Webfilter configuration on the UTM
Last adaptation to the version: 14.1.1 (11.2025)
New:
- BetaFor participants on the Beta Channel only:
- New options for moving elements now available
- New feature similarity detection
- Rule sets are now displayed as labels in the profiles (14.1.0)
- Rule sets are now added or removed directly in the profiles (14.1.0)
- International domain names (e.g. special character) are supported (14.1.0)
notemptyThis article refers to a Beta version
Prerequisite
In order for the UTM to "see" the network traffic it is supposed to filter, the proxy of the UTM must also be used for https.
Therefore either
- the SSL interception ( Area SSL interception)
and
the transparent mode for https must be activated (menu Area Transparent mode).
or
on every host the UTM is set up as a proxy in every browser
Overview
- In the rule sets, the entire access or individual domains, URLs or categories are blocked or allowed
- The validity of the rule sets can be limited according to the day of the week and time of the day
- The rule sets are assigned to profiles
- The profiles are assigned to network or user groups
- The rule sets are checked in sequence to see whether they apply (in terms of content and time)
Webfilter
Profiles Profiles
General profile | |||
In the individual profiles, the rule sets are linked to
For profiles applies:
| |||
| The elements can be moved. notemptyNew as of v14.1.1 Additional options available by right-clicking on the icon |
UTMuser@firewall.name.fqdnApplications 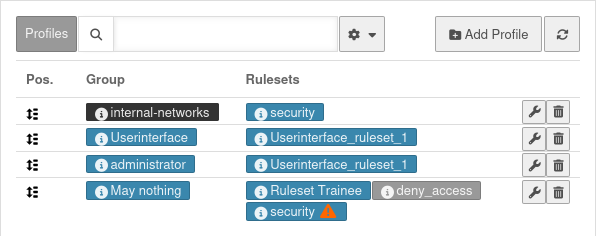 Webfilter - Profiles section Webfilter - Profiles section
| ||
| security | notemptyNew as of v14.1.0 Rule sets are displayed as labels. Blue: Rule set is applied | ||
| security | Gray: Rule set is decativated | ||
| security Rule set is overlaid by… | This rule set is completely or partially overlaid by another rule set and is therefore completely or partially not applied Details in the responsive hovertext | ||
| Edit | Opens the dialog for editing the profile. You can:
| ||
| Delete | Deletes the profile | ||
Add profile |
Opens the dialogue for adding a profile | ||
| Network or user group: | administrator | Network or user group to which the profile is to be applied | UTMuser@firewall.name.fqdnApplicationsWebfilter 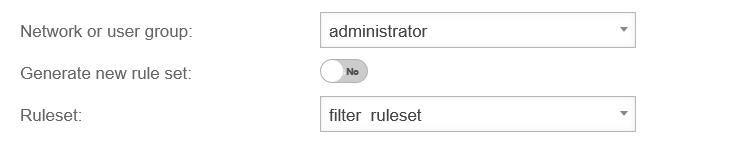
|
| Generate new rule set: | Yes Default |
If Yes, automatically creates a new rule set assigned to this profile
