access with the policy. The device receives the latest version of all available tracks. If no tracks are specified, the device uses only the production track.
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Play Store Mode | Allow list | Only apps that are configured here in the policy are available. Any app not included in this policy will be automatically uninstalled from the device. Blocklist means All apps in the Play Store are available, except for those configured here with Installation Type Block! | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Global permission granting | Add permission | Explicit permission or group grant or deny for all apps. These values override the Default permission policy. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Permission | The Android permission or group, for example android.permission.READ_CALENDAR or android.permission_group.CALENDAR. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Policy | Unspecified | The policy for granting authorization.
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Save | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
NetworksNetworks | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Caption | Value | Description | 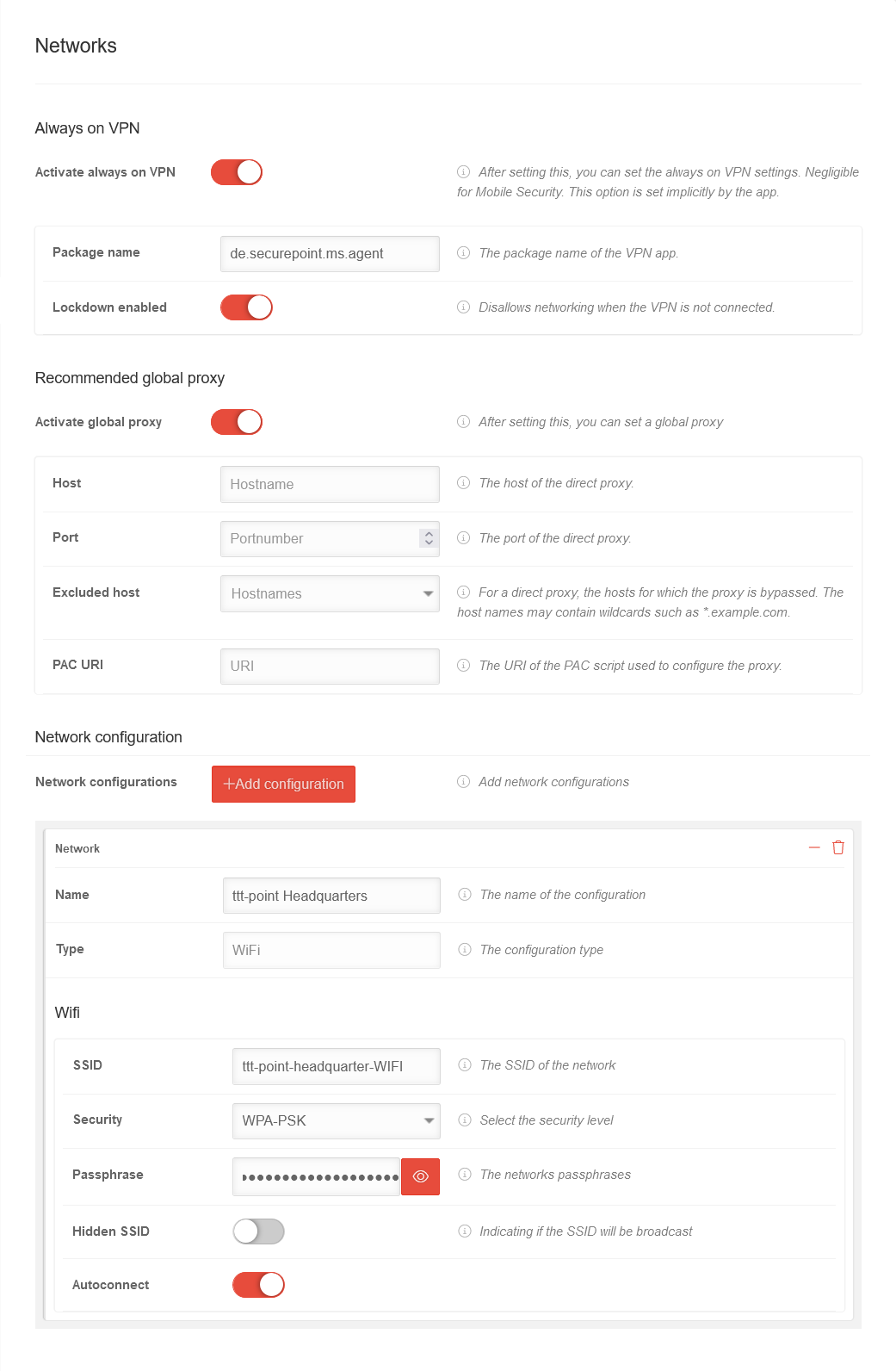 | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Always on VPN | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Enable "Always-On-VPN" | Always sets up a VPN. Enables further settings | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Package name | de.securepoint.ms.agent | The package name of the VPN app. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Lockdown enabled | If the VPN is not connected, any network connection is prevented. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Recommended global proxy | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Activate the global proxy | After activation, a global proxy can be set. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Host | Host name | The host of the direct proxy. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Port | Port number | The port of the direct proxy. