Last adaptation to the version: 12.6.0
- Updating the AD attributes that are entered in the UTM
- Enter additional parameter Cert attributes for attribute in the UTM
- Updated to Redesign of the webinterface
- 12.2023
Introduction
Users and groups can be connected to an SSL-VPN connection via AD attribute.
User authentication via the UTM with Active Directory for SSL-VPN
Certificate configuration
UTMuser@firewall.name.fqdn
AuthenticationUser 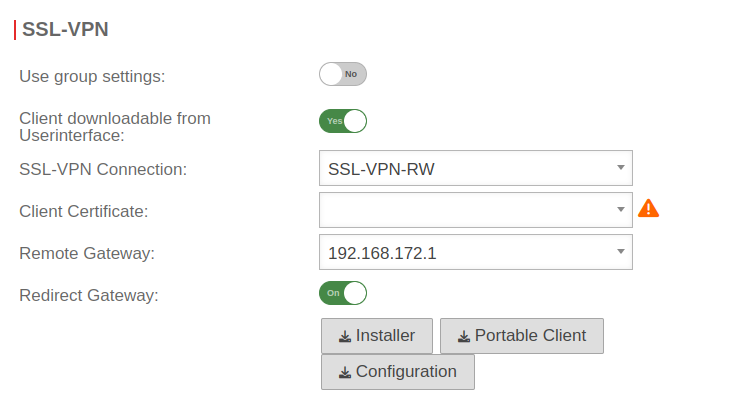 No certificate selected for a user
Under the selected certificates of the respective users and the groups are checked
No certificate selected for a user
Under the selected certificates of the respective users and the groups are checked
- In the User range, the Edit button opens the dialog
- Switch to SSL-VPN range
- For the parameter Client-certificate:, no certificate must be selected
If a certificate is selected in Client-certificate and it cannot be removed, the following command is entered in the CLI user attribute set name "user" attribute "openvpn_certificate" value 0
UTMuser@firewall.name.fqdn
AuthenticationUser 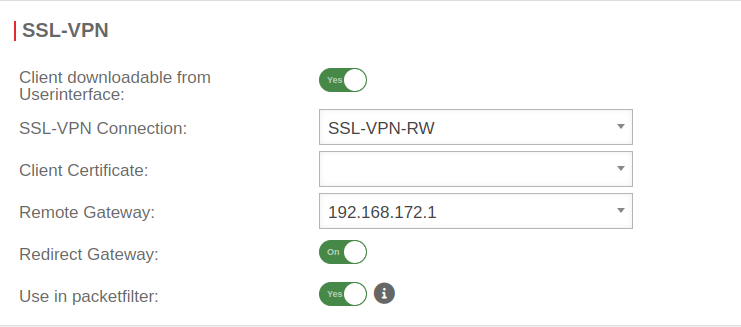 No certificate selected with the group
No certificate selected with the group
- In the Groups range, the Edit button opens the dialog
- Switch to the SSL-VPN range
- For the Client-certificate: parameter, no certificate must be selected
If a certificate is selected in Client-certificate and it cannot be removed, the following command is entered in the CLI user group attribute set name "group" attribute "openvpn_certificate" value 0
UTMuser@firewall.name.fqdnAuthentication 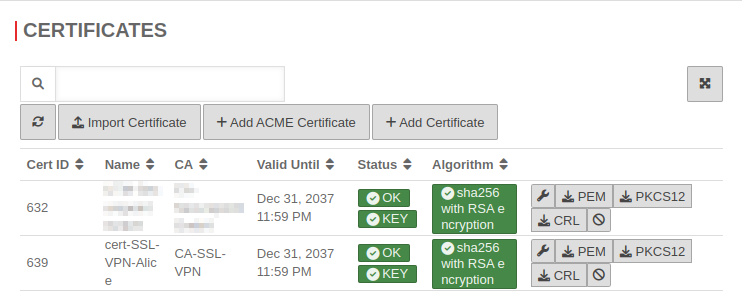 Example certificate of the user Alice
Example certificate of the user Alice
Via Area Certificates a certificate is created for a user using the button.