| |
| Ruleset: (Only if generate new rule set No is deactivated) |
filter_ruleset | Existing rule set to apply in this profile Information as in the following section edit Profile | |
Edit profile Edit profile
| |||
| Network or user group: | May nothing | Network or user group to which the profile is to be applied | UTMuser@firewall.name.fqdnApplicationsWebfilter 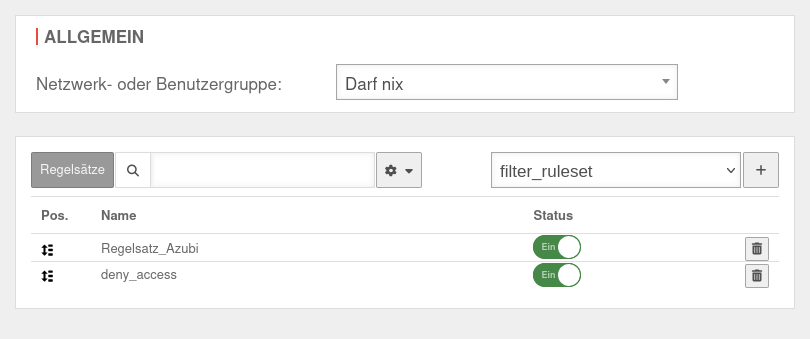
|
| Ruleset: | notemptyNew at this point | Existing rule set to be added to this profile with the button | |
| Status | On | Activates or deactivates Off a rule set Suitable for testing or temporary deactivation | |
| Delete | Removes the rule set from the profile | ||
Rule sets Rule sets
| |||
| The rule sets define which websites and categories are blocked and released. The rule sets can also be limited for a period of time, e.g. to allow employees to surf privately during their lunch break. | UTMuser@firewall.name.fqdnApplications 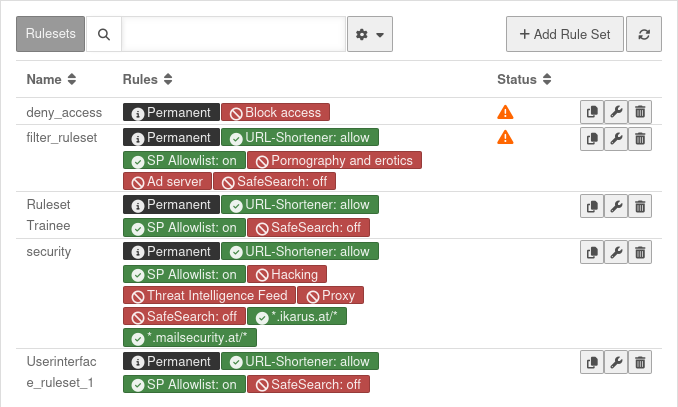 Rule sets Rule sets
| ||
| Copy rule set notemptyNew as of v12.7.0 |
Opens the dialogue for editing a rule set with the copied properties of the selected rule | ||
| Edit | Opens the settings of the rule set for editing | ||
| Delete | Deletes a rule set | ||
| Opens the dialogue for creating a new rule set | |||
Rule set detailsRule set details
GeneralGeneral | |||
| Name: | security | Unique name | UTMuser@firewall.name.fqdnApplicationsWebfilter 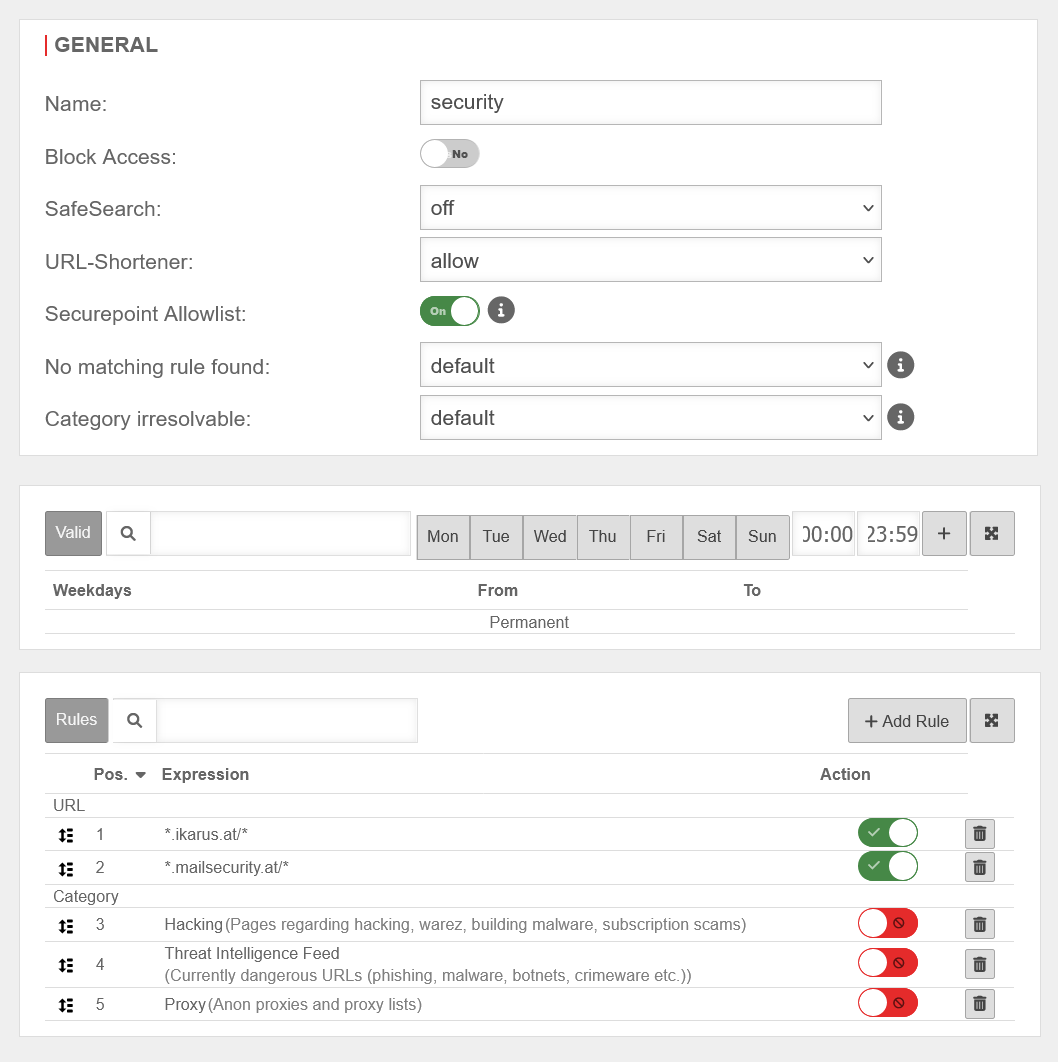 Display when adding a new rule set or editing an existing rule set Display when adding a new rule set or editing an existing rule set
|
| Block access: | No | All websites will be blocked | |
| SafeSearch: | Content that is not suitable for minors is not filtered. | ||
| Text, images and videos that are not suitable for minors are filtered out of the search results. | |||
| Pictures and videos that are not suitable for minors are filtered out of the search results, but corresponding texts are not. | |||
| URL-Shortener: | Defines access to websites whose host names use URL shortener services. Here, you can choose whether these are blocked or allowed regardless of the actual destination or whether the host name is resolved and then handled according to existing rules. | ||
| Securepoint Allowlist: | On | Access to URLs that Securepoint designates as trusted The Securepoint Allowlist contains, for example: Reputable addresses, public and corporate websites, technical services that should not be blocked. | |