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Excluded host | Host names | For a direct proxy, the hosts for which the proxy is bypassed. The host names can contain wildcards such as * .example.com. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| PAC URI | URI | The URI of the PAC script used to configure the proxy. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Network configuration | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Network configurations | Add configuration | Configuring Access Profiles for WiFi Networks | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Name | ttt-point Headquarters | The name of the configuration | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Type | WiFi | Profile type (see below) | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Wifi | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| SSID | ttt-point-headquarter-WIFI | The SSID of the network | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Security | WPA-PSK | High security level | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Password | •••••••••• | "Even if it sounds trivial: WIFI.MyCompany.123 or Location.HouseNumber are no secure passwords! Also 1234 and abcd or qwerty are not' really secure passwords!" | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Hidden SSID | Indicating if the SSID will be broadcast. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Autoconnect | The device should automatically connect to the network. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Save | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Status reportingStatus reporting | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Caption | Value | Description | 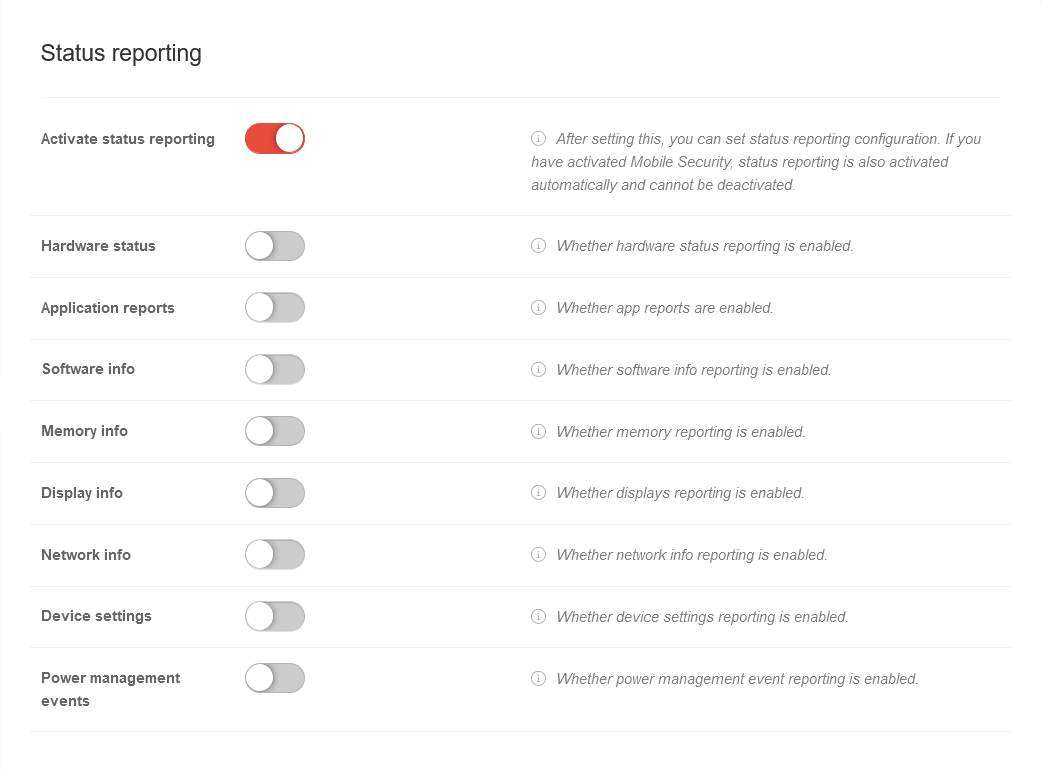 | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Activate the status message | After activation, the configuration of the status reports can be set. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Hardwarestatus | Indicates whether the hardware status message is enabled. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Application Reports | Indicates whether app reports are enabled. