Last adaptation to the version: 14.1.1 (11.2025)
- BetaFor participants on the Beta Channel only:
- Creating additional configuration profiles is possible
Introduction
The proxy serves as an intermediary between the internet and the network to be protected.
The clients send their request to the proxy and the proxy passes it on to the corresponding servers.
The actual address of the client remains hidden from the server.
In this way, it is possible to check the data traffic for viruses and unwanted content.
Globales Profil
General
| Caption | Value | Description | UTMuser@firewall.name.fqdnApplicationsHTTP-Proxy 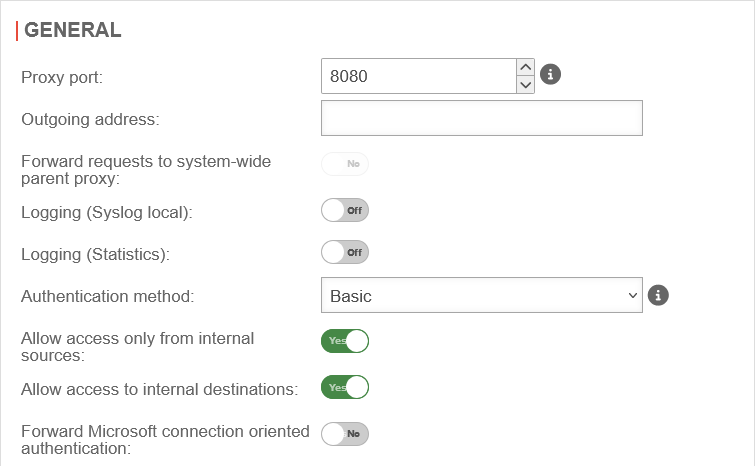 Area General Area General
|
|---|---|---|---|
| Proxy Port: | 8080 | Specifies on which port the proxy is to be addressed | |
| Outgoing Address: | The Outgoing Address is used for two scenarios:
In this example, the proxy is bound to the faster DSL line:
Connection to a web server in the VPN network:
| ||
| Forward requests to system-wide parent proxy: | No | If another proxy is used before the HTTP proxy, this function must be activated. The configuration takes place under | |
| Logging (Syslog lokal): | Off | Writes a general Syslog for the HTTP proxy (Open: Area Log | |
| Logging (Statistics): Only available if no anonymization for the HTTP proxy Settings at |
On | Writes a statistical Log call: Area HTTP proxy statistics | |
| Authentication method: | The proxy offers various possibilities for authentication. The possibilities are: | ||
| None | The HTTP proxy processes all requests without authentication | ||
| Basic | With basic authentication, the users are queried against the stored users under Area User on the firewall | ||
| NTLM / Kerberos | Here the firewall must be made known to the server. This can be set up in the web interface under | ||
| Radius | Here the firewall must be made known to the server. This can be set up in the web interface under | ||
| Allow access only from local sources: | Yes default |
Access to the HTTP proxy is now only possible from internal sources. These are:
| |
| Allow access to local destinations: | Yes default |
All internal networks can also be reached via the HTTP proxy (the packetfilter has already been passed through to reach the HTTP proxy). Disabling it prevents this and access to other internal networks must be explicitly allowed via the port filter without an HTTP proxy. | |
| Forward Microsoft connection-oriented authentication: | No | If it is enabled, login or authentication to websites is possible. For some websites this is not possible otherwise. With this option, NTLM, Negotiate and Kerberos authentications are forwarded If SSL-Interception is active, this parameter must be enabled for HTTPS-based authentications, otherwise no authentication/login is possible on these websites. | |
Authentication exceptions | |||
| Aktiviert | Off default |
Authentication exceptions are disabled by default.
