Last adaptation to the version: 14.1.1 (11.2025)
- BetaFor participants on the Beta Channel only:
- Installer for the Windows VPN-Client
- Icons in the User overview for active functions
- Info note added to WireGuard Peer Addresses
- Note on file names added User overview for active functions
- CLI command for Support-User Information
Introduction
The users entered here are stored in a local database on the appliance.
The authentication configured at this point is also performed against the local database.
In addition, local user groups can be assigned to an AD/LDAP group.
User overview
| Caption | Value | Description | UTMuser@firewall.name.fqdnAuthentication 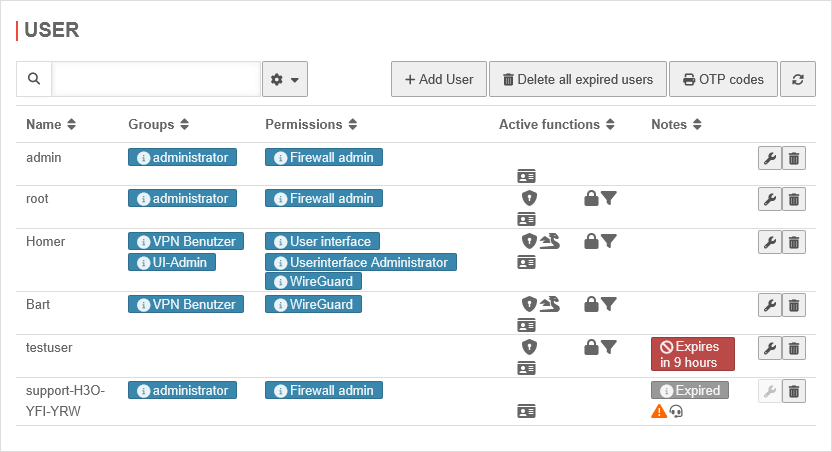 User administration User administration
|
|---|---|---|---|
| Name | admin |
Login name of the user | |
| Groups | Administrator | Group membership of the respective user | |
| Permissions | Firewall administrator | Authorizations, configuration under Groups | |
| Active functions notempty New as of v14.1.0 |
Application: SSL VPN Configured by: User |
Shows which user options are configured | |
| L2TP is configured | |||
| An SSL VPN connection is configured | |||
| A WireGuard connection is configured | |||
| An IPSec connection is configured | |||
| The login password may be changed | |||
| The mail filter is configured | |||
| Wake on LAN (WOL) is configured | |||
| The use of OTP is configured/possible | |||
| Notes | Expires in 9 hours | After expiration the user can no longer log in. | |
| Edit or delete the user | |||
| Search across all displayed values, including under notes or authorizations. | |||
| Creates a new user. see below | |||
| Does exactly that. Support users are automatically removed 24 hours after the expiry date at the latest. | |||
| Generates a pdf document with OTP codes in QR format and plain text for all users except the user admin. notempty One OTP code is displayed per page. | |||
| Updates the table | |||
| Enlarges the display area for the table to the height of the screen. | |||
Support User
The support user is a temporary administrator who can be activated, for example, to be supported by Securepoint support.