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Software information | Indicates whether software info reporting is enabled. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Working memory information | Indicates whether memory reporting is enabled. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Display information | Indicates whether the display of reports is enabled. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Network information | Indicates whether the network info message is enabled. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Device Settings | Indicates whether reporting is enabled for device settings. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Power Management Events | Indicates whether power management event reporting is enabled. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Save | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
ComplianceCompliance | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Rules can be defined for when the telephone or work profile is locked and when it is deleted (factory reset). The user is prompted to activate the selected policy on the device. Otherwise, the device / work profile will be blocked or set to factory defaults / deleted. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Caption | Value | Description | 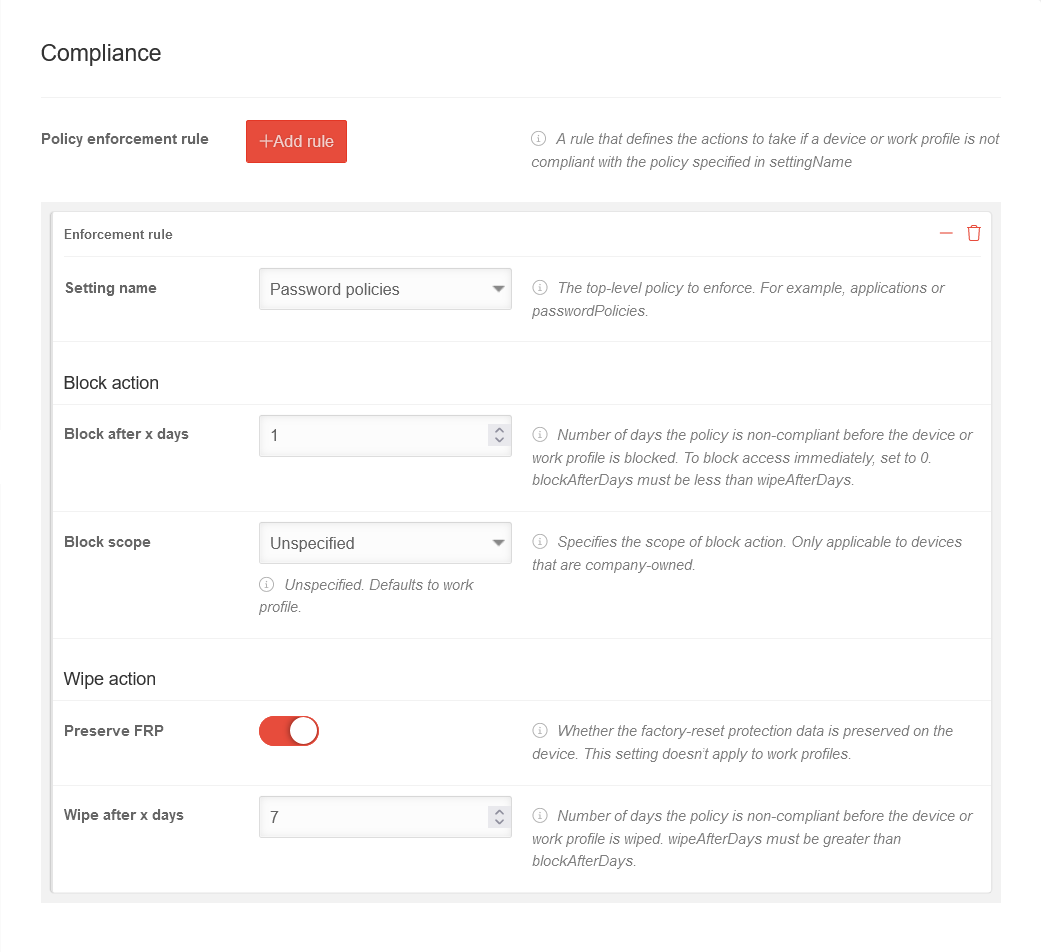 | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Rules for enforcing the profile | Add rule | A rule that defines the actions to be taken when a device or a work profile does not comply with the policy specified in "Setting name". | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Preference name | Password policy | The password policies must be applied to the phone. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Block | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Block after x days | 1 | Number of days on which the policy is not compliant before the device or work profile is blocked. To block access immediately, the value is set to 0. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Block scope | Unspecified | Specifies the scope of the blocking action. Applies only to devices owned by the company.