If enabled: URLs listed here are accessed without prior authentication. |
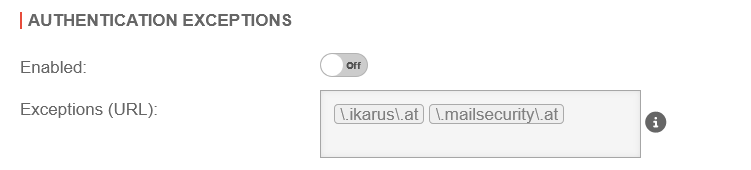 |
| Ausnahmen (URL): | \.ttt-point\.de | Wenn man die Authentifizierungsausnahmen aktiviert, dann kann man hier eigene Ausnahmen festlegen | |
Virusscan | |||
General | |||
|
Der Virenscanner im HTTP-Proxy kann Datenverkehr auf Viren prüfen. New as of v14.1.0 Die Funktion lässt sich per CLI deaktivieren oder aktivieren. Per Default ist die Funktion aktiviert. FastDiff Deaktivieren: extc value set { application ikarus variable ENABLE_FASTDIFF value 0 } FastDiff Aktivieren: extc value set { application ikarus variable ENABLE_FASTDIFF value 1 } FastDiff Status abfragen:extc value get { application ikarus variable ENABLE_FASTDIFF } application|variable |value -----------+---------------+----- ikarus |ENABLE_FASTDIFF|1 notempty New as of v14.1.0 Die Funktion lässt sich per CLI deaktivieren oder aktivieren. Per Default ist die Funktion aktiviert. SigQA Deaktivieren: extc value set { application ikarus variable ENABLE_SIGQA value 0 } SigQA Aktivieren: extc value set { application ikarus variable ENABLE_SIGQA value 1 } SigQA Status abfragen:extc value get { application ikarus variable ENABLE_SIGQA } application|variable |value -----------+------------+----- ikarus |ENABLE_SIGQA|1 | |||
| Virusscan: | On | The virus scanner is activated and the associated service is running (default setting) |
Datei:UTM v14.1.1 Anwendungen HTTP Proxy Virenscanner-en.png |
| On | The virus scanner service is deactivated. The HTTP proxy is not working correctly. The service can be started via the menu Virusscan | ||
| On | The virus scanner service is deactivated. The HTTP proxy is not working correctly.notempty On devices with less than 3GB RAM, the service for the virus scanner cannot start. Please change to current hardware or allocate more RAM! | ||
| Off | The virus scanner is deactivated. | ||
| Maximum scan size limit: | 2 Megabytes | Sets the size of the files to be scanned by the virus scanner | |
| Trickle Time: | 5 seconds | Interval at which data is transferred from the proxy to the browser so that the browser does not stop loading during the virus check | |
| Allowlist ICY-Protokoll: | Off | A web radio protocol that can be excluded from testing | |
| Cache Updates notempty New as of v12.7.2 |
Off | When activated On, the virus database updates are distributed to the connected clients with Securepoint Antivirus Pro after the initial download. In this way, traffic is reduced and the updates are rolled out smoothly. | |
| Mime type blocklist | application/x-shockwave-flash Example |
Mime types listed here are blocked in any case. The button opens a dialogue in which a mime type can be selected from a dop-down menu or an individual type can be entered. The MIME-Type detection is performed after the first few bytes of the file. Normally, this detection is accurate, and the blocklist is applied accordingly. Additionally, there is a rescan mechanism in place, which re-evaluates the MIME-Type specifically for Microsoft-Compound Storage Formate files. This rescan occurs once the full file is available or when the loaded portion of the file reaches the Virusscanner sizelimit.