| Caption | Value | Description | UTMuser@firewall.name.fqdnSupport User 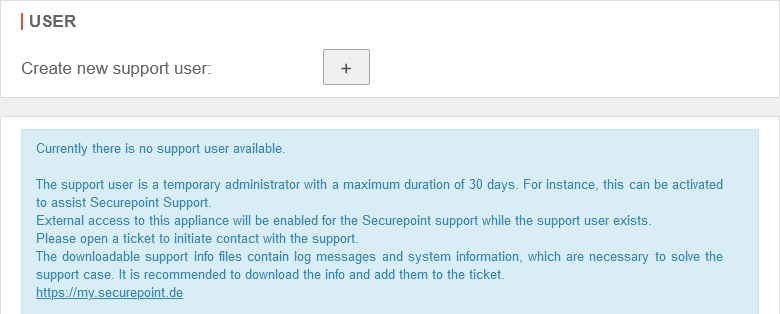 Create support users Create support users
|
|---|---|---|---|
| Create a new support user: | Click on to create a new support user. A new dialog box will open. | ||
| Login name: | support-XLP-QHY-EE5 | Arbitrary name beginning with support-. Manual entry is not possible. | UTMuser@firewall.name.fqdnSupport User 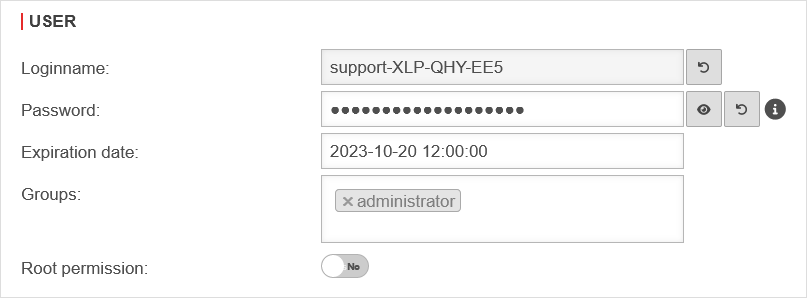 UTM v12.6 Authentifizierung Benutzer Supportbenutzer-en.png UTM v12.6 Authentifizierung Benutzer Supportbenutzer-en.png
|
| Generate new login name at random. | |||
| Password: | ••••••••••••••••••• | The Password tab defines the strength of the password and whether the password can be changed by the user. | |
| Show password | |||
| Generate new random password | |||
| Expiration date: | 2023-10-20 12:00:00 | After expiration the user can no longer log in. However, the expiration date can be extended again. (It cannot be set in the past in the web interface!) | |
| Groups: | administrator | By default, the first user group with the authorization Firewall Administrator is entered. You can select other groups that also have this permission. | |
| Root permission: | No | With activation gives the user additional root privileges. When connecting with SSH, the login is done directly on the root console! | |
| notempty New as of v14.0.0 |
The downloadable support information contains log messages and system information. These may be necessary to solve a support case. It is recommended to download these and attach them to a support ticket. | ||
| Username and password are saved to the clipboard. The content of the clipboard then looks like this: Username: support-NII-Z53-Yk2 Password: UMC-DP6-FSK-F46-ULD notempty Before saving, the login name and the password must be noted! The password can no longer be displayed after saving. | |||
| Save | Clicking the button creates and saves the support user. | ||
| CLI command | user support new name support-4711 password insecure-ChangeTh1s groups administrator expirydate 2024-10-20 12:00 flags ROOT |
The support user can also be created via CLI if required. The value for the expiration date can either be specified as Unixtime (time in seconds since 1.1.1970 00:00) or in the format: YYYYY-MM-DD HH:MM. notempty Neuer Befehl: Information on the support user can then be retrieved using the command view supportuser (Link to the Wiki article) | |
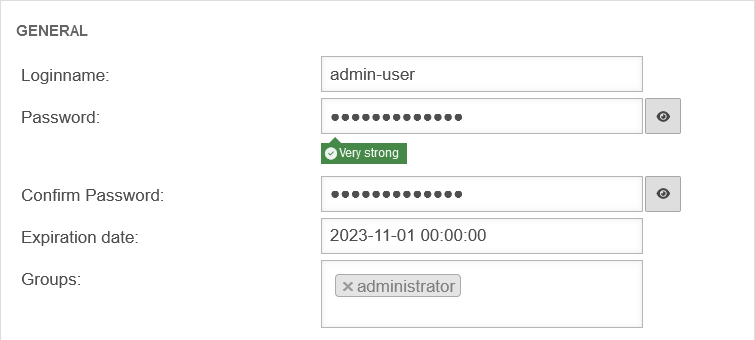
General User
Add / edit user
/The dialog Add user opens. This dialog contains several tabs. There is no need to make entries in all tabs. With the entries are accepted.