notempty
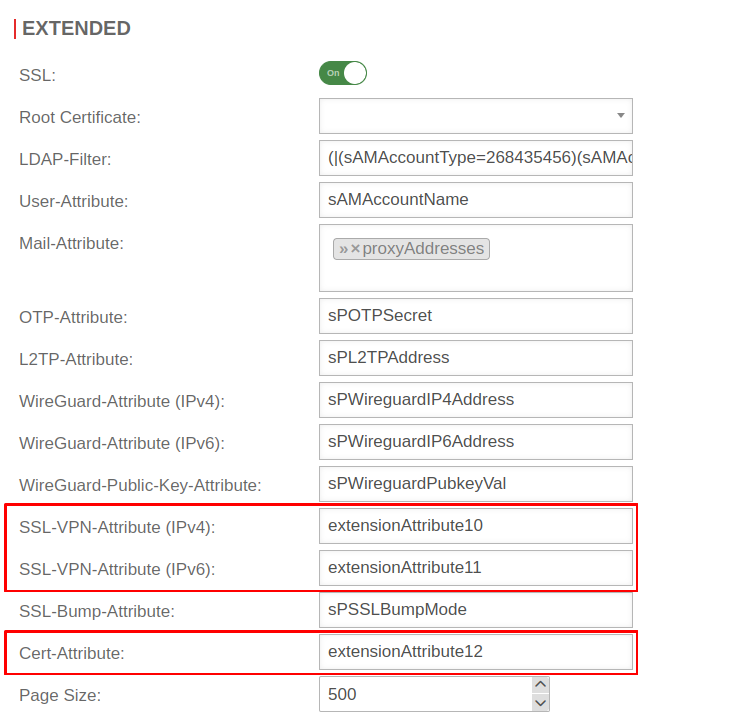
Attributes in Active Directory
The UTM is connected to the Active Directory. Instructions for this can be found in this Wiki article Active Directory Connection. An unused attribute in the Active Directory scheme is required. The certificate name of the user is stored in it.
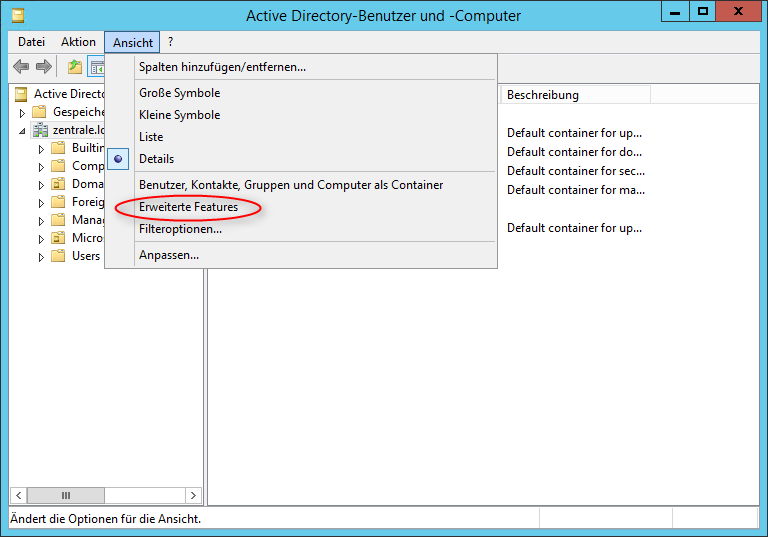
A list of attributes can be found in the Active Directory under Active Directory Users and Computers.
But for this it is necessary to activate the menu item Advanced Features under View.
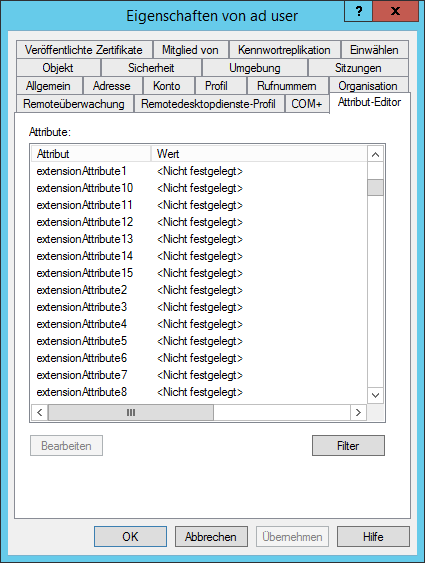
Open "Properties" for the desired user. Switch to the tab Attribute Editor. There is the list with the attributes.
In this example the attributes extensionAttribute1 - 15 are available. Select one of these attributes by storing the certificate name as an attribute for the user.
Enter attribute in the UTM
The name of the attribute from the AD with the certificate name must be entered in the UTM.
In the menu switch to the dialog Extended.