| |
Allowlist | |||
| Aktiviert | Die Allowlist für MIME-Types und Webseiten ist standardmäßig aktiviert | ||
| Mime-Type Allowlist | application/pkcs10 Example |
Mime types listed here are not scanned. Standard defaults:
| |
|
Websites Allowlist »^[^:]*://download\.windowsupdate\.com/ |
Here it is possible to create your own filters based on Regular Expressions (Regex). notempty Viruses from these pages are not detected! Some update servers that cause problems when using a virus scanner are already preconfigured. Hint: Further exceptions are necessary so that iTunes can communicate correctly with the internet. | ||
Bandwidth | |||
| Bandwidth limiting policy: | None | Default | 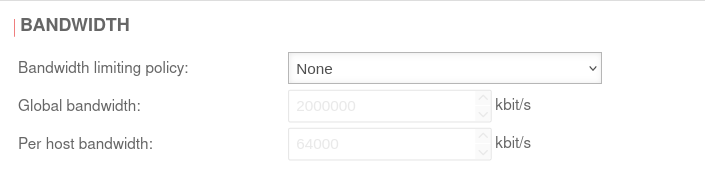 |
| Limit total bandwidth | In this case, the proxy only uses the specified maximum bandwidth and leaves the rest of the bandwidth untouched by your internet connection. (This bandwidth is shared by all hosts connected to the proxy.) | ||
| Per host bandwidth | Bandwidth for each host. The limited bandwidth for hosts cannot exceed the global bandwidth. | ||
| Global bandwidth: | 2.000.000 kbit/s | Default value, if activated | |
| Per host bandwidth: | 64.000 kbit/s | Default value, if activated | |
App Blocking | |||
| The general app blocking with fixed ports has been removed. Individual apps, or the ports they use, can be blocked flexibly via the packet filter. | |||
SSL-InterceptionWith the SSL interception feature, it is possible to recognise malicious code in SSL-encrypted data streams at the gateway. It interrupts the encrypted connections and makes the data packets visible to virus scanners and other filters. Data transmission to the client is then encrypted again. To do this, however, it is necessary to create a CA under and select this in the CA certificate field. | |||
| Caption | Value | Description | UTMuser@firewall.name.fqdnApplicationsHTTP-Proxy 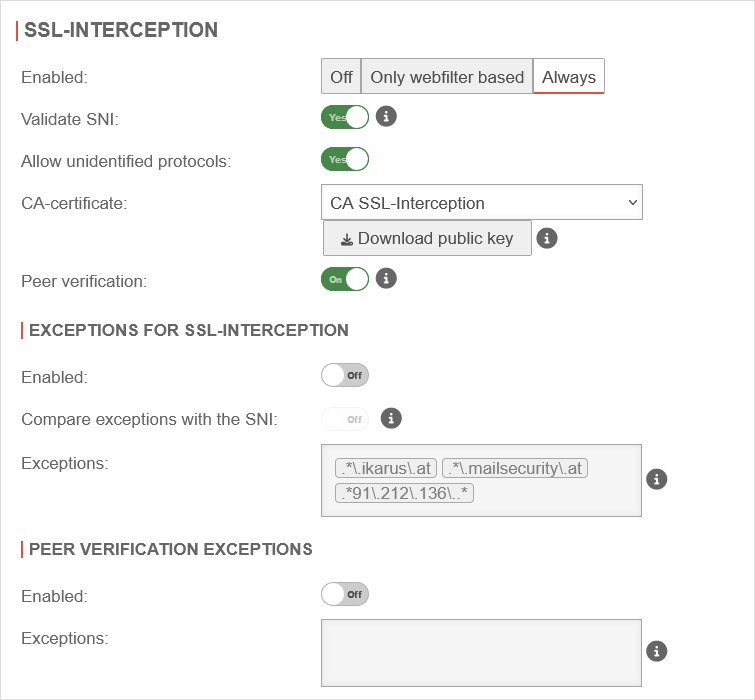 SSL Interception tab SSL Interception tab
|
| Enabled | The SSL-Interception is turned off | ||
| When enabled, only connections blocked by the web filter are intercepted. This avoids the problem that there are sites that do not tolerate an interruption of the encryption (e.g. banking software) without having to define an exception for it. | |||
| Activates the SSL interception | |||
| Validate SNI: |
Yes | When activated, any SNI in the ClientHello of the TLS handshake is checked. The host name contained is resolved and the addresses in the result are compared with the target address of the intercepted request. If they do not match, the connection is closed. Without Server Name Indication validation, clients can manipulate SNI arbitrarily to bypass the web filter. This setting should only be considered as a last resort when it seems impossible to standardize the DNS settings between the HTTP proxy and the UTM clients. If the client and UTM use different DNS servers, this can lead to false positives.