User General
root user
VPN
Here fixed tunnel IP addresses can be assigned to the users.
L2TP
| ||
| Caption | Description | 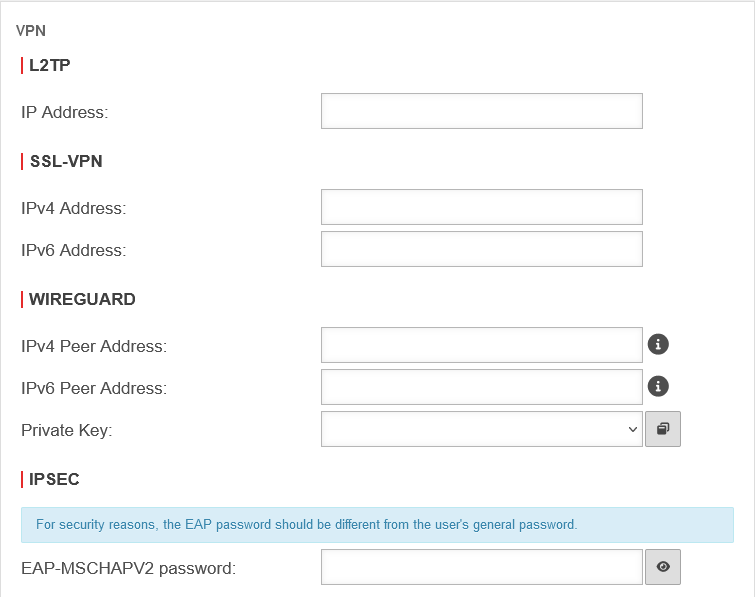 |
|---|---|---|
| L2TP IP Address: | The tunnel IP address for L2TP | |
SSL-VPN
| ||
| IPv4 Address: | The tunnel IPv4 address for SSL-VPN | |
| IPv6 Address: | The tunnel IPv6 address for SSL-VPN | |
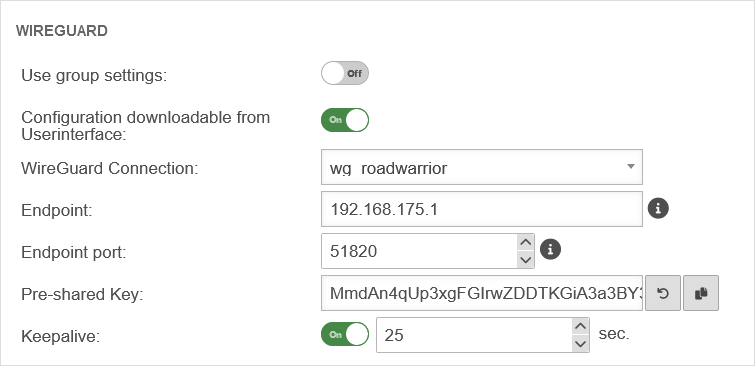
WIREGUARD
| ||
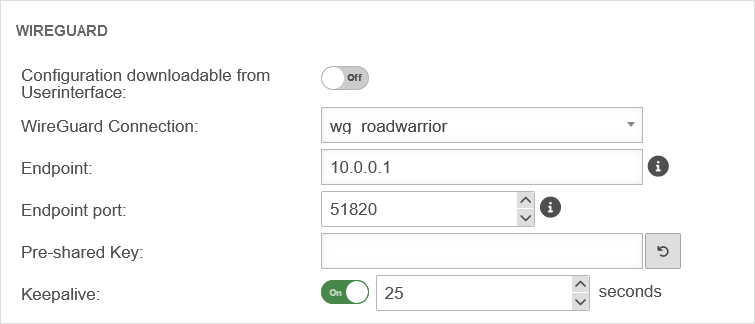
| IPv4 Peer Address: | Die Tunnel IPv4-Adresse für WireGuard Diese Option konfiguriert WireGuards AllowedIPs für den Benutzer-Client. Die IPs der Gegenstellen werden in der UTM als allowed IPs hinterlegt. | |
| IPv6 Peer Address: | Die Tunnel IPv6-Adresse für WireGuard Diese Option konfiguriert WireGuards AllowedIPs. Die IPs der Gegenstellen werden in der UTM als allowed IPs hinterlegt. | |
| Private key: | Private key to be used for a user-related WireGuard connection. | |
| By clicking the button, the key management can be opened and a key can be created. | ||
IPSEC
| ||
| EAP-MSCHAPV2 Password: | The password for EAP-MSCHAPV2 For security reasons, the EAP password should differ from the user's general password. This HowTo describes the configuration of IPSec EAP | |
WireGuard
SSL-VPN
| Caption | Value | Description | UTMuser@firewall.name.fqdnAuthenticationUser 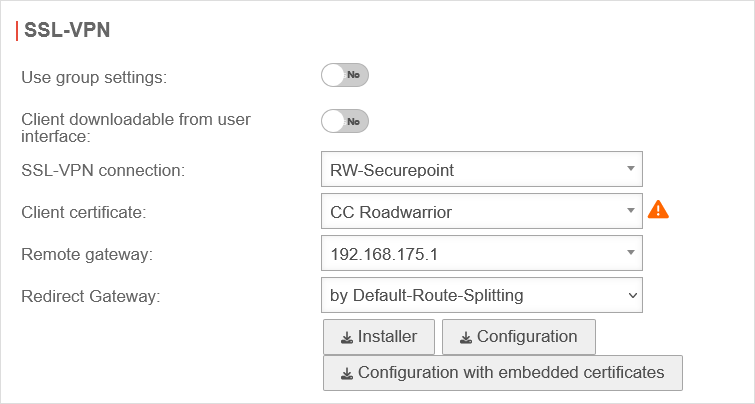 SSL-VPN settings for users SSL-VPN settings for users
|
|---|---|---|---|
| Use group settings: | No | If the user is a member of a group, the settings can be adopted from there. The following settings are then greyed out here and are to be configured in the Area Groups menu. | |
| Client downloadable in the user interface | Yes | The Securepoint VPN Windows client can be downloaded from the user web interface (accessible via port 1443 by default). The port is configurable in the Tab Server settings Button / User Webinterface Port: : 1443. | |