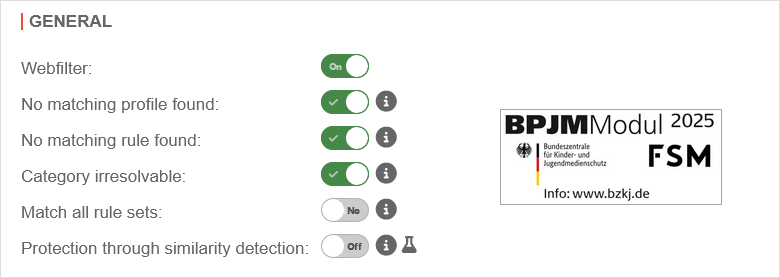
| No matching rule found: | Adopts the global settings from Webfilter general | ||
| Blocks the data traffic if no suitable rule was found in the rule set | |||
| Allows data traffic if no suitable rule was found in the rule set | |||
| Category irresolvable: | Adopts the global settings from Webfilter general | ||
| Blocks data traffic if the category has not been resolved. (For example, if no connection to the server could be established.) | |||
| Allows data traffic if the category has not been resolved. (For example, if no connection to the server could be established.) | |||
Valid Valid
| |||
| Here one or more time periods can be assigned to the rule set, during which it is valid | |||
Rules Rules
| |||
Define here which websites are allowed or not to be reached.
| |||
| The elements can be moved. notemptyNew as of v14.1.1 Additional options available by right-clicking on the icon | |||
| allow | Allows data traffic | ||
| block | Blocks data traffic | ||
| Delete | Deletes the rule | ||
Add Rule | |||
| Type | anyideas.com | Domain in plain text notation. All subdomains and subpages are filtered. | UTMuser@firewall.name.fqdnApplications 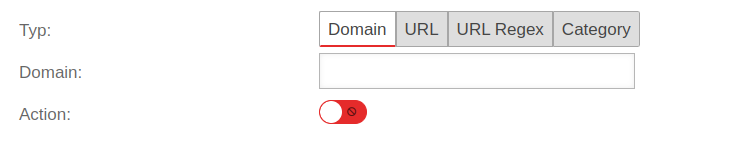 Filter rules Filter rules
|
| Type | *.anyideas.com/pages/* | Only the exact URL is filtered (wildcard * is possible). | |
| Type | .*\.anyideas\.com | URL in regex format, which allows numerous placeholders Syntax of regular expressions - Regex | |
| Type | Unknown |
This allows you to block access to all websites that have not yet been classified by Securepoint.
| |
Allowlisting example Allowlisting example
| |||
| In this example, the URL www.google.de and the category Education were added to the allowlisting via the function . Since the web filter processes the rules from top to bottom, in this example the category Education had to be manually pushed to the first position. |
UTMuser@firewall.name.fqdnApplicationsWebfilter 
| ||
Detailed application examples can be found on a separate page.
Examples of exceptions for Windows update server
For more examples on setting up the Webfilter, authentication exceptions, virus scanner and SSL interception regarding Windows updates, see the Knowledge Base article Windows Updates with HTTP proxy and webfilter