| |
| Allow non identified protocols: | Yes | If this switch is deactivated, unrecognized protocols are blocked. | |
| CA-Certificate: | CA-SSL-Interception | Here, a CA must be selected that can re-encrypt the connection after decryption (and scanning). The public key of the CA must be installed on all client computers that are to use SSL Interception. Download can be done here directly with . | |
| The public key should be installed on the clients that are going to use SSL interception to avoid certificate errors. | |||
| Peer verification: not for Only webfilter based |
On | This should definitely be enabled! With this, the HTTP proxy checks whether the certificate of the called page is trustworthy. Since the browser only sees the local certificate, a check by the browser is no longer possible. | |
Exceptions for SSL-Interception Exceptions for SSL-Interception not for Only webfilter based | |||
| Enabled | Off | It is possible to define exceptions in the format of Regular Expressions. However, since only https can arrive here, it is not filtered for protocols, unlike the virus scanner. New exceptions can be added directly in the input field. So an exception for www.securepoint.de would be:
.*\.securepoint\.de" | |
| Compare exceptions with the SNI: Only available if salidate SNI is active. |
Off | Applies Server Name Indication validation only to activated Exceptions of SSL-Interception . | |
| Ausnahmen: | .*\.ttt-point\.de Vordefiniert im Globalen Konfigurationsprofil: .*\.ikarus\.at.*\.mailsecurity\.at .*91\.212\.136\..* |
Ausnahmen bestimmen, hier für ttt-point.de | |
Peer verification exceptions Peer verification exceptions only if peer verification is active | |||
| Enabled | Off | Here exceptions for certificate verification in regex format can be added.
| |
Transparent Mode | |||
| Transparent Mode | On | Due to the transparent mode, the proxy is not visible to the clients, the client sees its internet connection (HTTP) as if no proxy was connected in front of it. Nevertheless, the entire HTTP stream goes through the proxy, which means that no settings have to be made on the client. However, there are the same possibilities to analyze / block / filter / manipulate the data stream as if a fixed proxy were used. Each network object or group of network objects that are to use the transparent proxy must be stored here. |
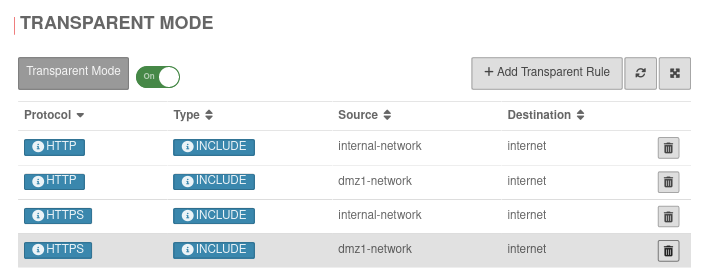 |
| Protocol: | HTTP or HTTPS |
Protocol that is used | UTMuser@firewall.name.fqdnApplicationsHTTP-ProxyGlobales Konfigurationsprofil bearbeiten 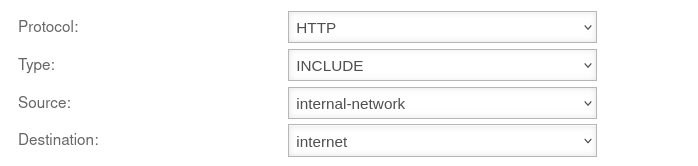 Adding a Transparent Rule Adding a Transparent Rule
|
| Type: | INCLUDE | The transparent mode is applied | |
| EXCLUDE | Transparent mode is not applied | ||