| SSL VPN connection: | RW-Securepoint | Selection of a connection created in the menu. | |
| Client certificate: | CC Roadwarrior | A certificate must be specified that the client uses to authenticate itself to the UTM. It is also possible to use ACME certificates. | |
| Remote Gateway: | 192.168.175.1 (Example-IP) | External IP address or DNS resolvable address of the gateway to which the connection is to be established. | |
| Redirect Gateway: |
by Default-Route-Splitting notempty New as of v14.1.1 |
All data traffic is routed through the tunnel. The VPN tunnel acts as the primary default gateway. If the tunnel does not respond, the regular default gateway is used. | |
| by replacing the default gateway (deprecated) | All data traffic is routed through the tunnel. Completely replaces the default gateway (without fallback). | ||
| Off | Only destinations behind the VPN are routed through the tunnel. The default gateway is used for all other destinations | ||
notempty New as of v14.1.1 |
Lädt ein Installationsprogramm herunter, mit dem man entweder
Der installierte Client aktualisiert sich bei neuen Updates eigenständig - unabhängig von der UTM-Version. | ||
| Downloads the configuration files for any VPN clients. The file contains the necessary configuration files and certificates in the local_firewall.securepoint.local.tblk folder. | |||
| notempty New as of v14.0.1 |
Downloads the configuration file for any VPN client. The certificates are written directly to the ovpn file. | ||
| The file name contains the user name and notempty v14.1.1 | |||
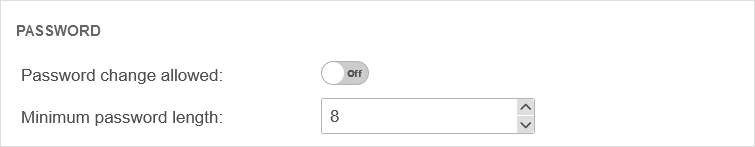
Password
The Password tab defines the strength of the password and whether the password can be changed by the user.
