Last adaptation to the version: 14.1.1 (11.2025)
- BetaFor participants on the Beta Channel only:
- HTTP proxy profiles added
- Updated to Redesign of the webinterface
Introduction
Why do the update servers of the respective antivirus software in the firewall's own virusscanner have to be added to the Allowlist?
When downloading virus signature updates, error detections may occur. Therefore, it is advisable to add the update servers of your AV vendor to the exception list.
Virusscanner exceptions | |||
| These exceptions are entered either in the global configuration profile or in another optional configuration profile. The virusscanner works with the following exceptions Regular expression. | |||
| Caption | Value | Description | UTMuser@firewall.name.fqdnAnwendungen  Ein Profil bearbeiten Ein Profil bearbeiten
|
|---|---|---|---|
| Edit | Click on the corresponding button to edit the desired profile. | ||
|
Virusscanner | |||
| Website-Allowlist | »^[^:]*://[^\.]*\.mailsecurity\.at/ | Entering exceptions as regular expressions | UTMuser@firewall.name.fqdnAnwendungenHTTP-Proxy 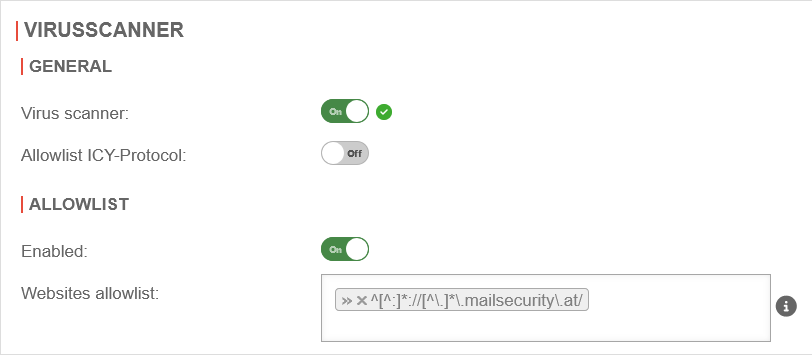 Eintragung von Ausnahmen Eintragung von Ausnahmen
|
Securepoint Antivirus Pro | |||
|
To do this, use the settings from the article HTTP Proxy and Securepoint Antivirus | |||
G Data | |||
| Website-Allowlist | »^[^:]*://[^\.]*\.gdatasecurity\.com/
»^[^:]*://[^\.]*\.gdata\.de/ »^[^:]*://[^\.]*\.gdatasecurity\.de/ »^[^:]*://[^\]*\.lumension\.com/ »^[^:]*://[^\.]*\.dedicated\.hosteurope\.de/ |
Entering regular expressions for G Data | |
G Data Outbreak Shield | |||
| Website-Allowlist | »^[^:]*://[^.]*.gdata\.ctmail\.com/ | Entering regular expressions for G Data Outbreak Shield | |
Trendmicro | |||
| Website-Allowlist | »^[^:]*://[^\.]*\.activeupdate\.trendmicro\.com/
»^[^:]*://[^\.]*\.trendmicro-g\.georedirector\.akadns\.net/ »^[^:]*://[^\.]*\.trendmicro\.com/ »^[^:]*://[^\/]*\.census\.trendmicro\.com/ |
Entering regular expressions for Trendmicro | |
McAfee SaaS | |||
| Website-Allowlist | »^[^:]*://vs\.mcafeeasap\.com/
»^[^:]*://download\.mcafee\.com/ |
Entering regular expressions for McAfee SaaS | |
Symantec | |||
| Website-Allowlist | »^[^:]*://[^\/]*\.symantecliveupdate\.com/ | Entering regular expressions for Symantec | |
Avira | |||
| Website-Allowlist | »^[^:]*://.*\.avira-update\.(com|net)/ or »^[^:]*://.*\.avira\.(com|net)/ |
Entering regular expressions for Avira | |
F-Secure | |||
| Website-Allowlist | »^[^:]*://.*\.sp\.f-secure\.com/ »^[^:]*://[^\.]*\.f-secure\.com/ »^[^:]*://[^\.]*\.orsp\.f-secure\.com/ | Entering regular expressions for F-Secure | |
Bitdefender | |||
| Website-Allowlist | »^[^:]*://upgr-mmxiii\.cdn\.bitdefender\.net | Entering regular expressions for Bitdefender | |
Microsoft Office | |||
| Website-Allowlist | (tested with Office 2013, Office 365) »^[^:]*://officecdn\.microsoft\.com/ »^[^:]*://officecdn\.microsoft\.com\.edgesuite\.net/ |
Entering regular expressions for Microsoft Office | |
Sophos | |||
| Website-Allowlist | »^[^:]*://.*\.sophosupd\.(com|net)/ »^[^:]*://http\.00\.s\.sophosxl\.net/ | Entering regular expressions for Sophos | |
ESET | |||
| Website-Allowlist | »^[^:]*://[^\.]*\.eset\.com/ | Regular Expression für ESET | |
Create network object | |||
| Additionally, with ESET-Scanner you must exclude the update servers from the proxy. Since the scanner first compares the database differences and the license at a server. Then an update server is communicated, which is addressed directly via IP address (not via the host name). | |||
To do this, create network objects in the "external" zone with the following IP addresses (it is best to create a group into which you move all network objects).
| |||
| Further information on this topic can be found in the article on network objects. | |||
Add rule | |||
| Name global |
Edit | Edit global configuration profile | |
| Transparent Mode | |||
| Click on the “+ Add transparent rule” button | |||
In Transparent mode, you then add a rule:
| |||
| Further information on this topic can be found in the article on HTTP proxies. | |||