| Source: | internal-network | Source network object created under Area Network objects | |
| Destination: | internet | Destination network object | |
Konfigurationsprofil hinzufügen
notemptyGeneral
| Caption | Value | Description | UTMuser@firewall.name.fqdnApplicationsHTTP-Proxy 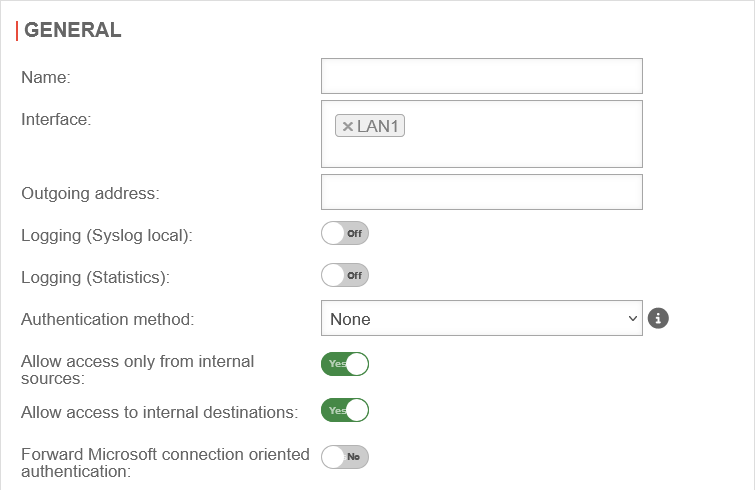 Der Bereich Allgemein in einem weiteren Konfigurationsprofil Der Bereich Allgemein in einem weiteren Konfigurationsprofil
|
|---|---|---|---|
| Name: | Konfigurationsprofil 2 | Angabe des Namens für das Konfigurationsprofil | |
| Interface | LAN1 | Dieses Konfigurationsprofil einer Schnittstelle zuweisen wie z. B. LAN1 | |
| Outgoing Address: | The Outgoing Address is used for two scenarios:
In this example, the proxy is bound to the faster DSL line:
Connection to a web server in the VPN network:
| ||
| Forward requests to system-wide parent proxy : Wird im globalen Konfigurationsprofil festgelegt |
No | ||
| Logging (Syslog lokal): | Off | Writes a general Syslog for the HTTP proxy (Open: Area Log | |
| Logging (Statistics): Only available if no anonymization for the HTTP proxy Settings at |
On | Writes a statistical Log call: Area HTTP proxy statistics | |
| Authentication method: | The proxy offers various possibilities for authentication. The possibilities are: | ||
| None | The HTTP proxy processes all requests without authentication | ||
| Basic | With basic authentication, the users are queried against the stored users under Area User on the firewall | ||
| NTLM / Kerberos | Here the firewall must be made known to the server. This can be set up in the web interface under | ||
| Radius | Here the firewall must be made known to the server. This can be set up in the web interface under | ||
| Allow access only from local sources: | Yes default |
Access to the HTTP proxy is now only possible from internal sources. These are:
| |
| Allow access to local destinations: | Yes default |
All internal networks can also be reached via the HTTP proxy (the packetfilter has already been passed through to reach the HTTP proxy). Disabling it prevents this and access to other internal networks must be explicitly allowed via the port filter without an HTTP proxy. | |
| Forward Microsoft connection-oriented authentication: | No | If it is enabled, login or authentication to websites is possible. For some websites this is not possible otherwise. With this option, NTLM, Negotiate and Kerberos authentications are forwarded If SSL-Interception is active, this parameter must be enabled for HTTPS-based authentications, otherwise no authentication/login is possible on these websites. | |
Authentication exceptions | |||
| Enabled | Off default |
Authentication exceptions are disabled by default.
