Last adaptation to the version: 12.1
Description
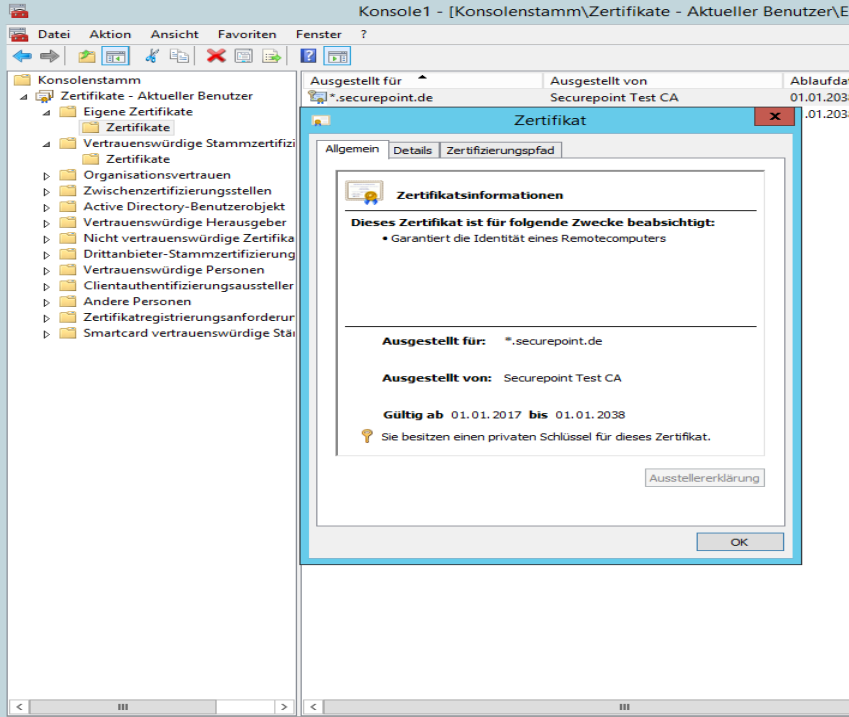
The following describes how a third-party certificate (x509) can be imported into a Securepoint UTM to use it for the reverse proxy, for example.
To import the certificates, they must be available either in PEM format or in PKCS12 format and Base64 encoded.
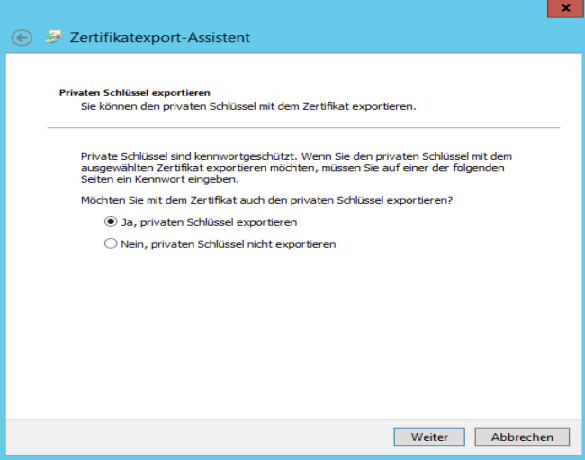
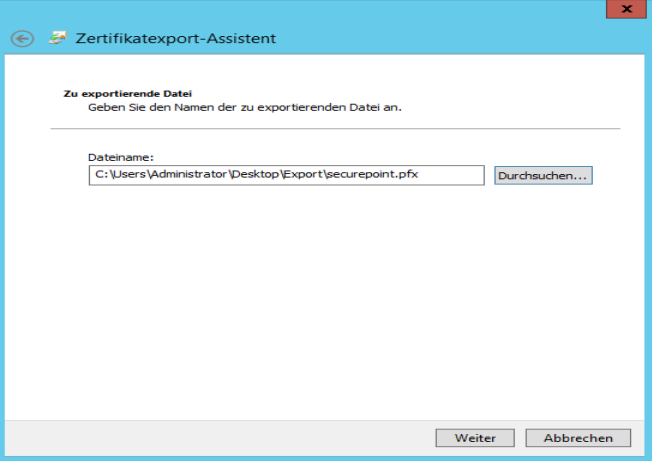
Export certificate
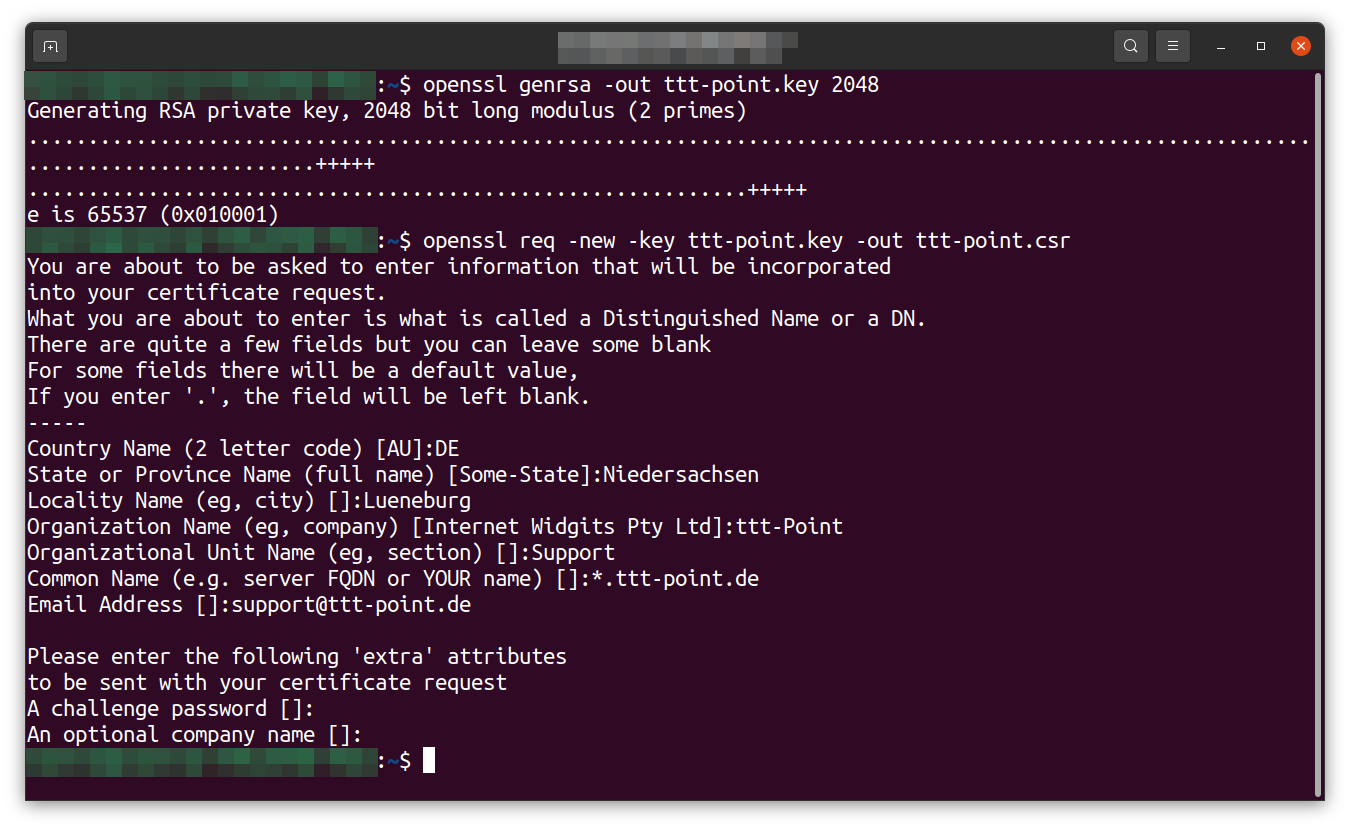
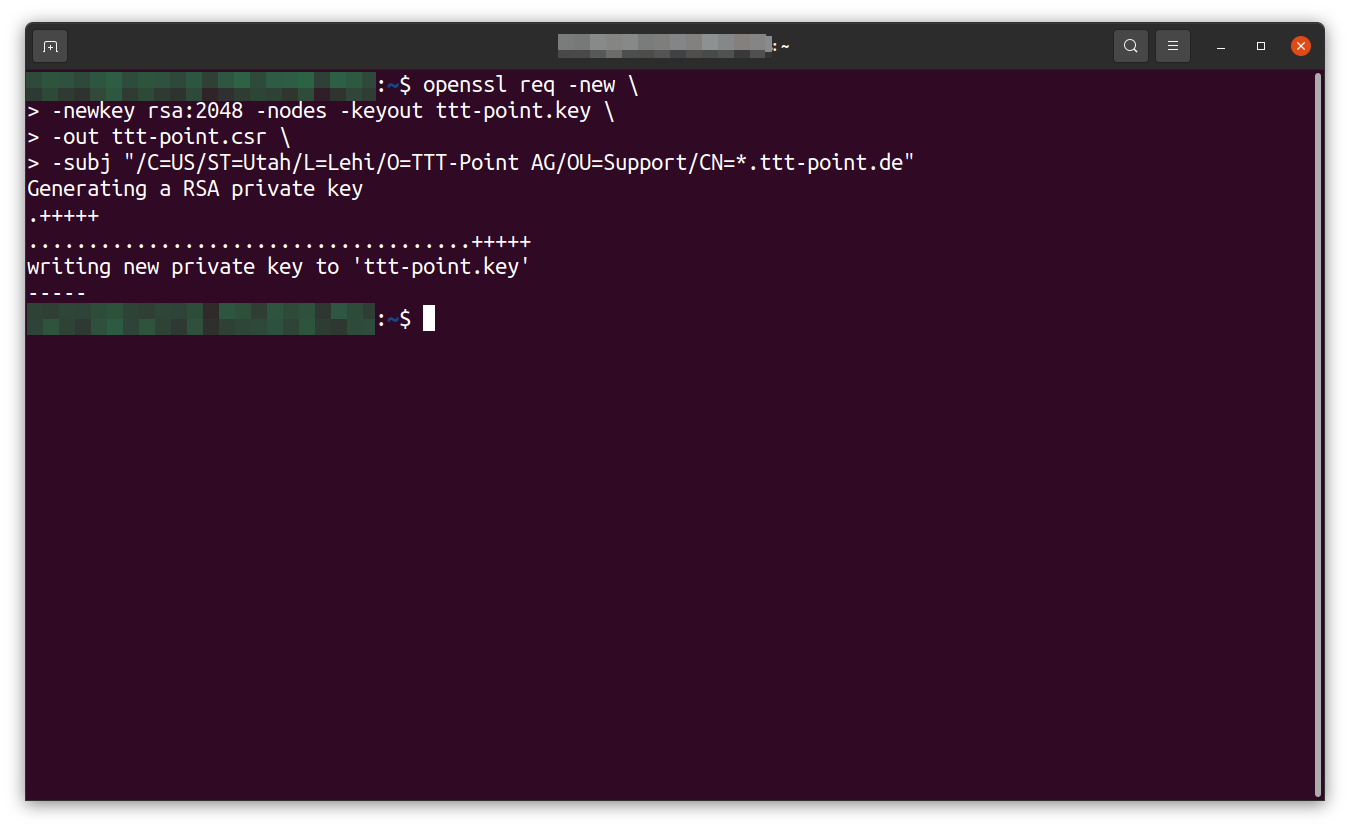
Create CSR for third-party certificate
Import
Certificates and CAs can be imported on the UTM in the menu in the CA tab with the button or in the Certificates tab with the button.
As long as the status is green, the certificate can be used like any other.
Special notes
Sequence of the certificate chain
The following order should be considered during import:
- CA
- Intermediate certificate 1 (if available)
- Intermediate certificate 2 (if available)
- Web server certificates
Convert certificate
Import format