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Delete | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Get factory reset protection | If enabled, the factory settings reset protection is preserved in the profile. In the event of theft or loss, you must first log into your Google Account before the device can be reset to factory defaults. This setting does not work with work profiles. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Wipe after x days | 7 | Number of days before the device or work profile is deleted if the policy (here: password policies) has not been implemented on the device. Delete must be greater than Block. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Save | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
SecuritySecurity | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| notemptyThe Security tab is only available if a Mobile Security license is present. EMM licenses do not have VPN functionality that enables these security functions. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Caption | Value | Description | 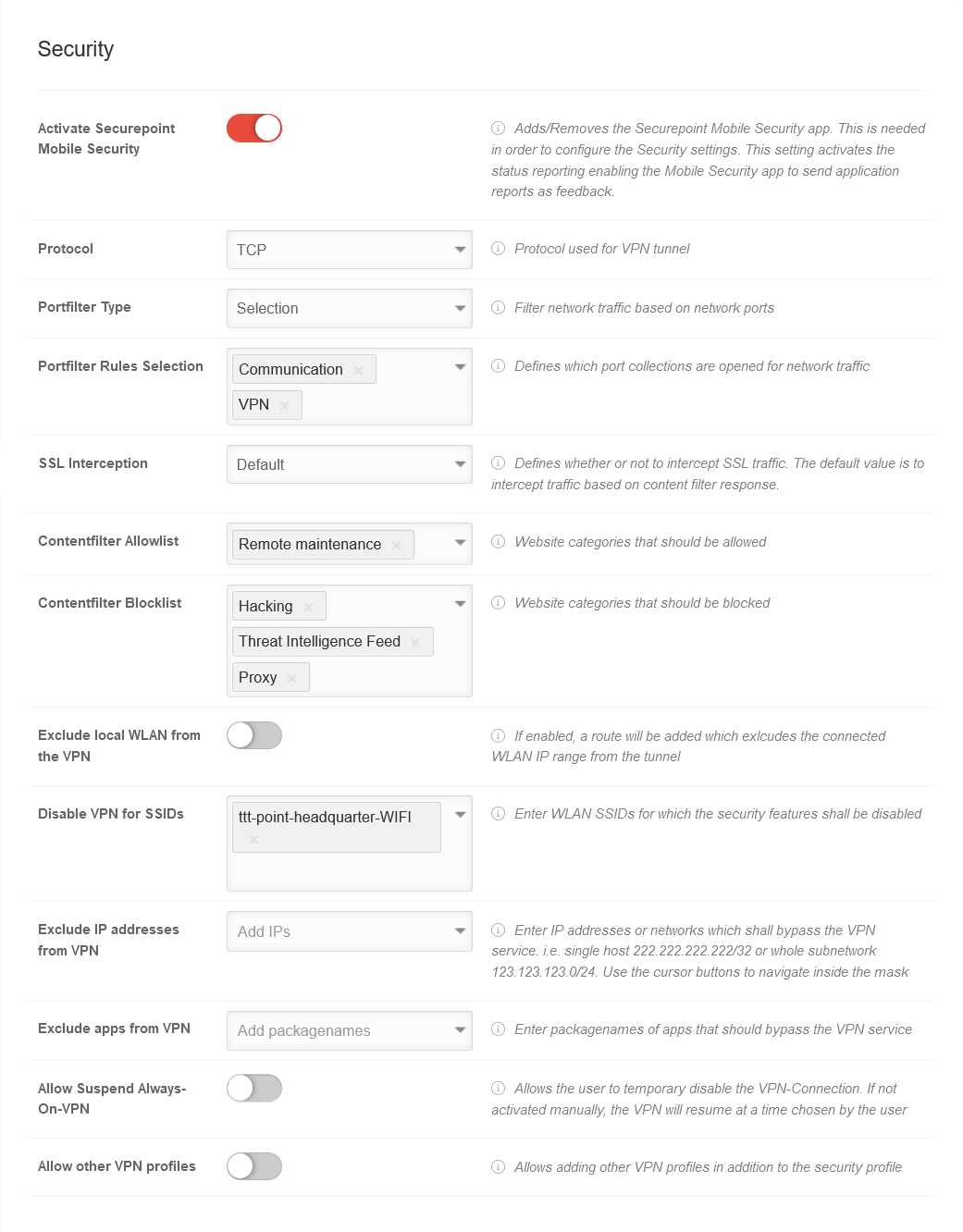 | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Activate Securepoint Mobile Security | With Activation, the Securepoint Mobile Security app is added or removed in the Applications tab and can be configured here. This is required to configure the security settings. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Protocol | TCP | The protocol TCP or UDP used for the VPN tunnel | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Portfilter Type | Selection | Filter network traffic based on network ports. Closed Open Selection | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Port filter rule selection Appears when Port filter type Selection is selected |
Communication VPN | Specify which port collections are open for network traffic