If enabled: URLs listed here are accessed without prior authentication. |
 |
| Ausnahmen (URL): | \.ttt-point\.de | Wenn man die Authentifizierungsausnahmen aktiviert, dann kann man hier eigene Ausnahmen festlegen | |
Virusscan | |||
General | |||
|
Der Virenscanner im HTTP-Proxy kann Datenverkehr auf Viren prüfen. New as of v14.1.0 Die Funktion lässt sich per CLI deaktivieren oder aktivieren. Per Default ist die Funktion aktiviert. FastDiff Deaktivieren: extc value set { application ikarus variable ENABLE_FASTDIFF value 0 } FastDiff Aktivieren: extc value set { application ikarus variable ENABLE_FASTDIFF value 1 } FastDiff Status abfragen:extc value get { application ikarus variable ENABLE_FASTDIFF } application|variable |value -----------+---------------+----- ikarus |ENABLE_FASTDIFF|1 notempty New as of v14.1.0 Die Funktion lässt sich per CLI deaktivieren oder aktivieren. Per Default ist die Funktion aktiviert. SigQA Deaktivieren: extc value set { application ikarus variable ENABLE_SIGQA value 0 } SigQA Aktivieren: extc value set { application ikarus variable ENABLE_SIGQA value 1 } SigQA Status abfragen:extc value get { application ikarus variable ENABLE_SIGQA } application|variable |value -----------+------------+----- ikarus |ENABLE_SIGQA|1 | |||
| Virusscan: | Off | The virus scanner is deactivated, but the associated service is running (default setting) |
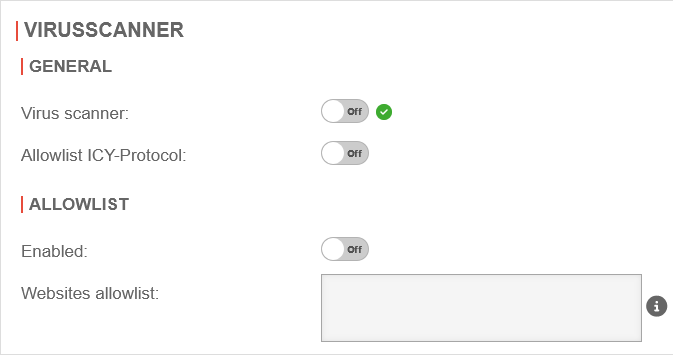 |
| On | The virus scanner is activated and the associated service is running | ||
| On | The virus scanner service is deactivated. The HTTP proxy is not working correctly. The service can be started via the menu Virusscan | ||
| On | The virus scanner service is deactivated. The HTTP proxy is not working correctly.notempty On devices with less than 3GB RAM, the service for the virus scanner cannot start. Please change to current hardware or allocate more RAM! | ||
| Off | The virus scanner is deactivated. | ||
| Maximum scan size limit: Wird im globalen Konfigurationsprofil festgelegt |
2 Megabytes | ||
| Trickle Time: Wird im globalen Konfigurationsprofil festgelegt |
5 seconds | ||
| Allowlist ICY-Protokoll: | Off | A web radio protocol that can be excluded from testing | |
Allowlist | |||
| Enabled | Die Allowlist für MIME-Types und Webseiten ist standardmäßig aktiviert | ||
| Mime-Type Allowlist Wird im globalen Konfigurationsprofil festgelegt |
application/pkcs10 Example |
||
|
Websites Allowlist »^[^:]*://download\.windowsupdate\.com/ |
Here it is possible to create your own filters based on Regular Expressions (Regex). notempty Viruses from these pages are not detected! Some update servers that cause problems when using a virus scanner are already preconfigured. Hint: Further exceptions are necessary so that iTunes can communicate correctly with the internet. | ||
| Cache Updates notempty New as of v12.7.2 Wird im globalen Konfigurationsprofil festgelegt |
Off | ||
Bandwidth | |||
| Bandwidth limiting policy: | None | Default |  |
| Limit total bandwidth | In this case, the proxy only uses the specified maximum bandwidth and leaves the rest of the bandwidth untouched by your internet connection. (This bandwidth is shared by all hosts connected to the proxy.) | ||
| Per host bandwidth | Bandwidth for each host. The limited bandwidth for hosts cannot exceed the global bandwidth. | ||
| Global bandwidth: | 2.000.000 kbit/s | Default value, if activated | |
| Per host bandwidth: | 64.000 kbit/s | Default value, if activated | |
App Blocking | |||
| The general app blocking with fixed ports has been removed. Individual apps, or the ports they use, can be blocked flexibly via the packet filter. | |||