Mailfilter
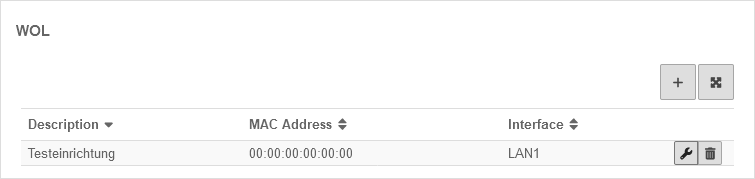
WOL
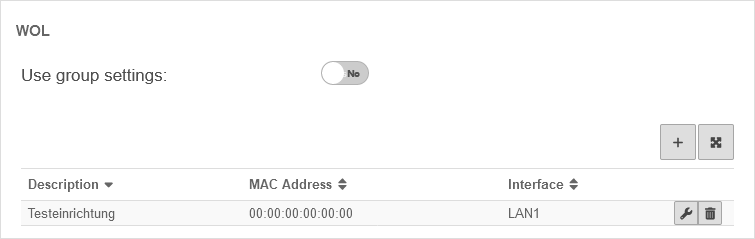
WOL stands for Wake on LAN and switches on a computer via the network card. In order to start the computer via data packet, the computer must also support this. This is usually configured in the BIOS or UEFI.
- After logging into the user interface, the user can trigger a WOL for devices entered here.
- 2 magic packets are sent via UDP to destination ports 7 and 9. notemptyNew as of v12.7.0
- The magic packets can also be sent in VLANs
OTP
There is a separate page in the wiki for the OTP settings.
Groups
Some settings described in the Users section can also be set for the entire group. However, the settings for the individual user replace the group settings.
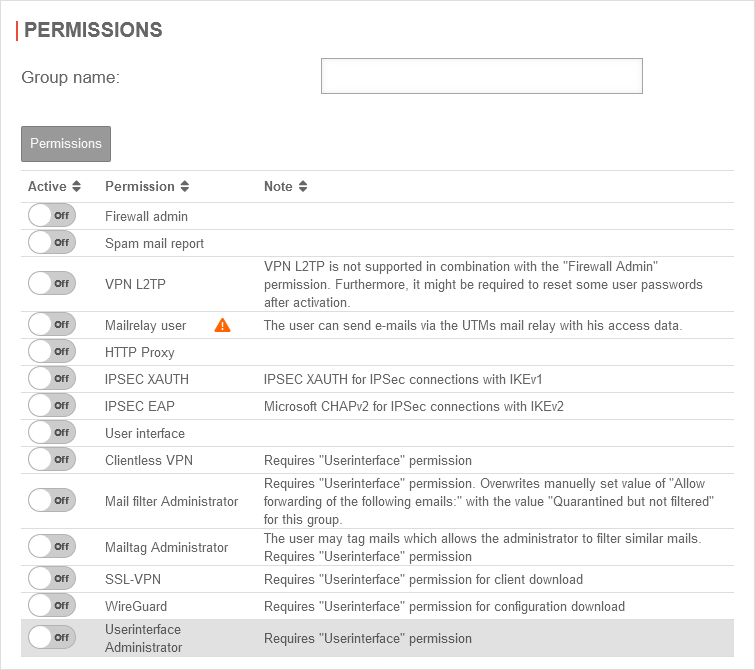
Permissions
Clientless VPN
Connections created under are displayed here.