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| SSL-Interception | Default | SSL traffic from web pages listed in the content filter allowlist is not intercepted, other pages are checked using SSL interception. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Content-Filter Allowlist | Remote maintenance | Click box: Web pages that are to be added to a allowlist. Possible entries: Contentfilter | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Content-Filter Blocklist | Default-Values HackingProxyThreat Intelligence Feed | Click box: Websites that are to be added to a blocklist. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Exclude local WLAN from VPN | If enabled , a route is added that excludes the local WLAN IP range from the tunnel | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Disable VPN for SSIDs | ttt-point-headquarter-WiFi | Enter WiFi SSIDs for which the security features shall be disabled. | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Exclude IP addresses from VPN | Add IPs | Enter IP addresses or networks for which the security functions are to be bypassed, i.e. the individual host 222.222.222/32 or the entire subnet 123.123.123.0/24. Use the cursor keys to navigate within the mask | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Exclude apps from VPN | Add package name | Enter the package names of the apps that are to bypass the VPN service | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Allow Suspend Always-On-VPN | Allow Suspend Always-On-VPN | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Allow other VPN profiles | Adding other VPN profiles in addition to the Securepoint Security profile shall not be allowed. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Save | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
LocalizeLocalize | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Caption | Value | Description | 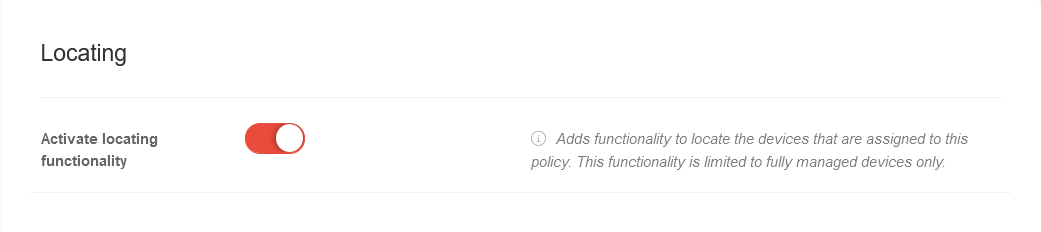 | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Enable localization function | Adds functionality to find the devices assigned to this policy. This functionality is limited to fully managed devices only. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Save | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
notemptyThe settings shown here are examples that provide a most comprehensive basic protection. Adjustment to local requirements must be carried out!