SSL-InterceptionWith the SSL interception feature, it is possible to recognise malicious code in SSL-encrypted data streams at the gateway. It interrupts the encrypted connections and makes the data packets visible to virus scanners and other filters. Data transmission to the client is then encrypted again. To do this, however, it is necessary to create a CA under and select this in the CA certificate field. | |||
| Caption | Value | Description | UTMuser@firewall.name.fqdnApplicationsHTTP-Proxy 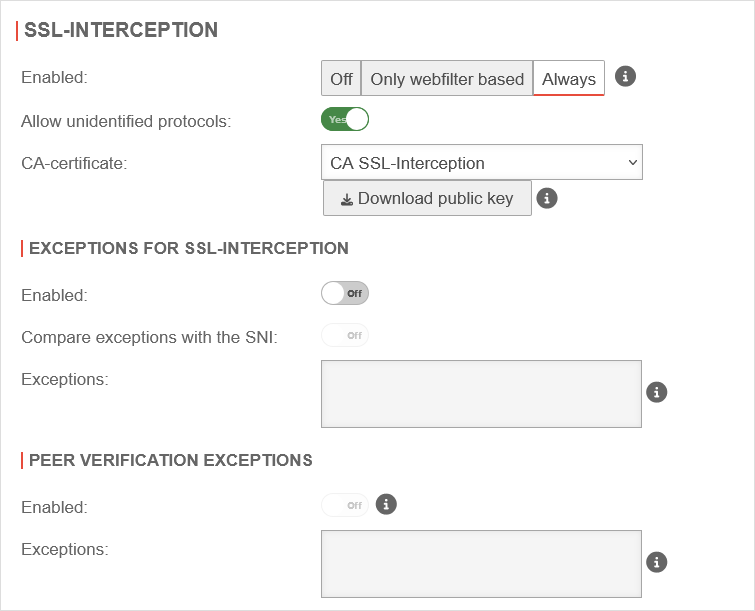 SSL Interception tab SSL Interception tab
|
| Enabled | The SSL-Interception is turned off | ||
| When enabled, only connections blocked by the web filter are intercepted. This avoids the problem that there are sites that do not tolerate an interruption of the encryption (e.g. banking software) without having to define an exception for it. | |||
| Activates the SSL interception | |||
| Validate SNI: Wird im globalen Konfigurationsprofil festgelegt |
Yes | When activated, any SNI in the ClientHello of the TLS handshake is checked. The host name contained is resolved and the addresses in the result are compared with the target address of the intercepted request. If they do not match, the connection is closed. Without Server Name Indication validation, clients can manipulate SNI arbitrarily to bypass the web filter. This setting should only be considered as a last resort when it seems impossible to standardize the DNS settings between the HTTP proxy and the UTM clients. If the client and UTM use different DNS servers, this can lead to false positives.
| |
| Allow non identified protocols: | Yes | If this switch is deactivated, unrecognized protocols are blocked. | |
| CA-Certificate: | CA-SSL-Interception | Here, a CA must be selected that can re-encrypt the connection after decryption (and scanning). The public key of the CA must be installed on all client computers that are to use SSL Interception. Download can be done here directly with . | |
| The public key should be installed on the clients that are going to use SSL interception to avoid certificate errors. | |||
| Peer verification: not for Only webfilter based Wird im globalen Konfigurationsprofil festgelegt |
On | This should definitely be enabled! With this, the HTTP proxy checks whether the certificate of the called page is trustworthy. Since the browser only sees the local certificate, a check by the browser is no longer possible. | |
Exceptions for SSL-Interception Exceptions for SSL-Interception not for Only webfilter based | |||
| Enabled | Off | It is possible to define exceptions in the format of Regular Expressions. However, since only https can arrive here, it is not filtered for protocols, unlike the virus scanner. New exceptions can be added directly in the input field. So an exception for www.securepoint.de would be:
.*\.securepoint\.de" | |
| Compare exceptions with the SNI: Only available if salidate SNI is active. |
Off | Applies Server Name Indication validation only to activated Exceptions of SSL-Interception . | |
| Ausnahmen: | .*\.ttt-point\.de Vordefiniert im Globalen Konfigurationsprofil: .*\.ikarus\.at.*\.mailsecurity\.at .*91\.212\.136\..* |
Ausnahmen bestimmen, hier für ttt-point.de | |
Peer verification exceptions Peer verification exceptions only if peer verification is active | |||
| Enabled | Off | Here exceptions for certificate verification in regex format can be added.
| |
Captive Portal
The Captive Portal is configured since v12.1 in its own menu under . There is a separate Wiki-article for this.