Here you can configure and add connections.
| Clientless VPN | |||
| Caption | Default | Description | 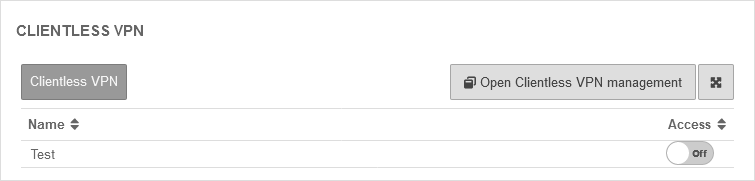 |
|---|---|---|---|
| Name | Name of the connection | ||
| Access | Off | If activated, members of this group can use this connection. | |
Further information in the article to Clientless VPN.
WireGuard
SSL-VPN
This is where to configure settings for the SSL VPN for an entire group.
All users share the same certificate when using the group settings!
SSL VPN settings of individual users override the group settings.
| Caption: | Value | Description: | UTMuser@firewall.name.fqdnAuthenticationUser 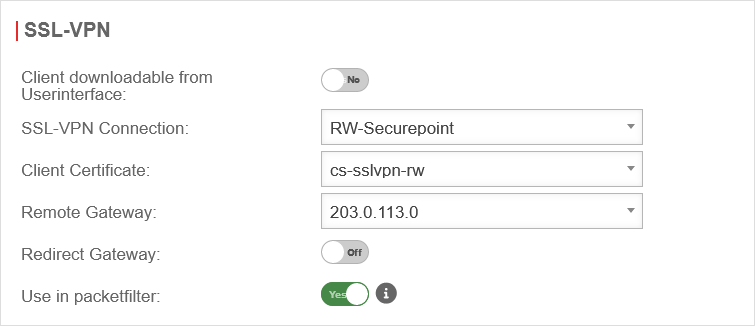 SSL VPN group settings SSL VPN group settings
|
|---|---|---|---|
| Client downloadable in the user interface: | No | If enabled, the VPN client can be downloaded in the user interface | |
| SSL VPN connection: | RW-Securepoint | Select the preferred connection (created under ) | |
| Client certificate: | cs-sslvpn-rw | Select the certificate for this group (created under Area Certificates) It is also possible to use ACME certificates. | |
| Remote Gateway: | 203.0.113.0 | IP address of the gateway on which the SSL VPN clients dial in. Free input or selection via drop-down menu. | |
| Redirect Gateway: | Off | Requests to destinations outside the local network (and thus also the VPN) are usually routed directly to the Internet by the VPN user's gateway. When the On button is activated, the local gateway is redirected to the UTM. This way, these packets also benefit from the protection of the UTM. This setting changes the configuration file for the VPN client. | |
| Use in packet filter: | No | By enabling Yes this option, rules for this group can be created in the packet filter. This can be used to control access for users who are members of this group connected via SSL VPN. | |
Directory Service
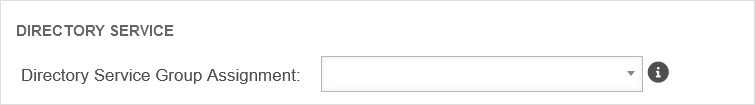
Here you can specify which directory service group the members of this user group should belong to.
In order for a group to be selected here, a corresponding connection must be configured under .