Certificates and CAs to be imported into a UTM must be in the format .pem or .p12 (pkcs12).
Certificates can be converted with the tool openssl - available for all common platforms (part of Linux, call via console) - and the following commands:
| Certificate | Command |
|---|---|
| X509 to PEM | openssl x509 -in certificatename.cer -outform PEM -out certificatename.pem |
| DER to PEM | openssl x509 -inform der -in certificate.cer -out certificate.pem |
| P7B to PEM | openssl pkcs7 -print_certs -in certificate.p7b -out certificate.pem |
Error message during import
During import, the error message "The certificate format is not supported..." may appear.
Password protected certificates in pkcs12 format (.p12 , .pfx , .pkcs12) in conjunction with older ciphers can trigger this error.
Import is usually possible if in the tab General the option Support legacy cryptographic algorithms On is enabled.
Options for importing certificates:
- Convert certificate to *.pem
Certificates can be converted with the tool openssl - available for all common platforms (part of Linux, call via console) - and the following commands:
openssl pkcs12 -in Zertifikat.pfx -out Zertifikat.pem -nodes
Alternatively with the help of an online service
- CLI commands to allow certificate import with obsolete ciphers in the UTM
extc global set variable GLOB_ENABLE_SSL_LEGACY value 1
appmgmt config application "securepoint_firewall"
appmgmt config application "fwserver"
system reboot
cli> extc global get variable GLOB_ENABLE_SSL_LEGACY variable |value ----------------------+----- GLOB_ENABLE_SSL_LEGACY|0 cli> extc global set variable GLOB_ENABLE_SSL_LEGACY value 1 OK cli> extc global get variable GLOB_ENABLE_SSL_LEGACY variable |value ----------------------+----- GLOB_ENABLE_SSL_LEGACY|1 cli> appmgmt config application "securepoint_firewall" cli> appmgmt config application "fwserver"
Issuer
If the message "no issuer found" occurs, the previous certificate is initially missing from the certificate chain.
The issuer of a certificate can be found out with the command: openssl x509 -in file.pem -text
Under the item "Issuer:" you can now view the issuer located at the issuer for download'.