Selection of an AD/LDAP group
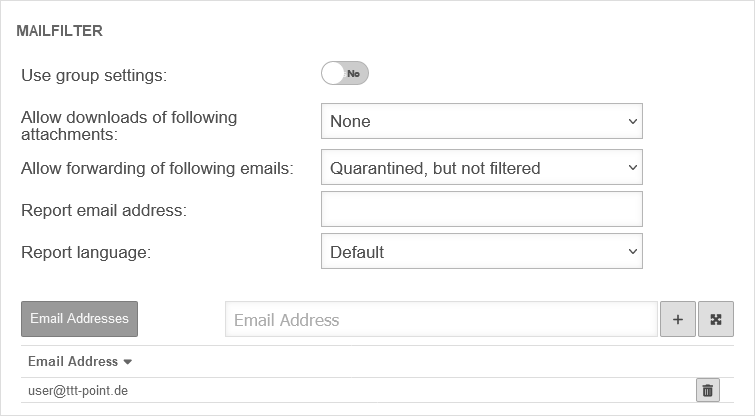
Mailfilter
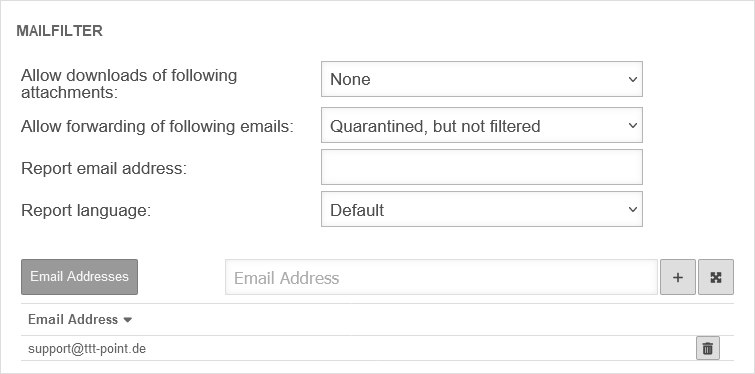
The authorization Userinterface Ein is required.
| Caption | Default | Description |
|---|---|---|
| Allow downloads of following attachments: | (Default) | Members of this group can download attachments from mails in the user interface that meet certain criteria. |
| Allow forwarding of following emails: updated |
Members of this group can forward emails in the user interface that meet certain criteria | |
| (Default) | ||
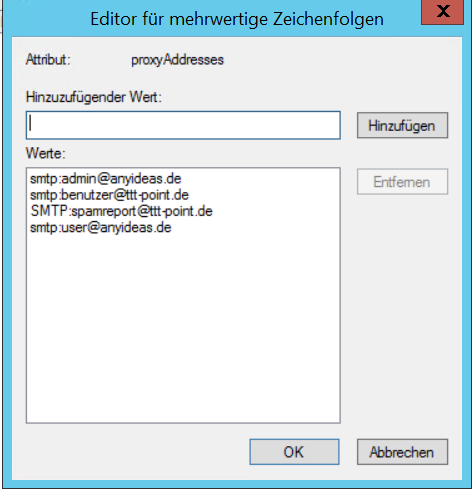
| Report email address: | Email address to which a spam report is sent. If no entry is made here, the spam report is sent to the first email address in the list. If several mail addresses for a user are stored in an AD, the entry configured there as Primary SMTP address is used as the default address..
| |
| Report language: | Default under → Firewall → language of reportsIt can be specifically selected: or | |
| Email address | ||
| Email address | Adding a mail address to the list | |
| support@ttt-point.de | Email accounts that can be viewed by members of this group to control the mail filter. Delete with |
WOL
WOL stands for Wake on LAN and switches on a computer via the network card. In order to start the computer via data packet, the computer must also support this. This is usually configured in the BIOS or UEFI.
- After logging into the user interface, the user can trigger a WOL for devices entered here.
- 2 magic packets are sent via UDP to destination ports 7 and 9. notemptyNew as of v12.7.0
- The magic packets can also be sent in VLANs
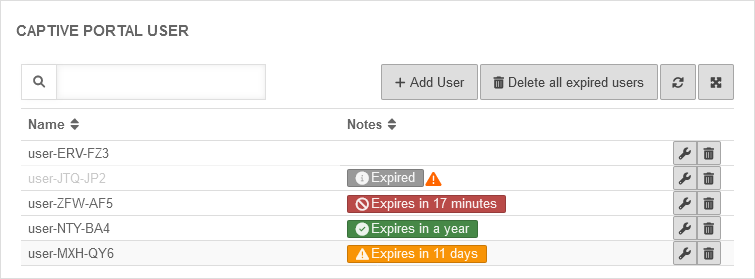
Captive Portal User
Add user
Captive Portal users can be managed by:
- Administrators
- Users who are members of a group with the permission Userinterface Administrator .
They reach the user administration via the user interface.